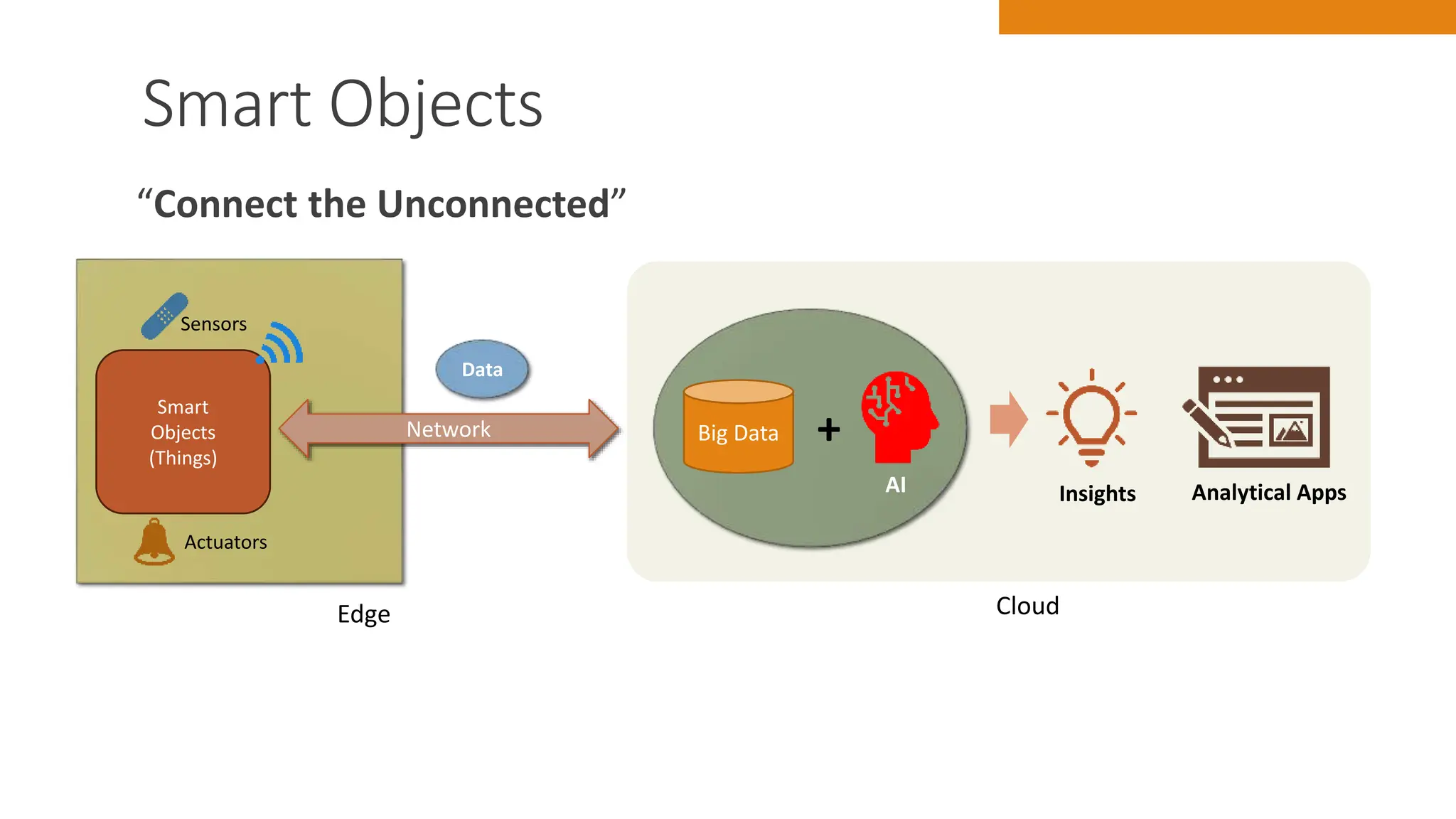
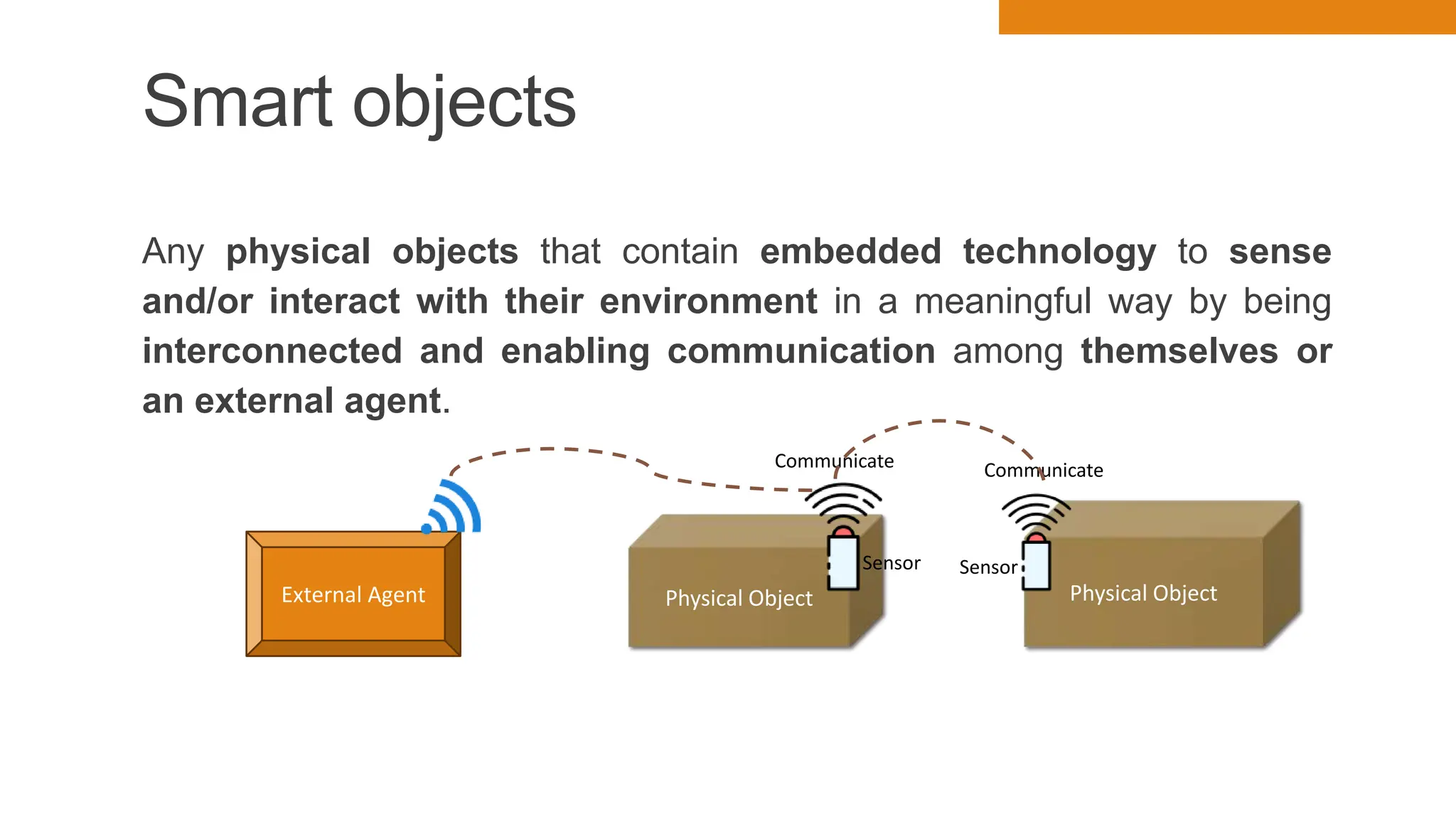
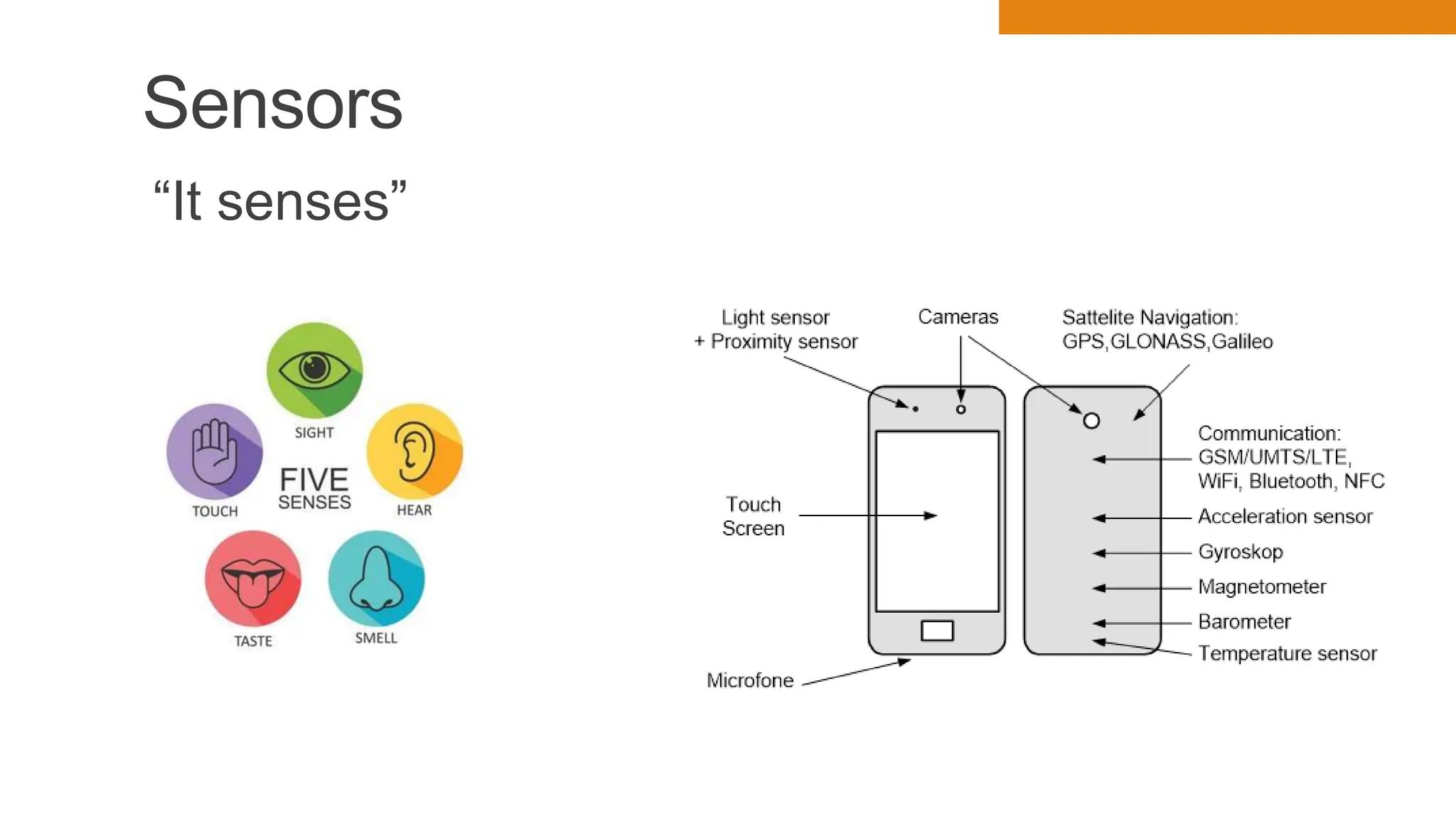
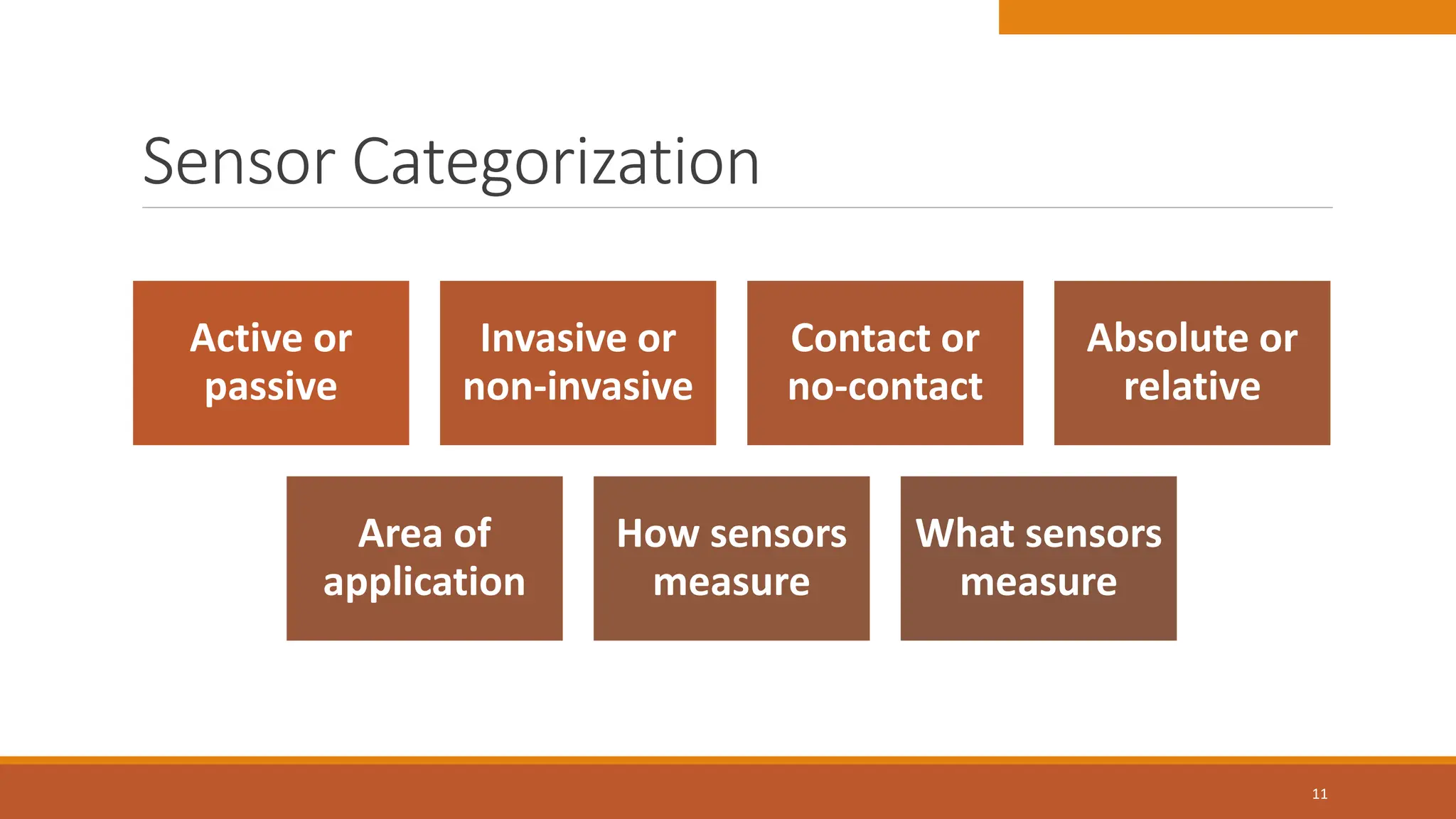
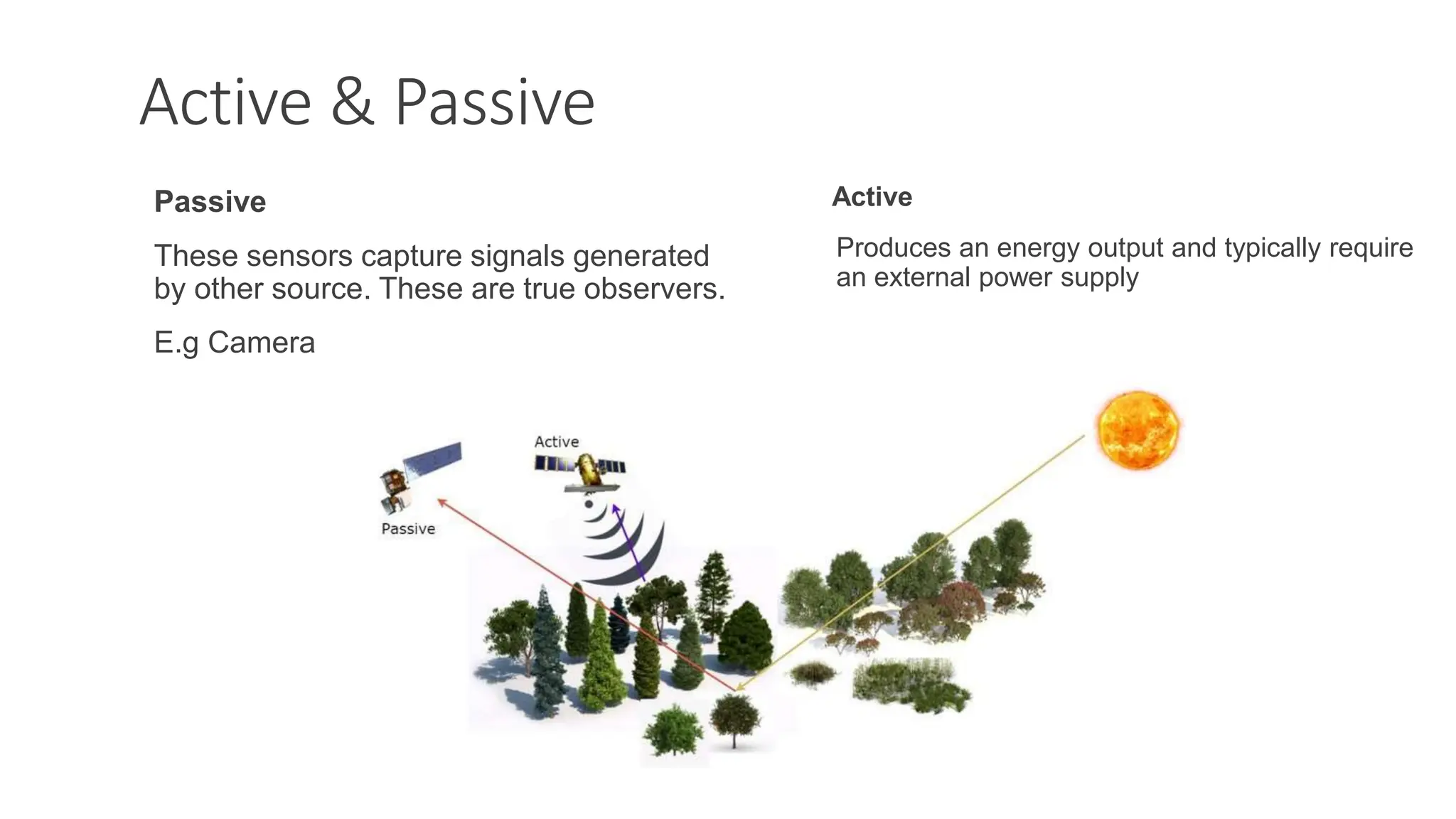
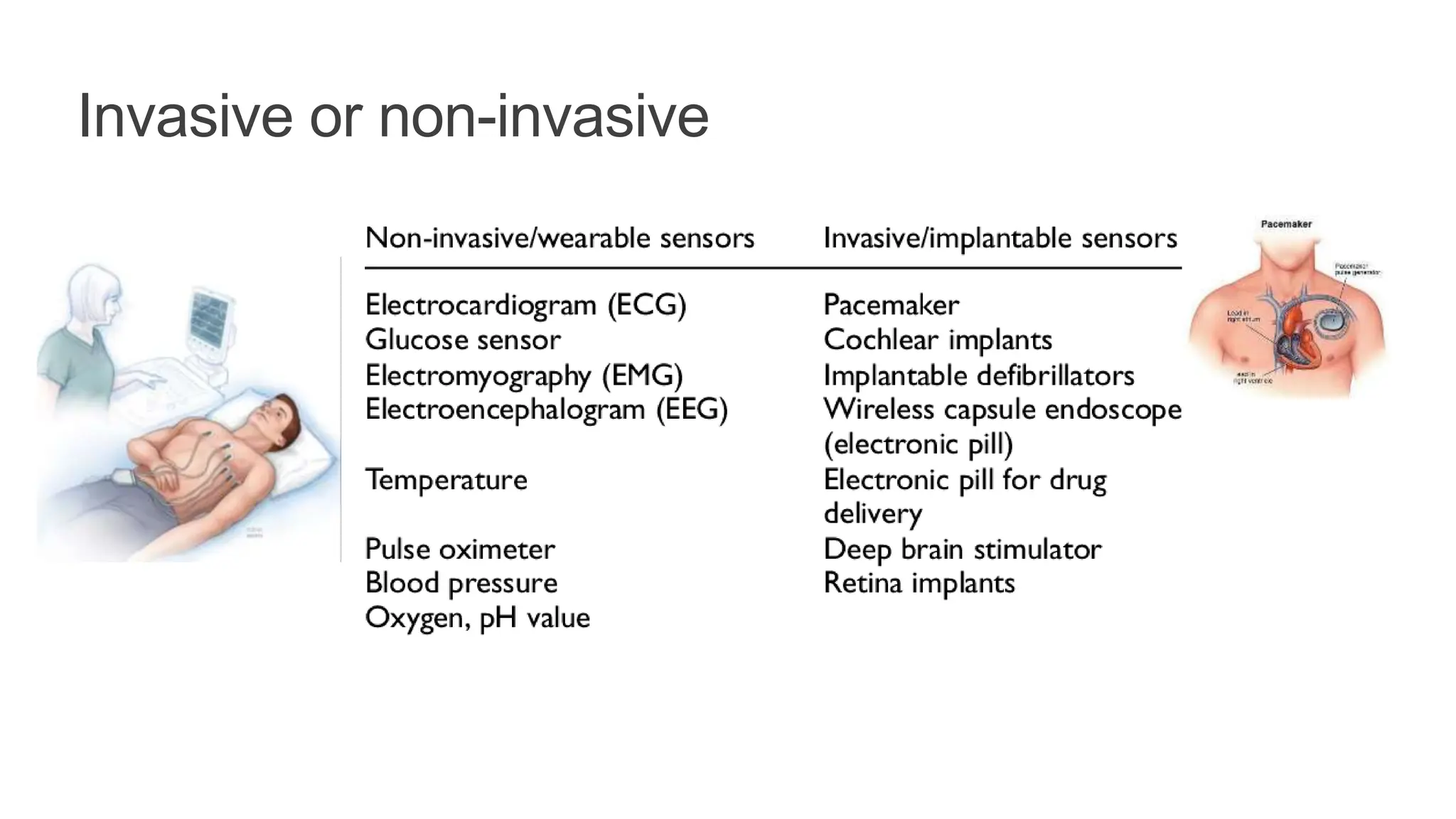
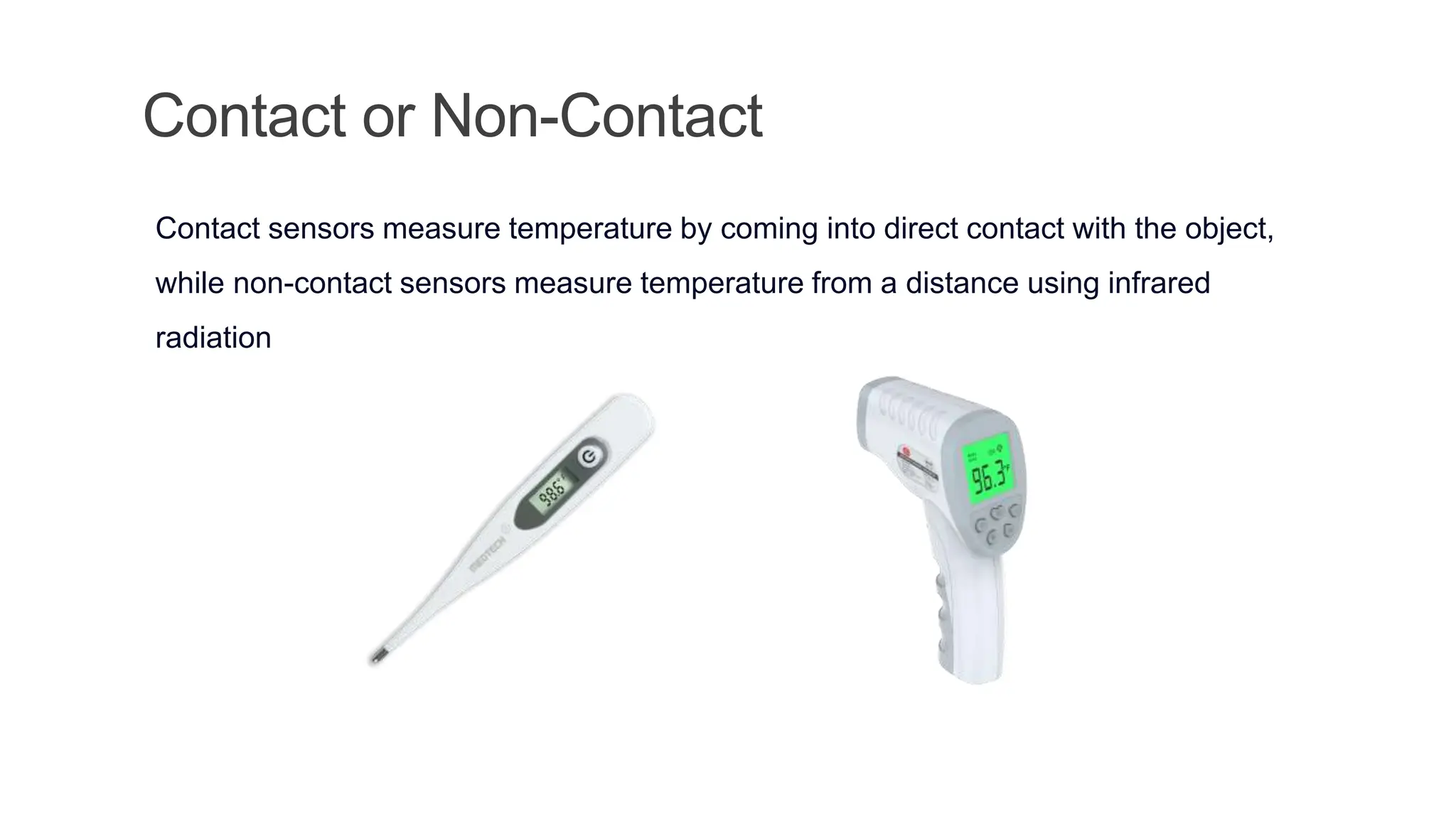
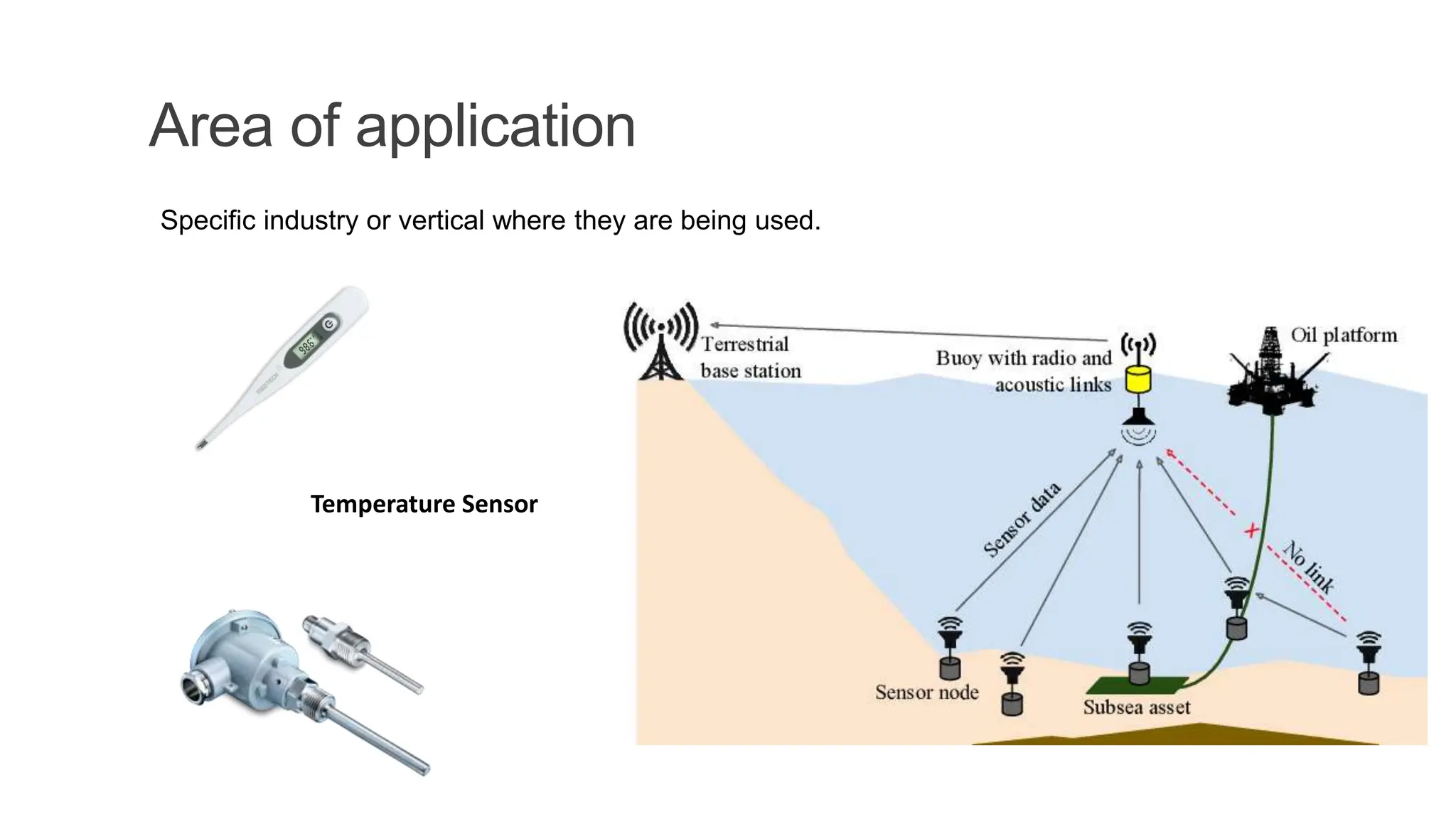
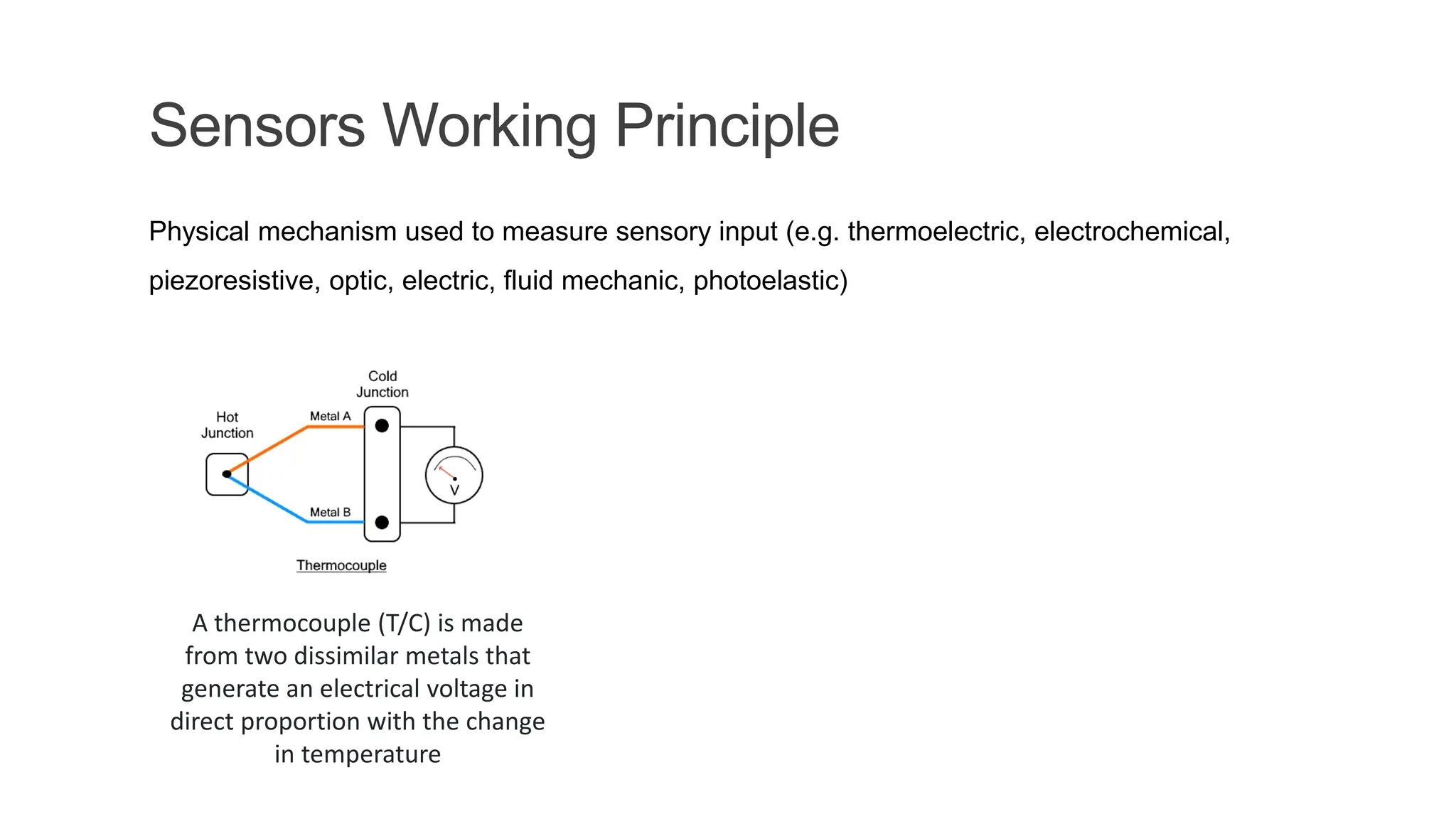
