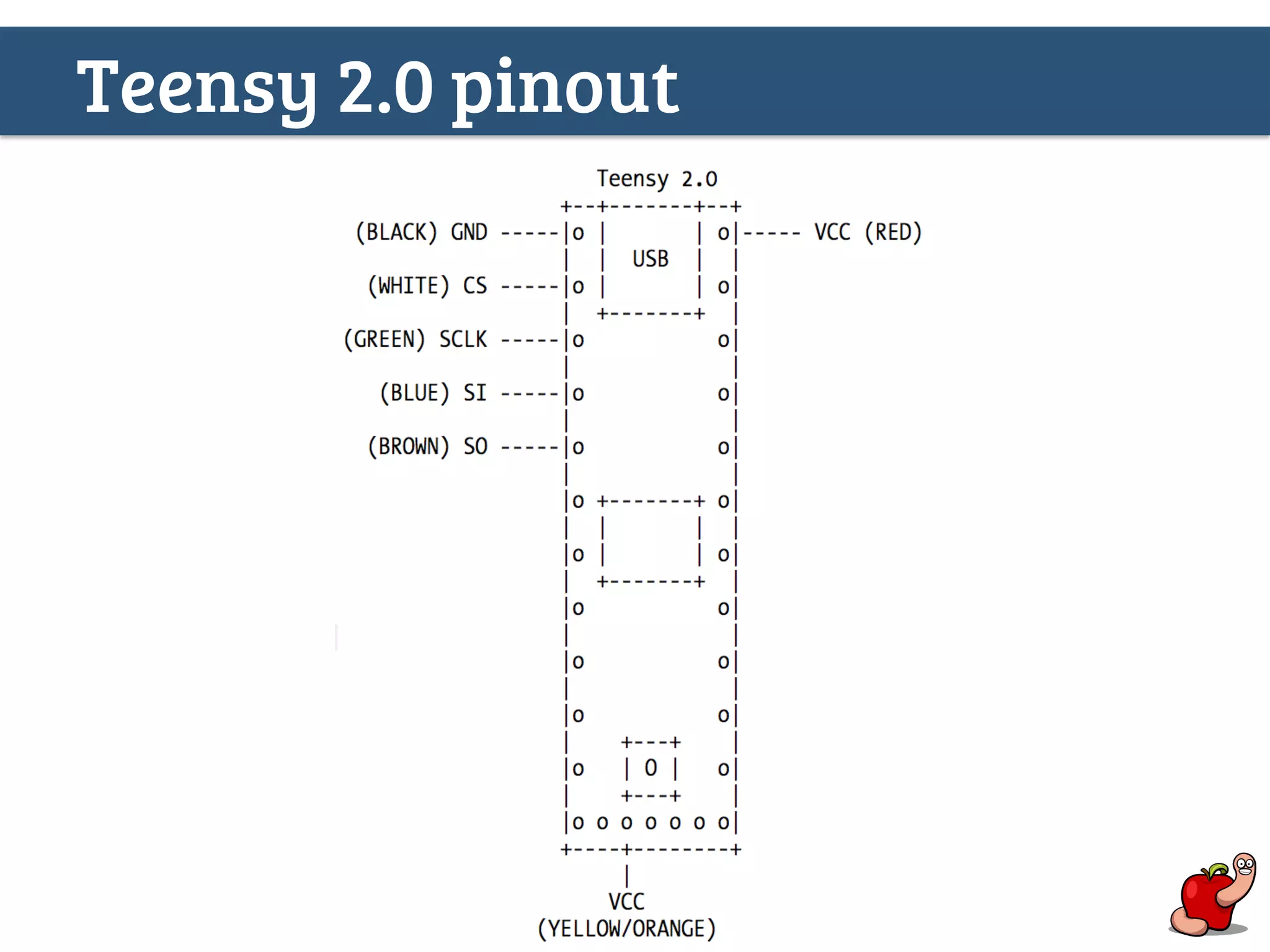
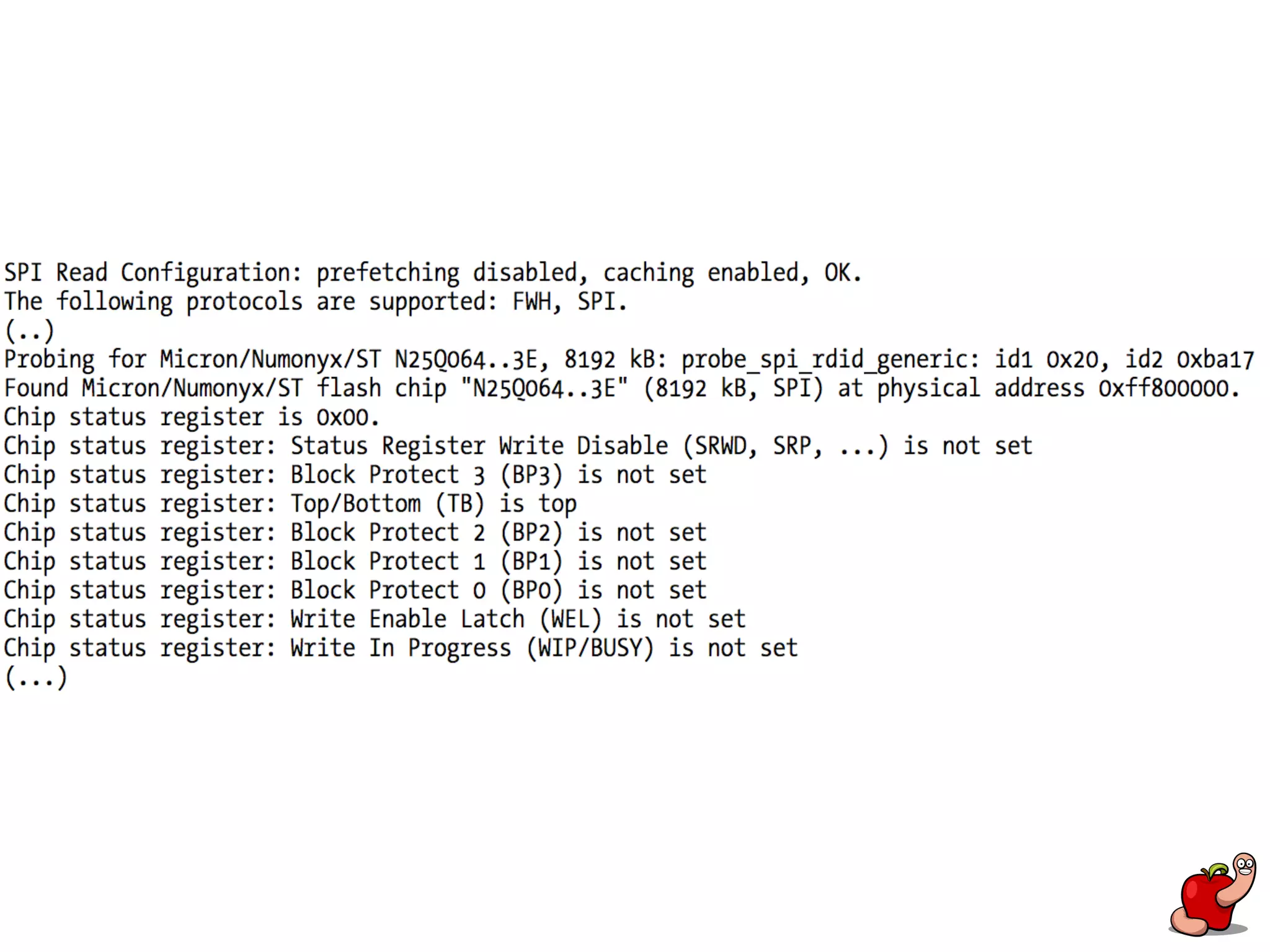
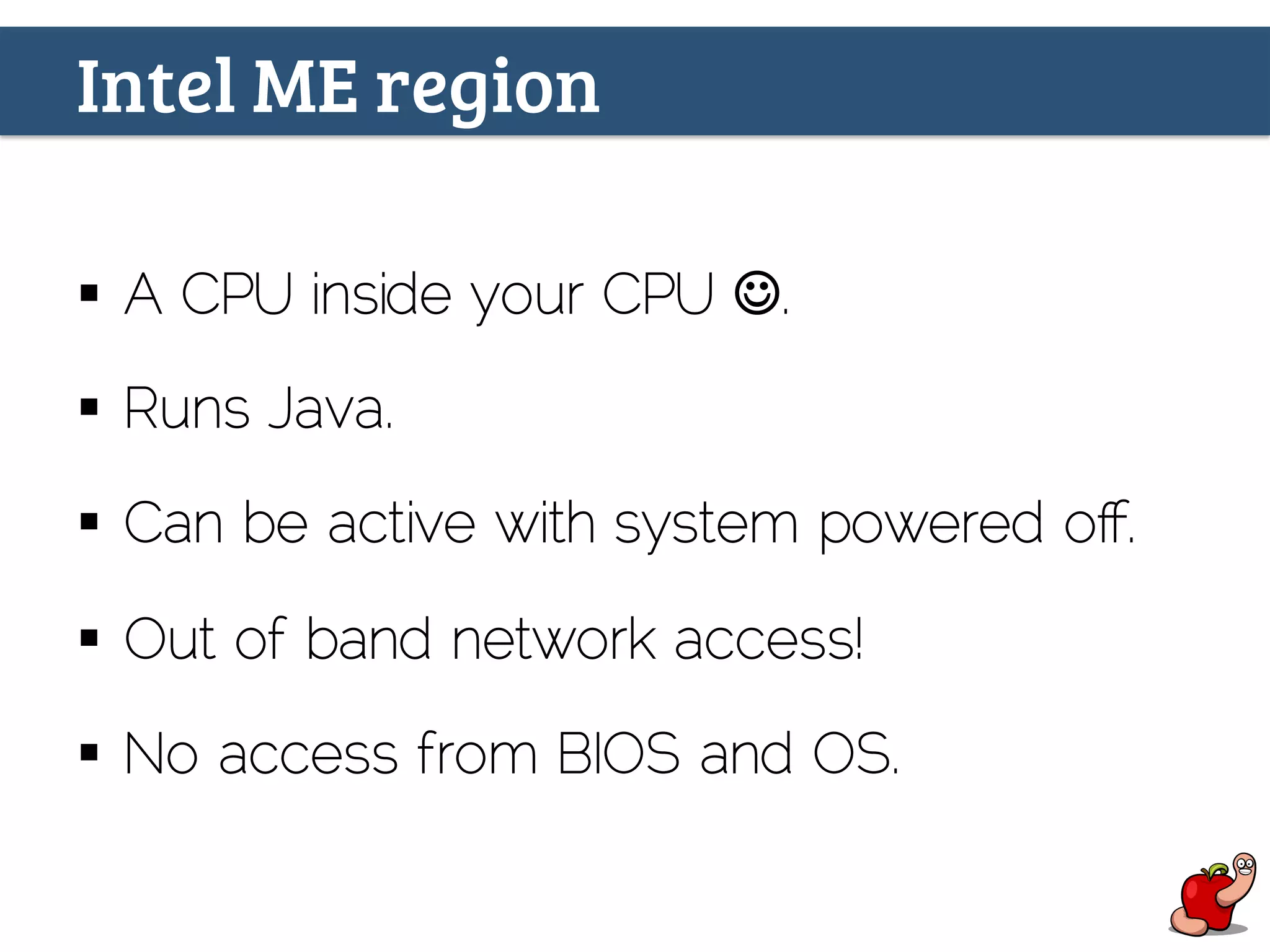