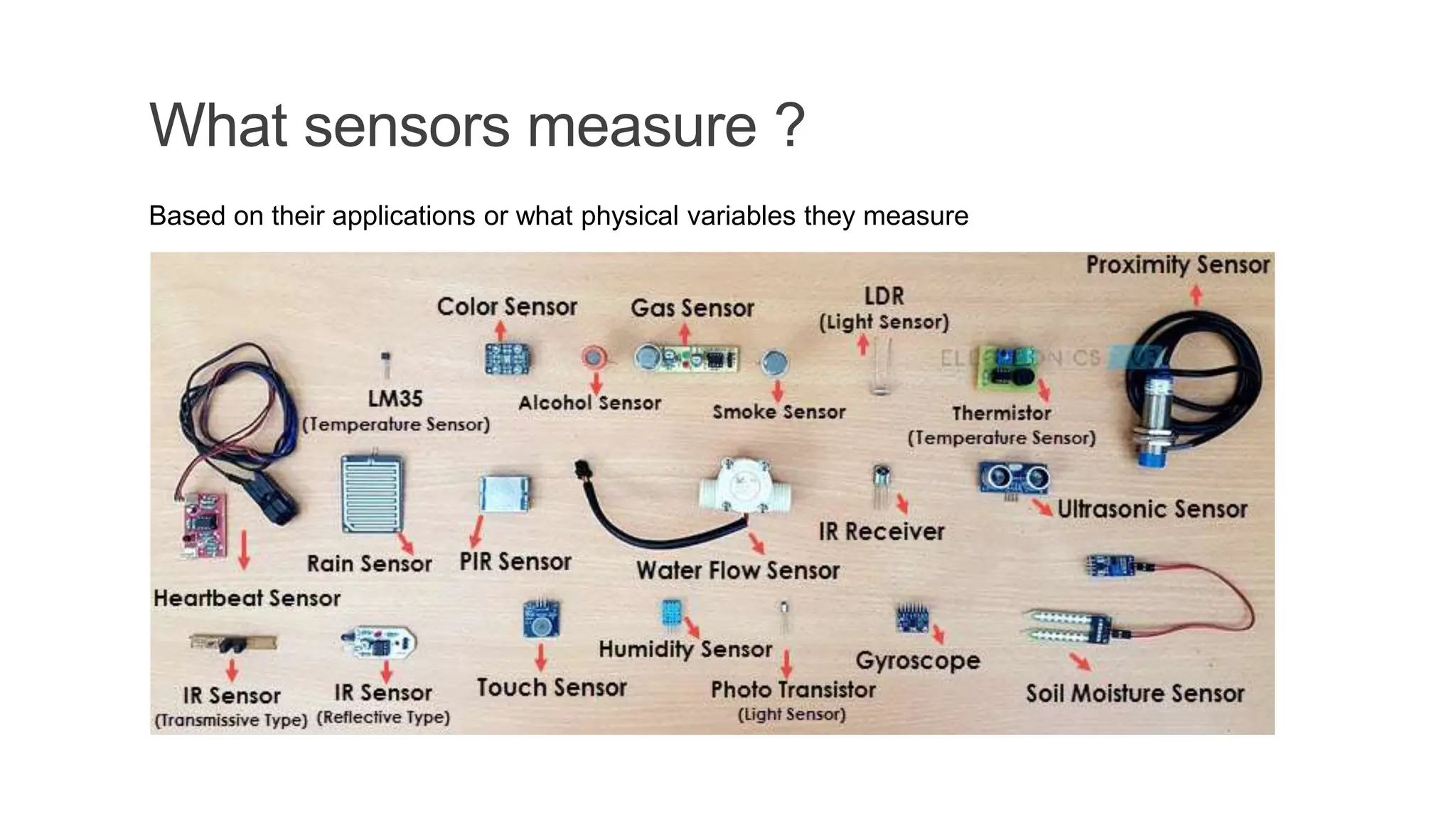
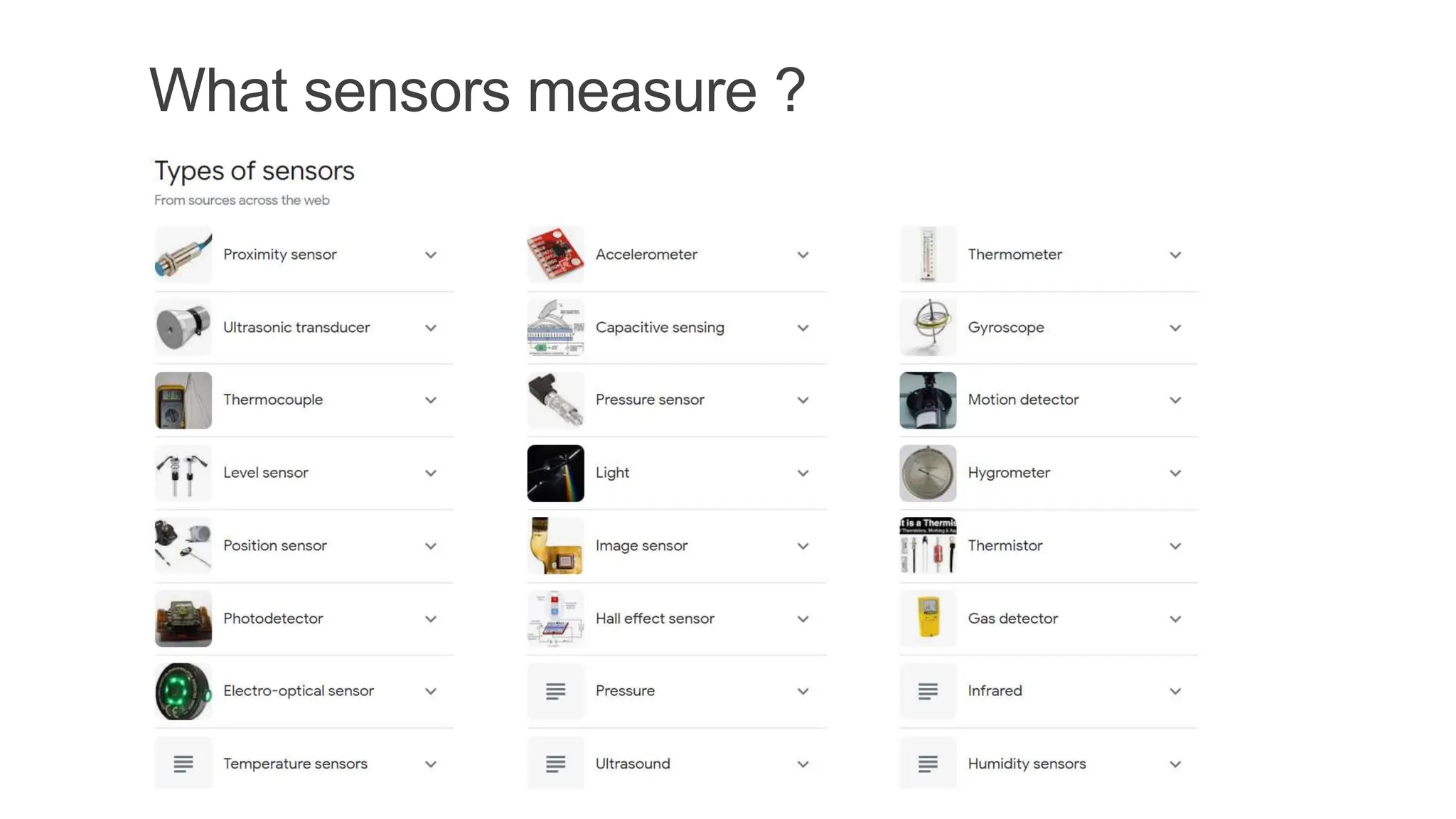
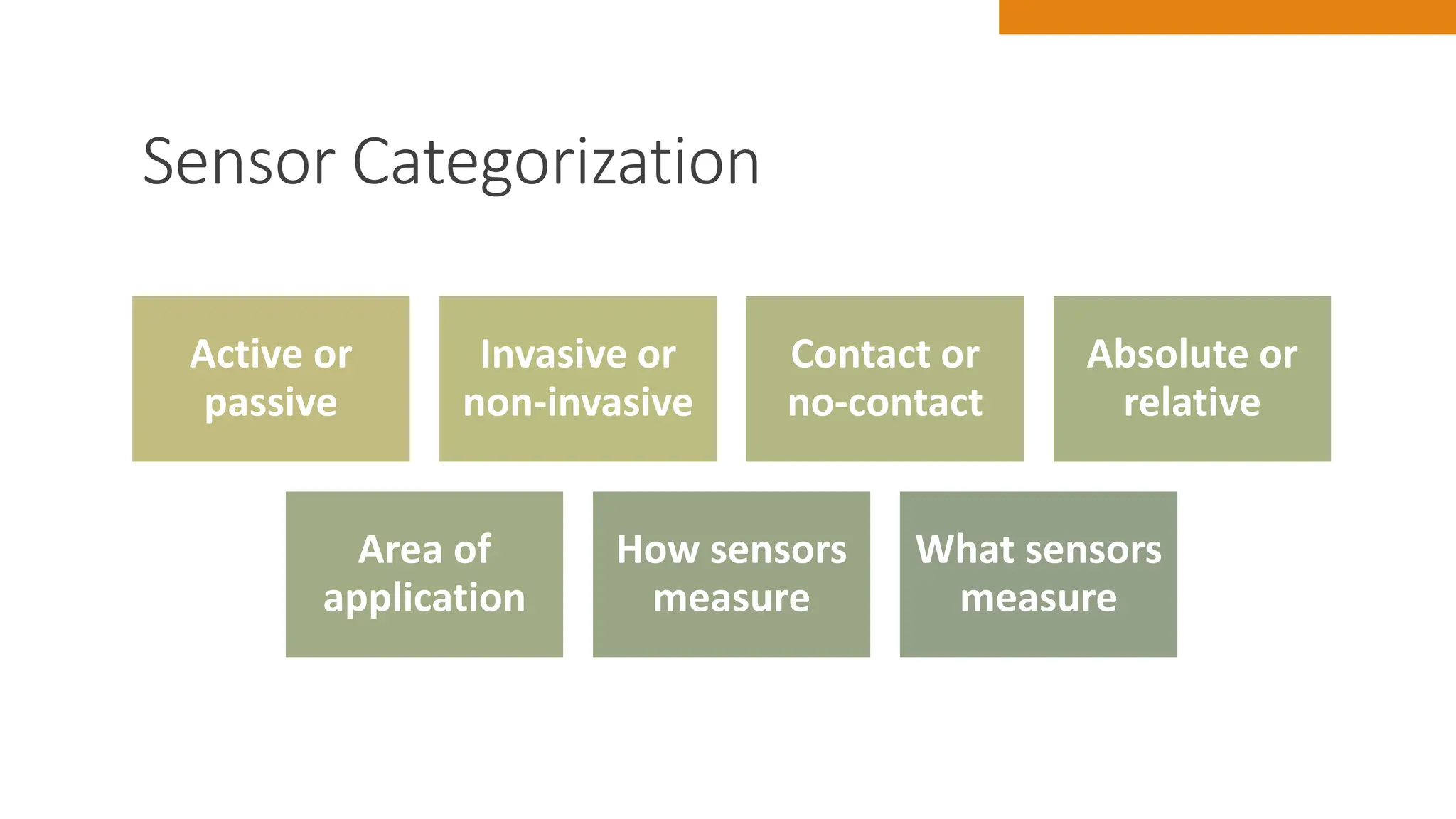
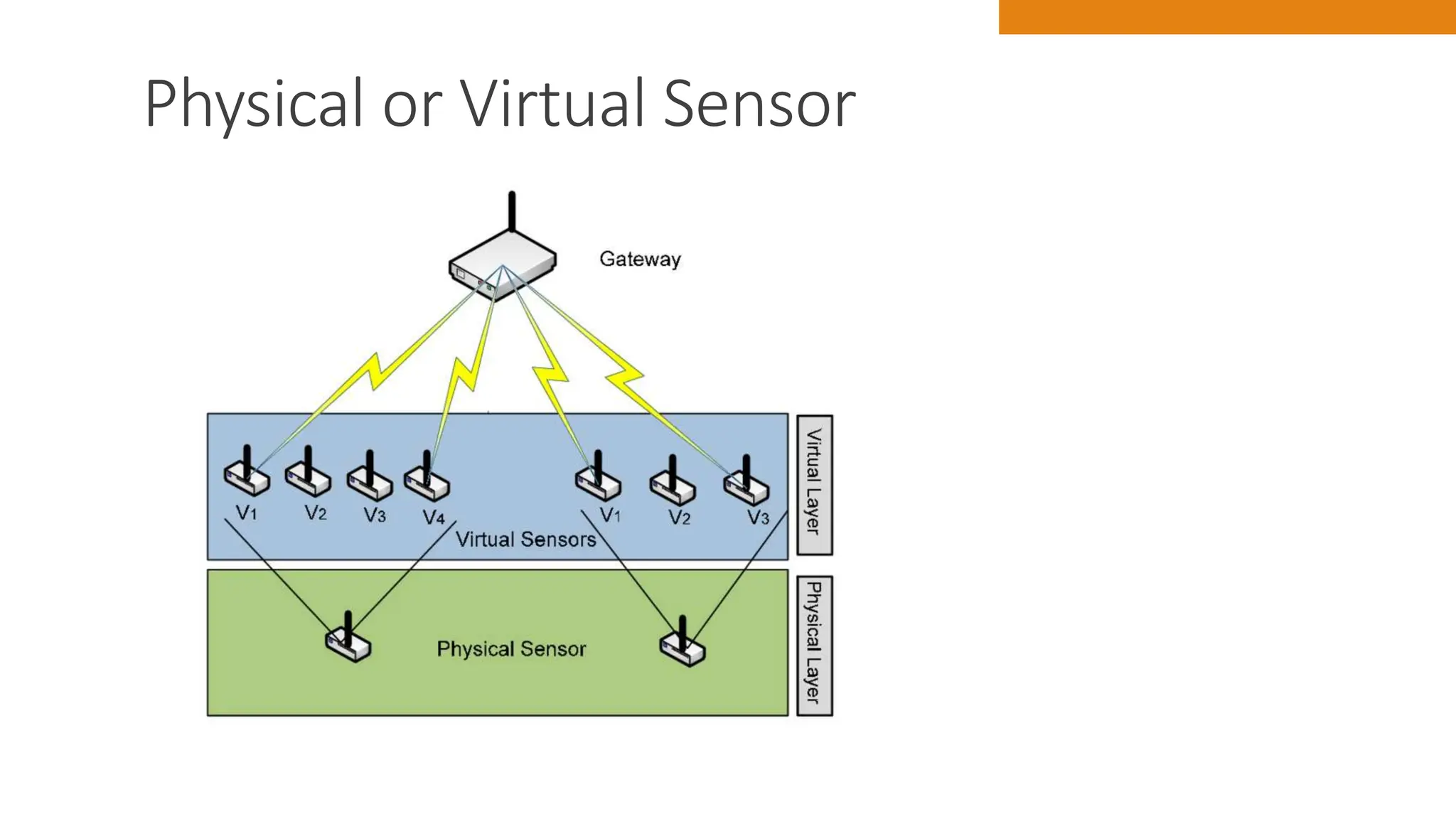
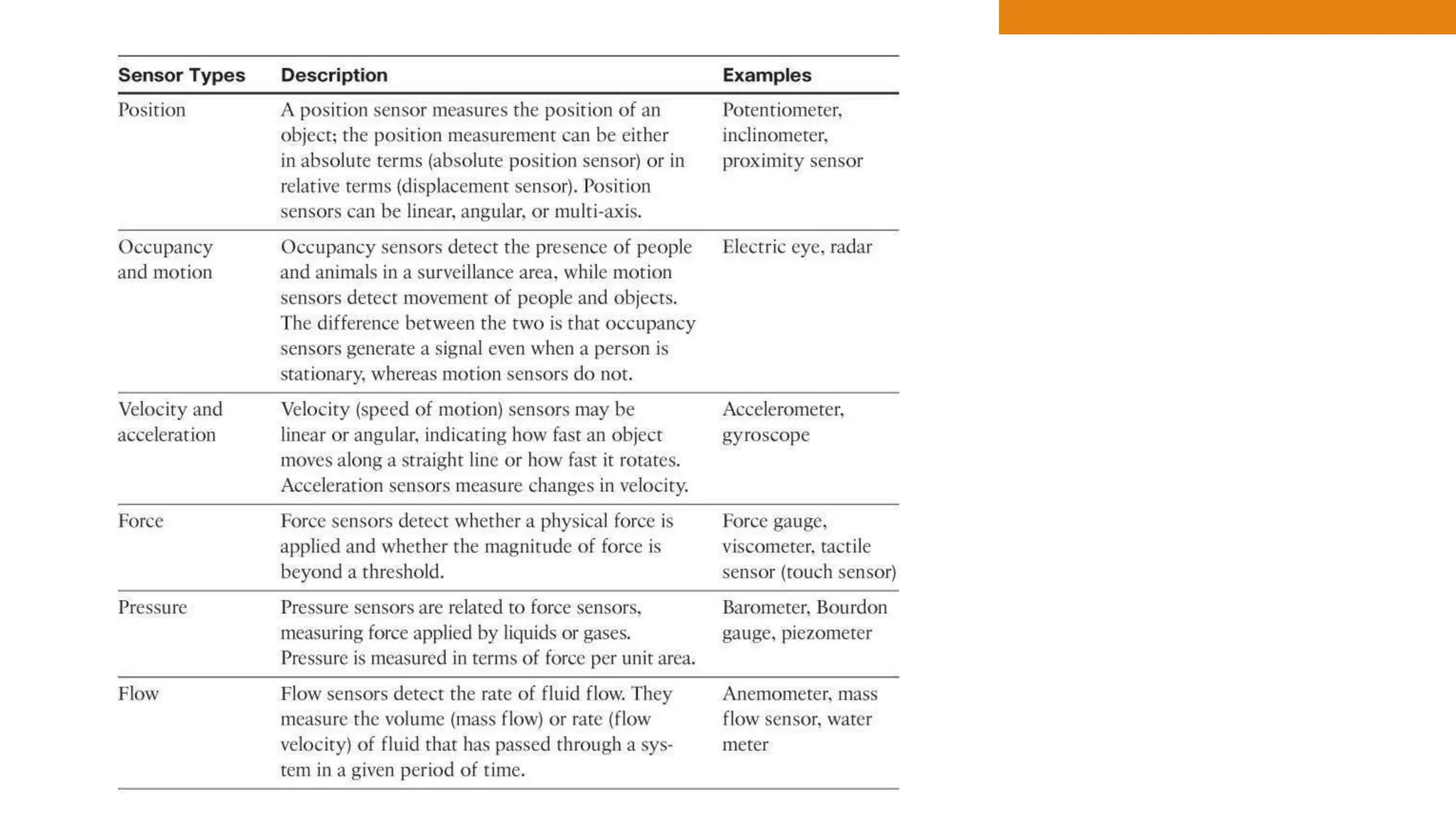
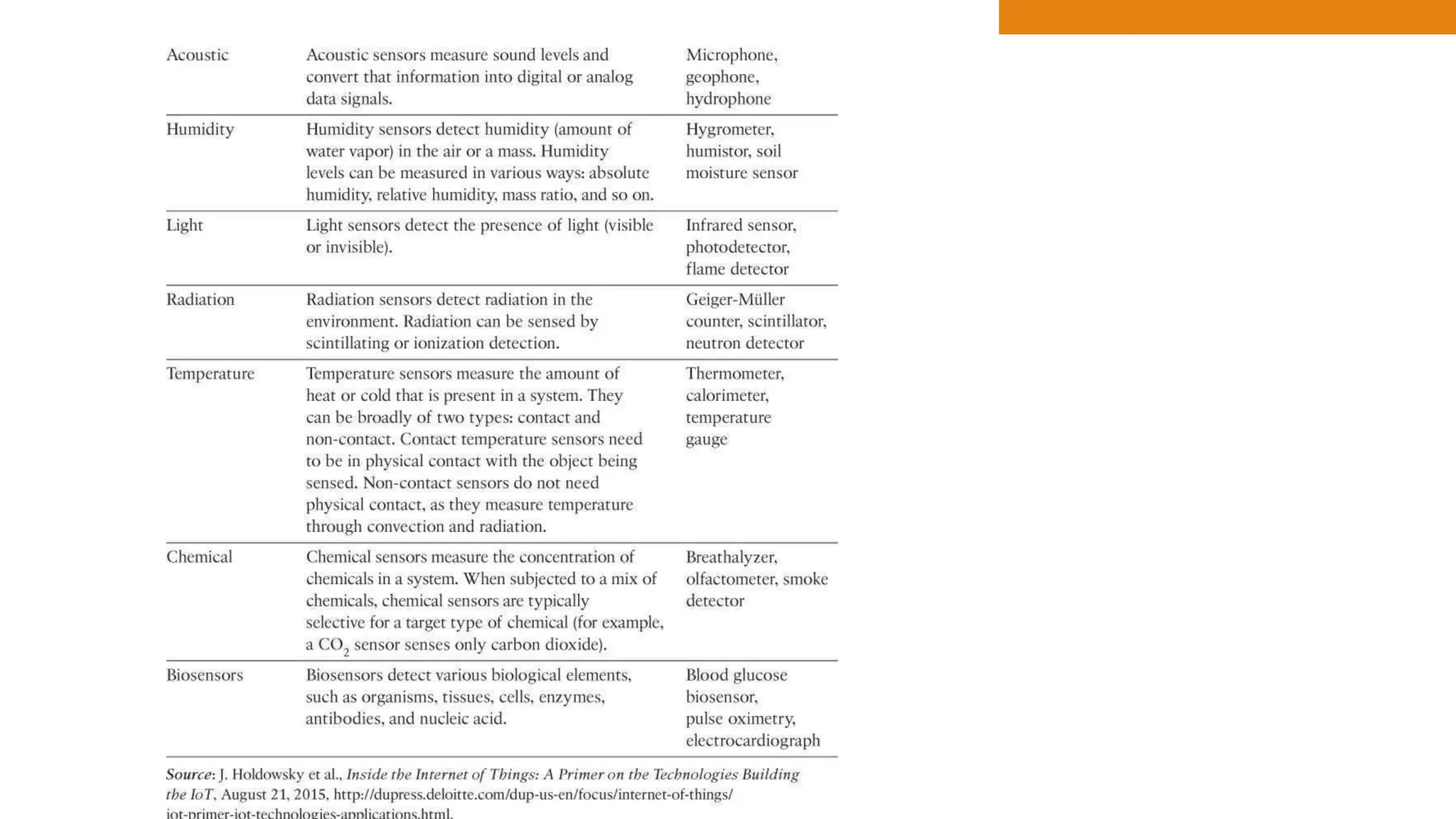
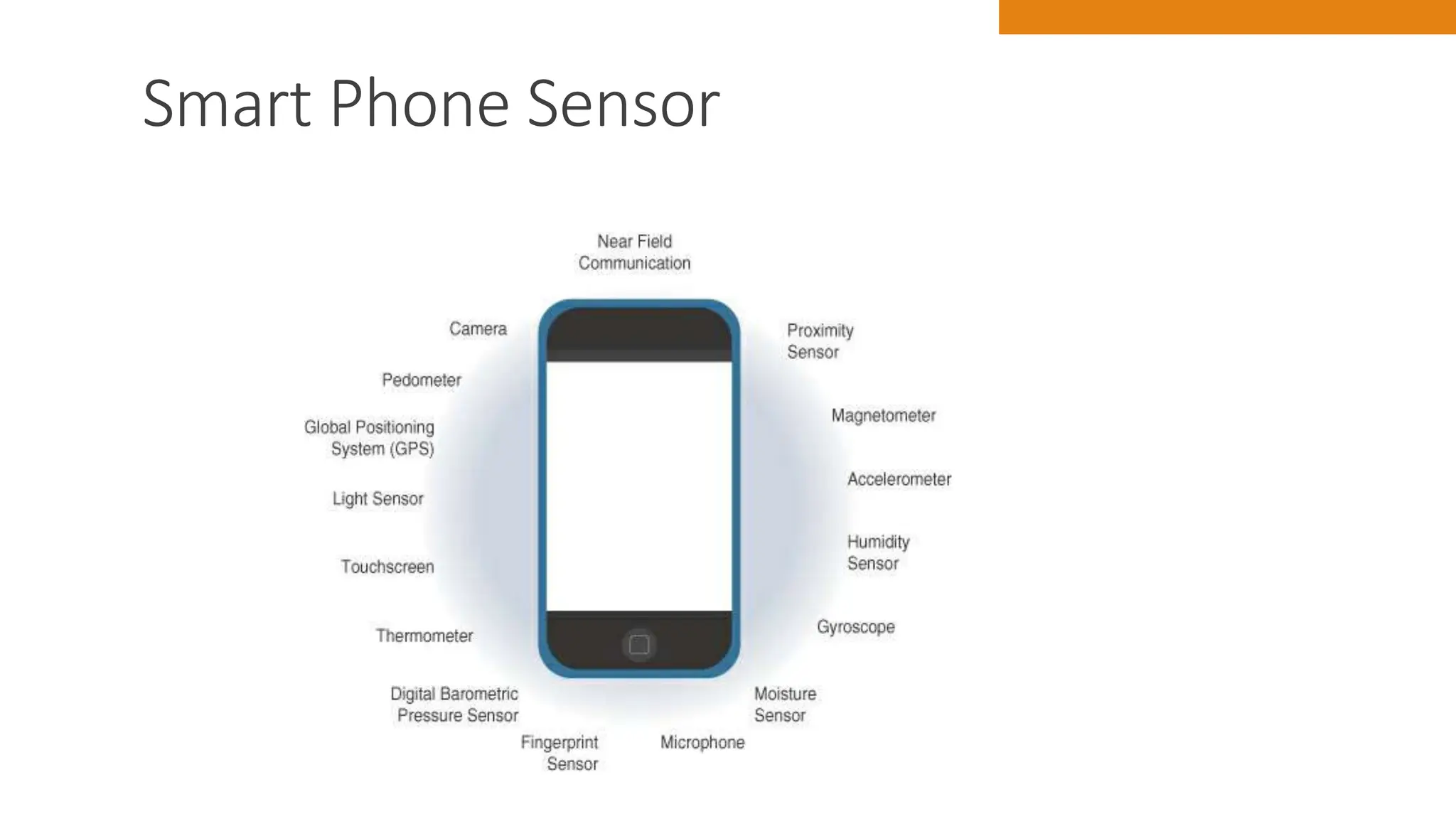
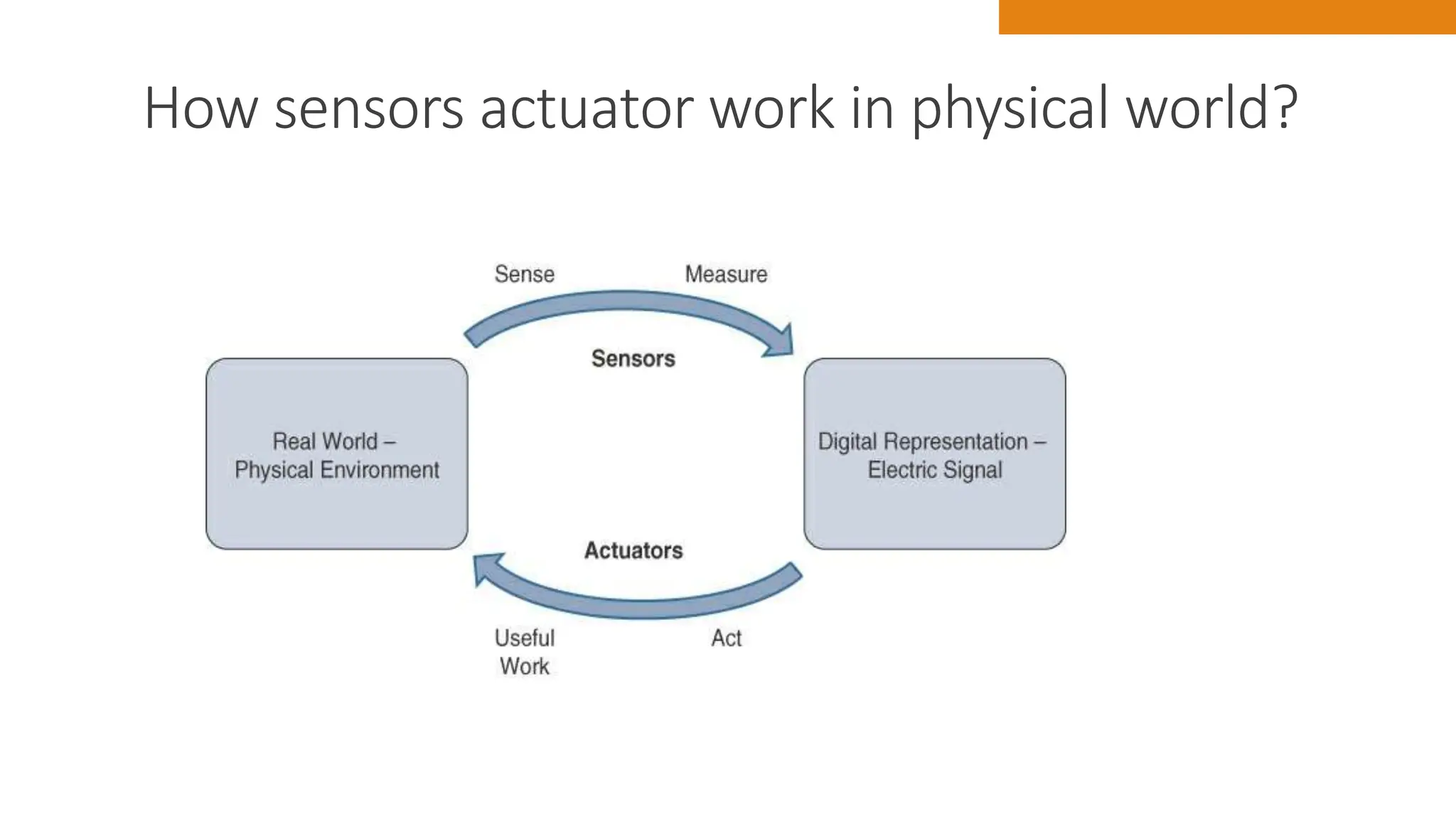
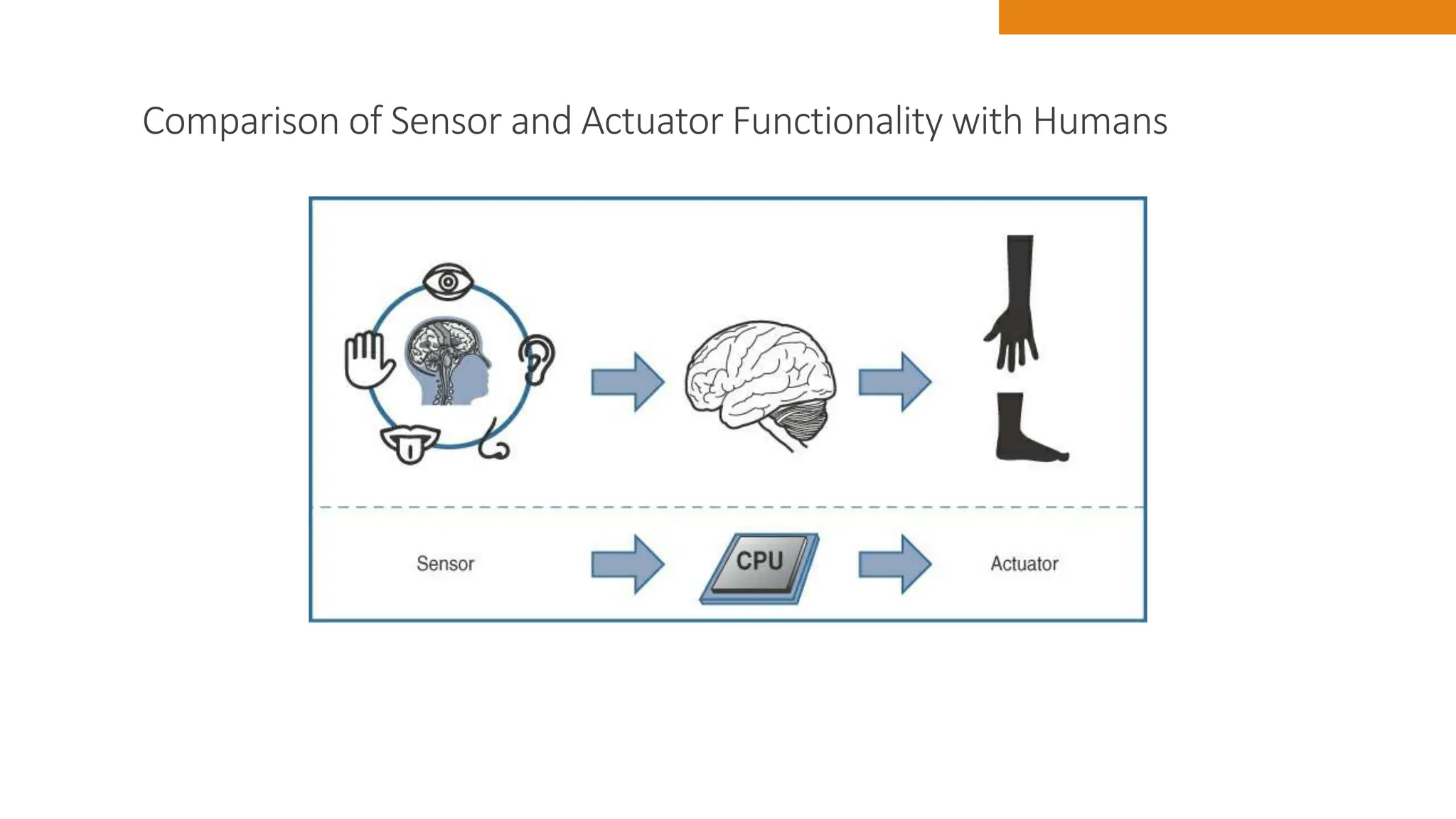
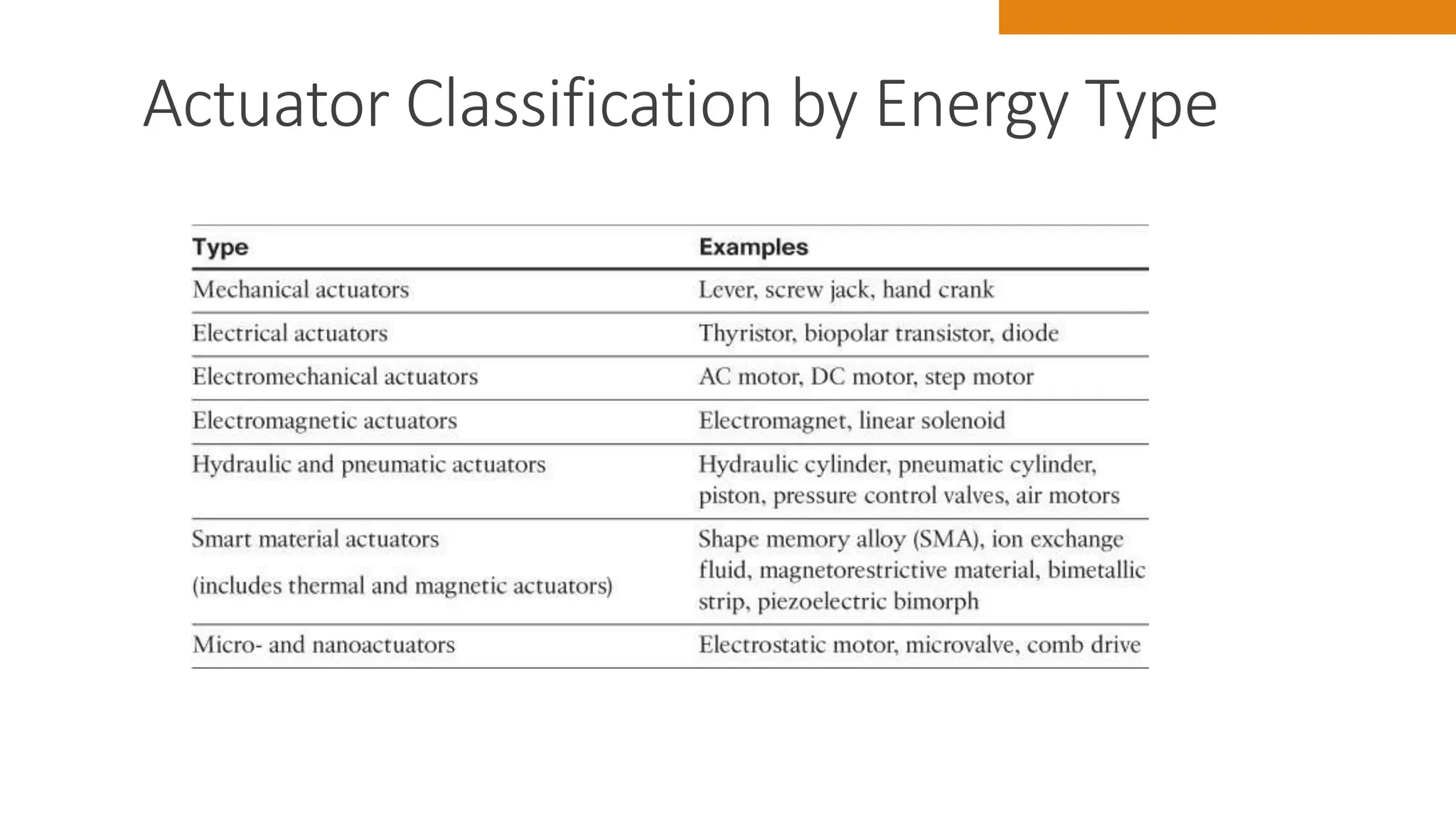
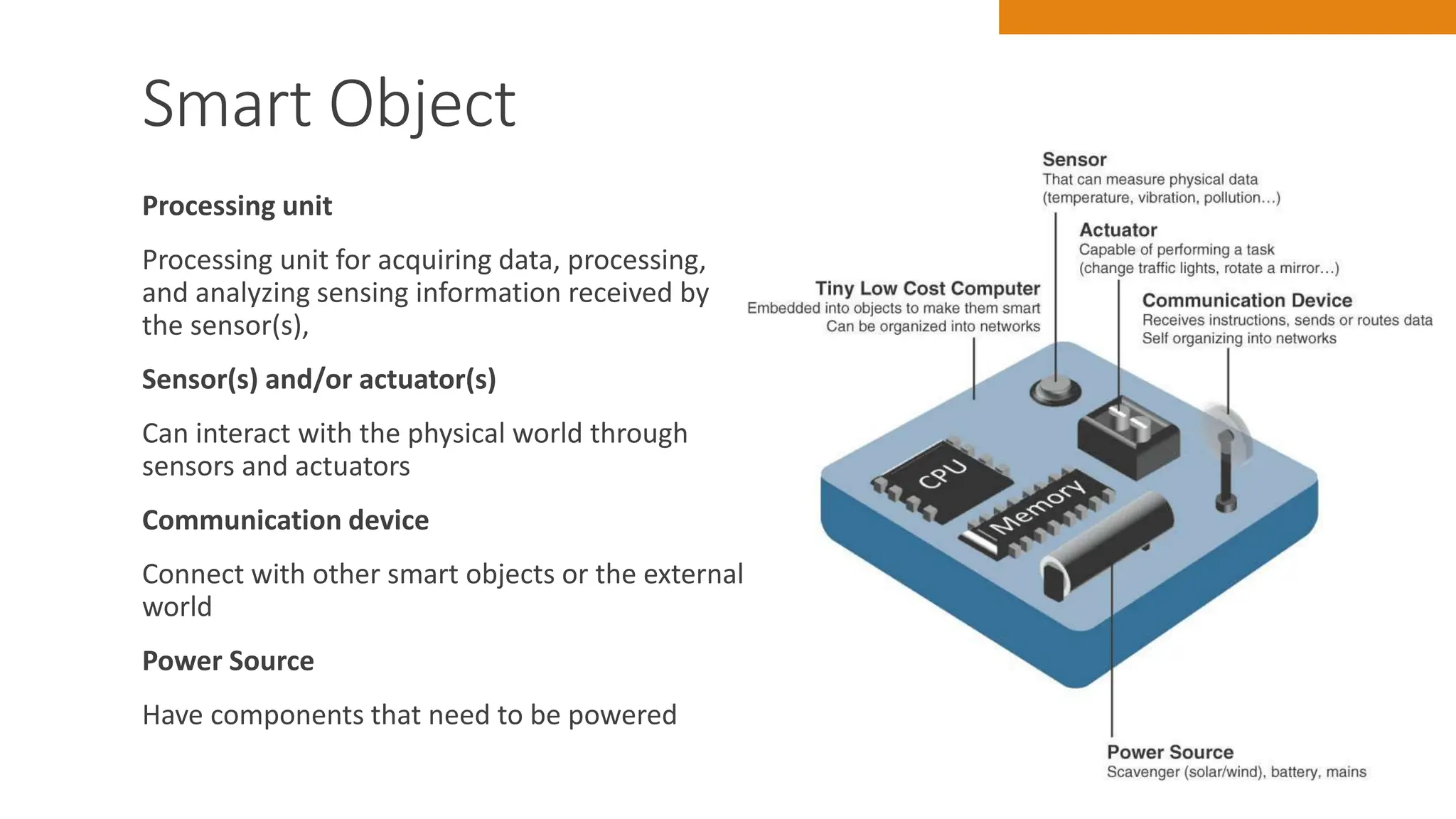
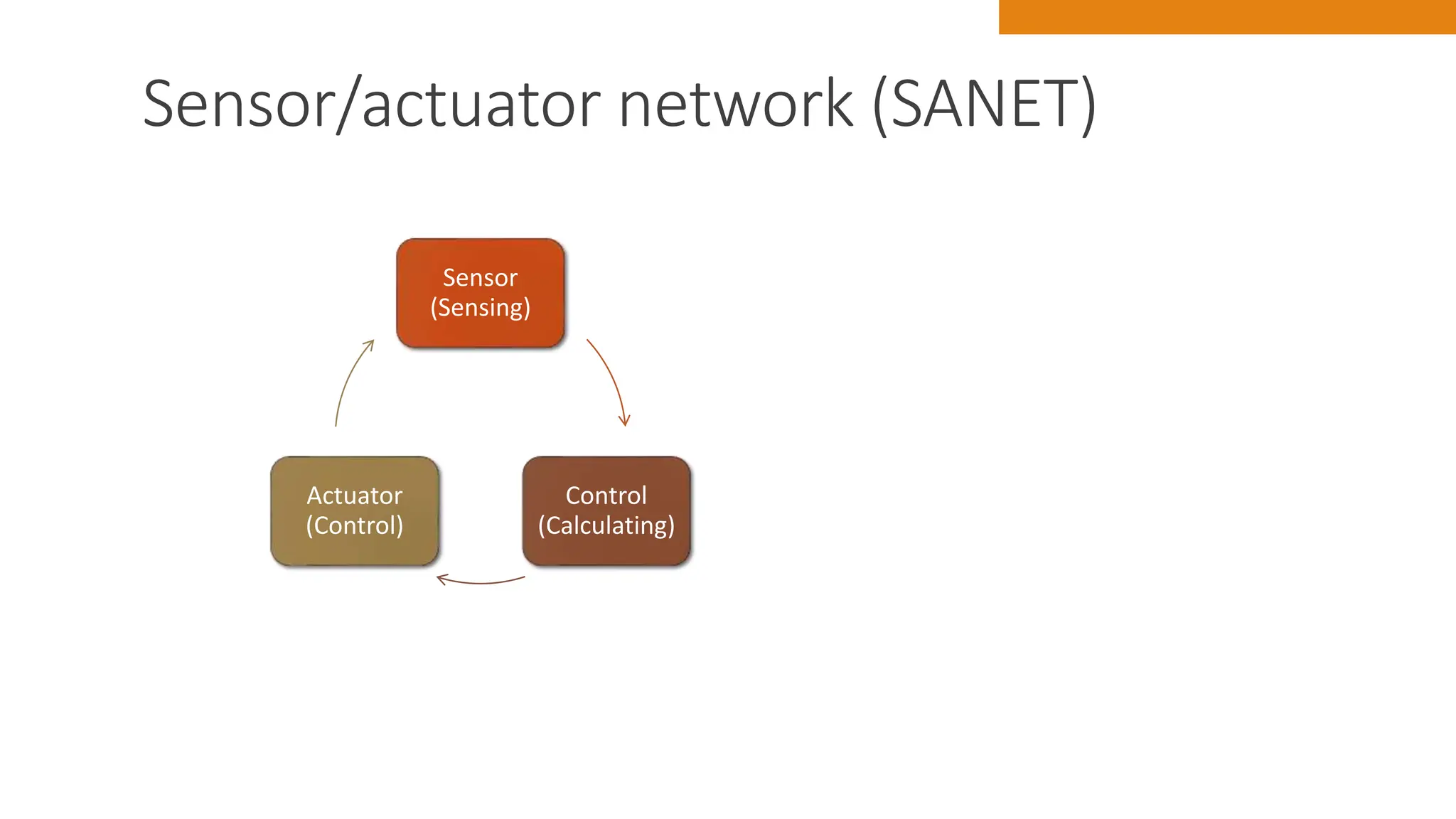
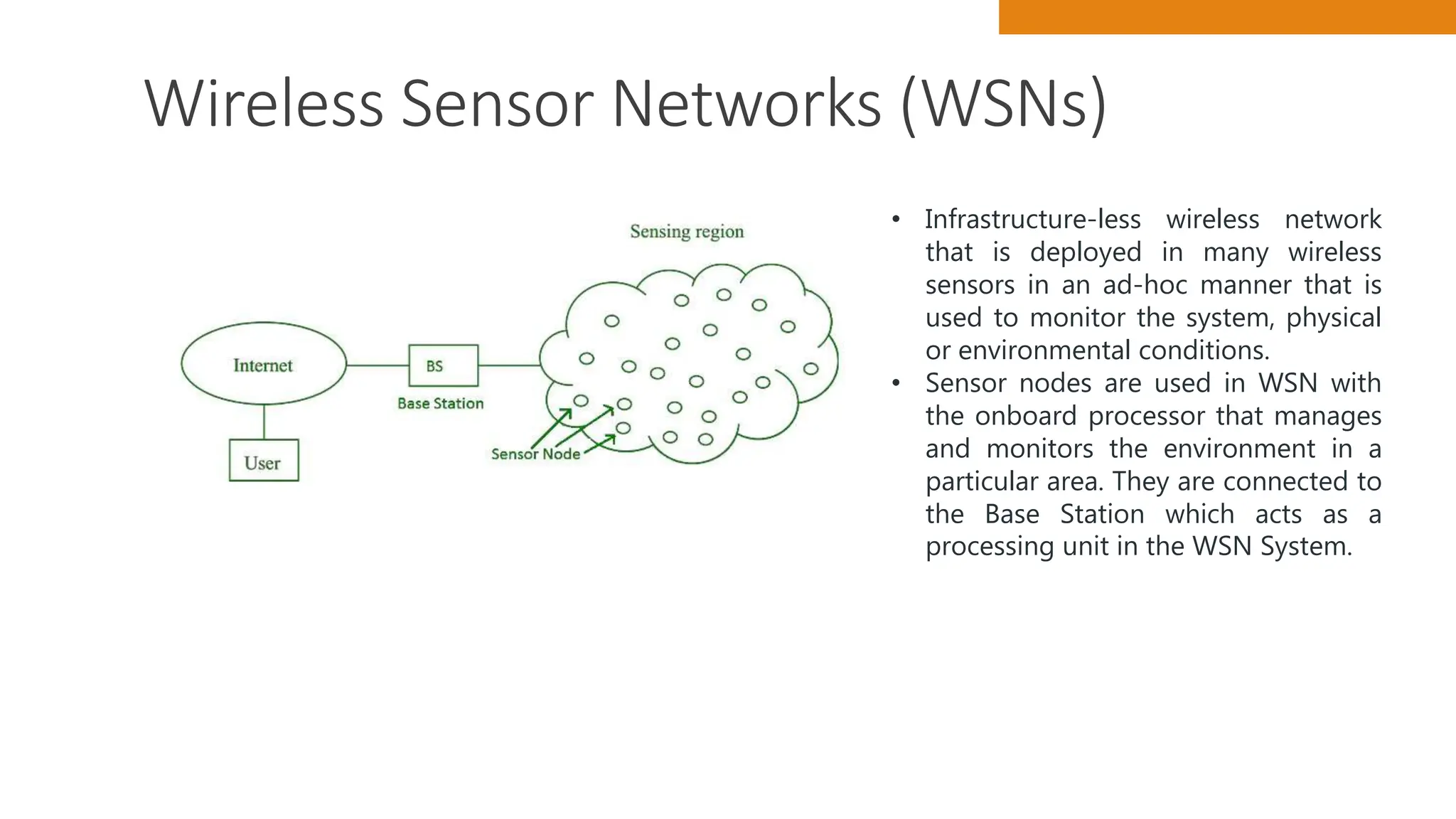
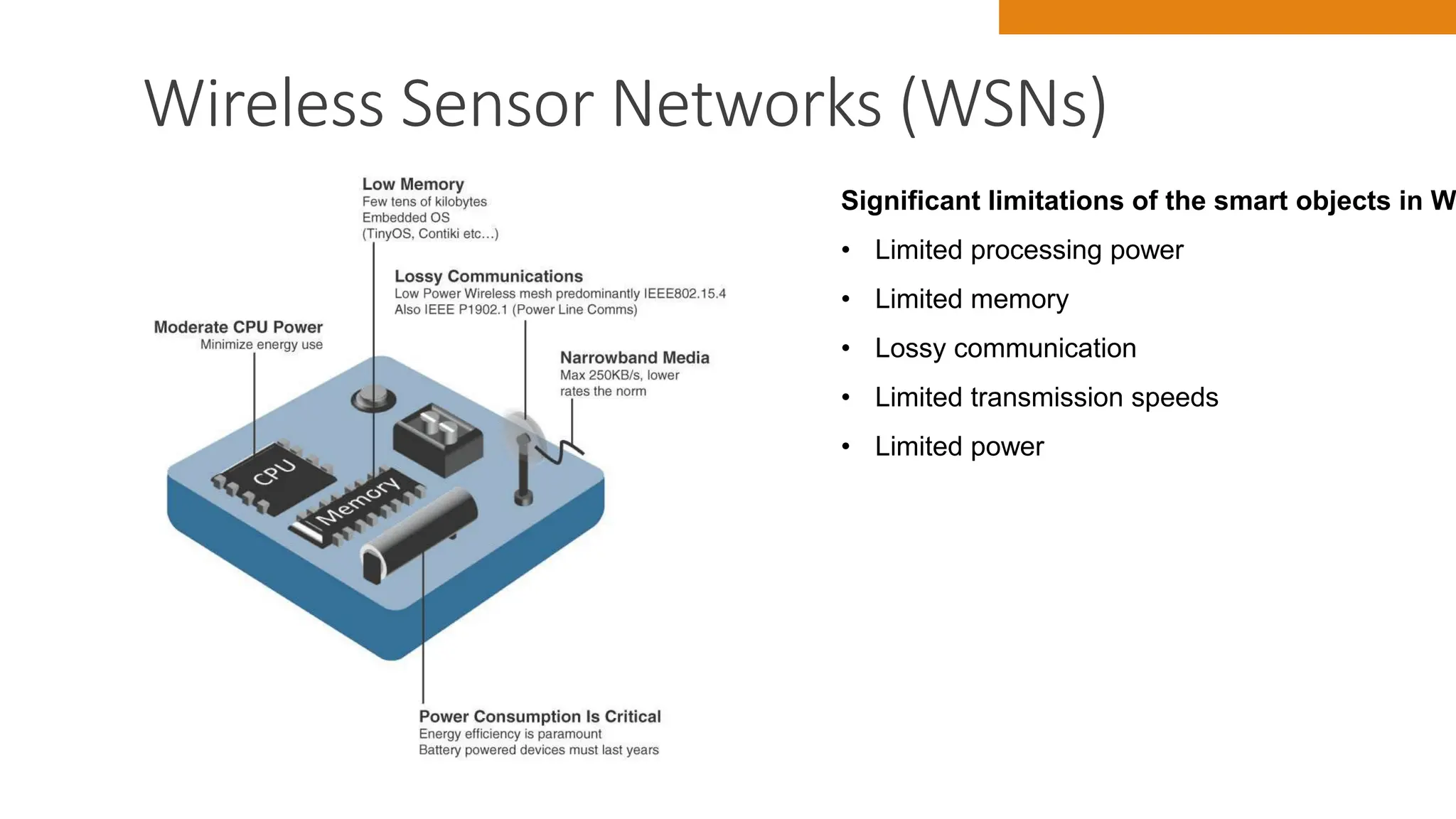
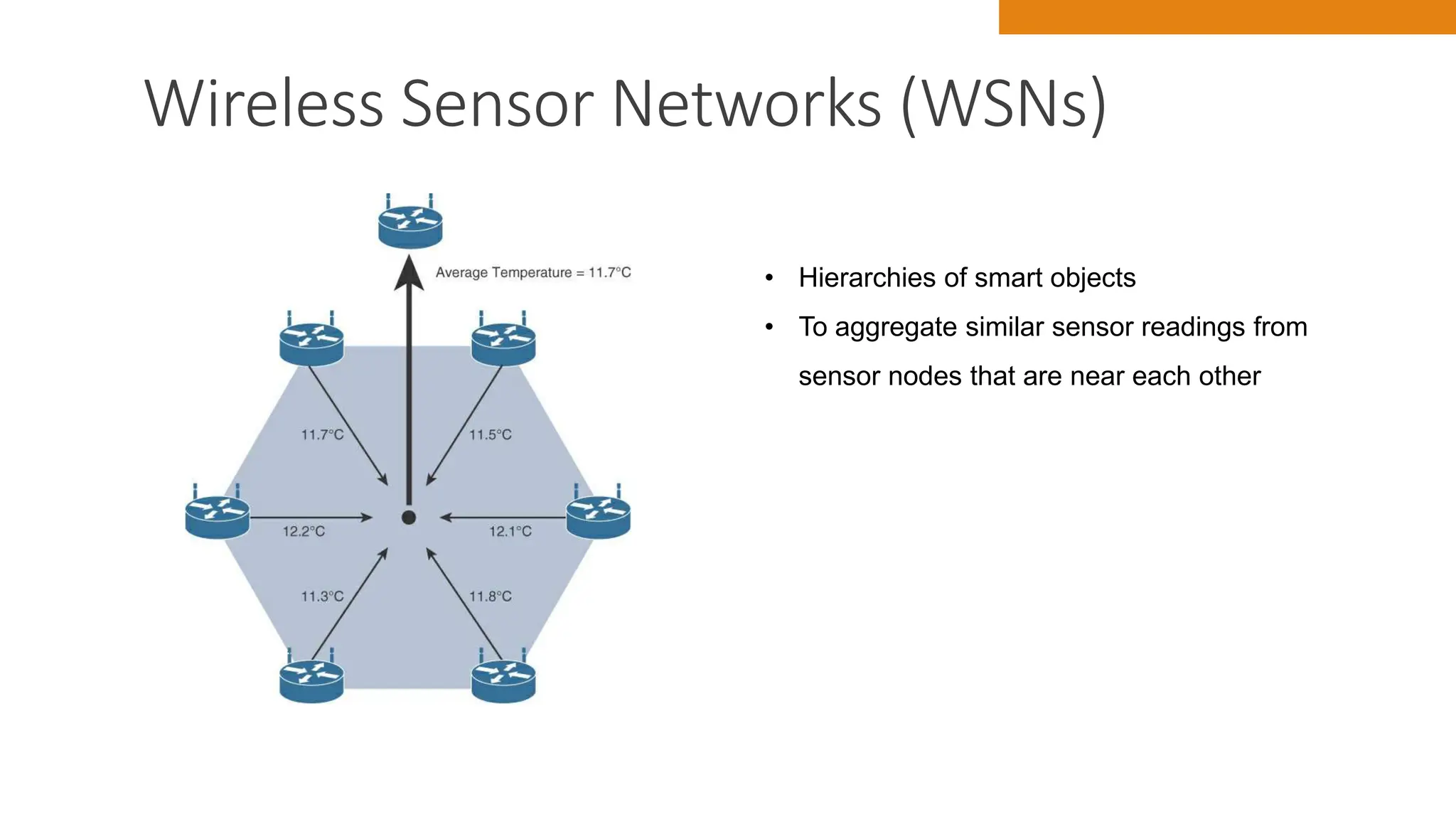
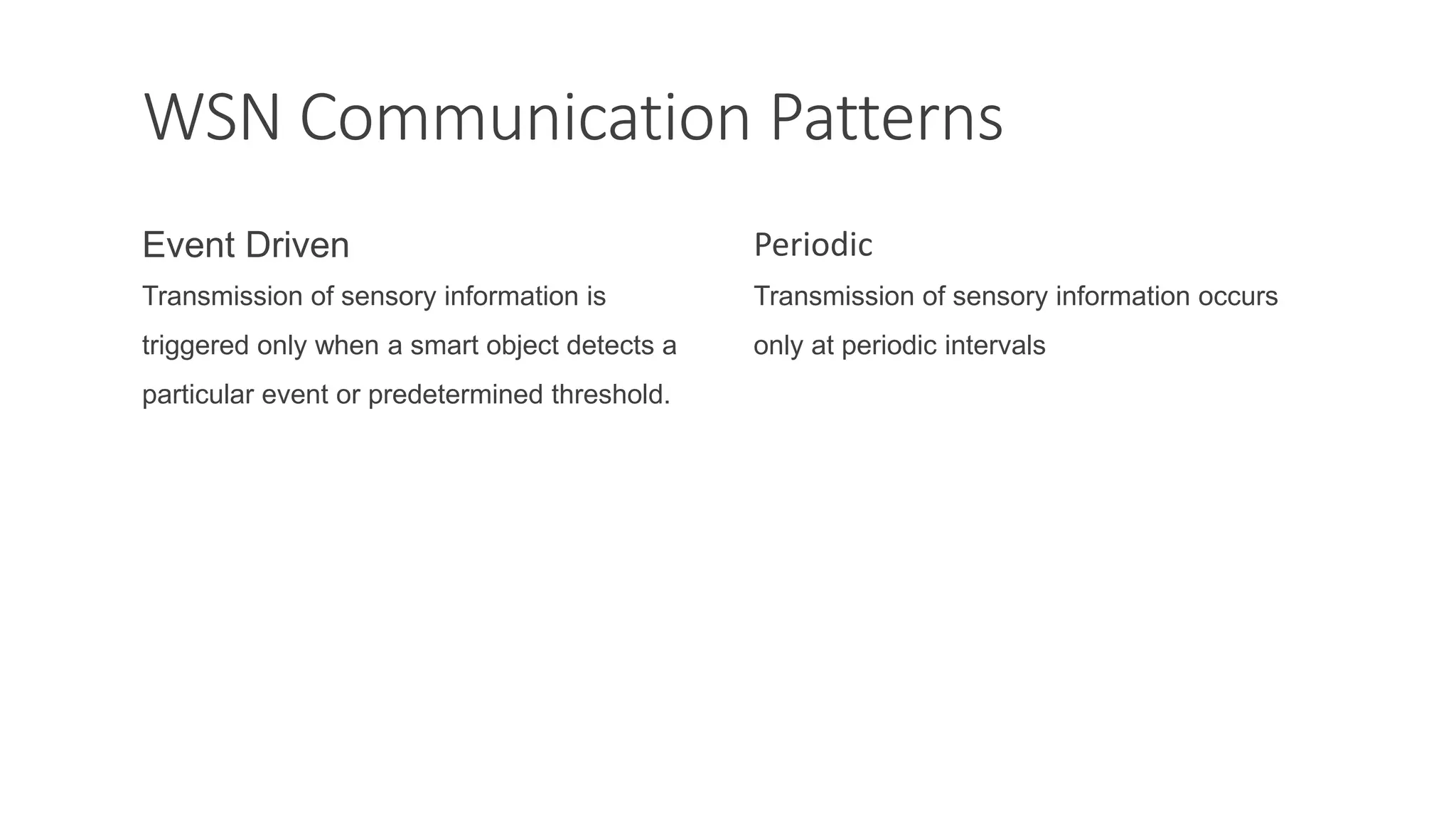
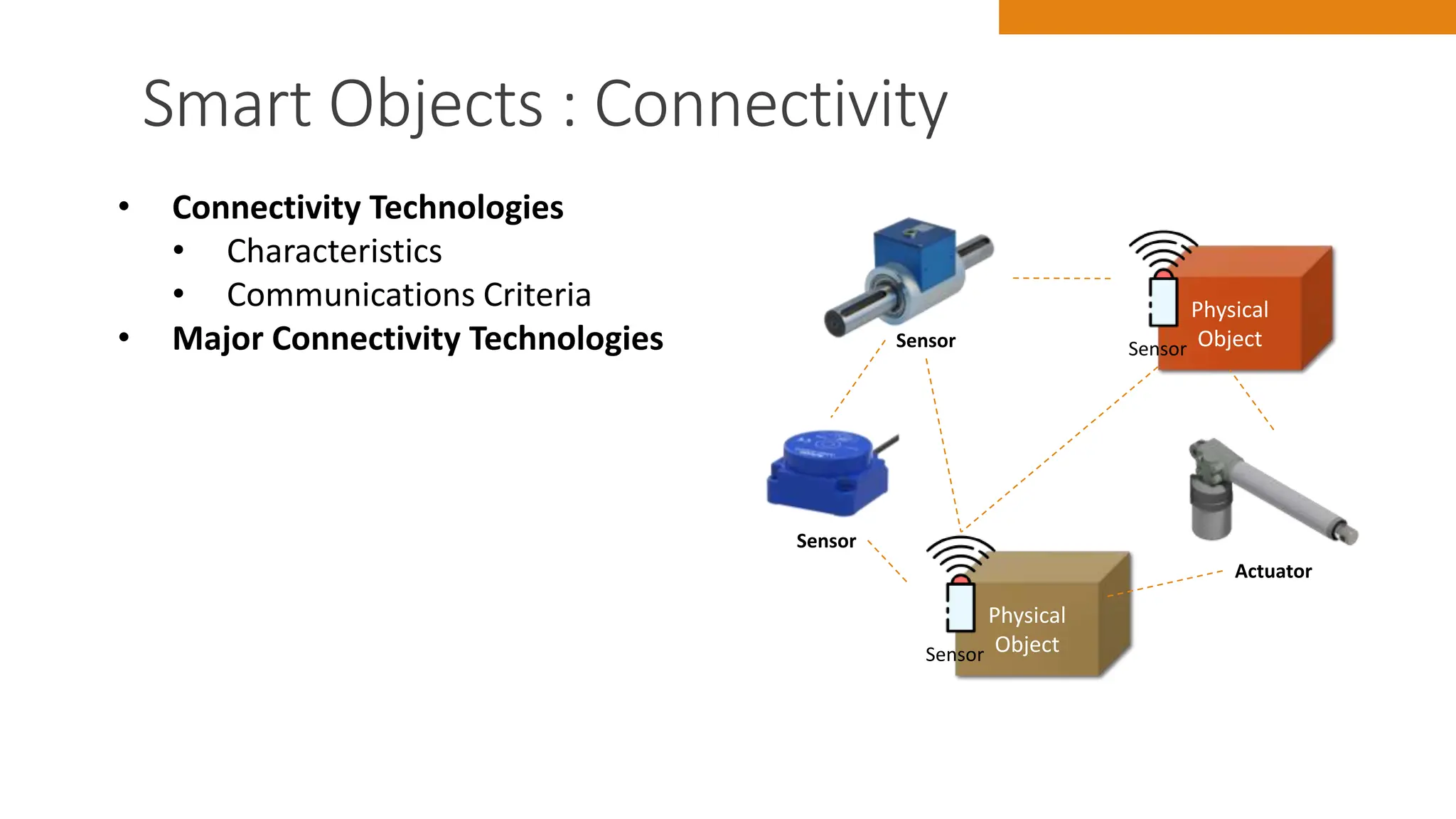
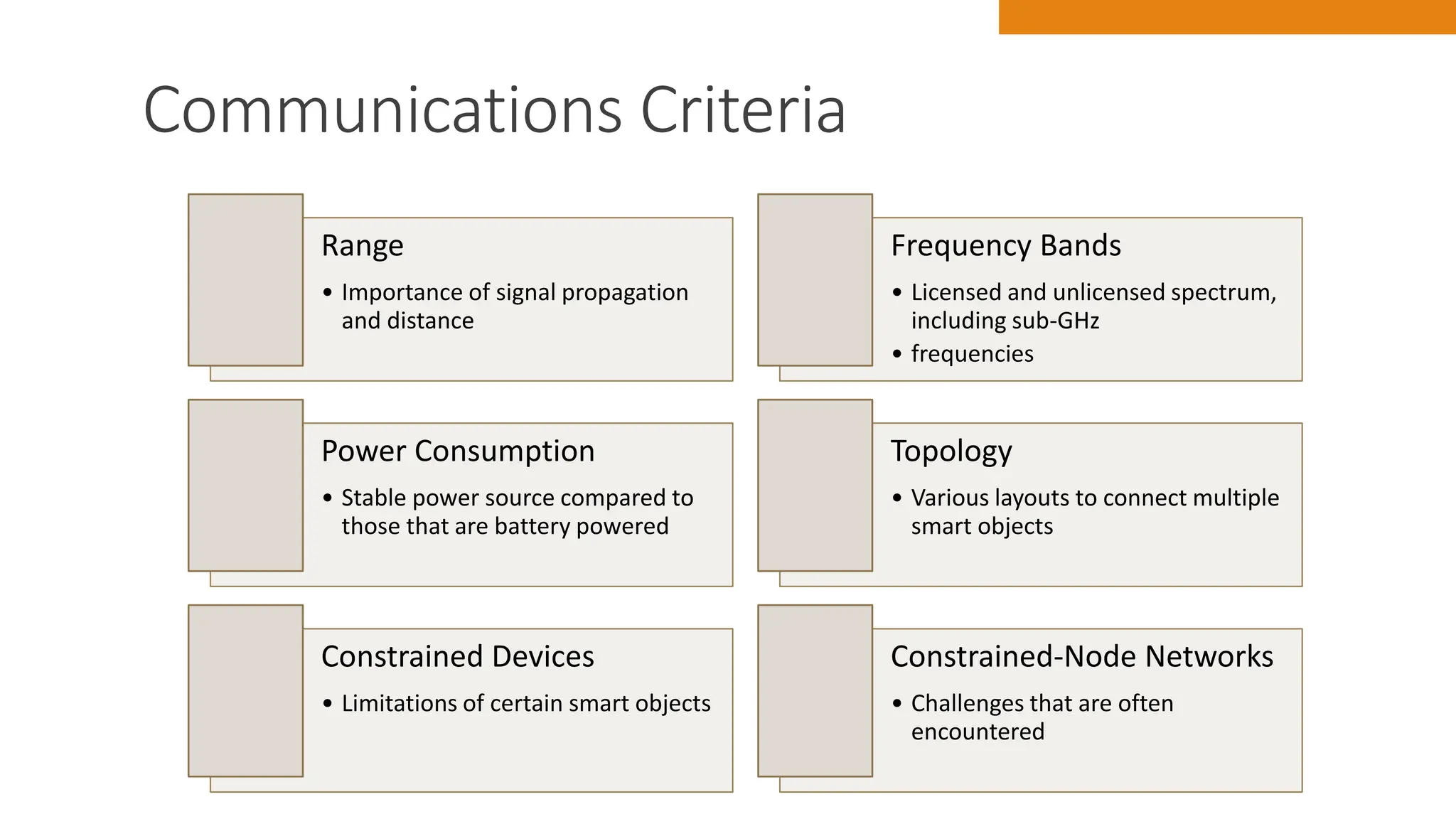
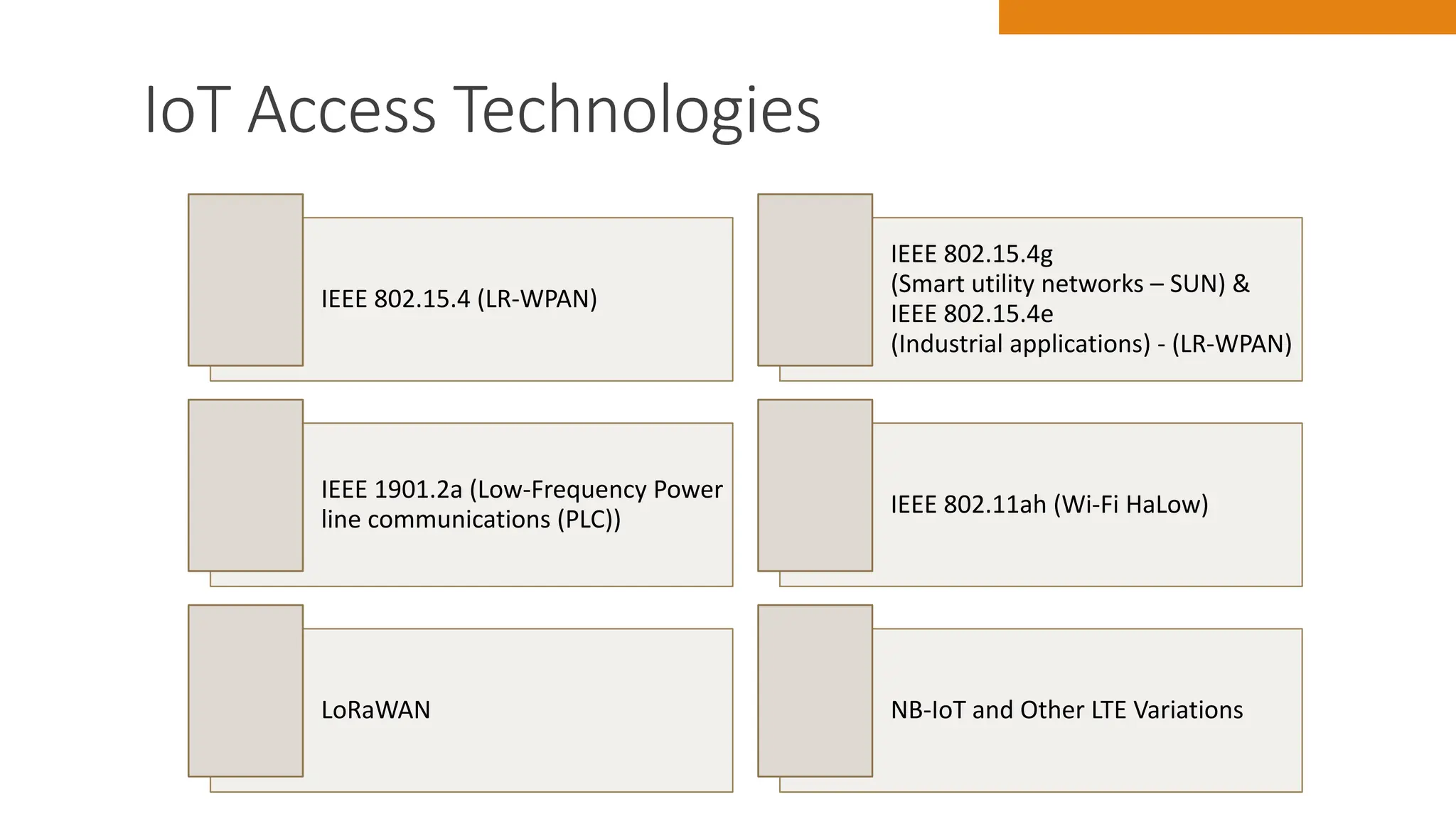