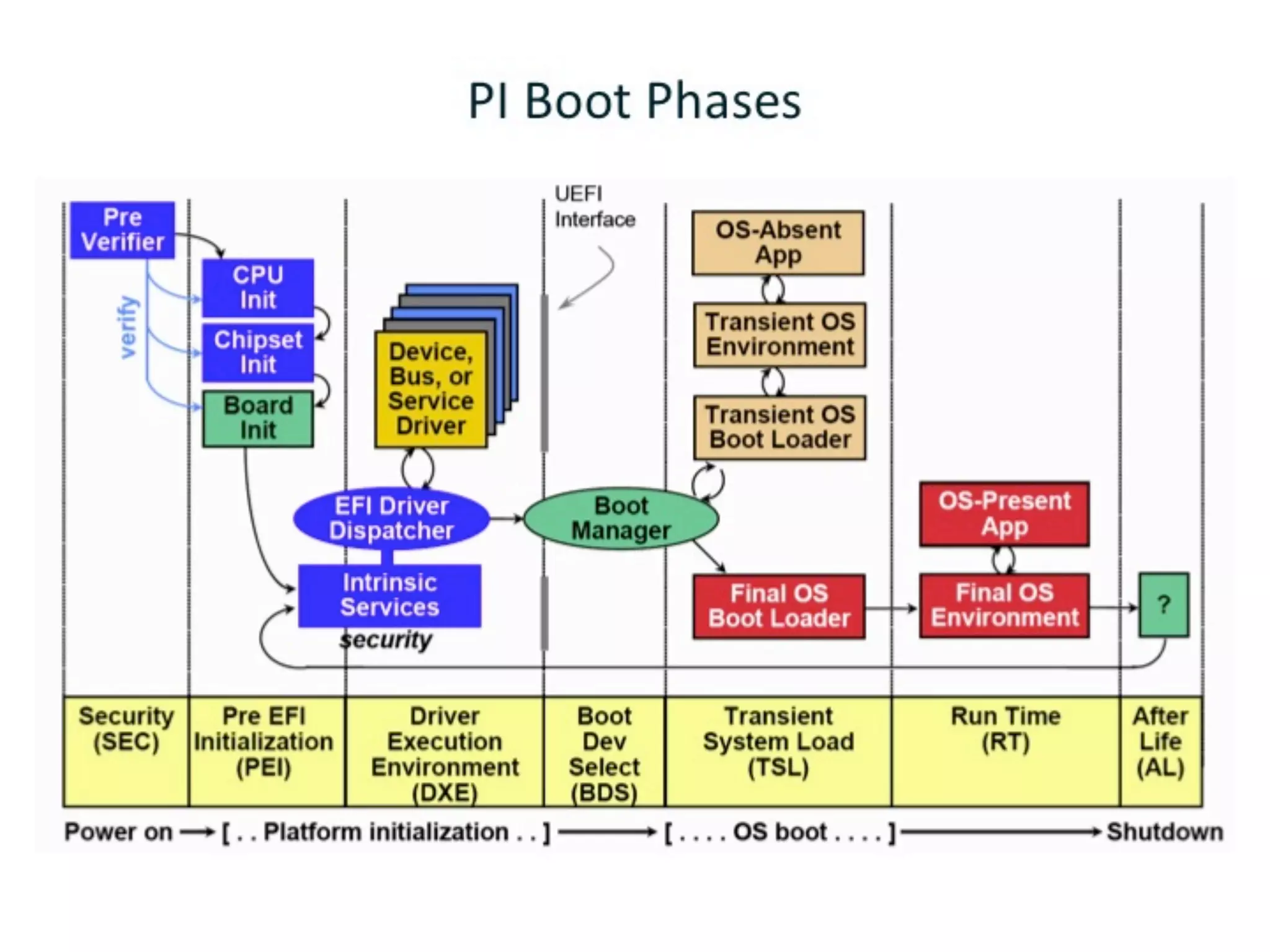
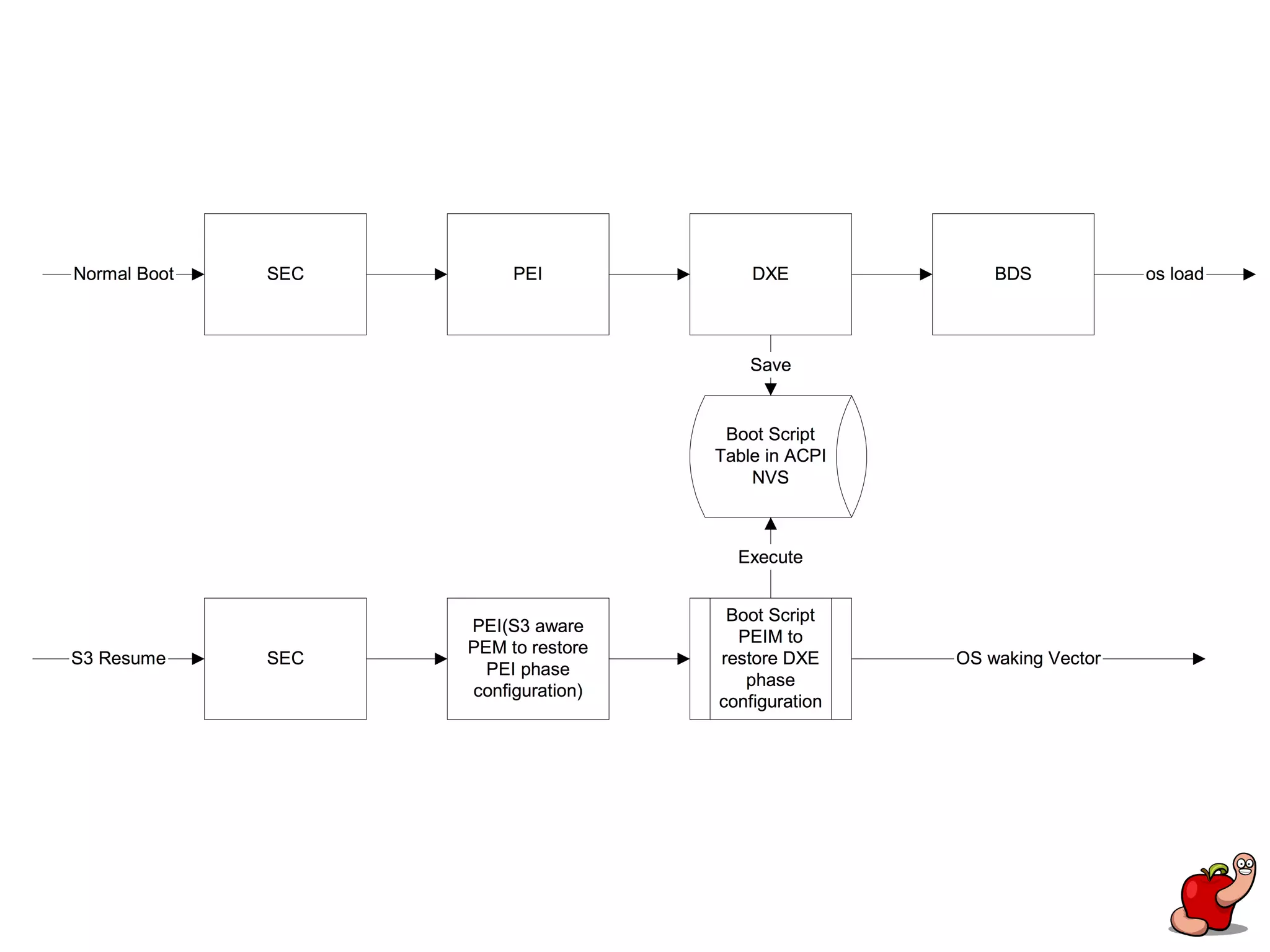
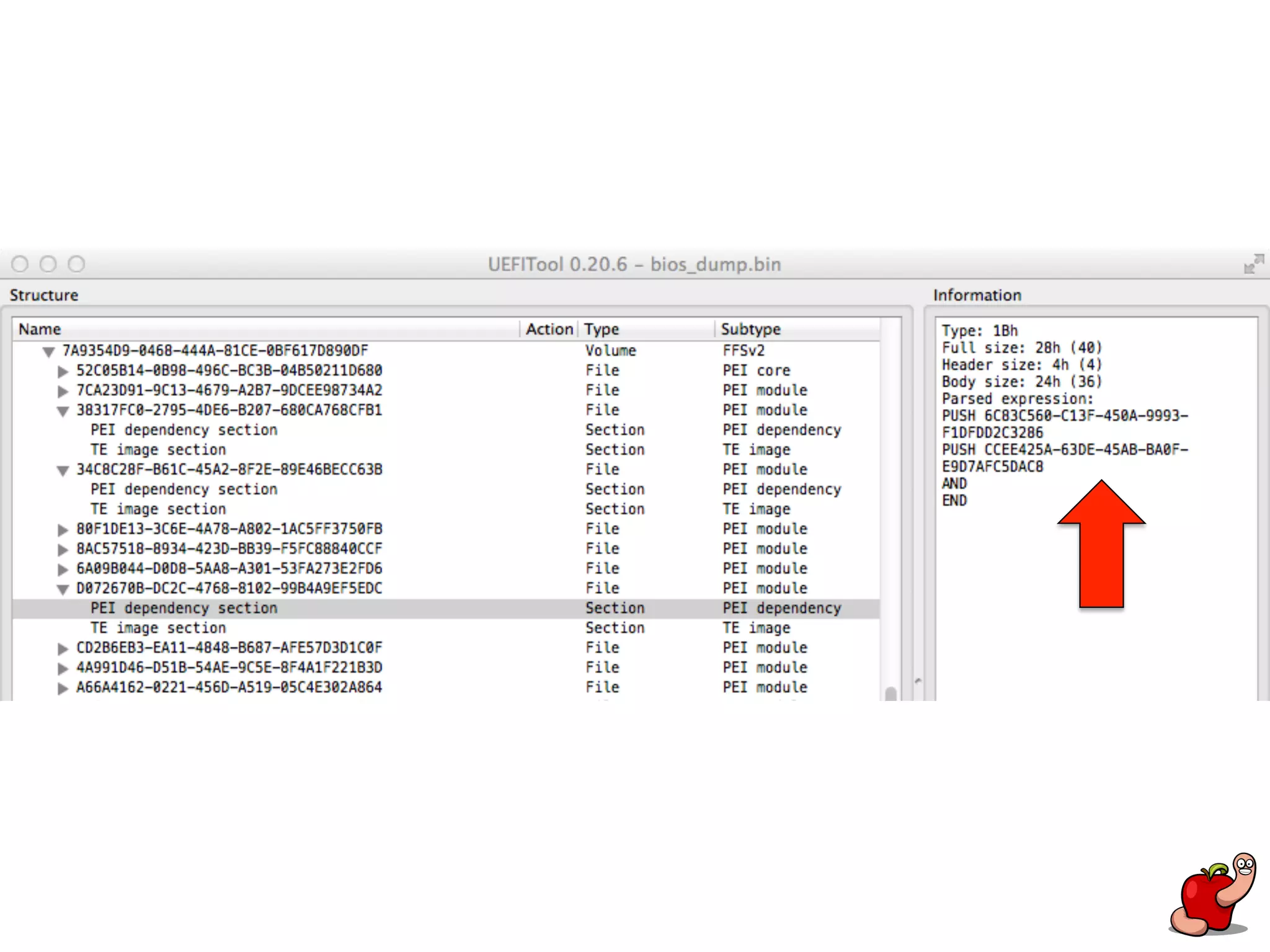