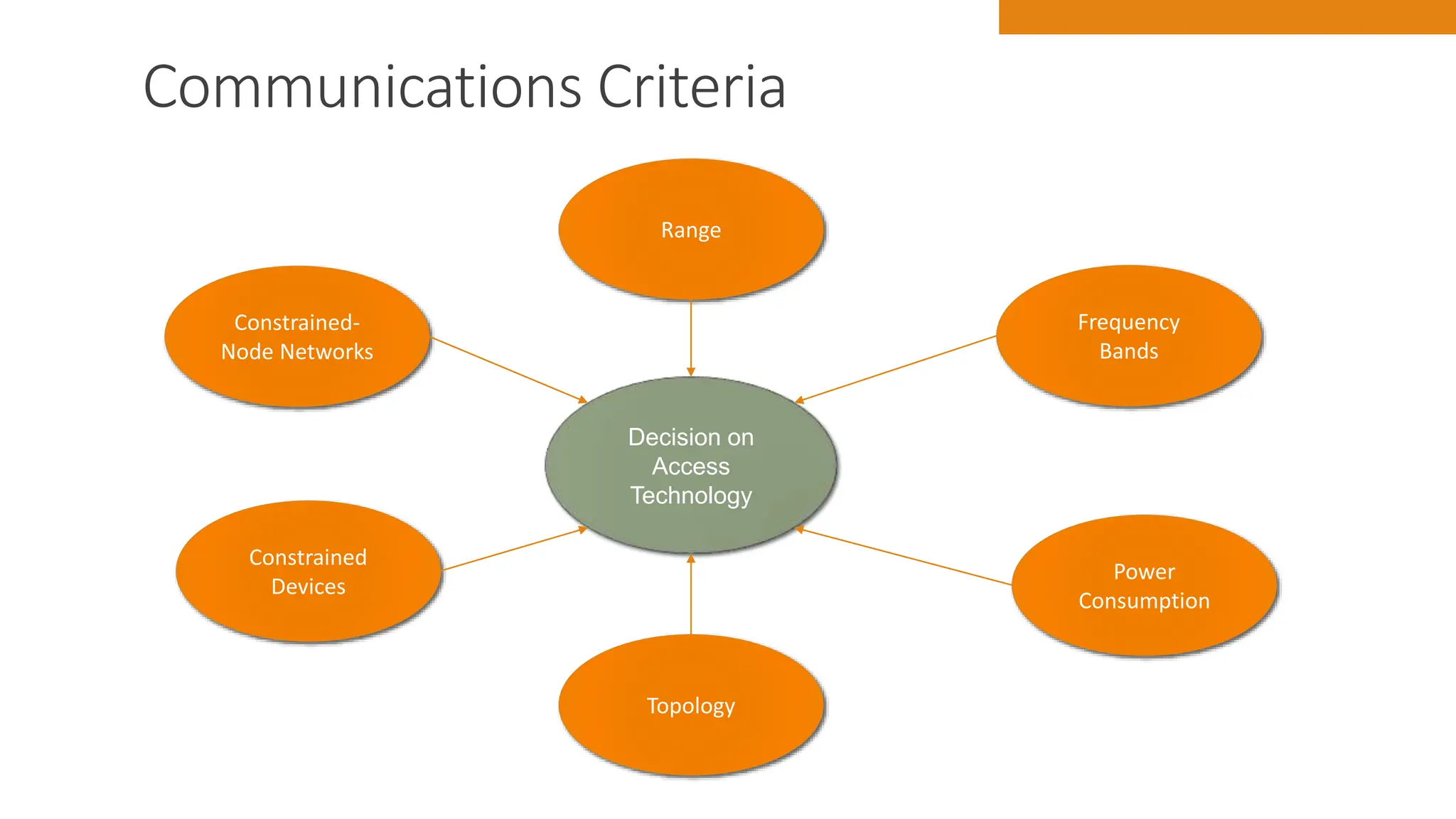
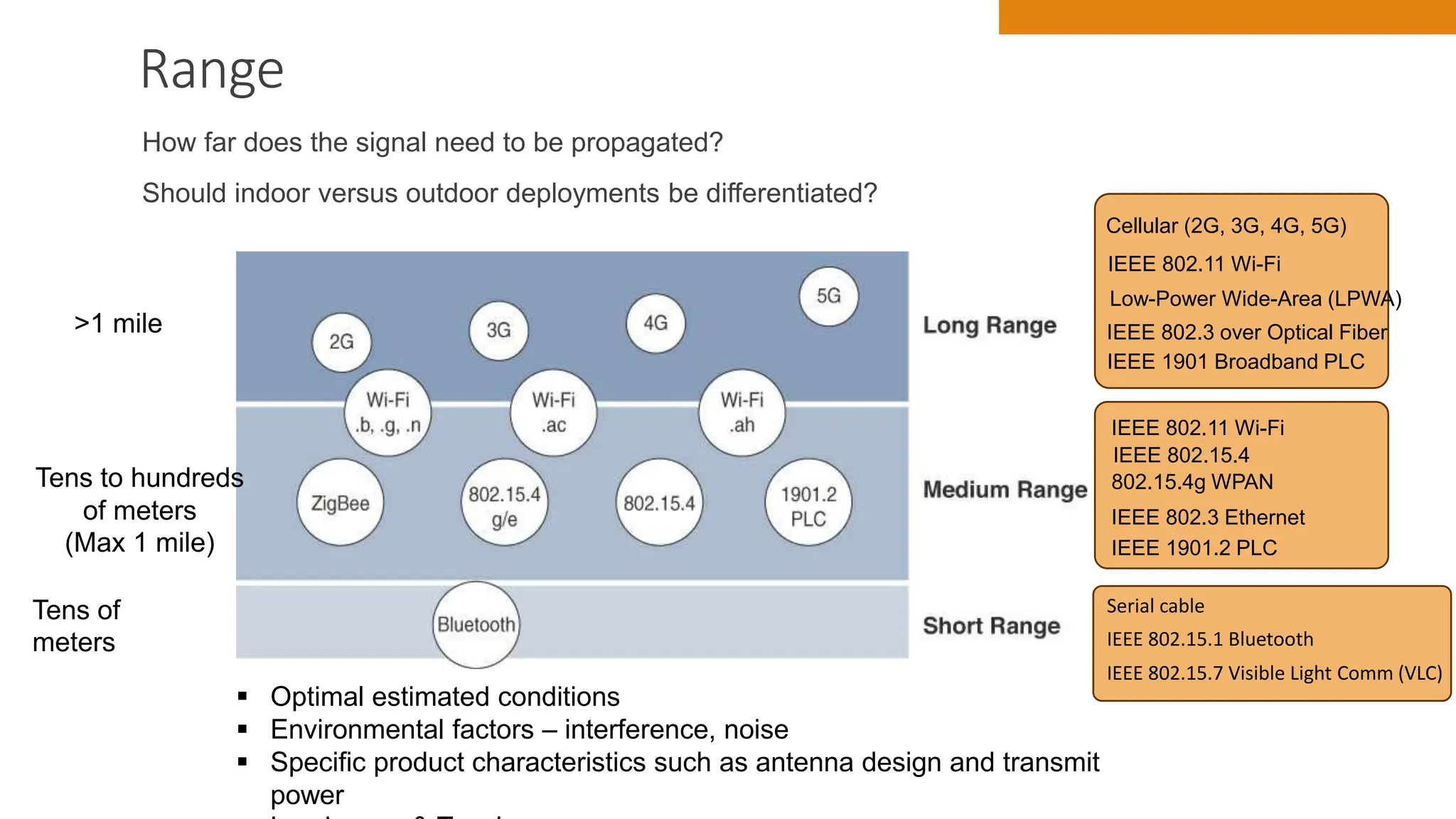
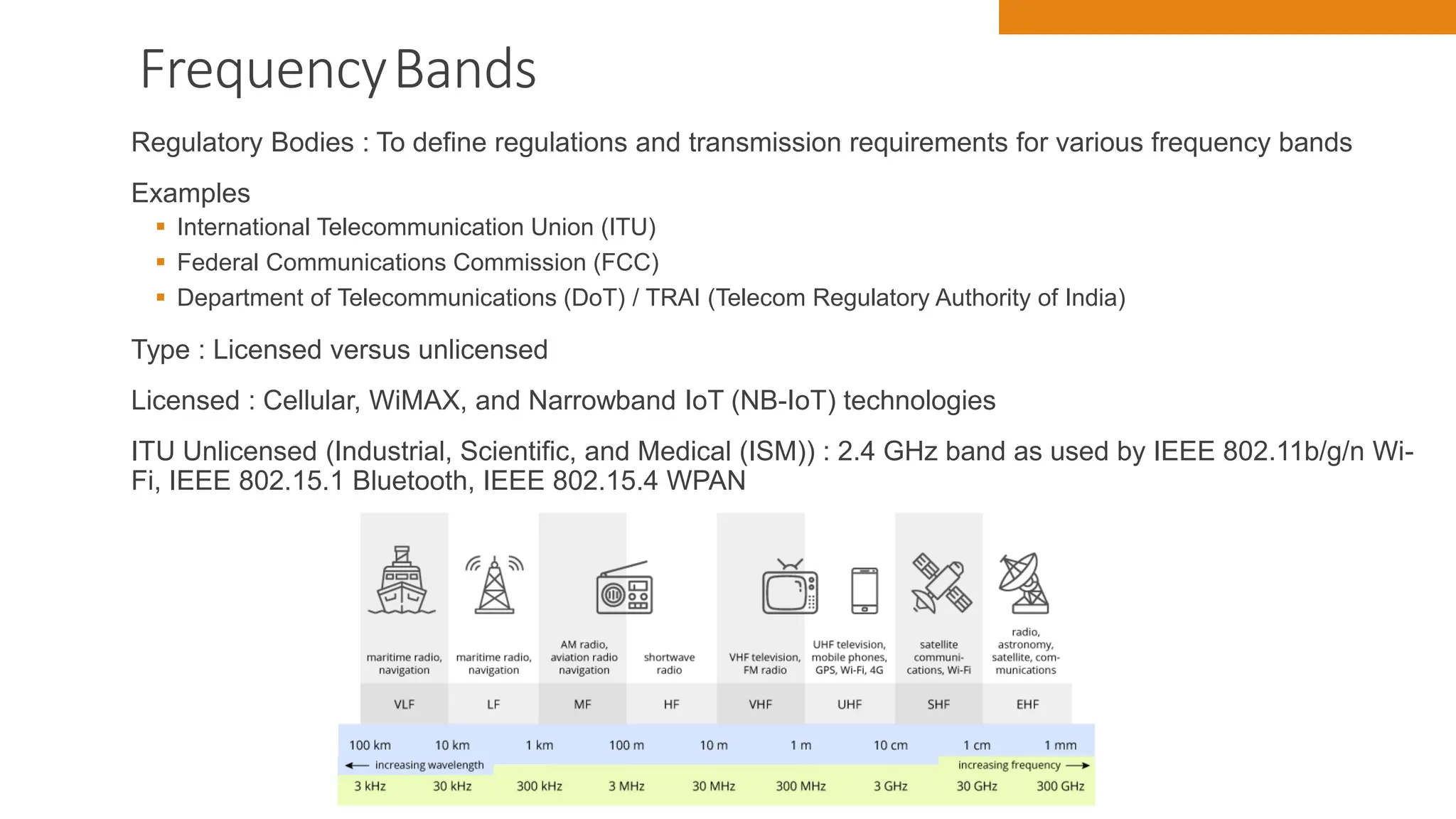
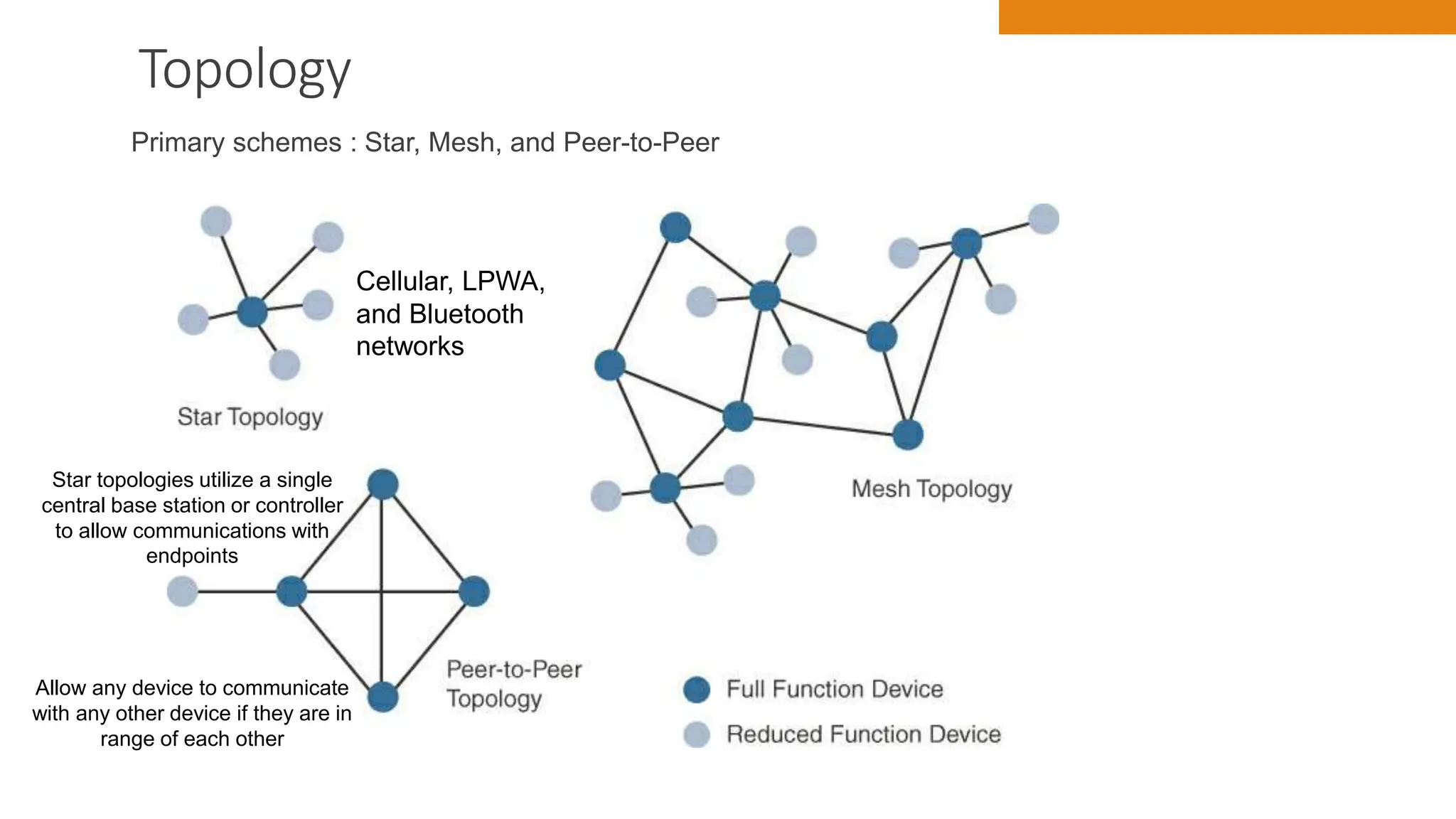
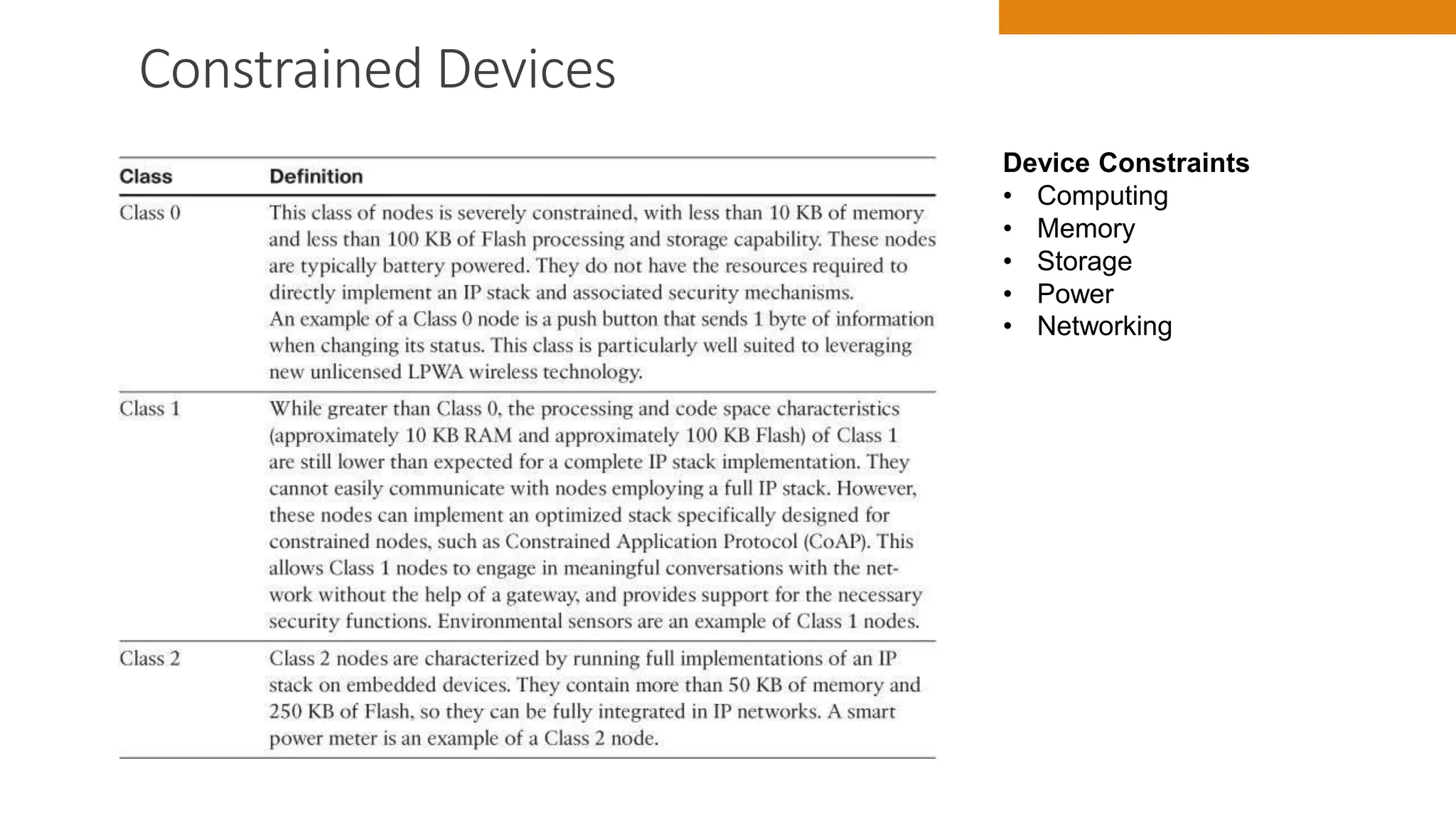
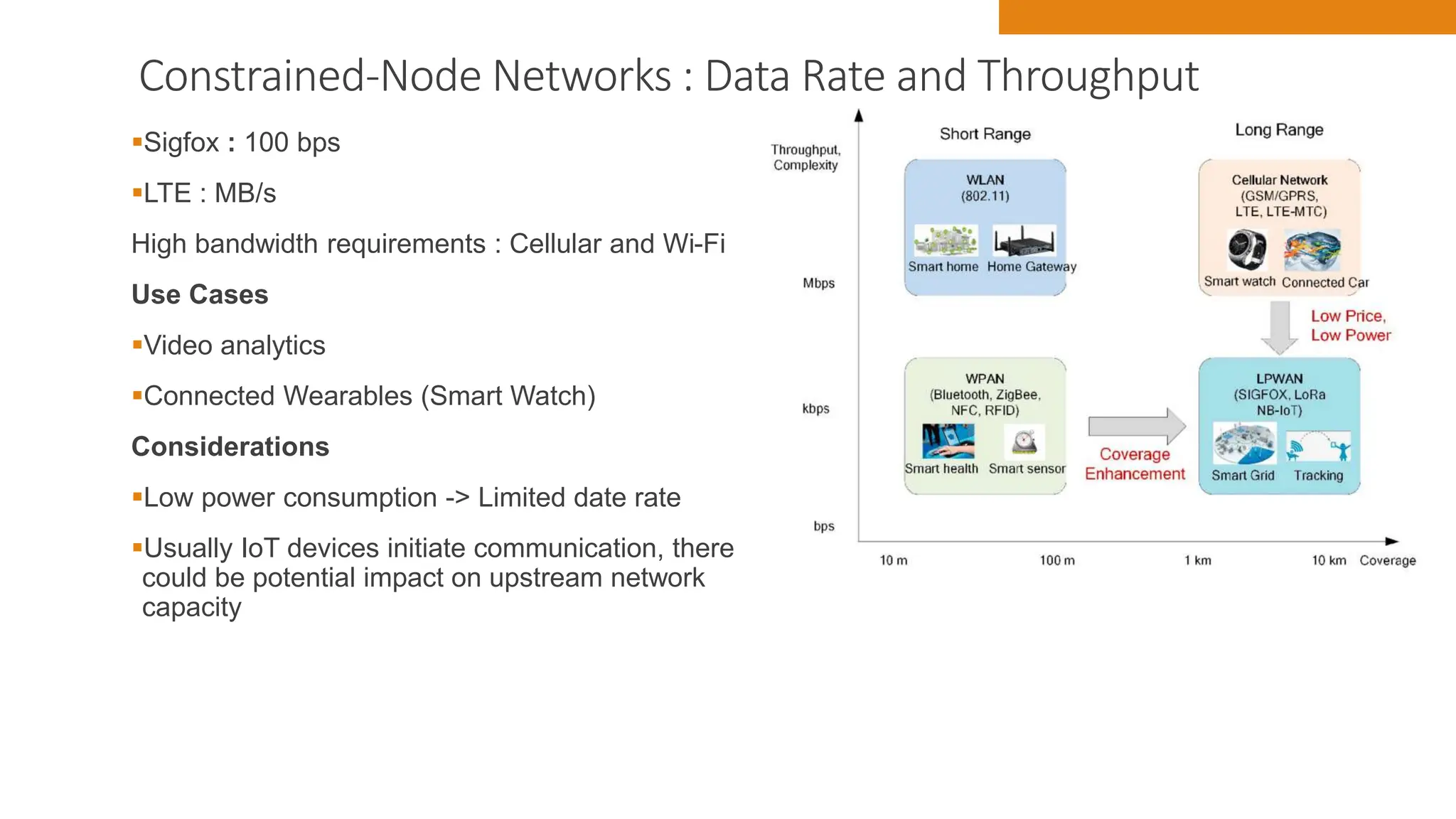
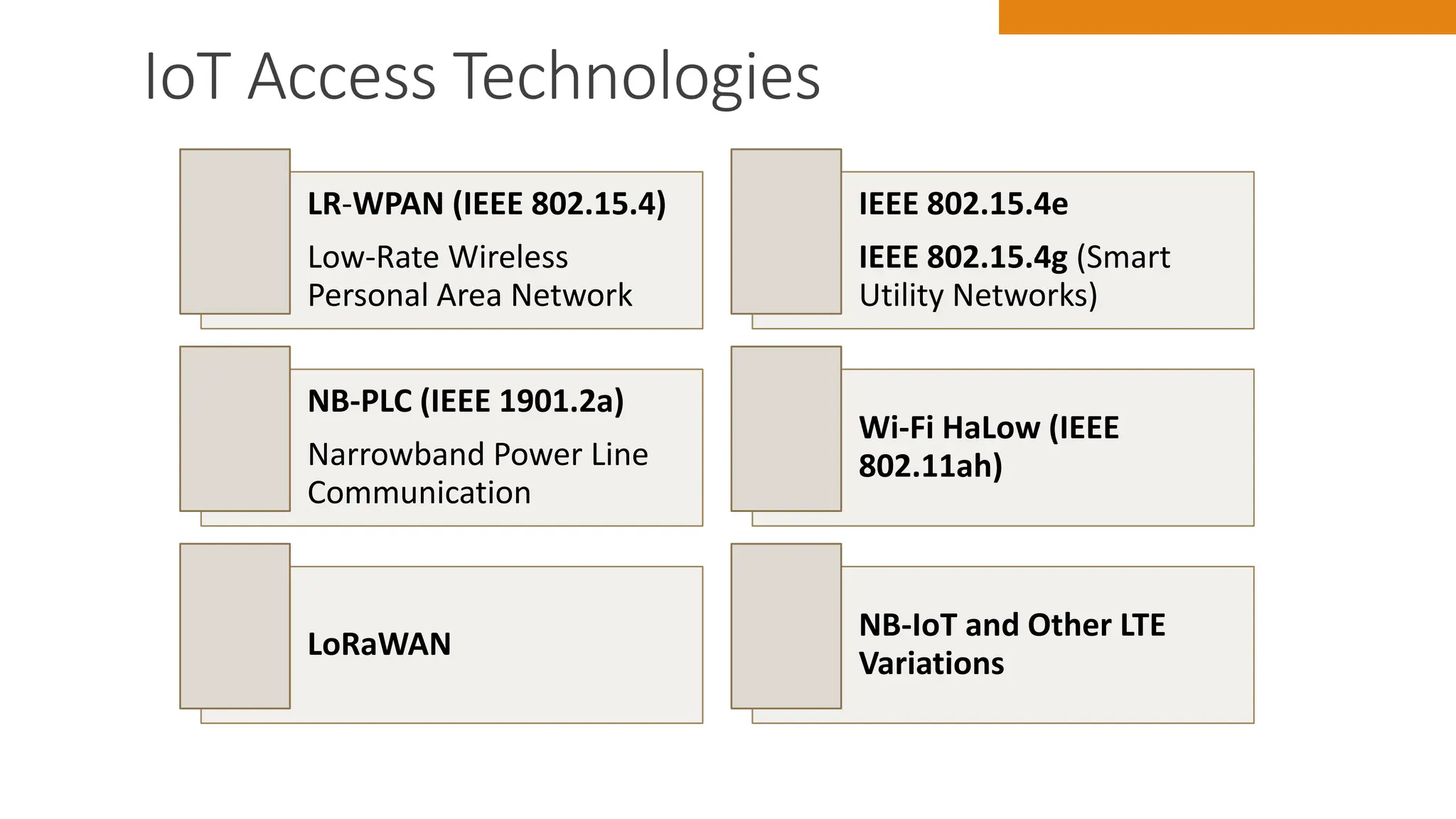
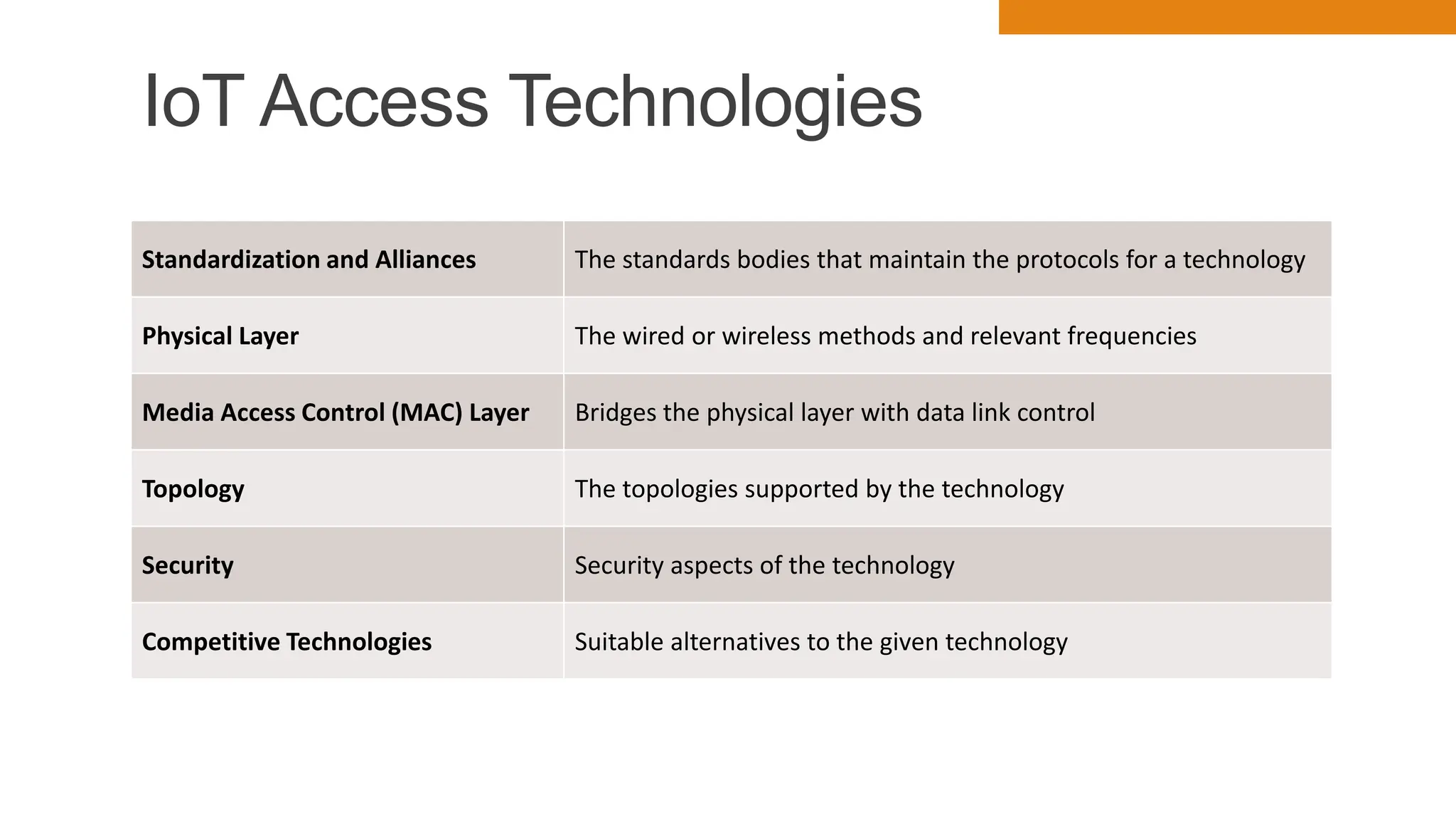
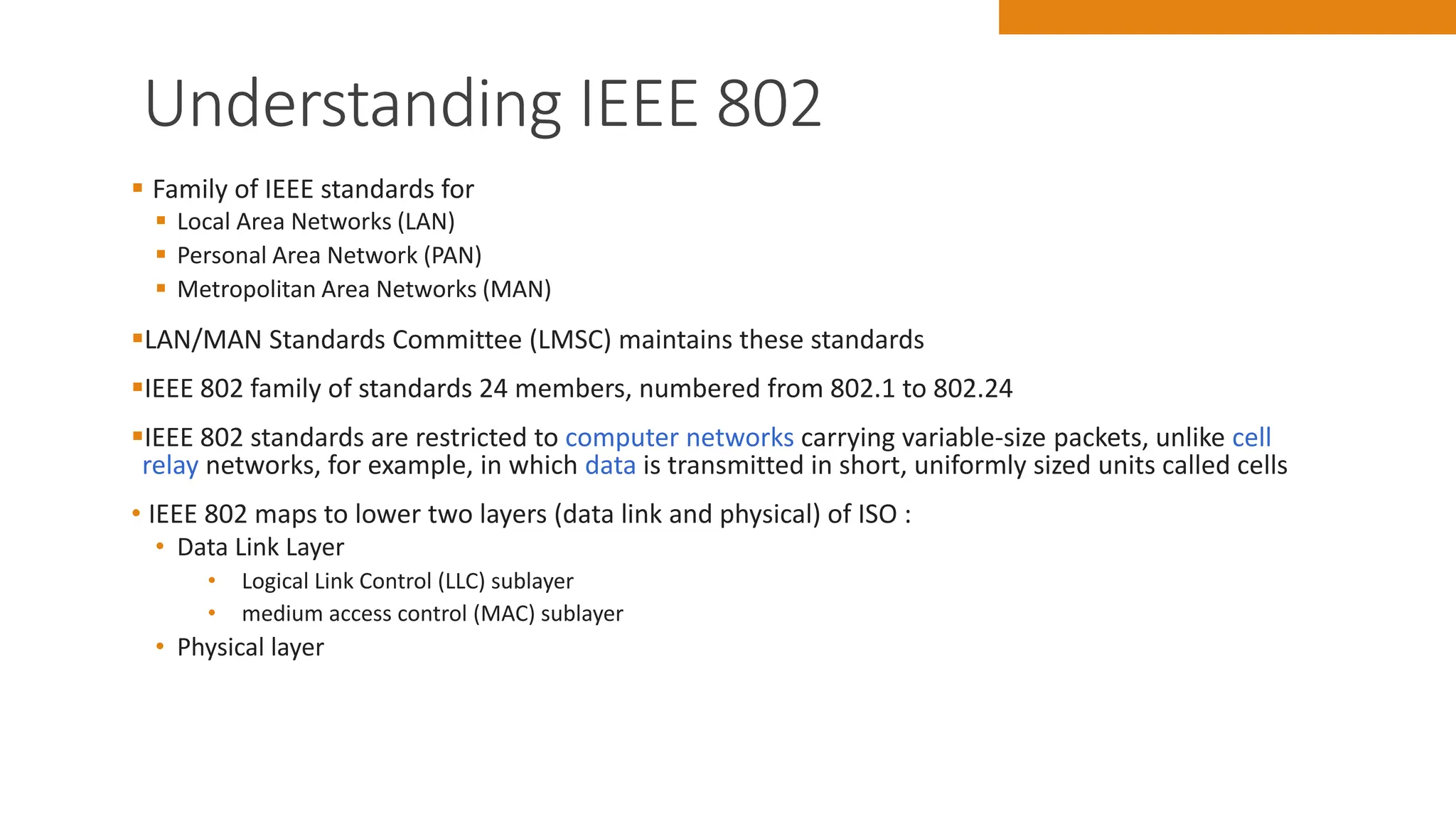
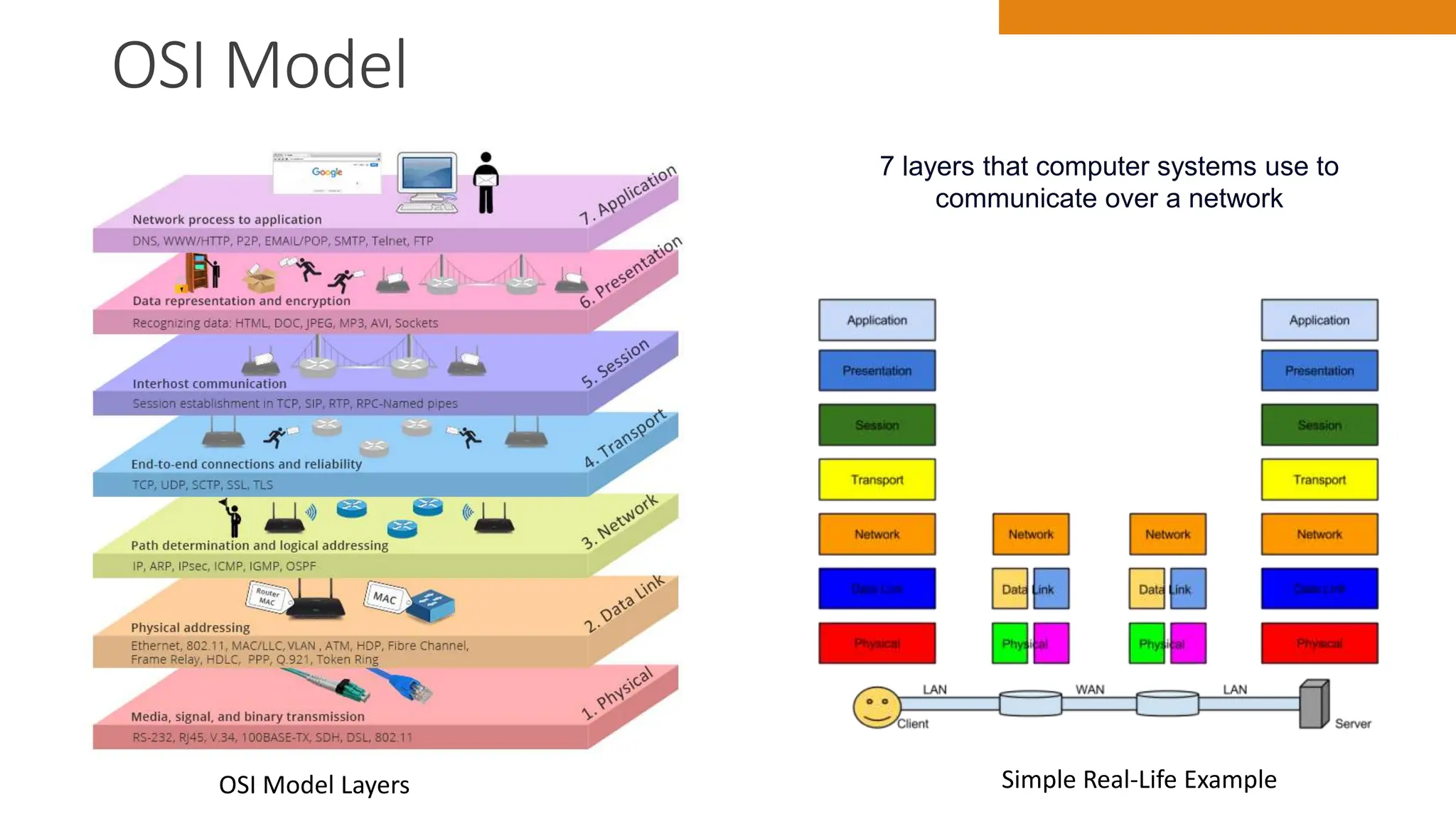
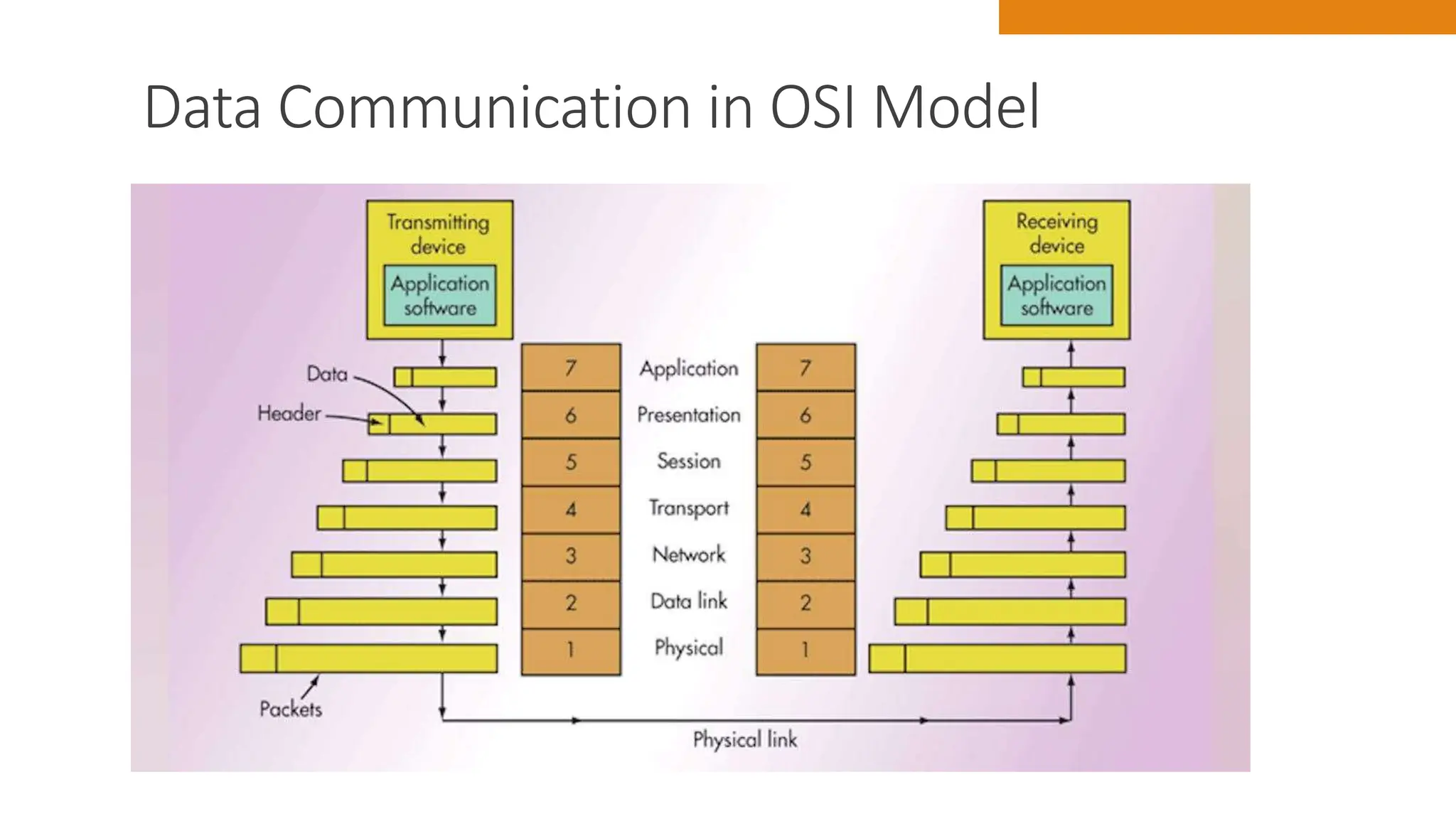
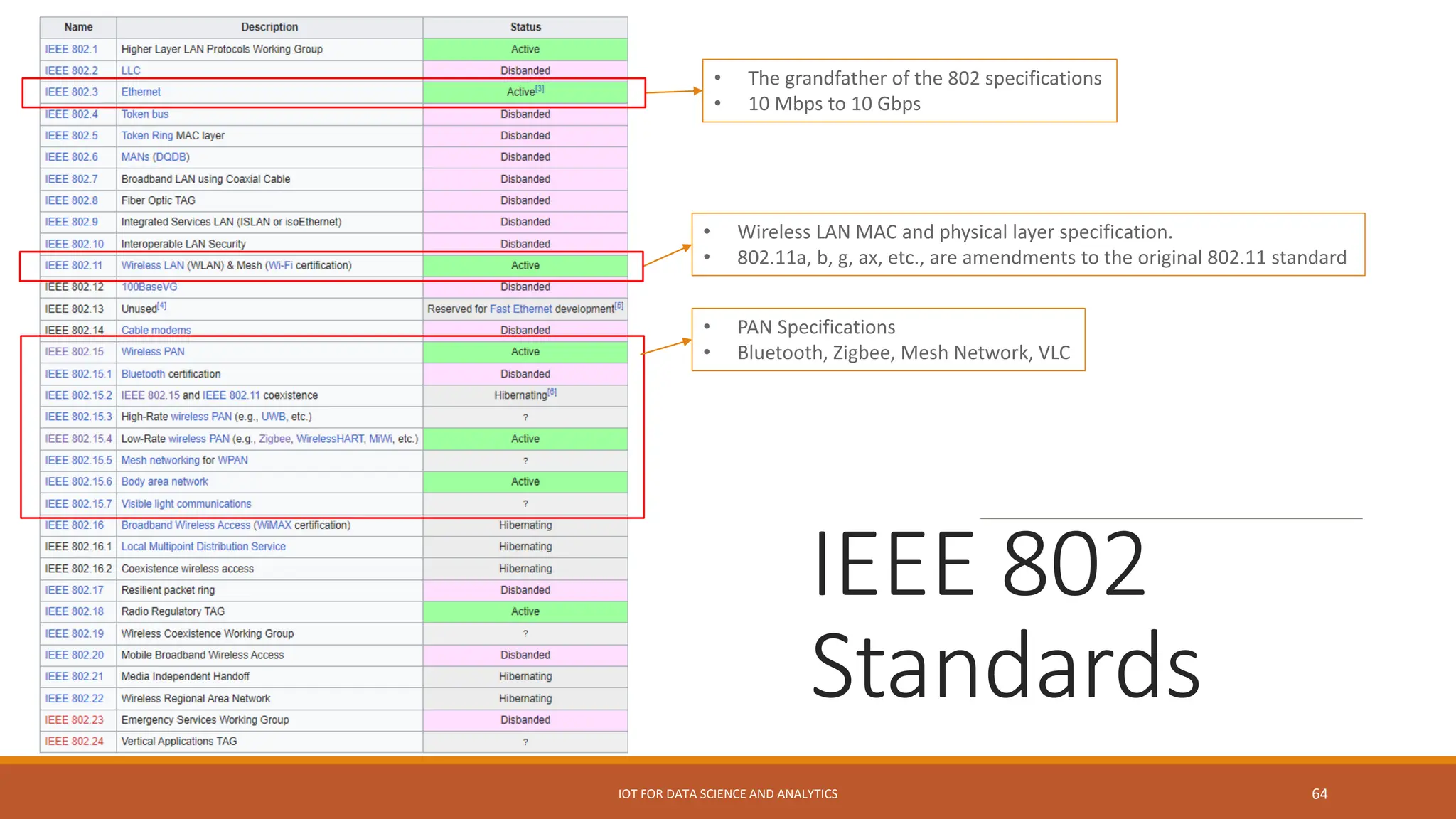
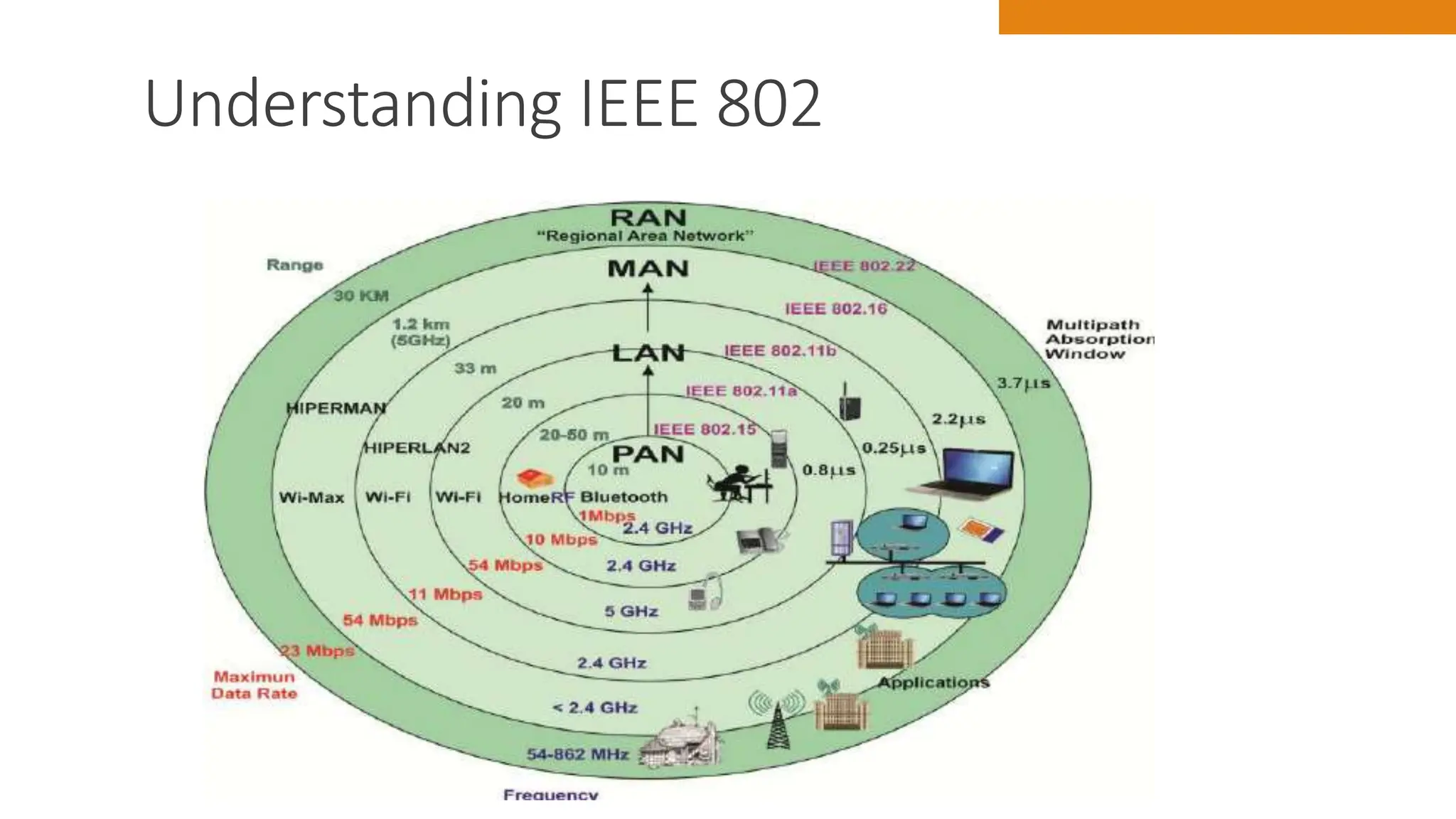
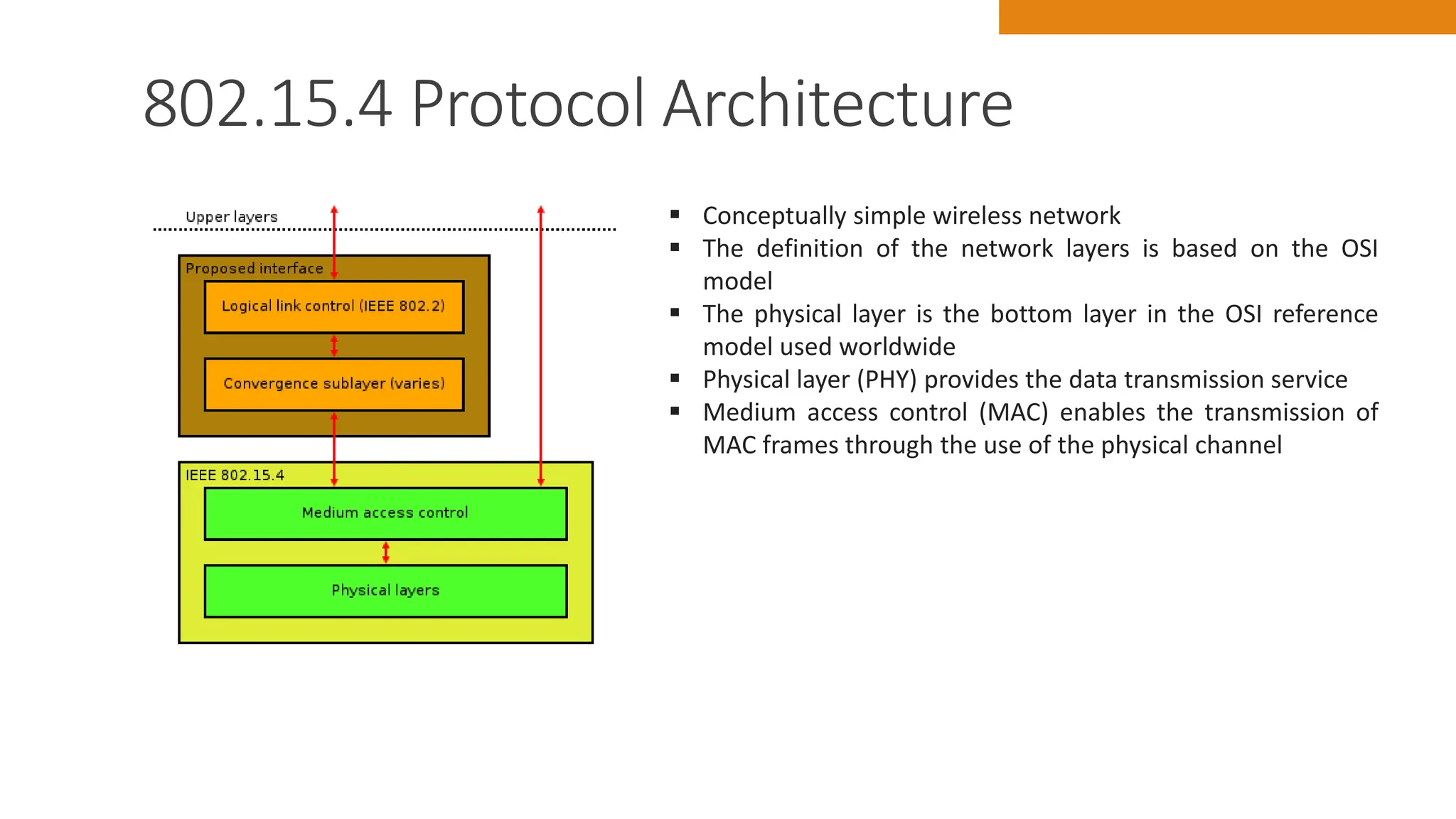
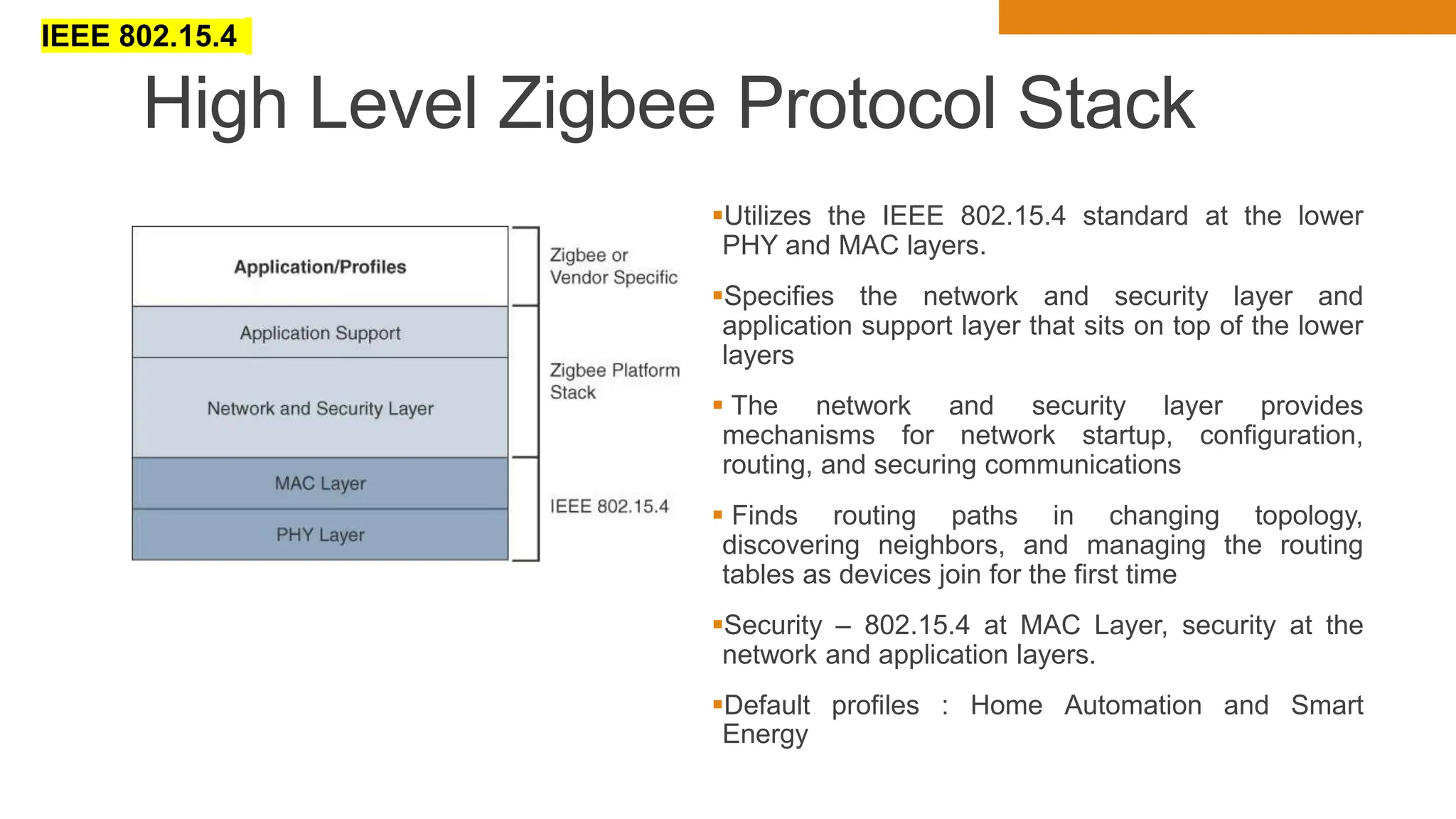
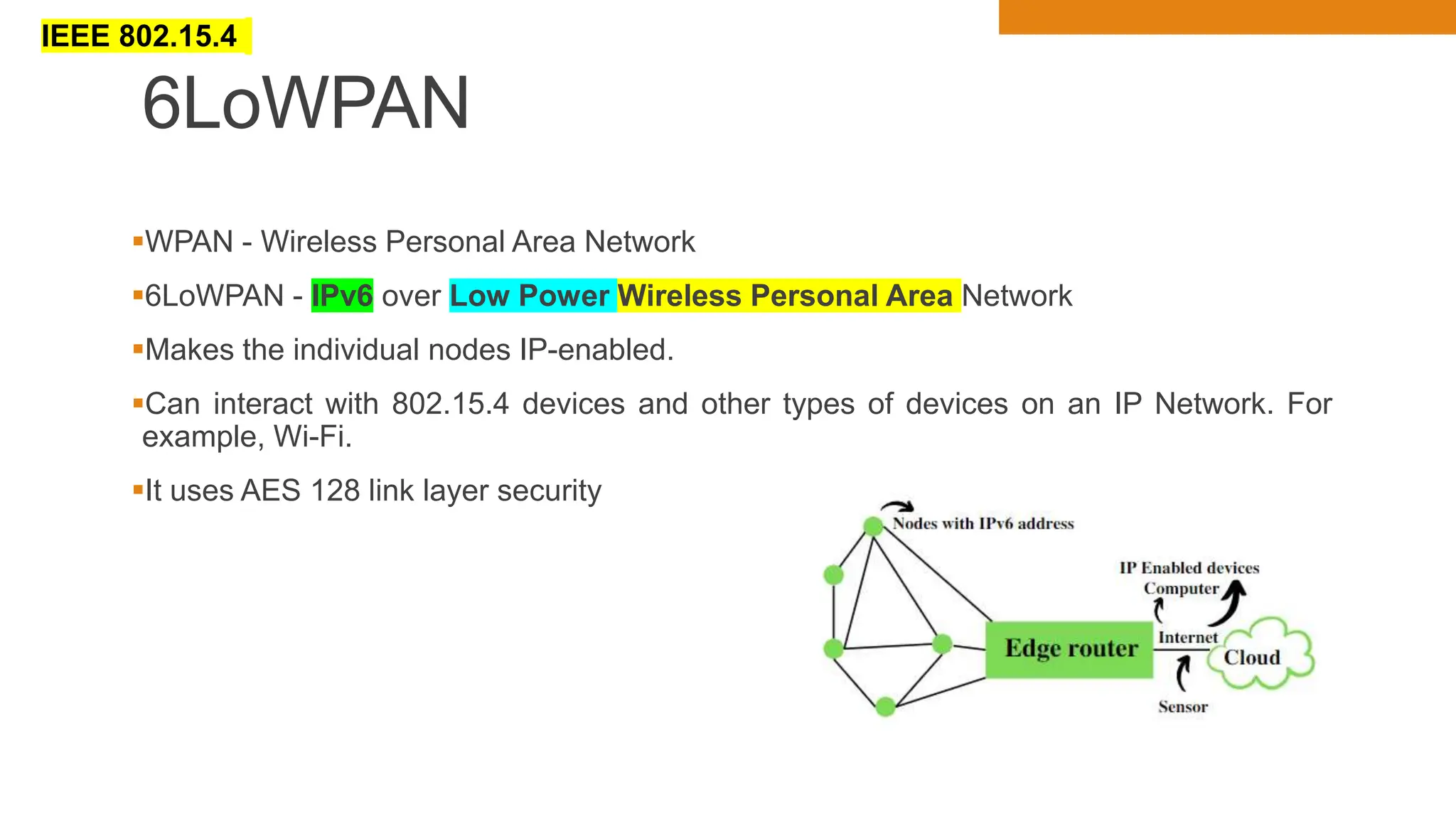
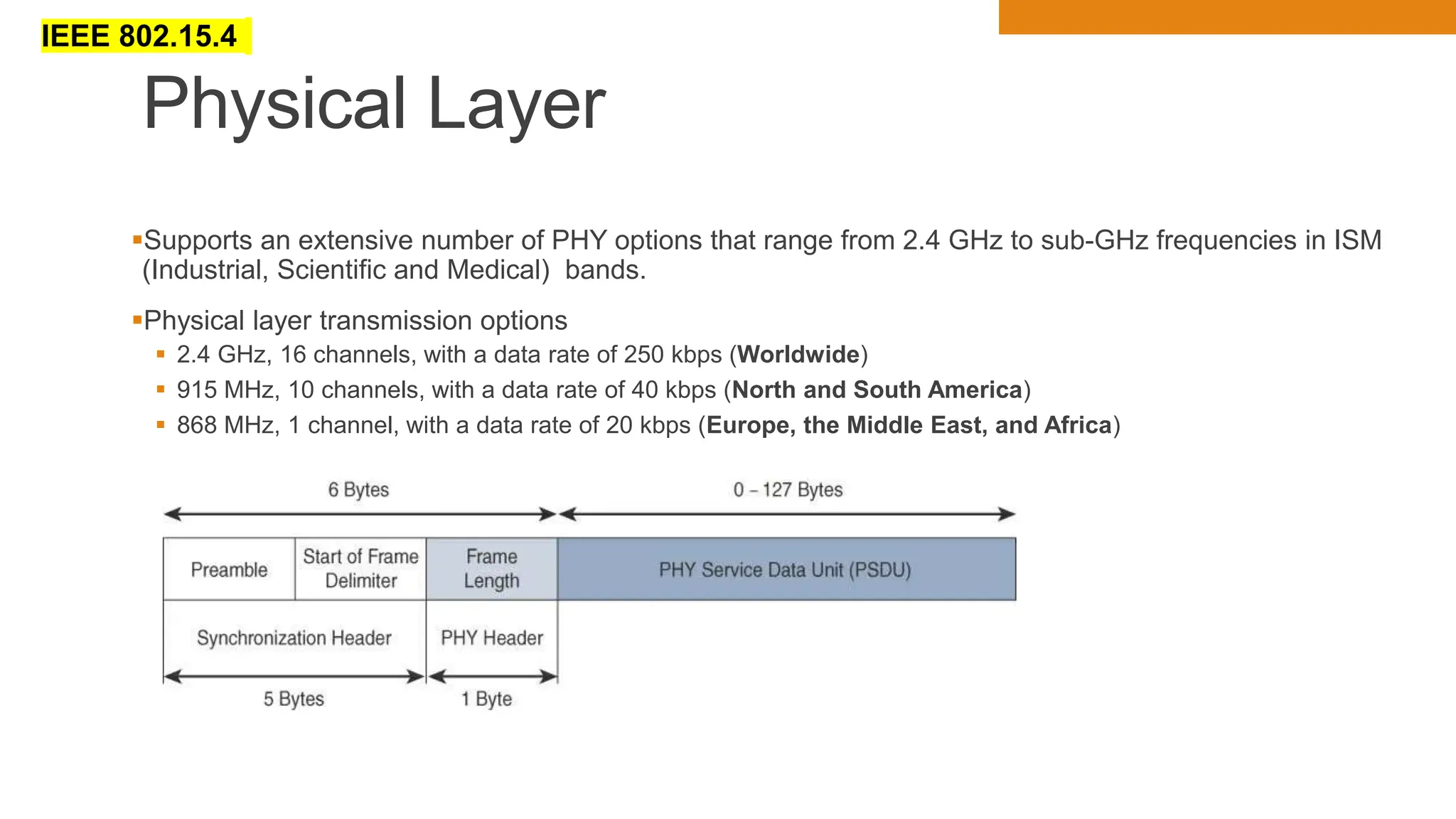
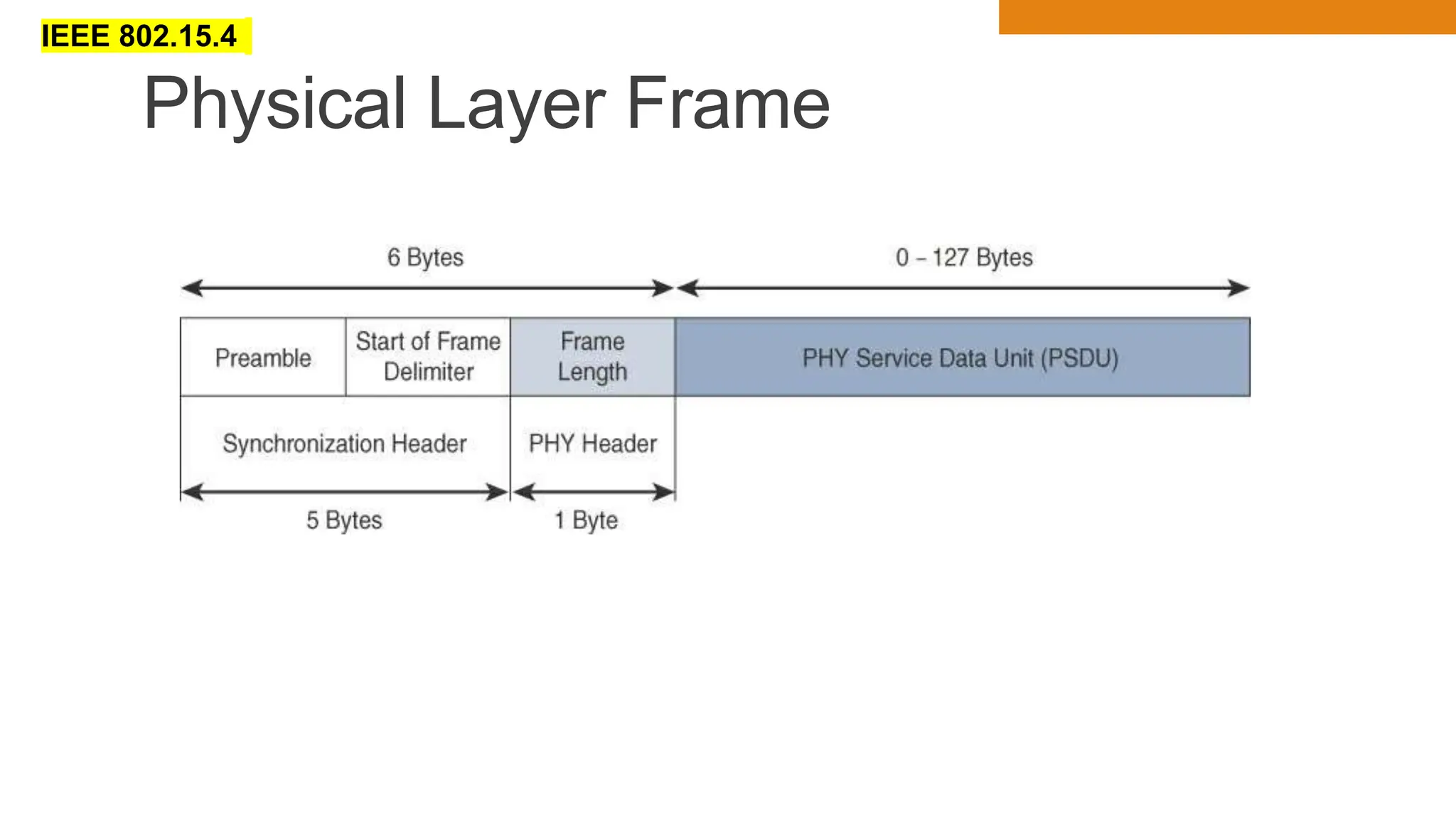
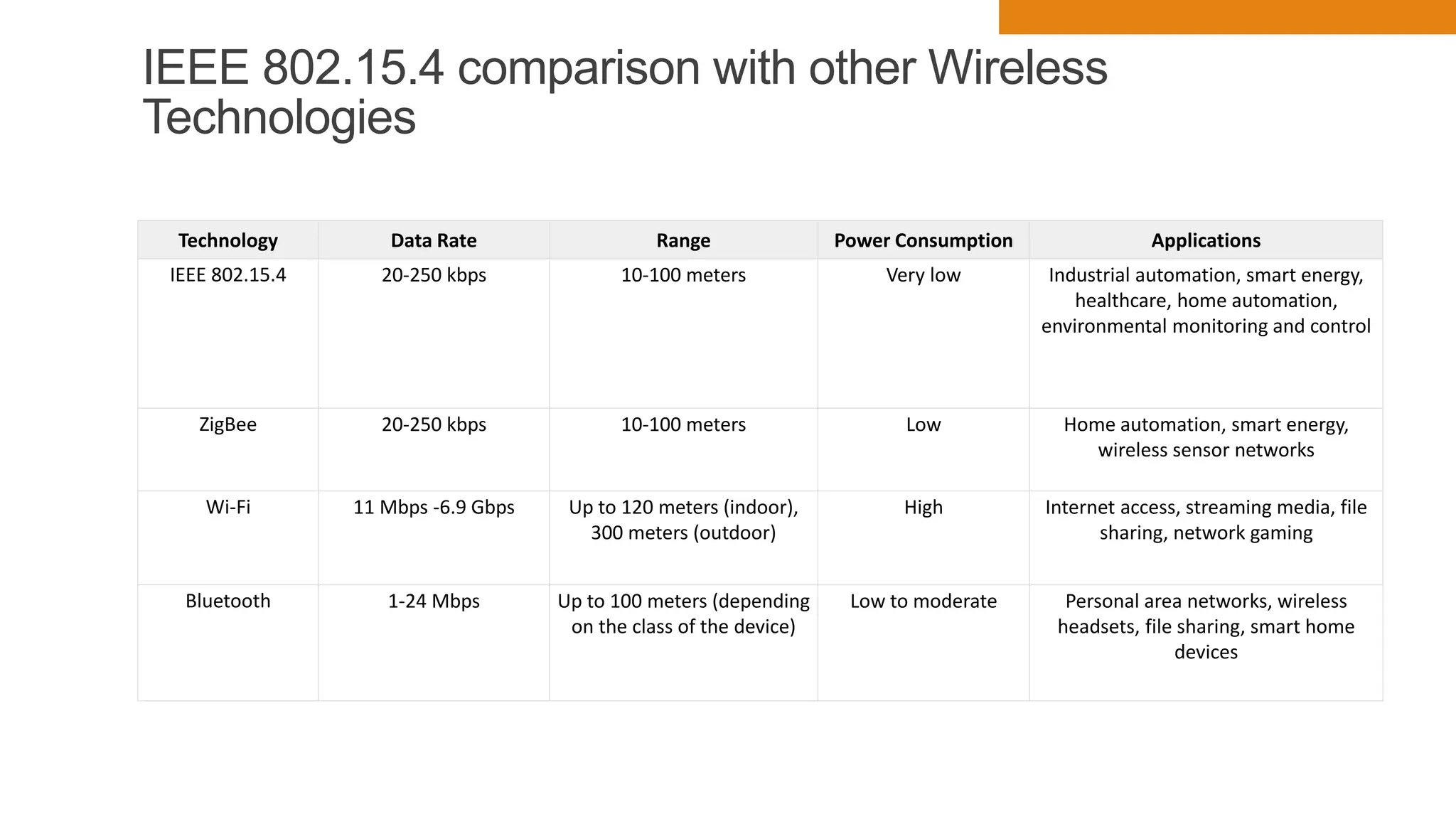