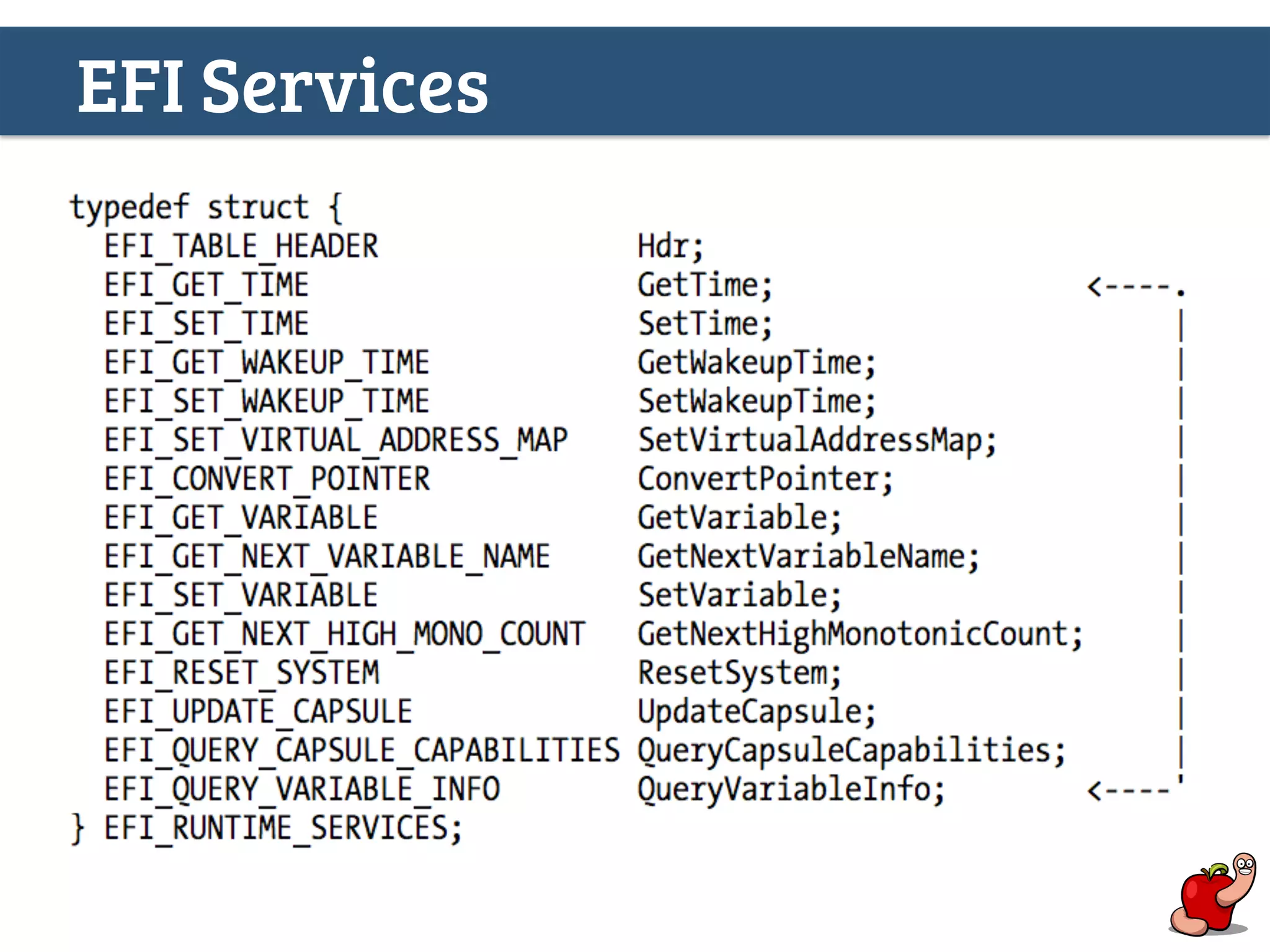
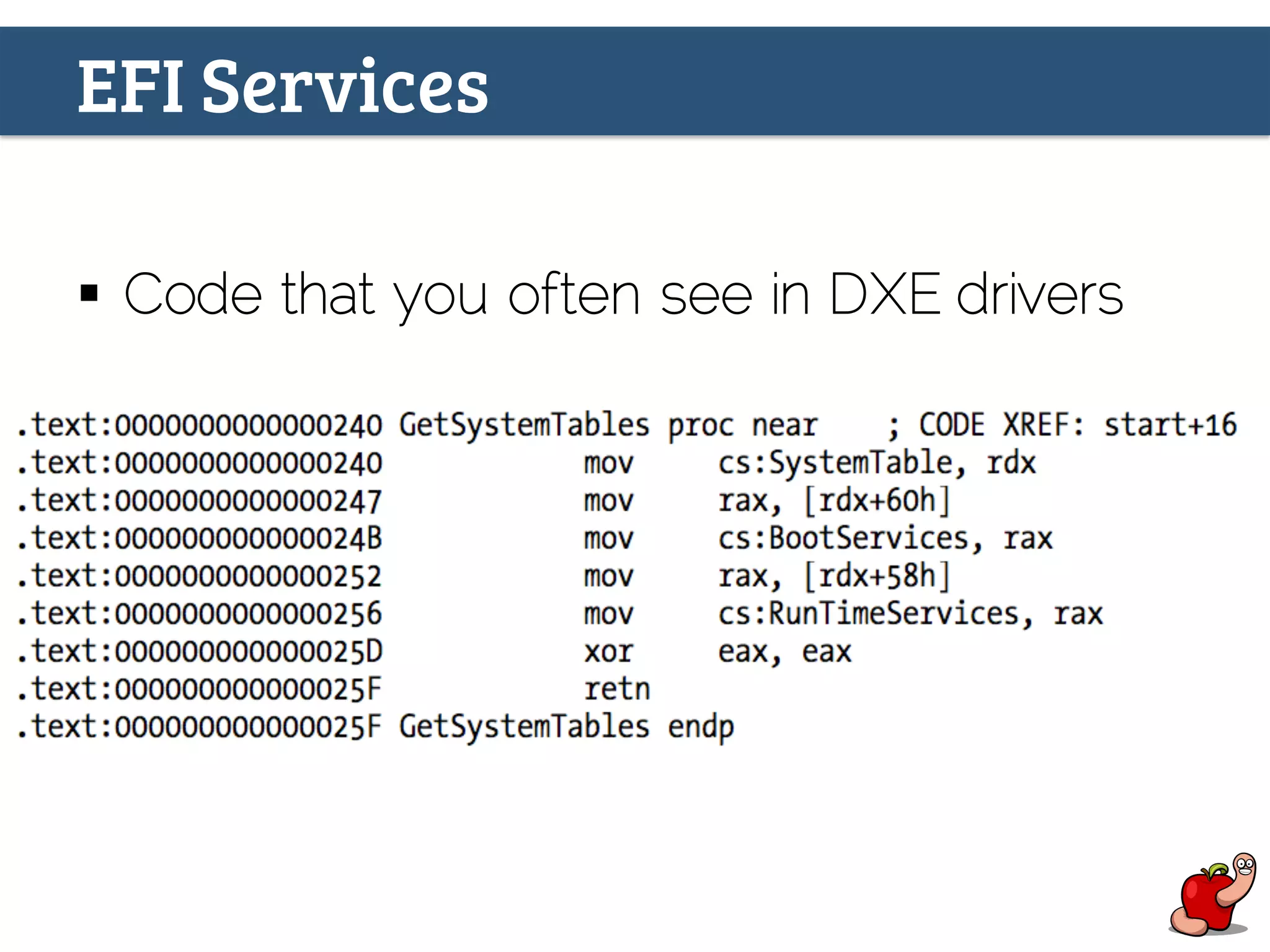
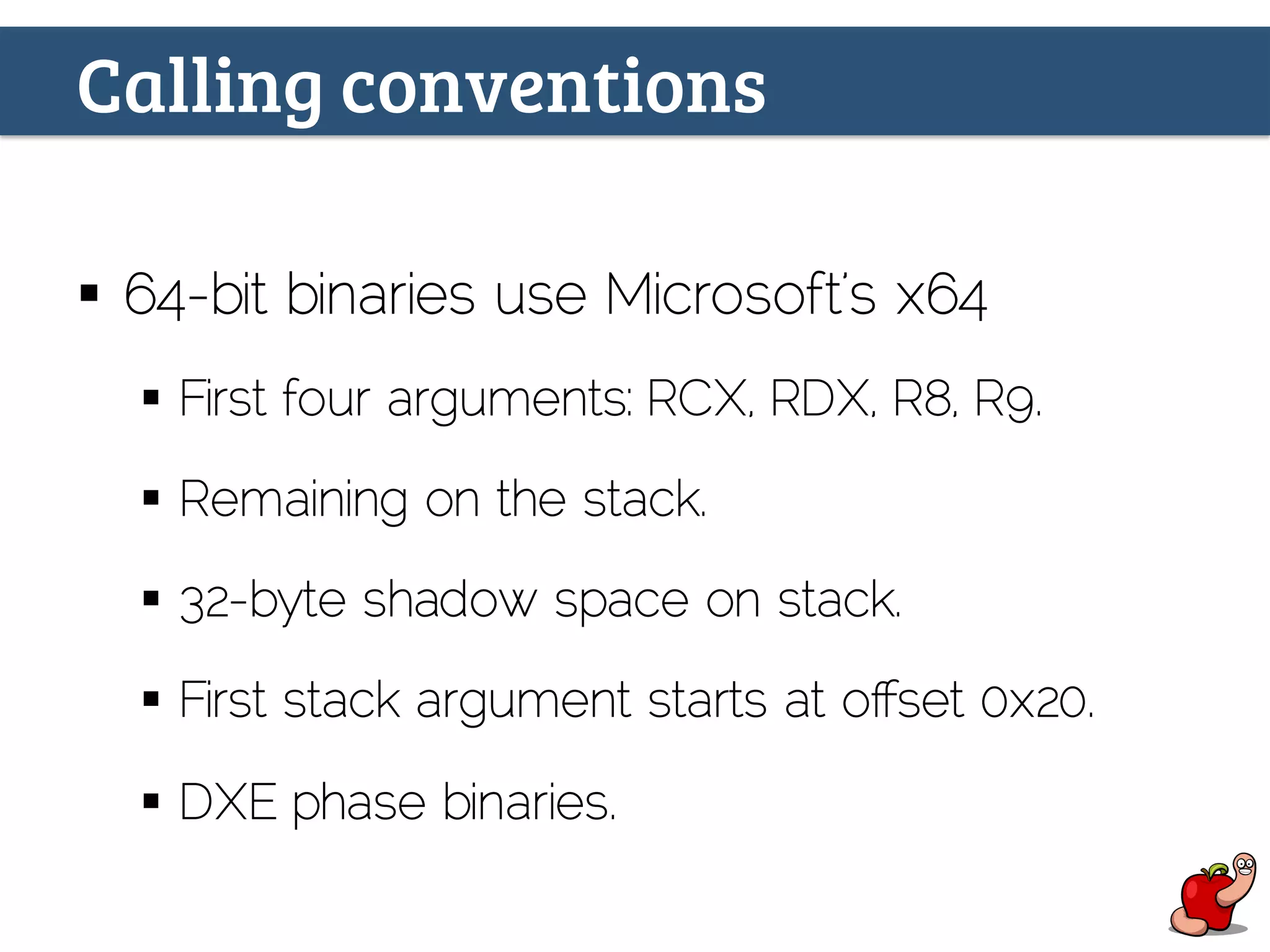