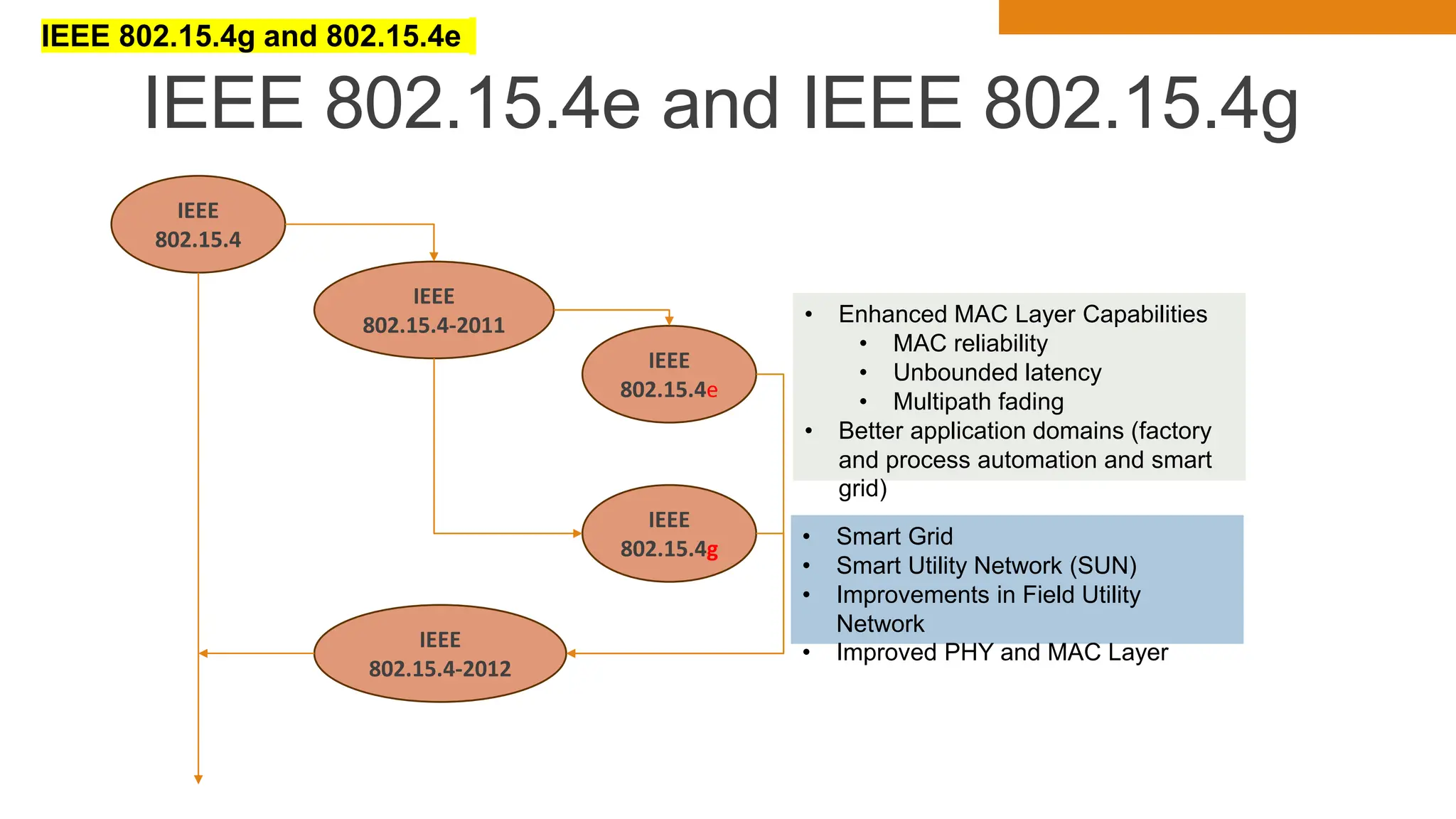
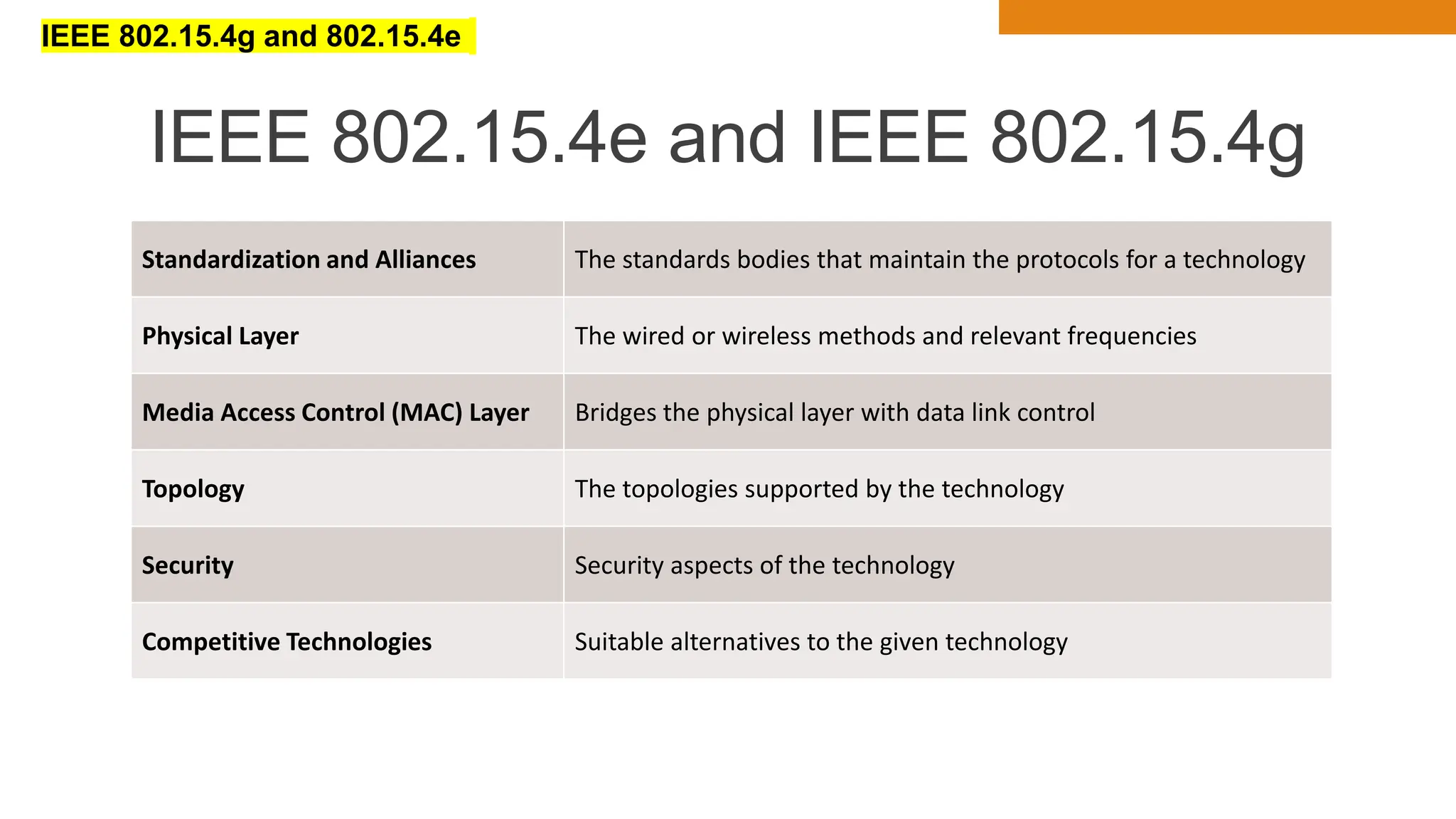
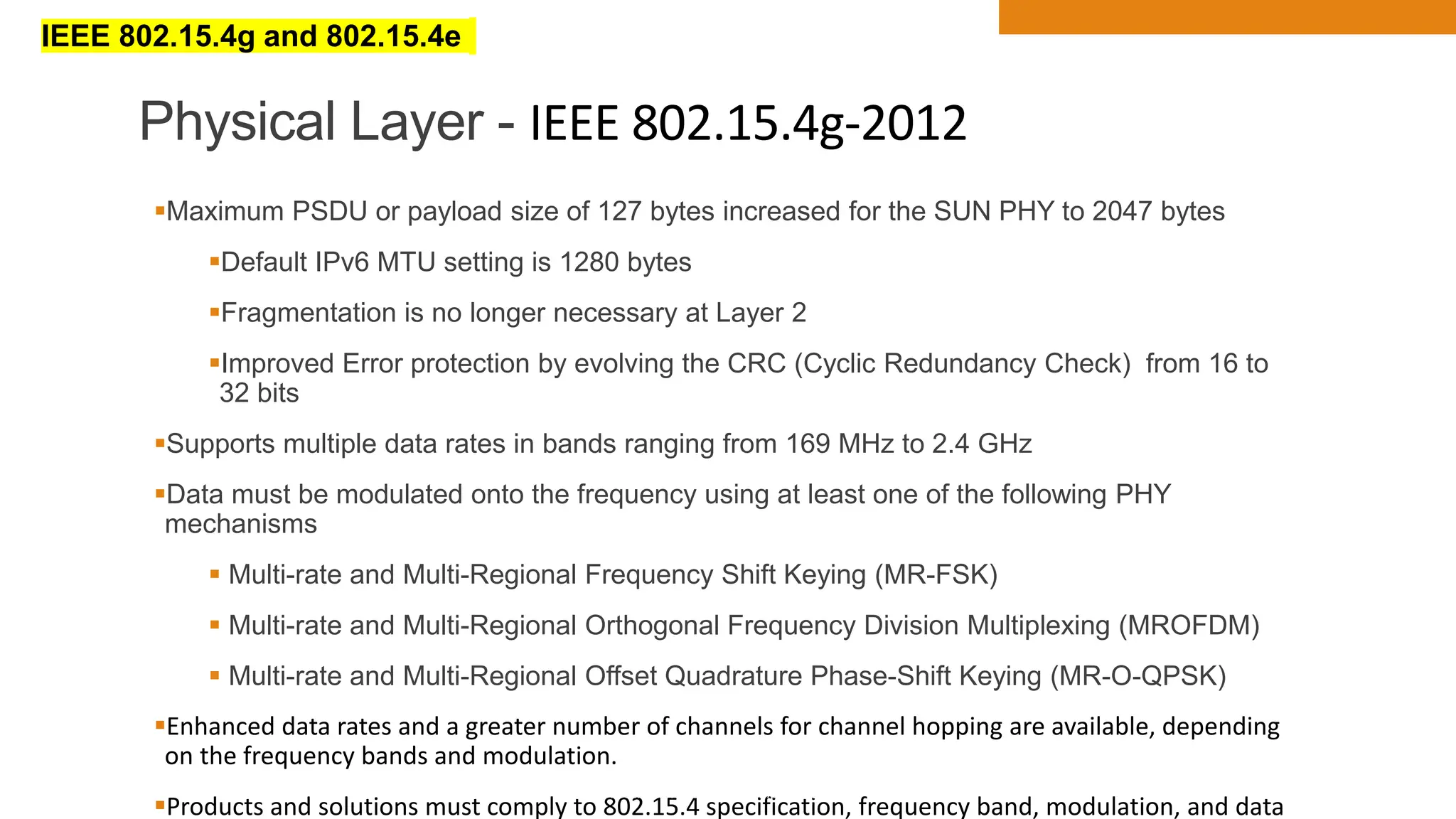
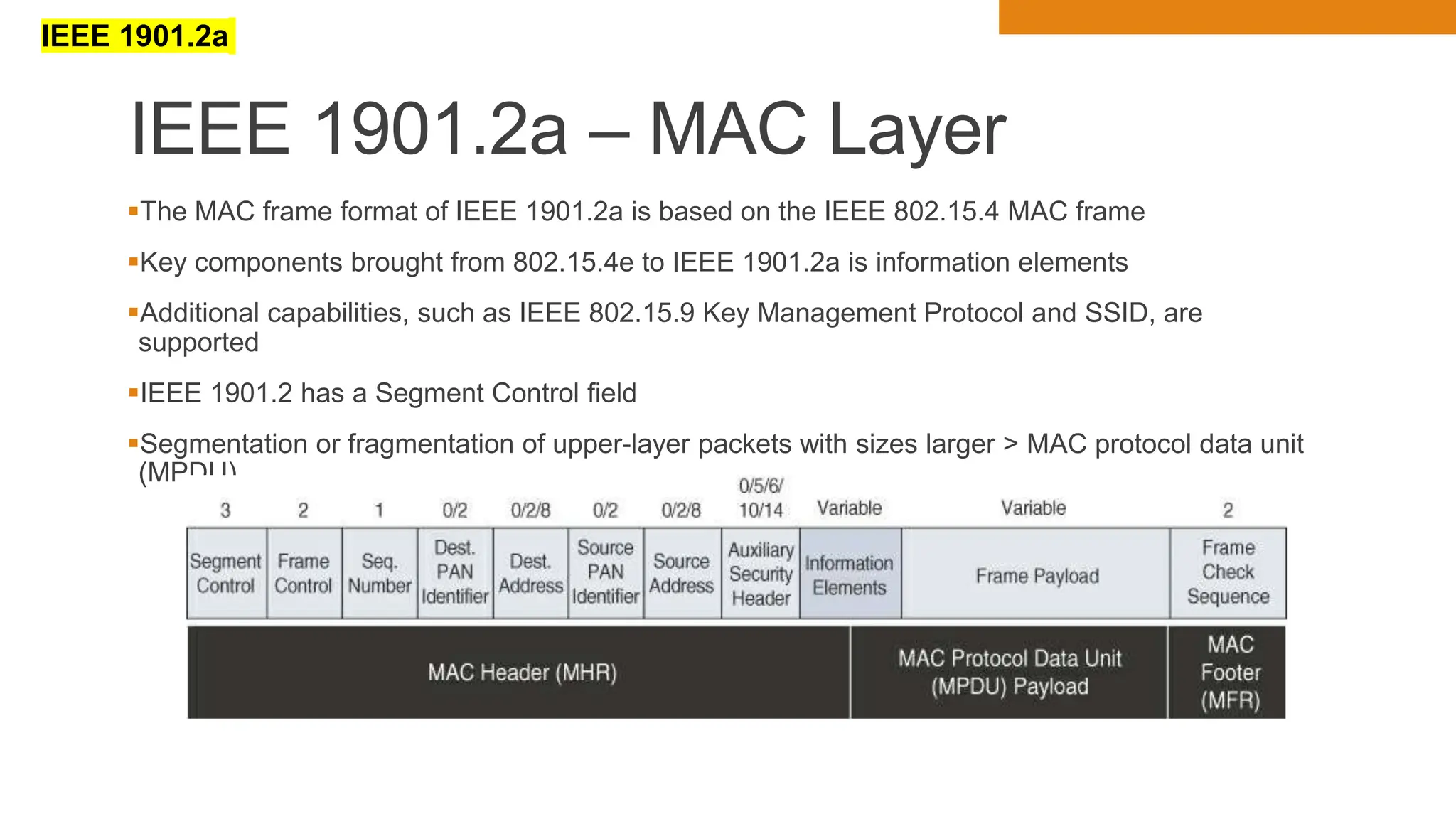
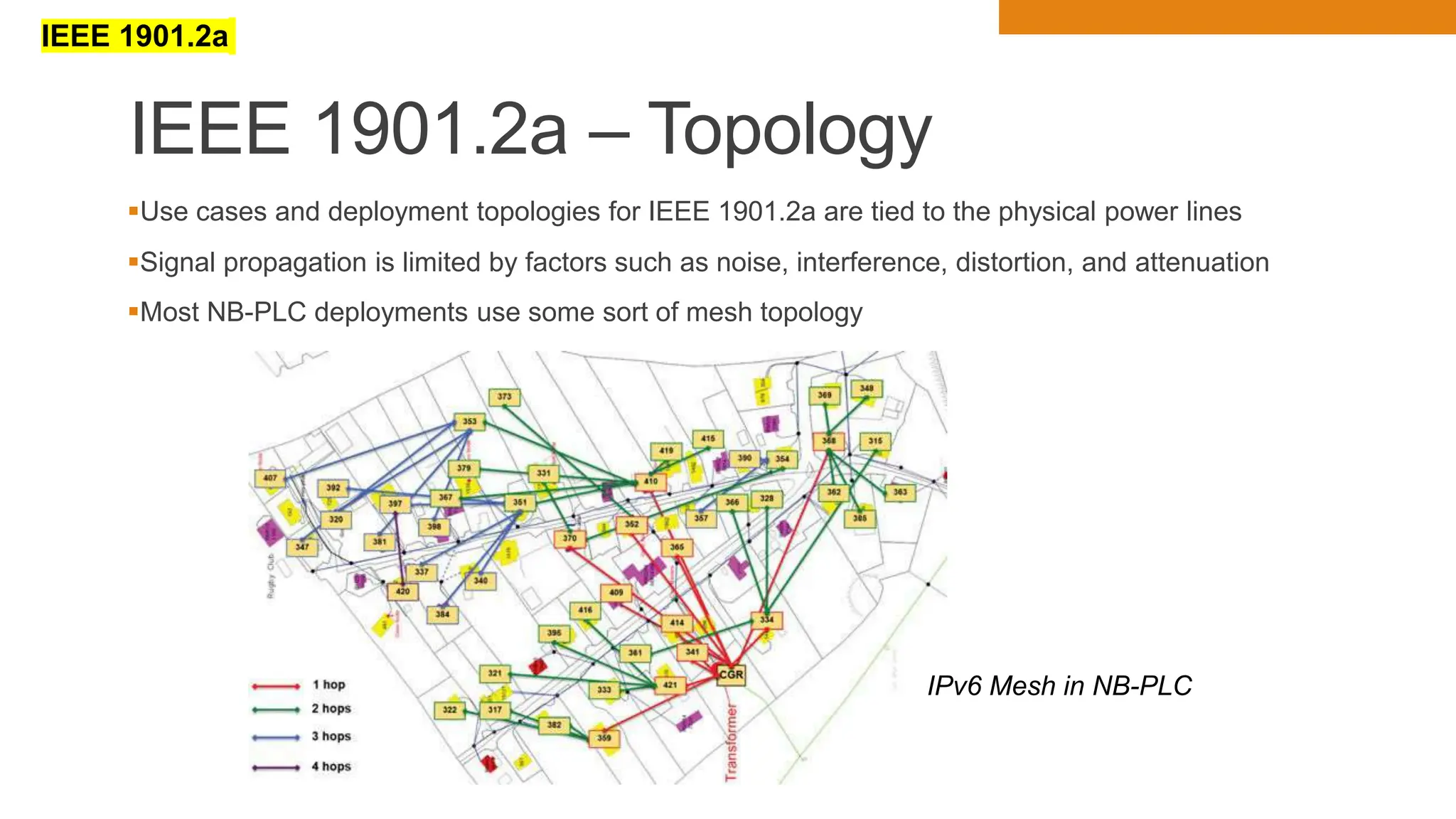
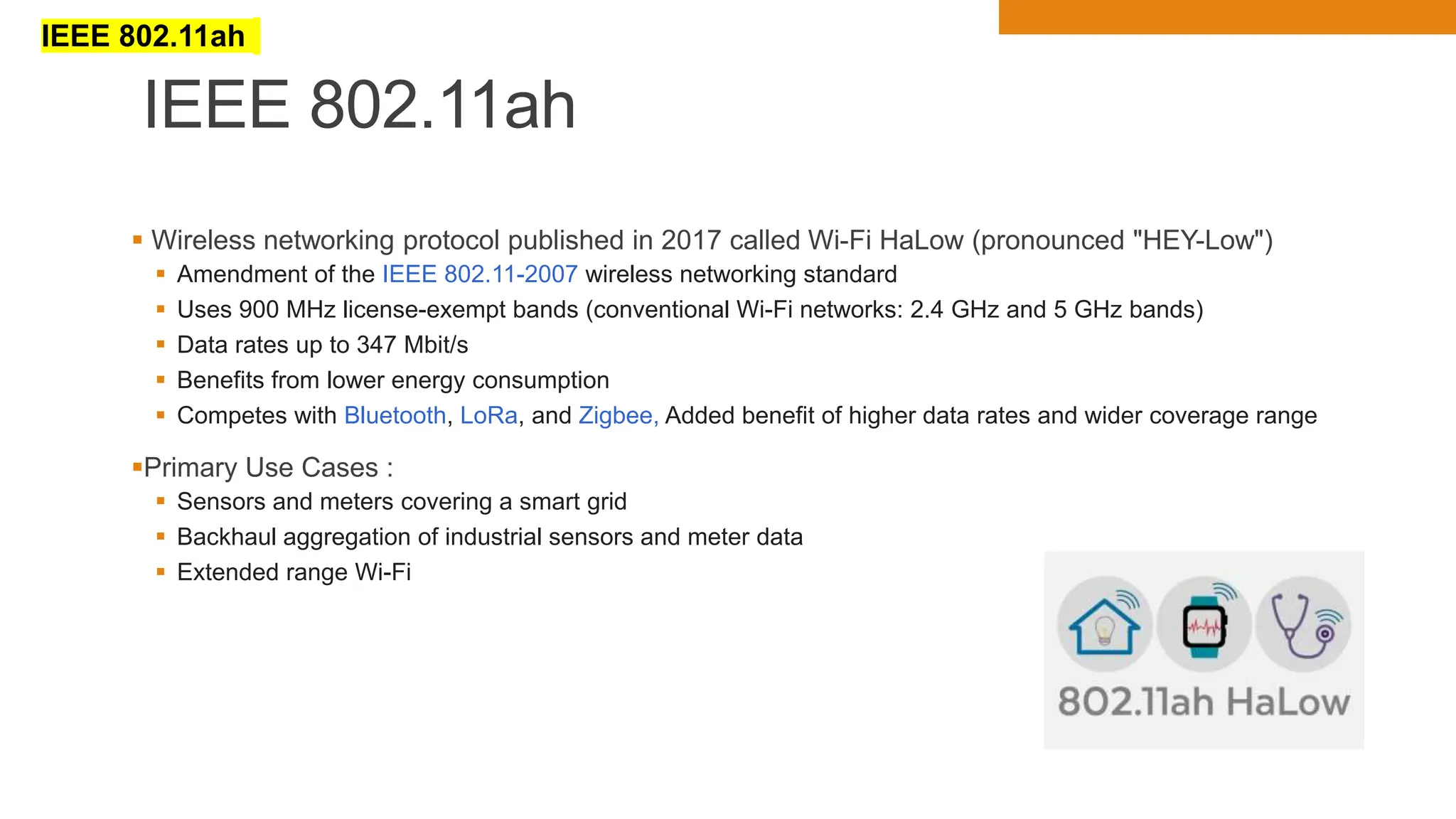
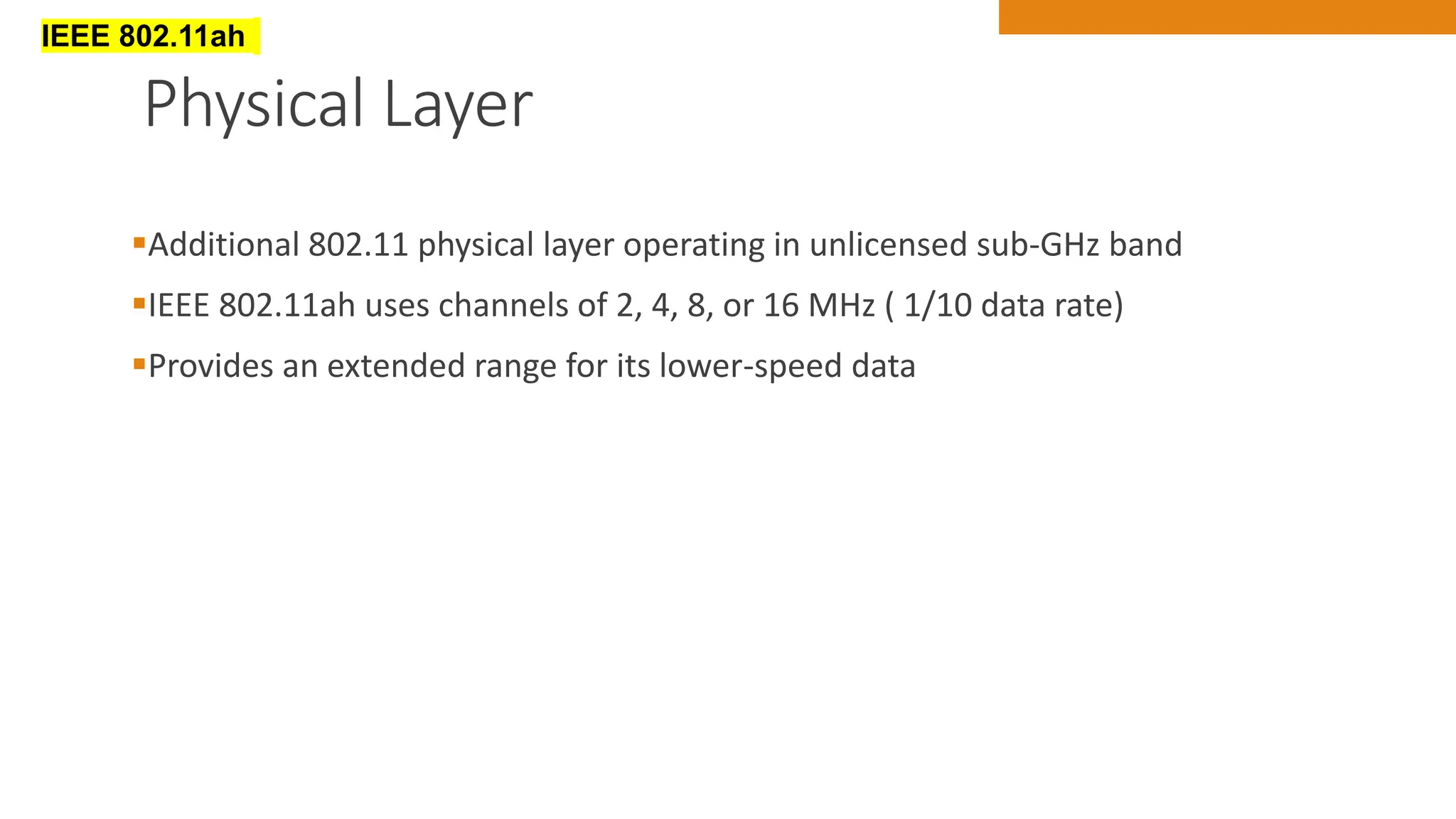
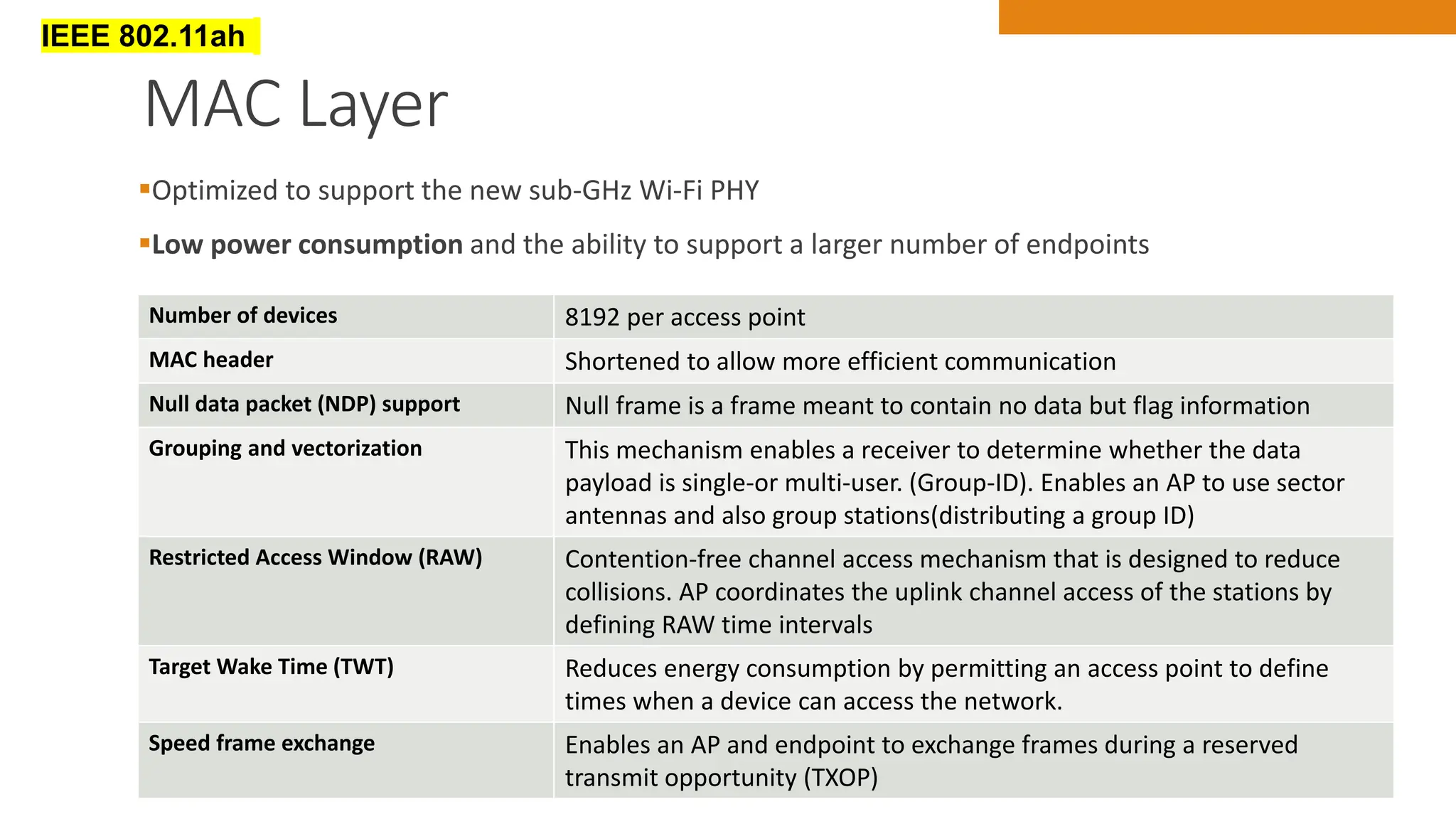
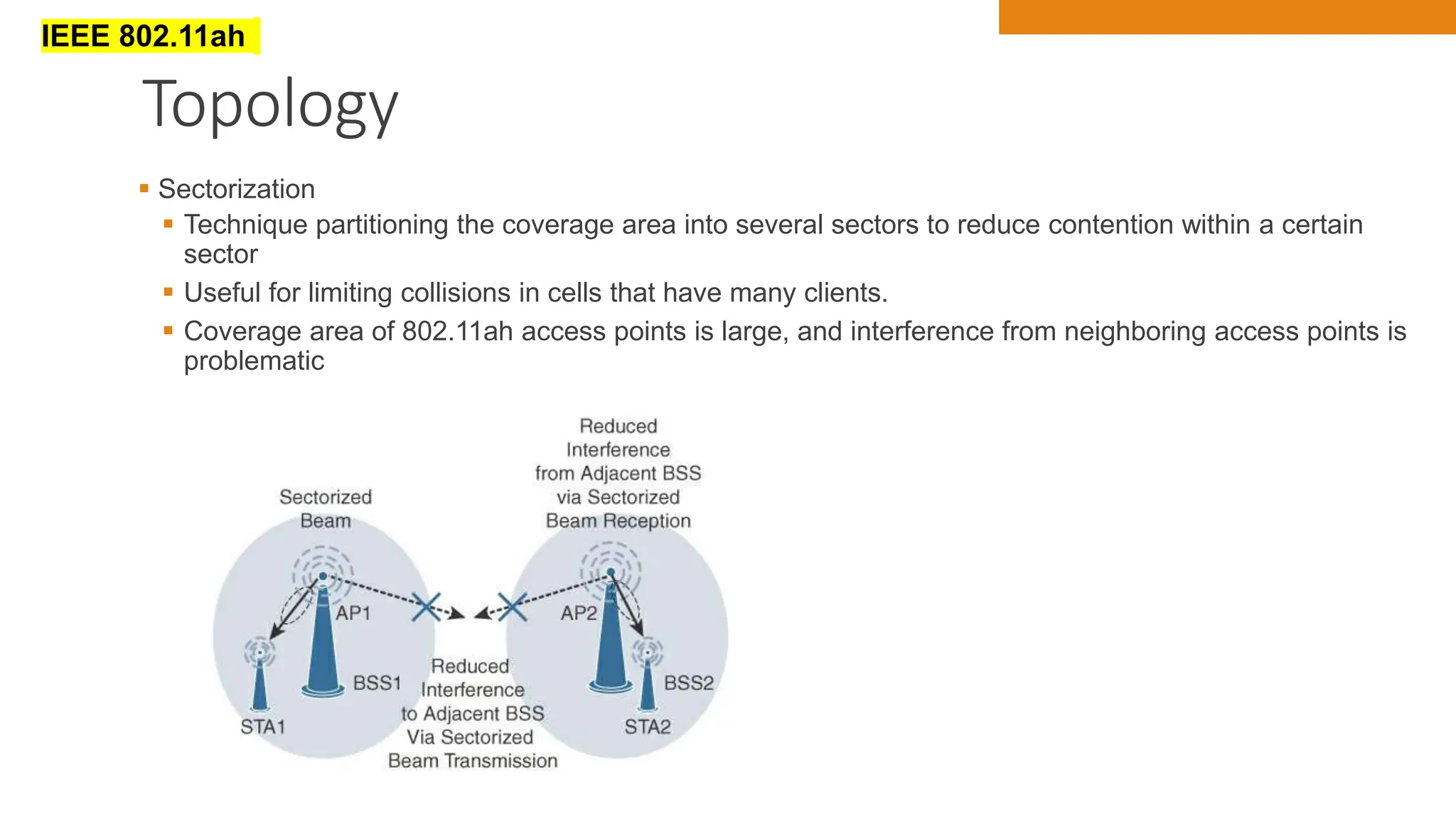
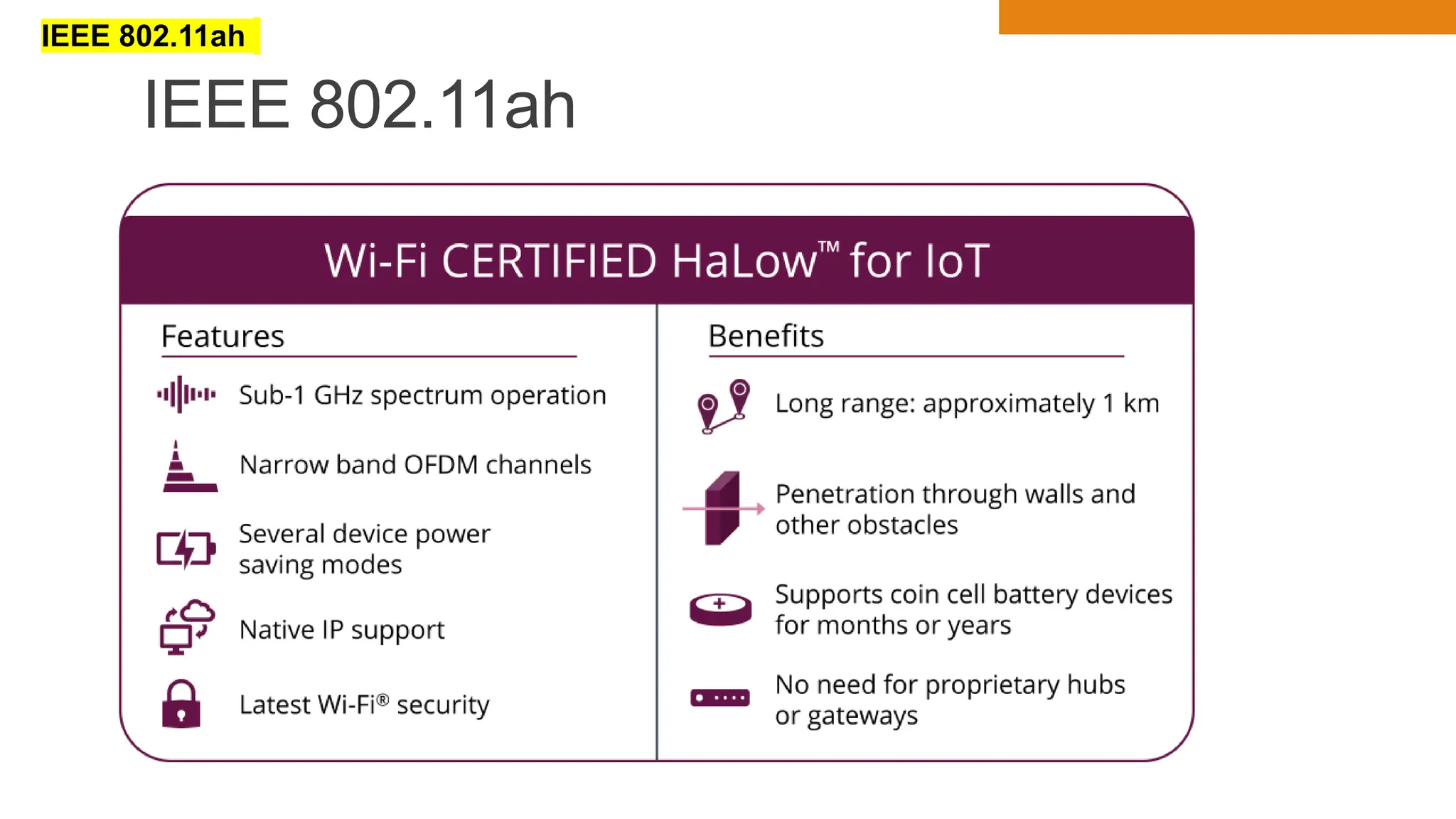
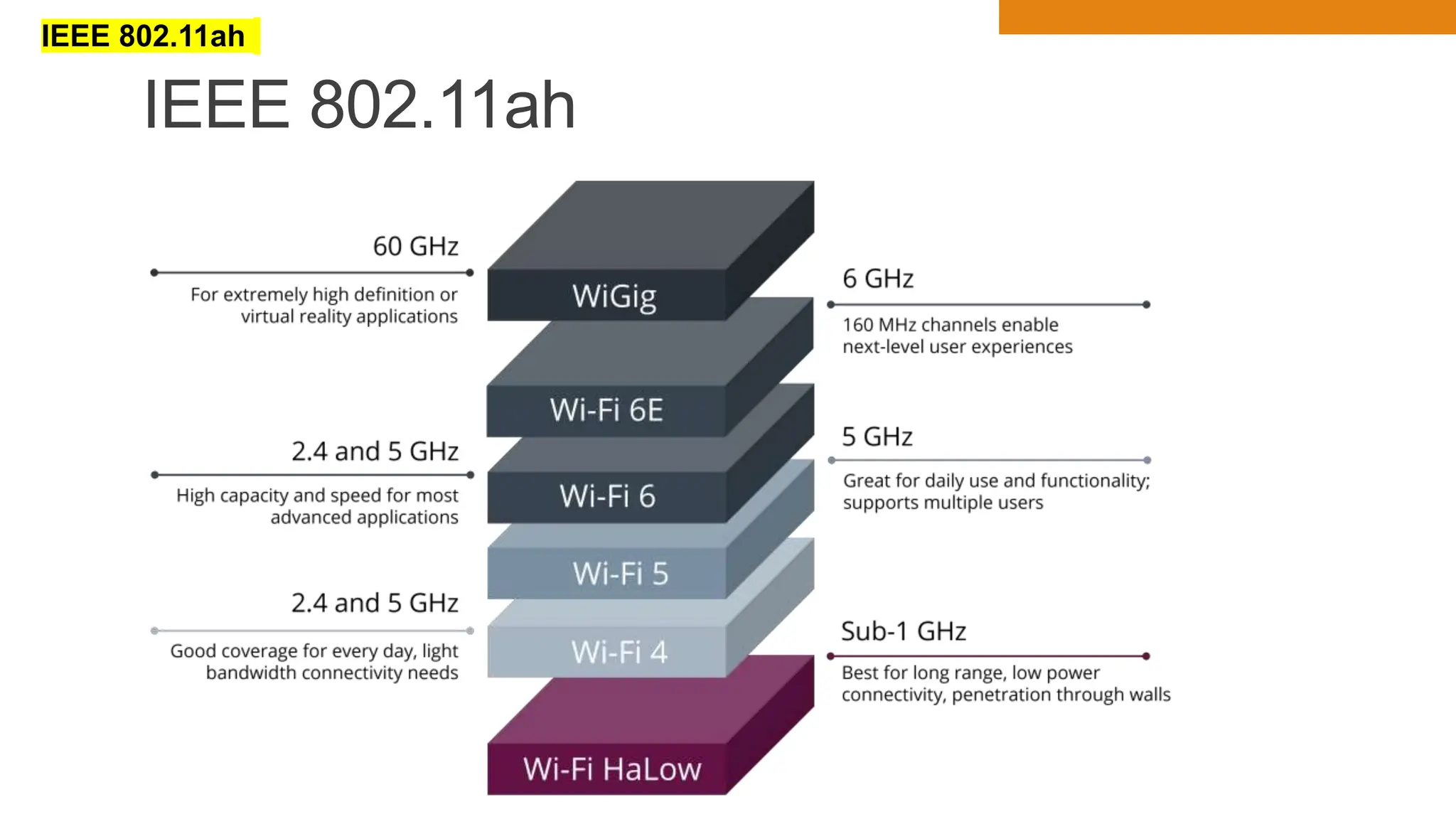
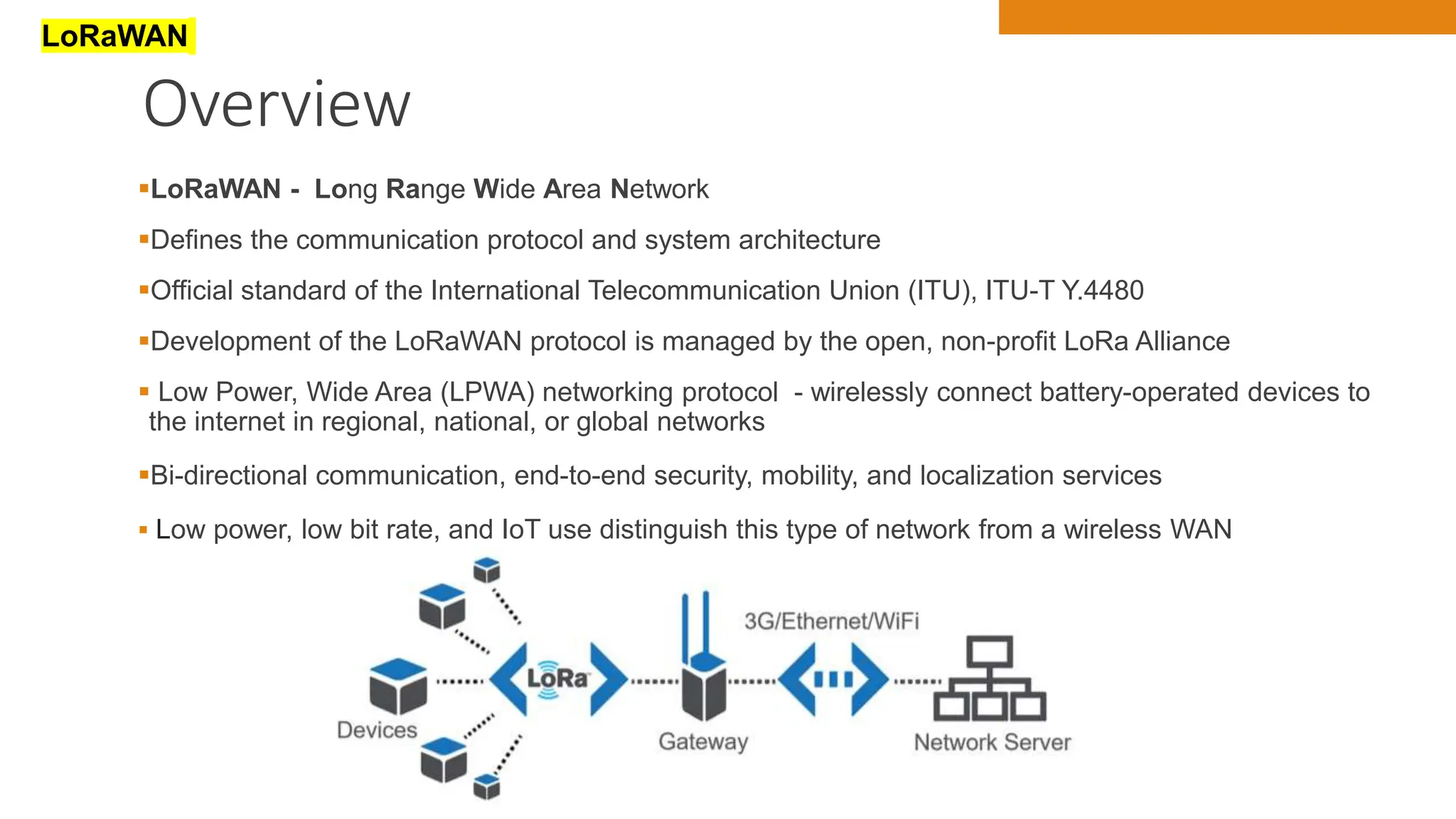
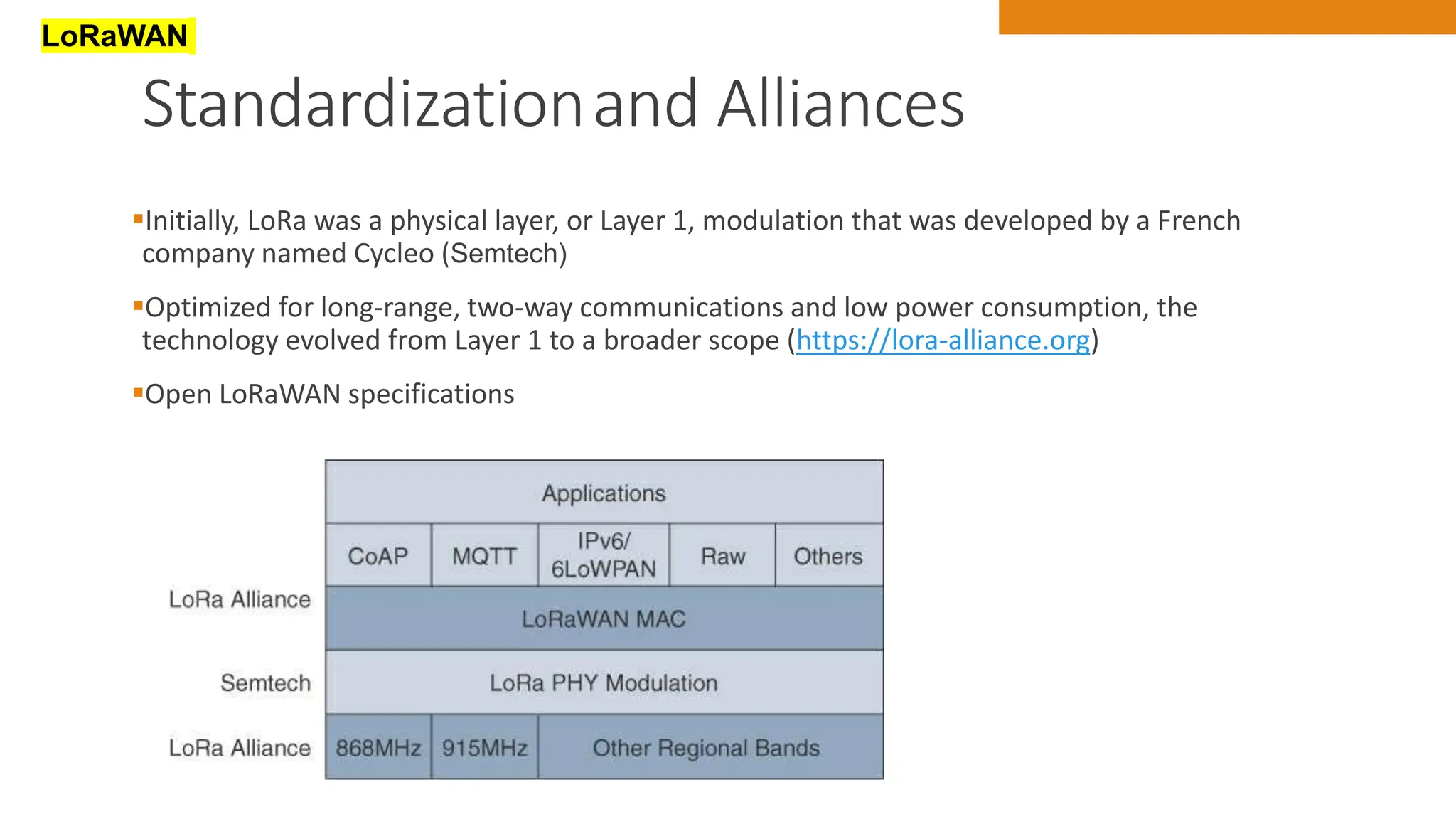
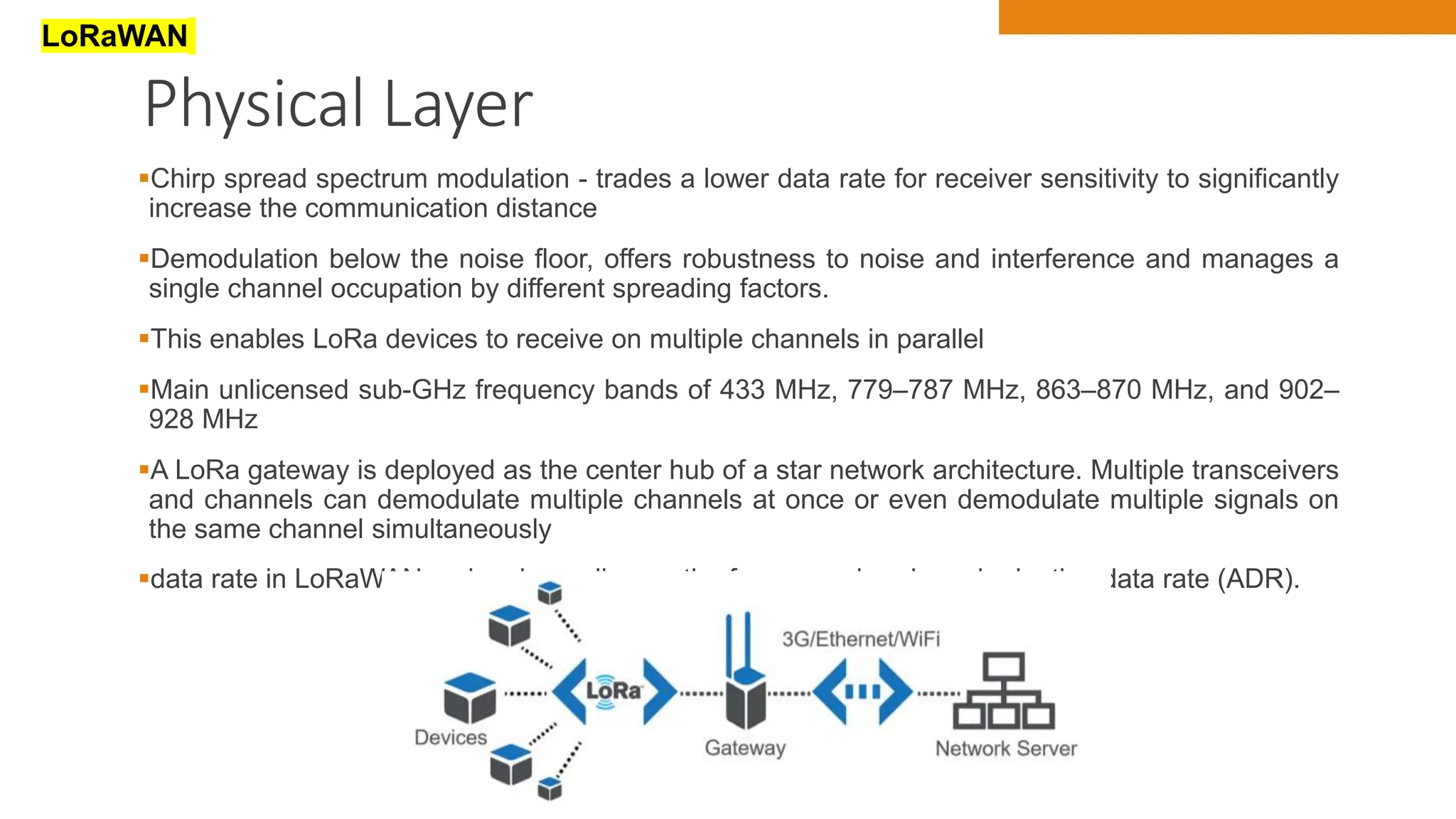
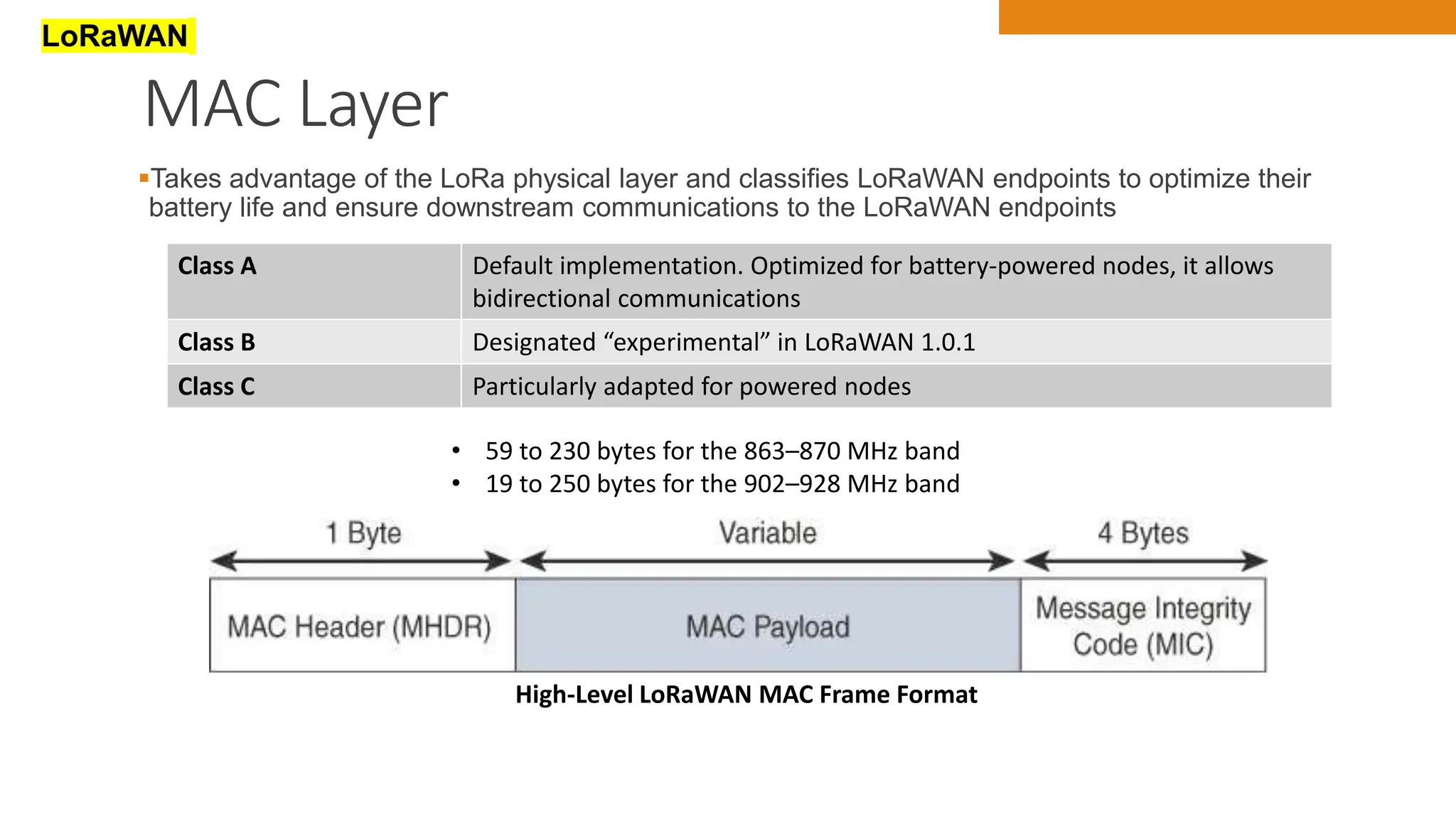
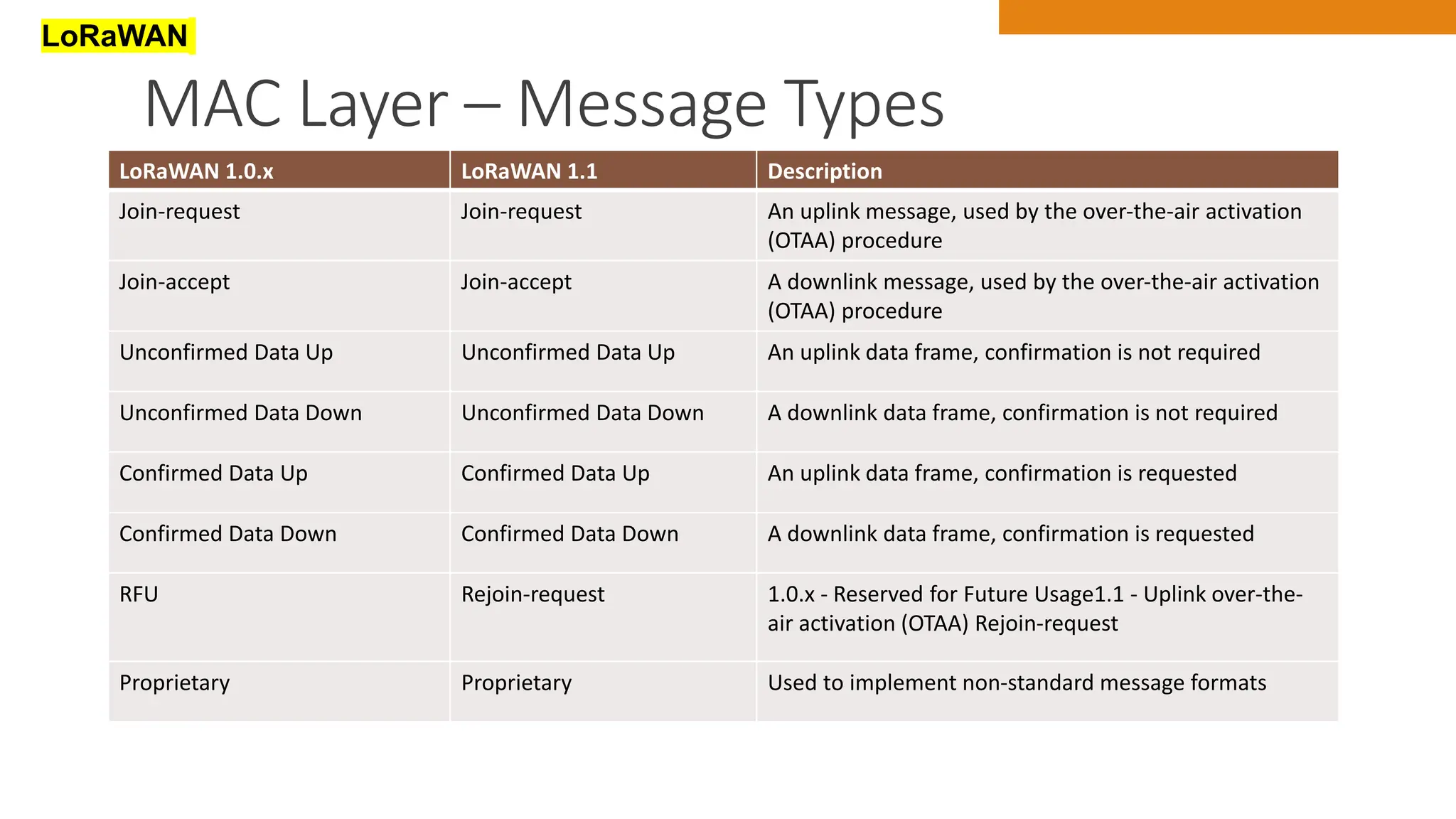
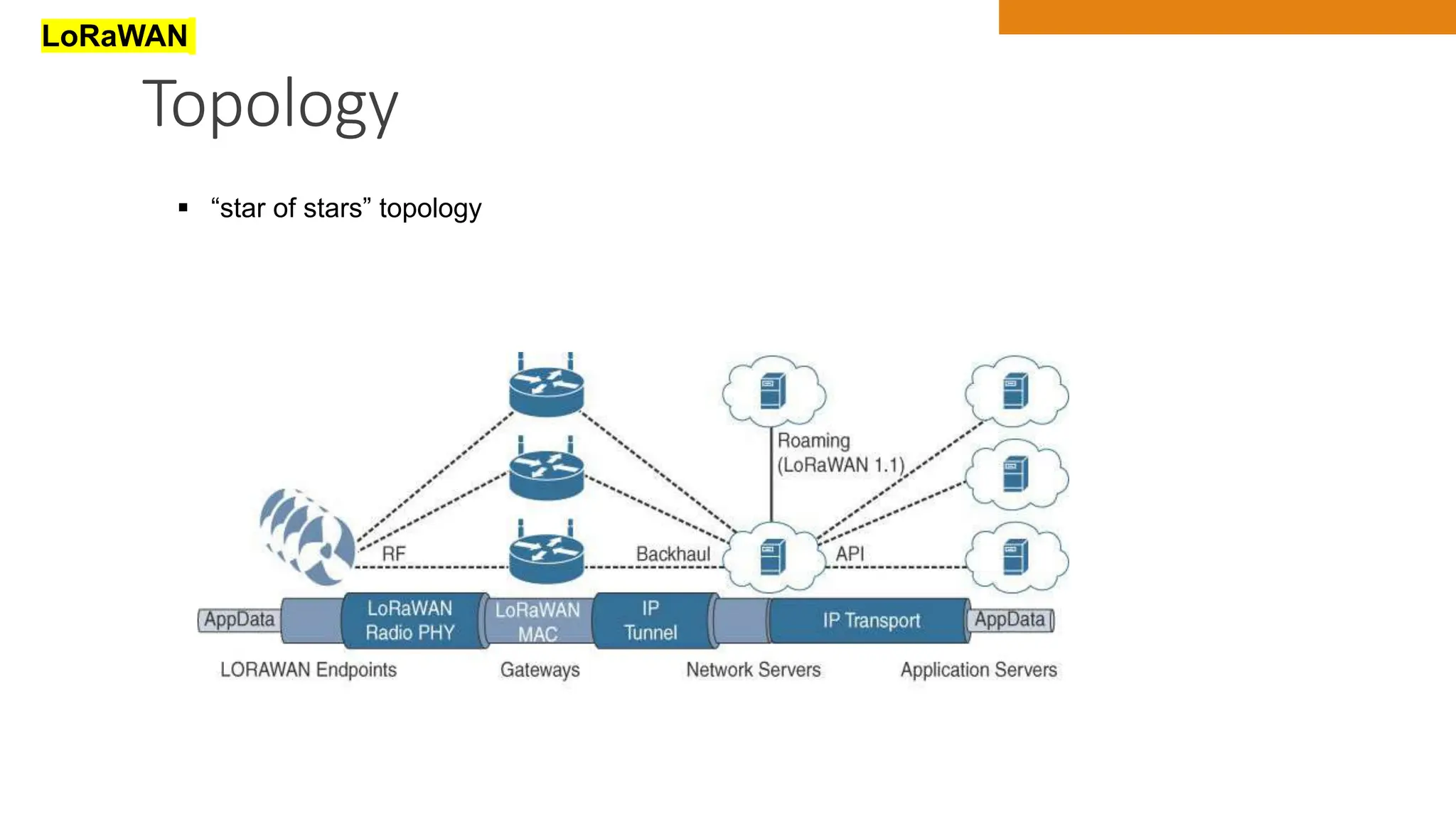
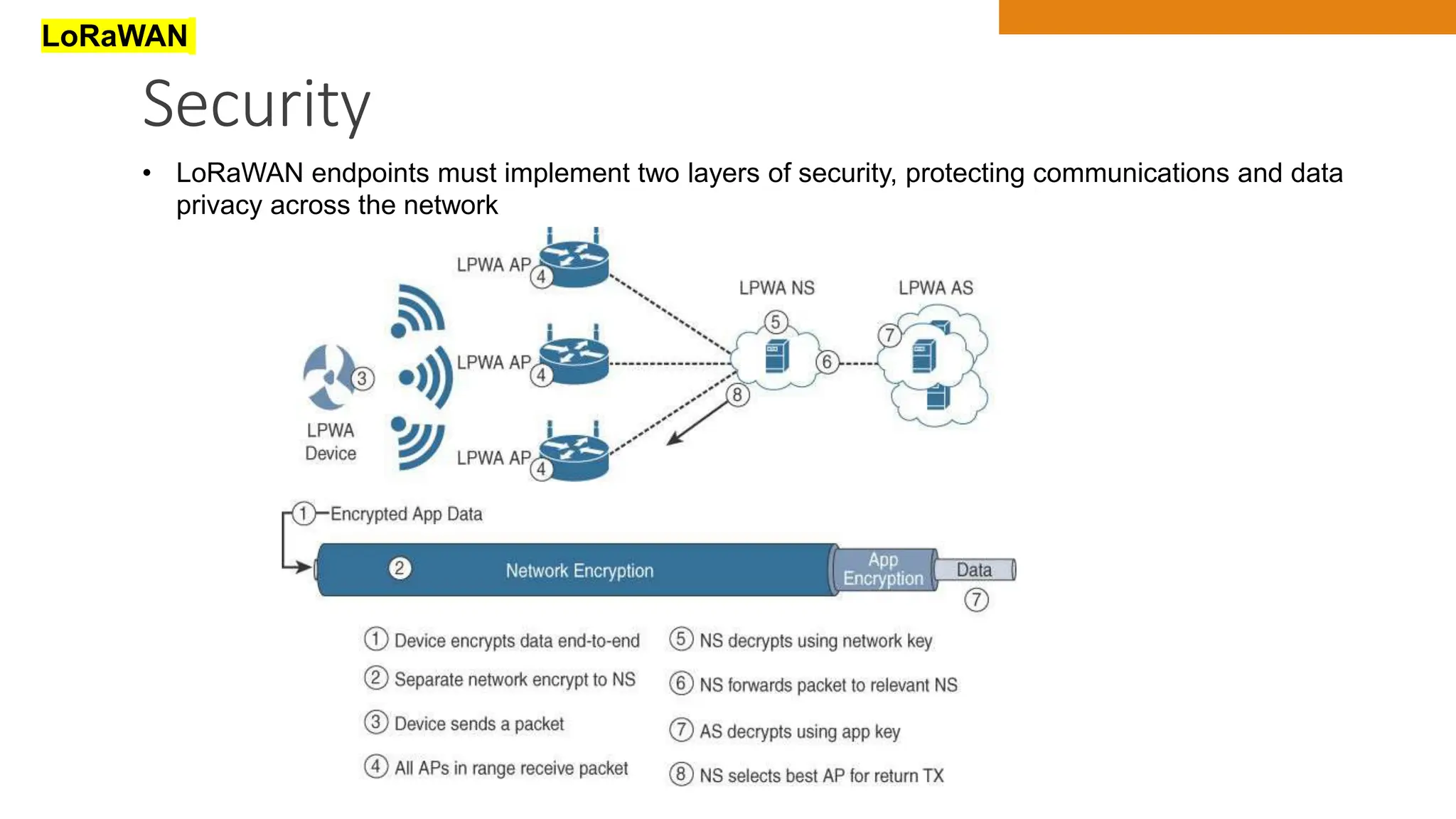
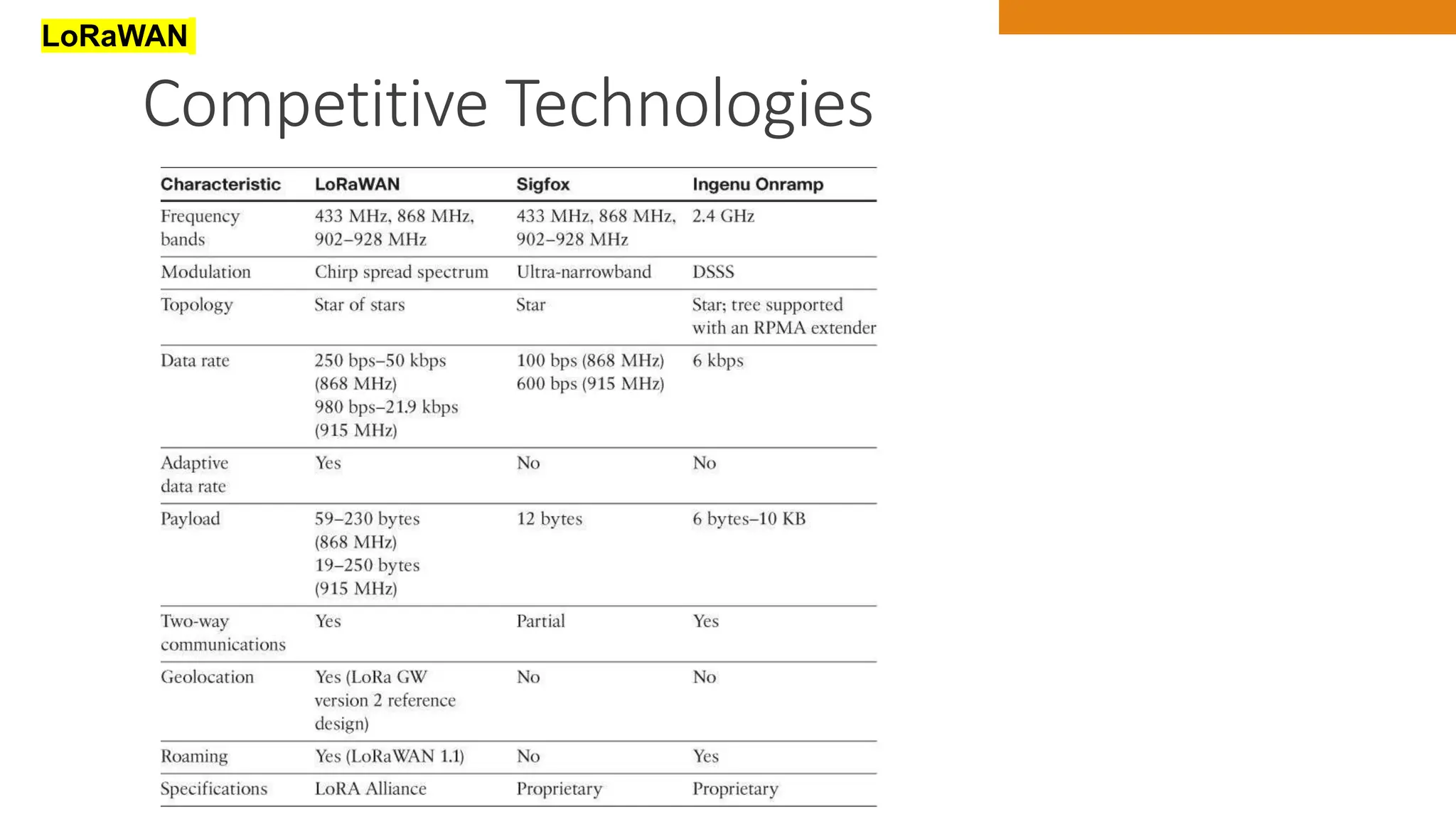