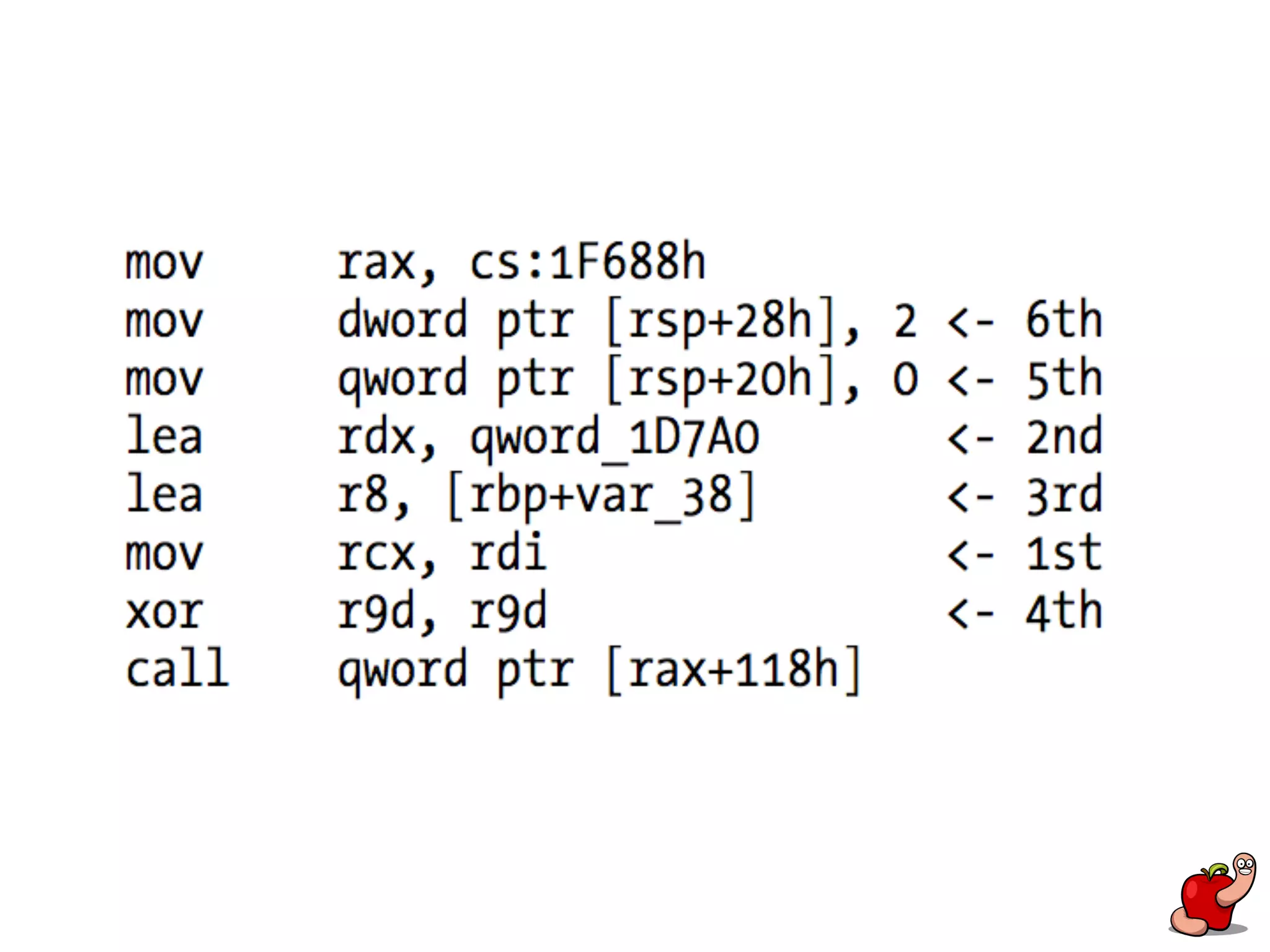
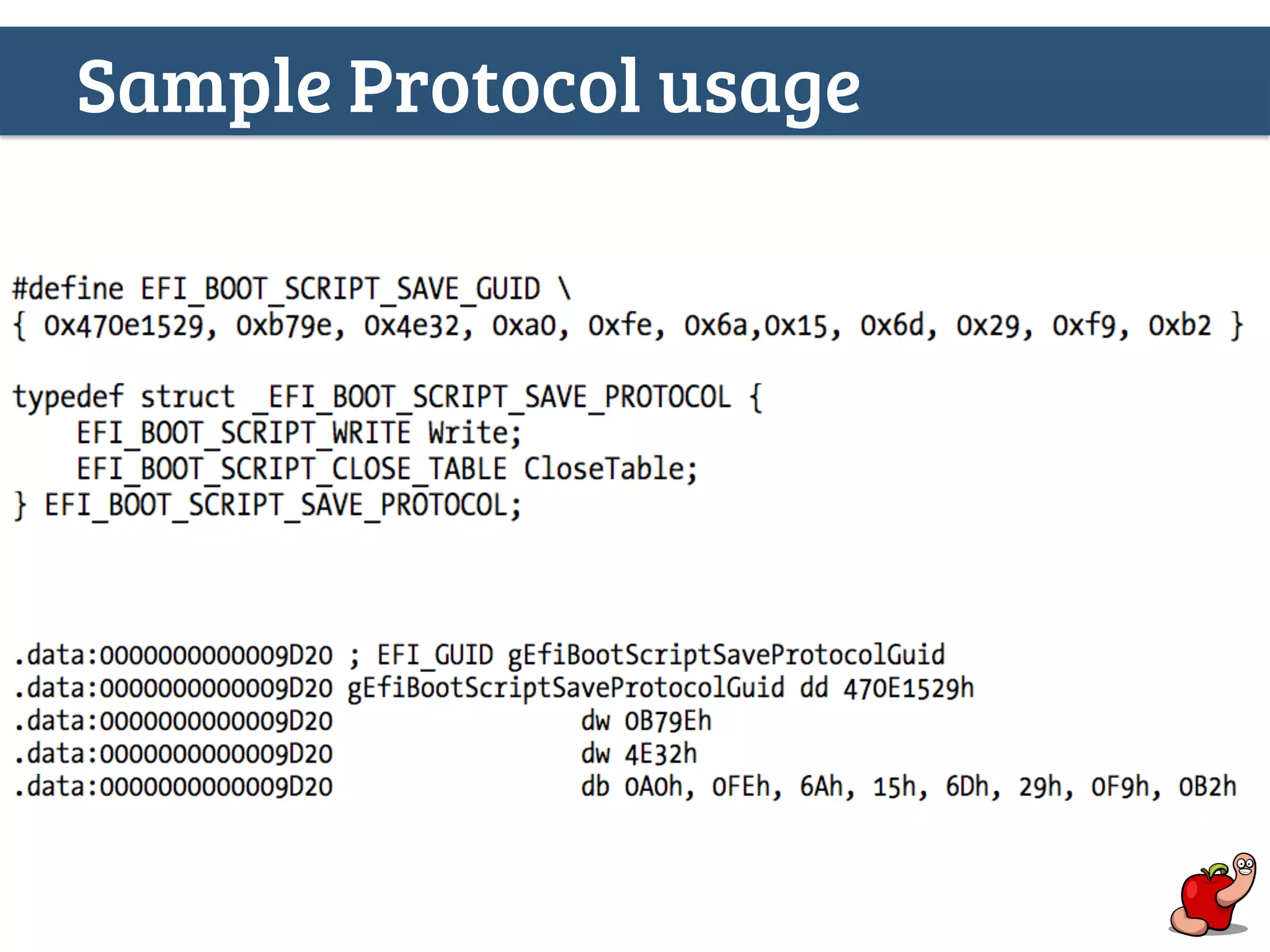
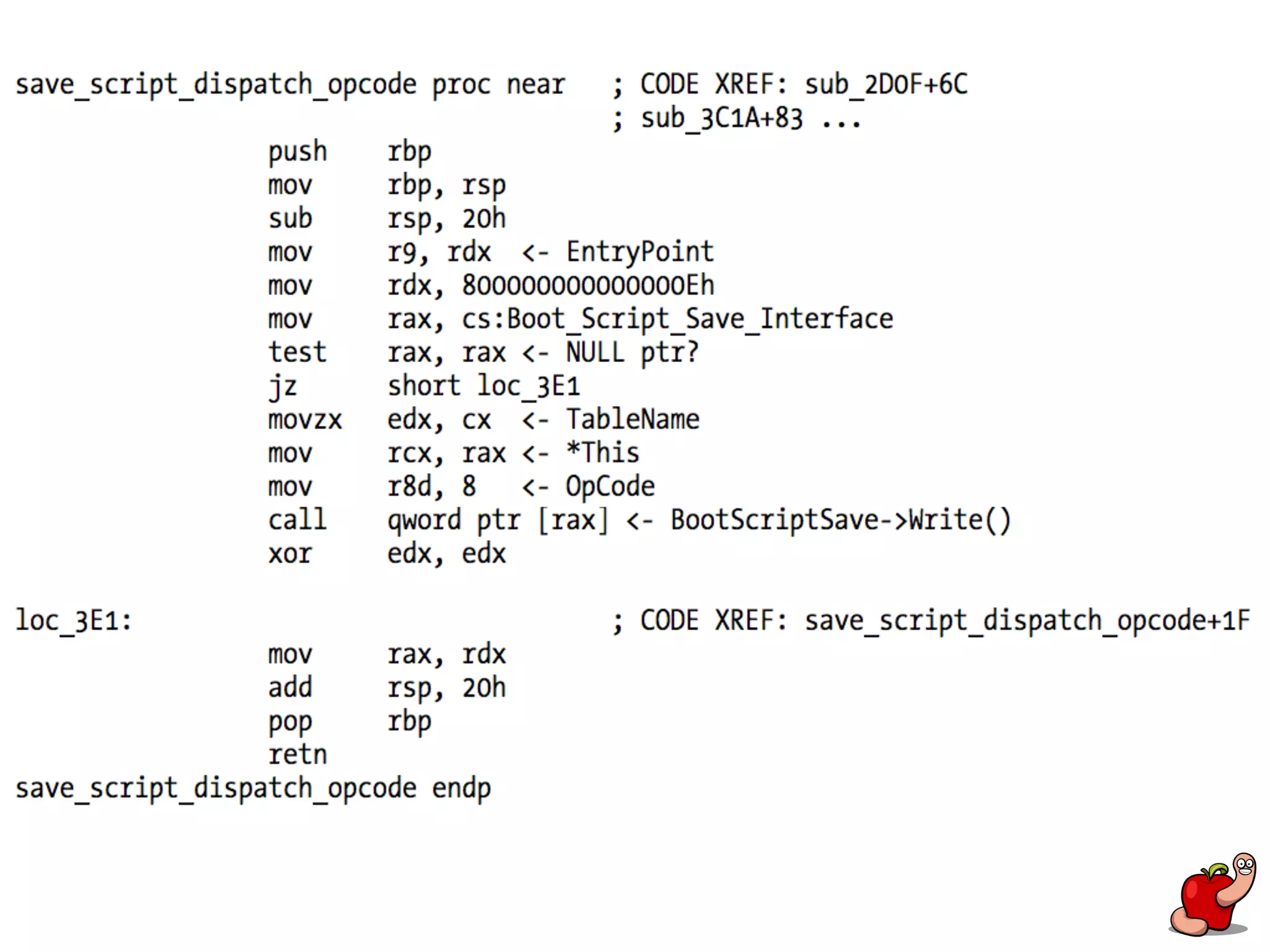
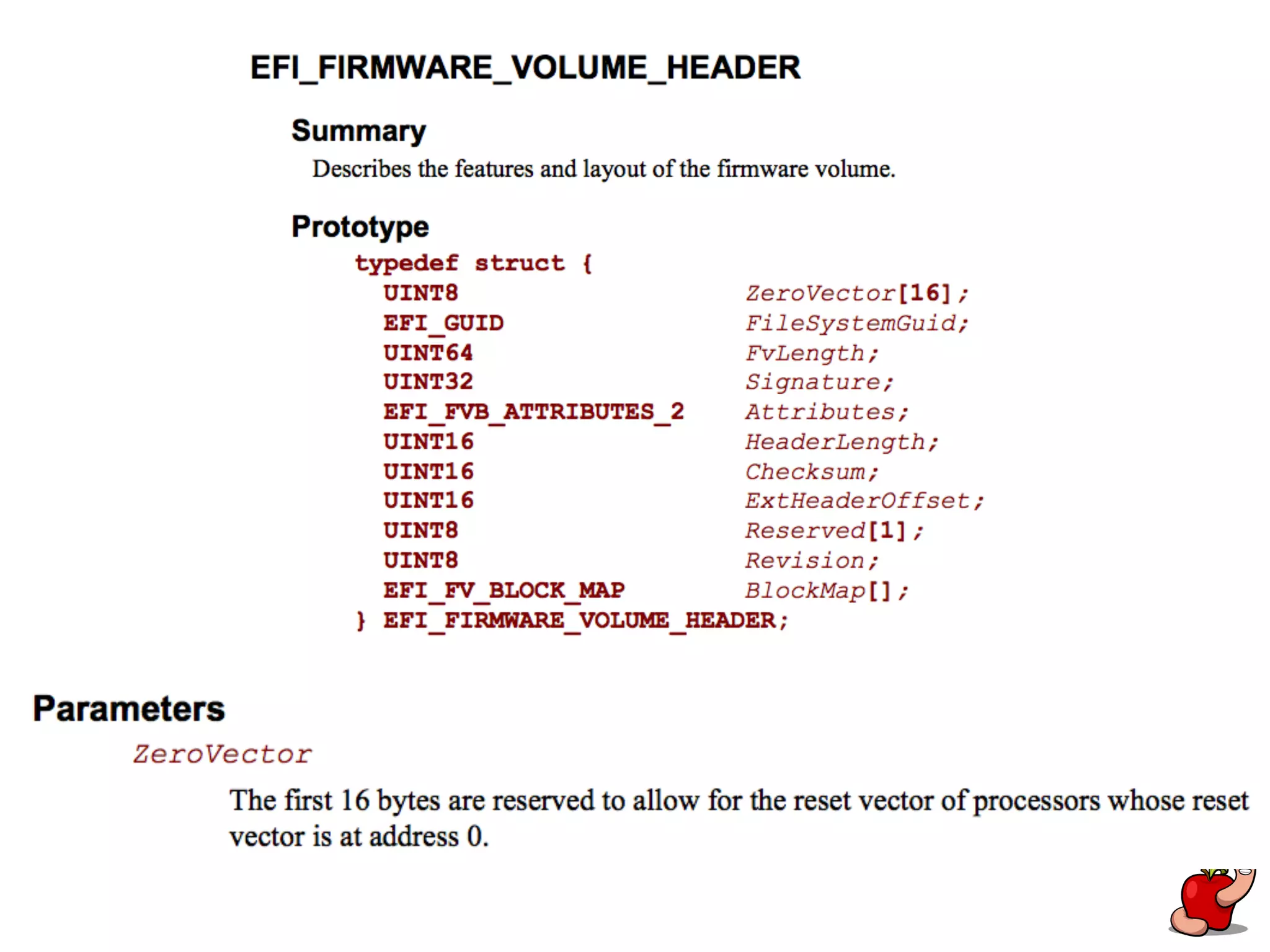
(U)EFI rootkits pose significant threats to Apple devices, particularly through vulnerabilities in the EFI firmware that can allow for undetectable malicious software. The document details methods for reverse engineering and identifying EFI malware, alongside examples of attacks and necessary tools for analyzing EFI binaries. Notably, the text emphasizes the risks associated with firmware vulnerabilities and highlights ongoing research into potential exploits and defenses.