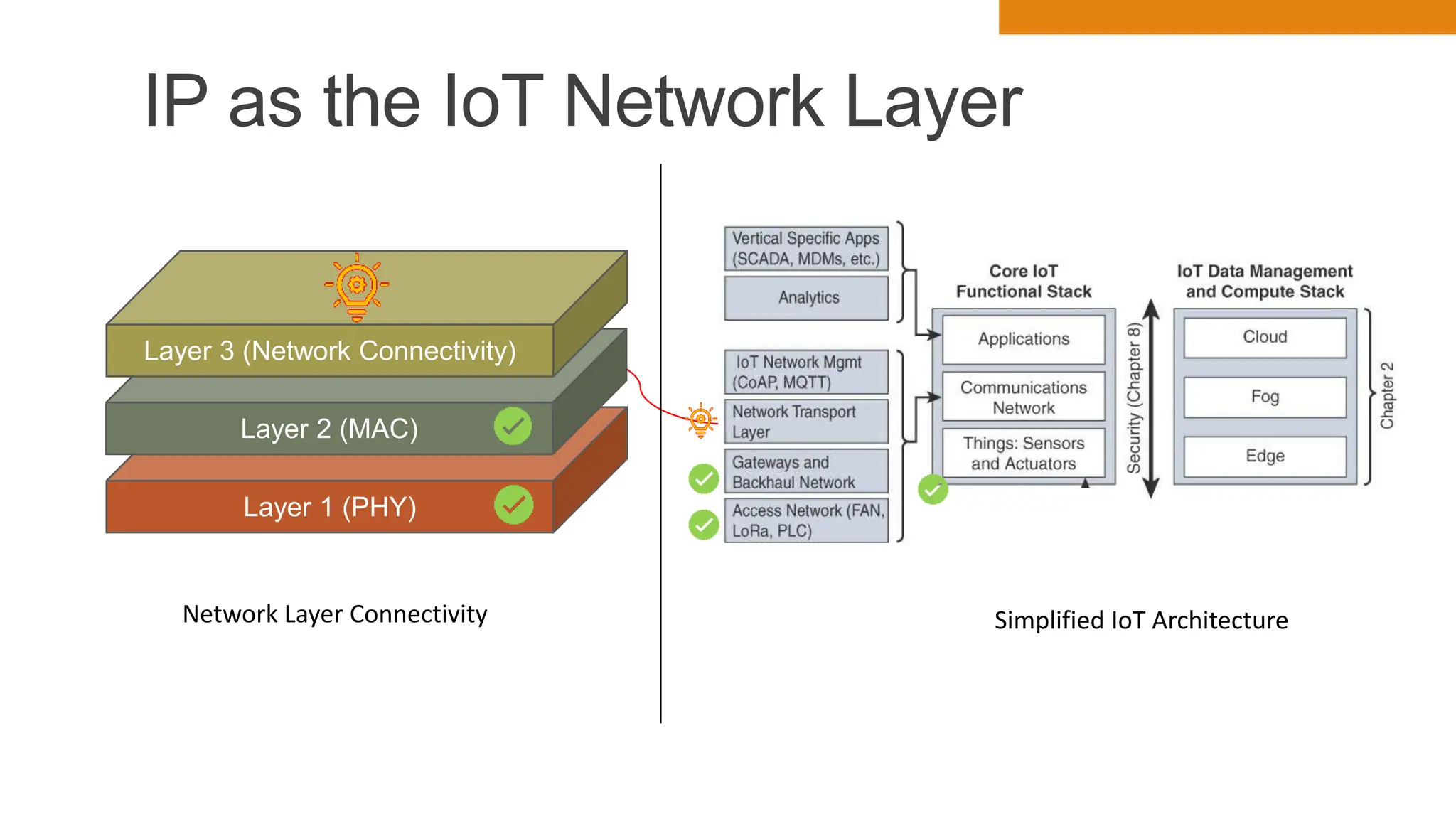
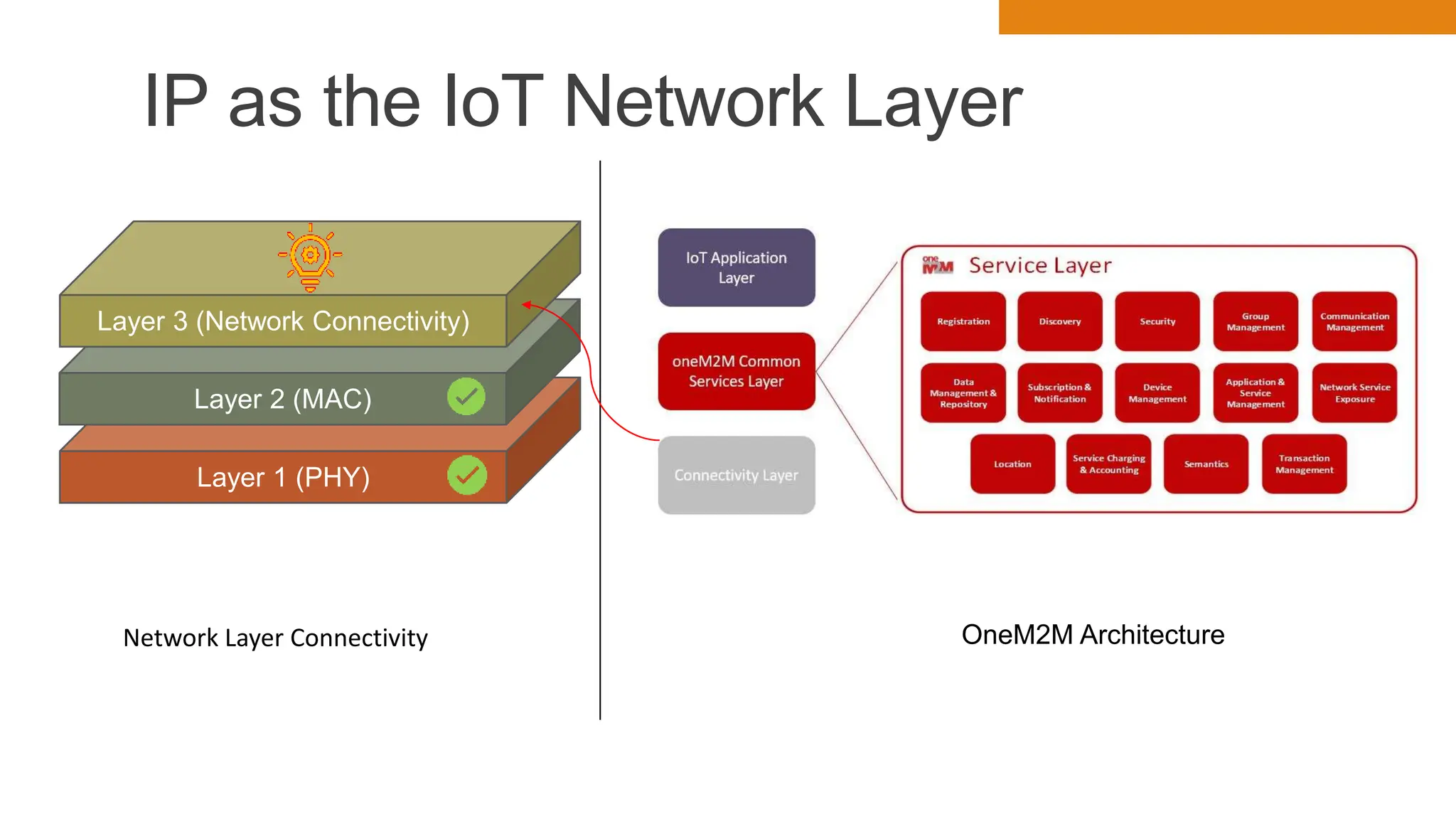
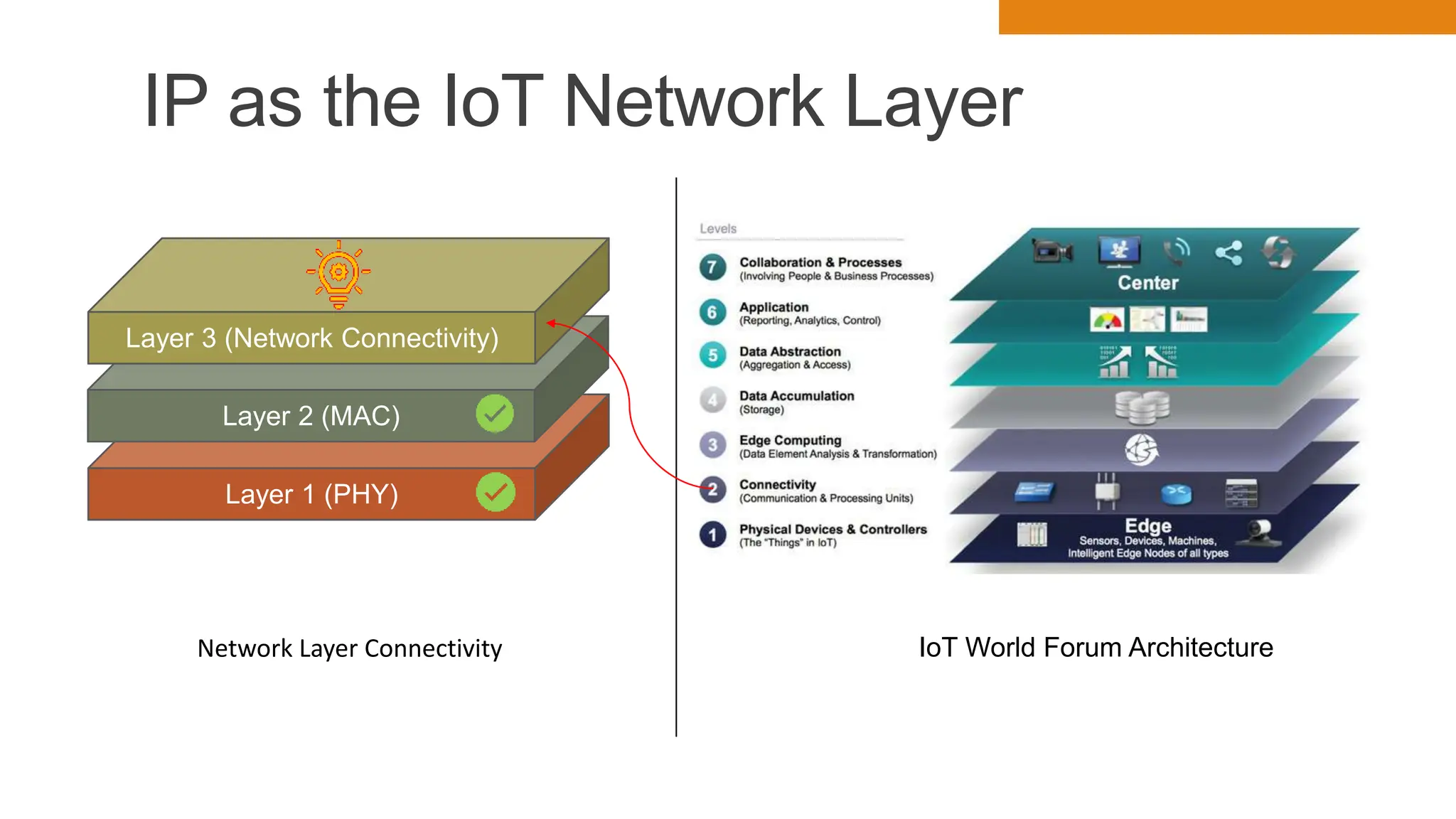
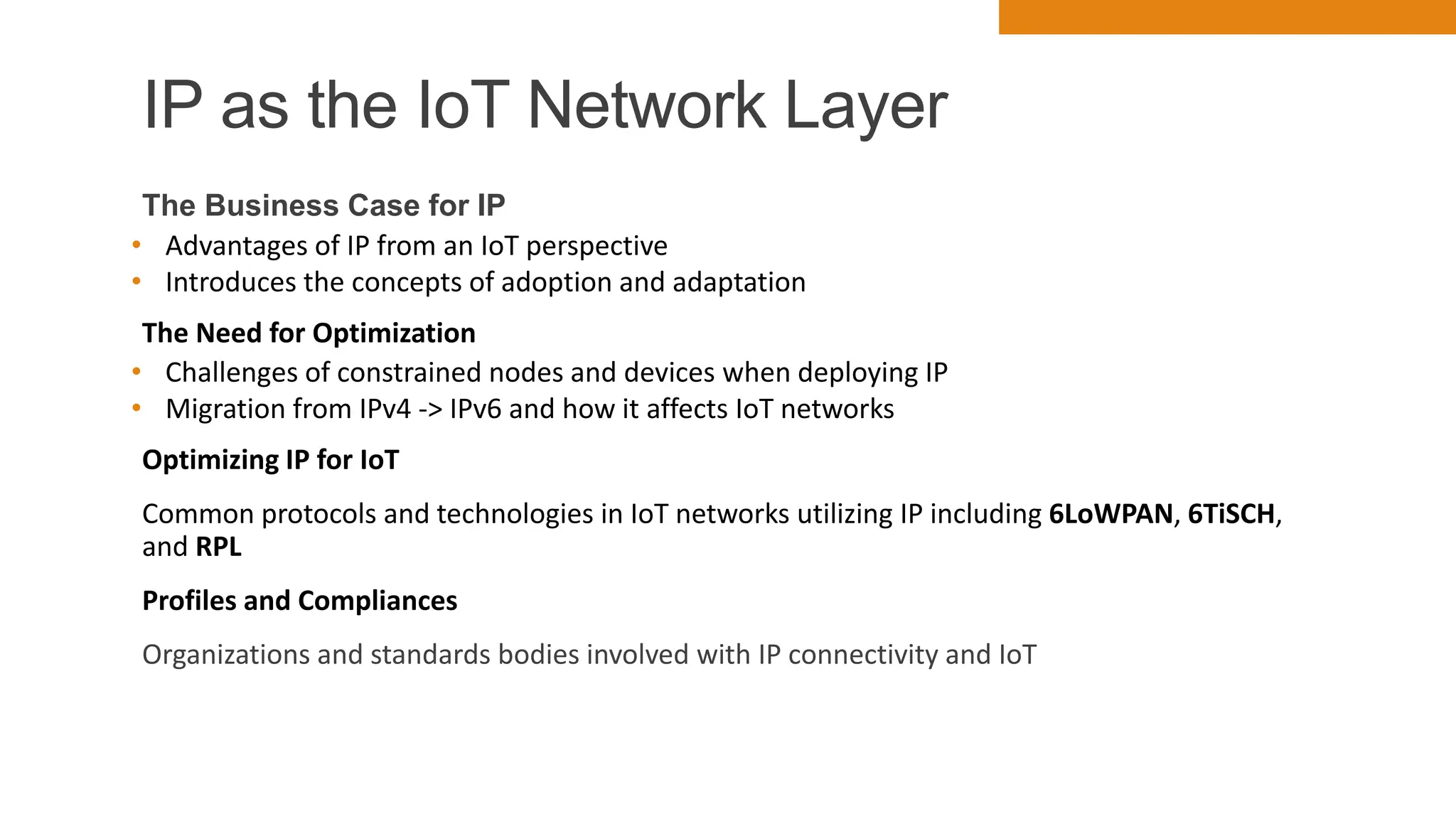
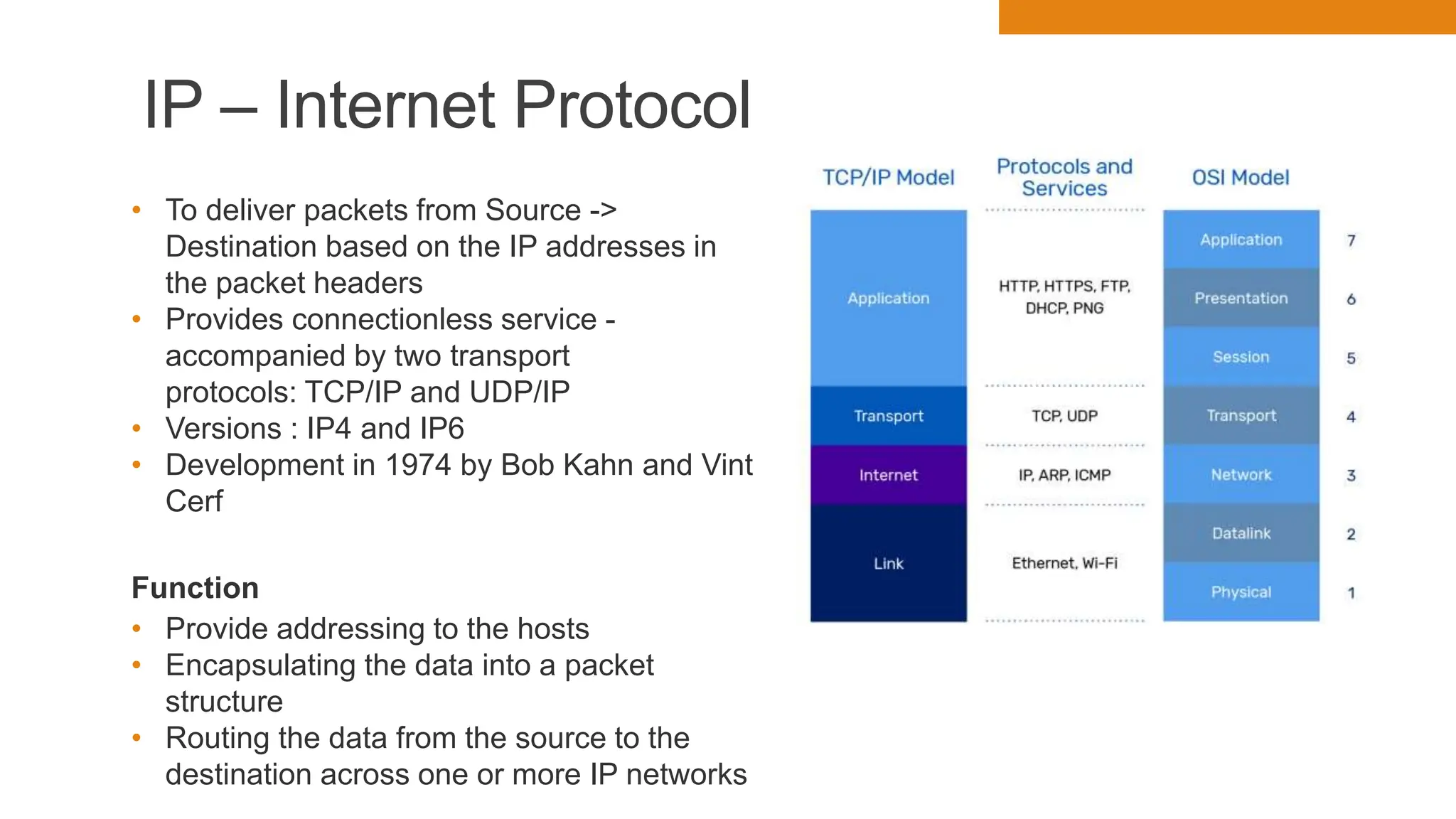
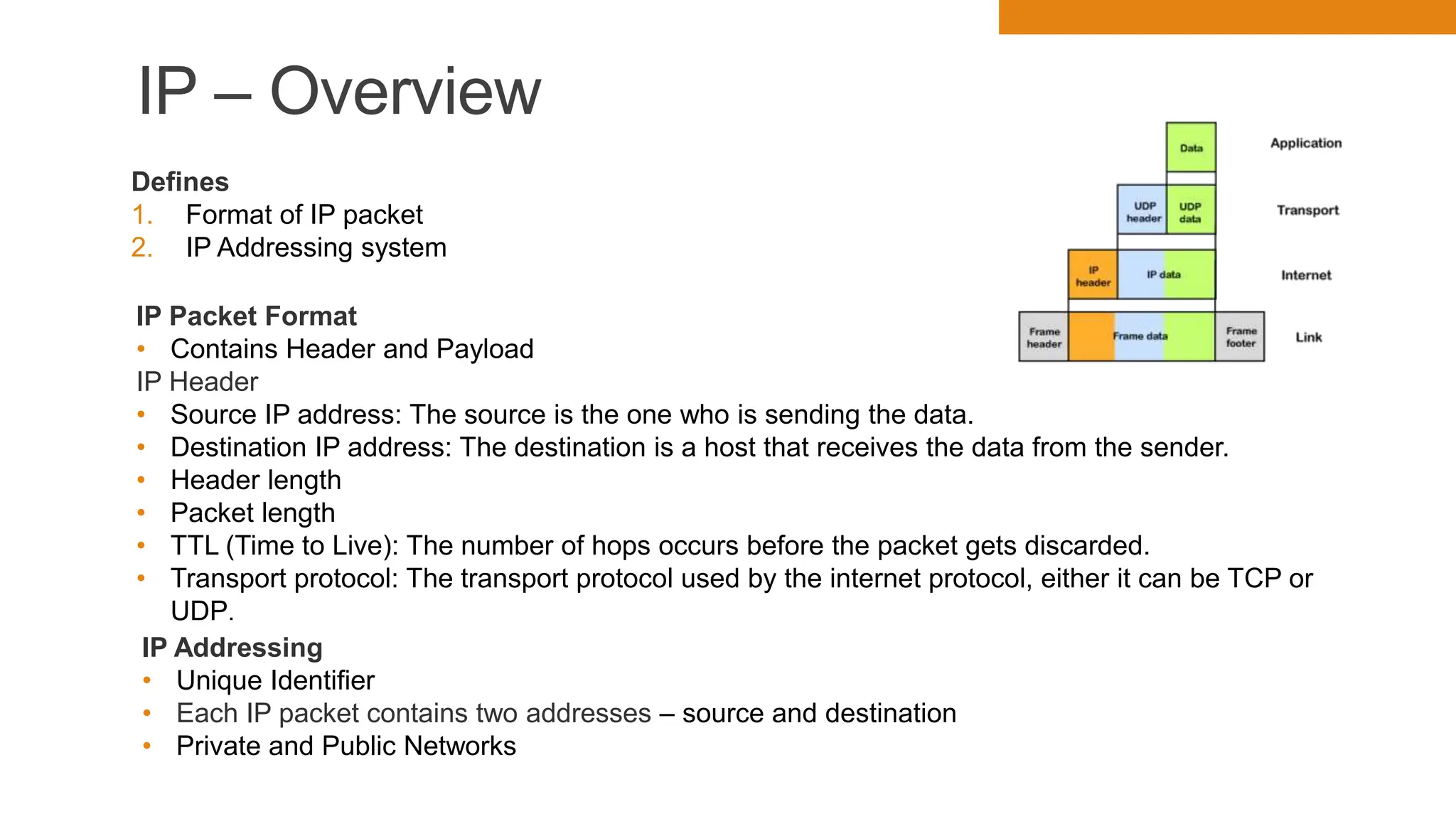
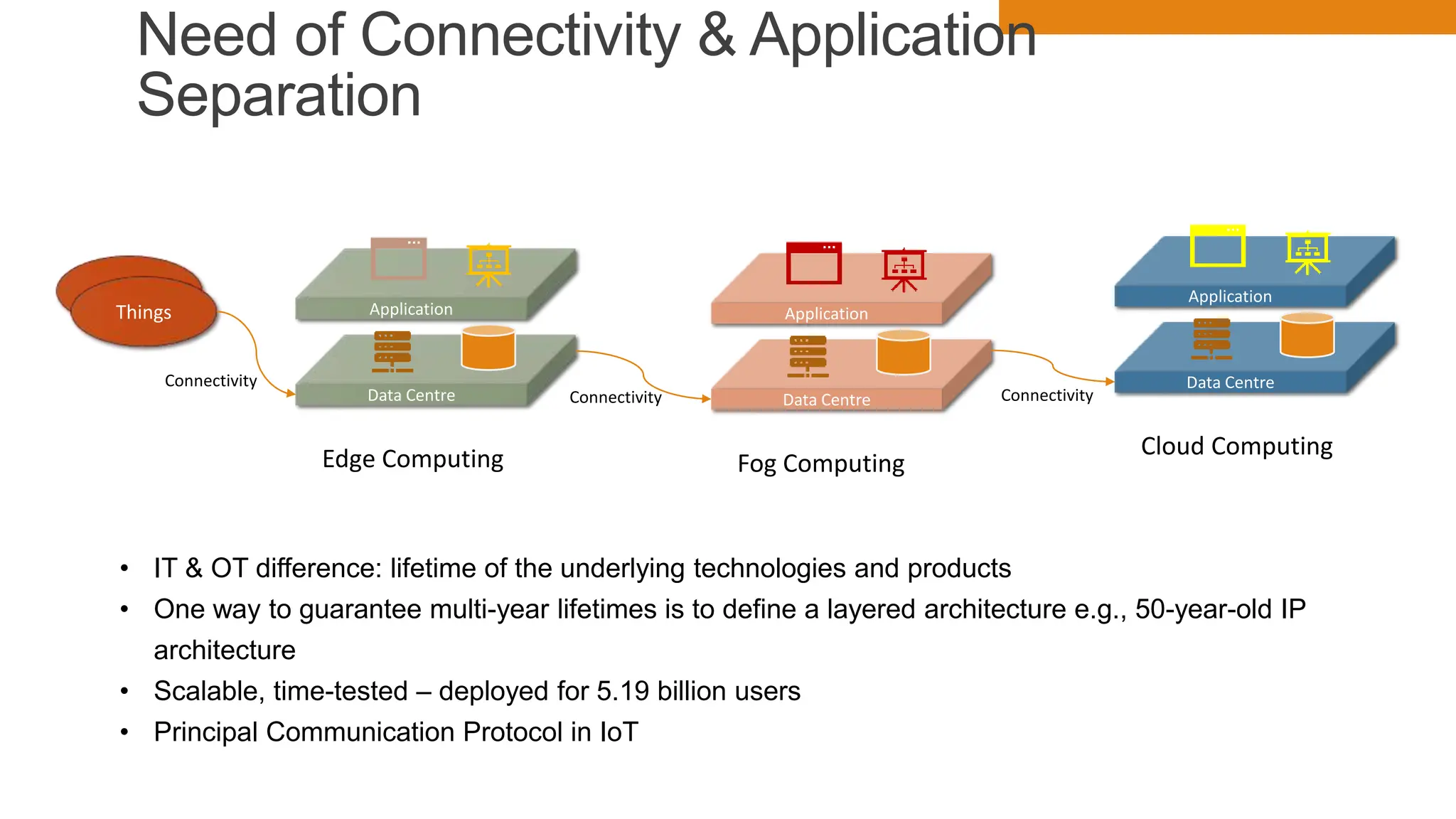
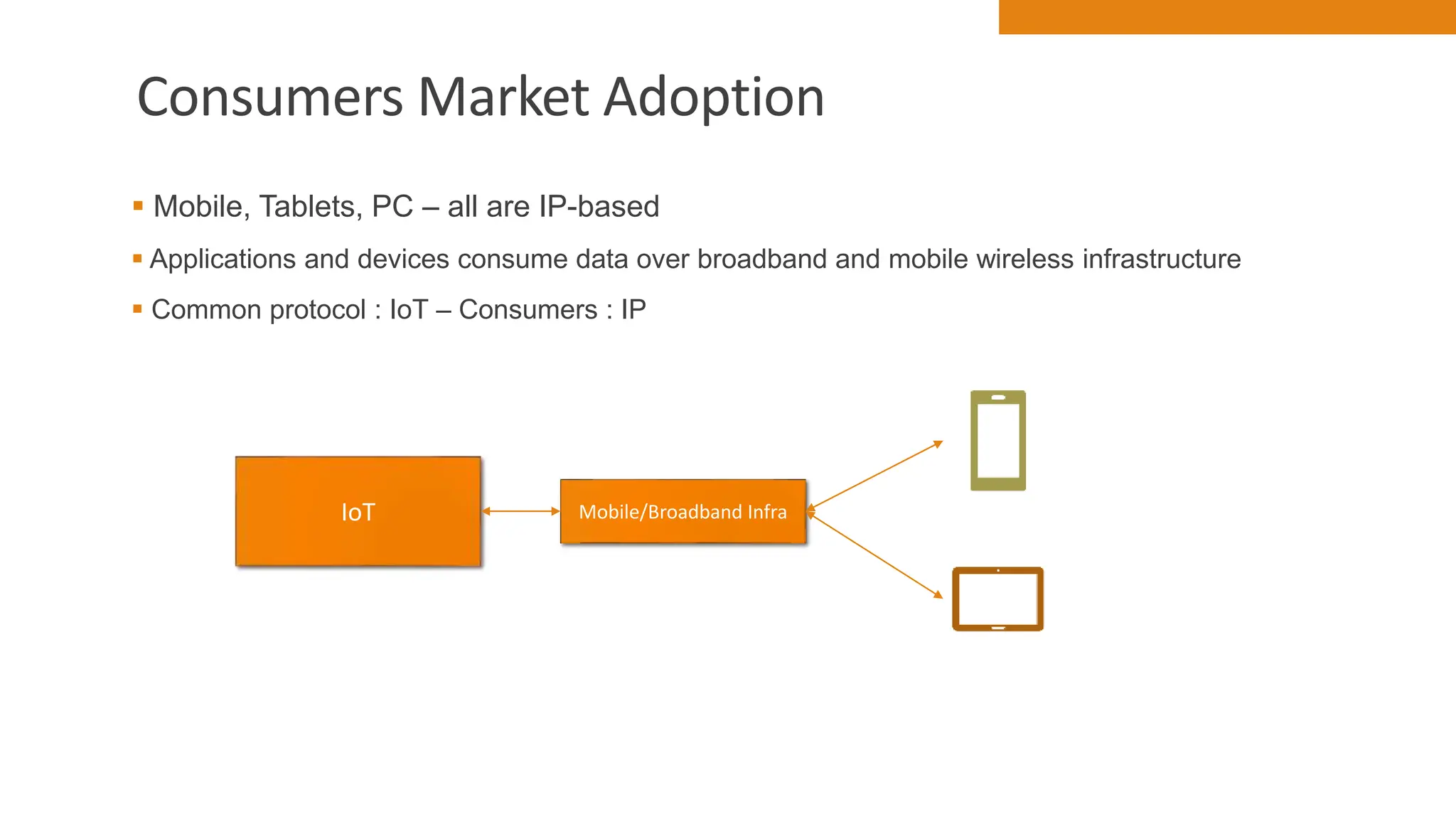
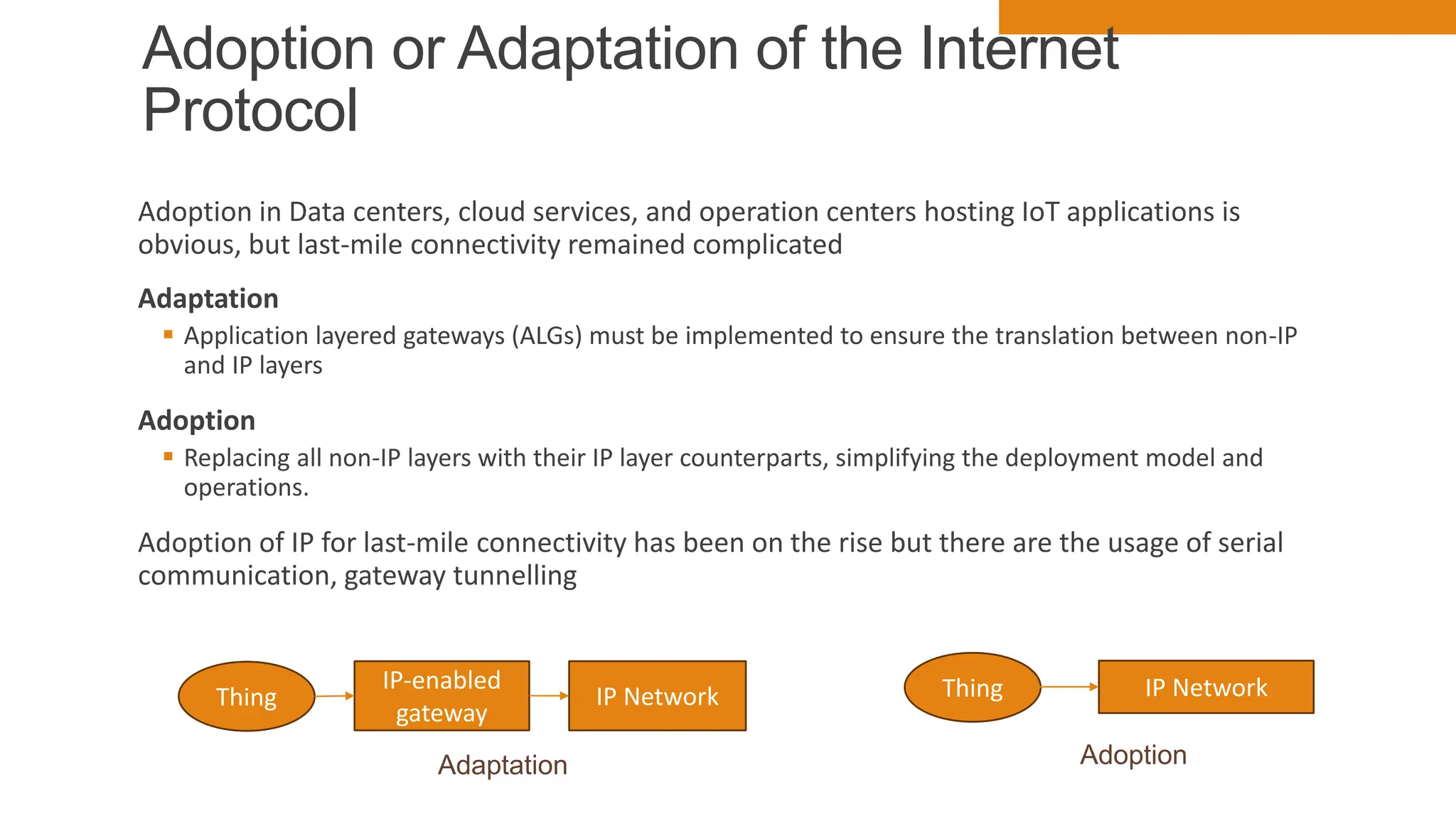
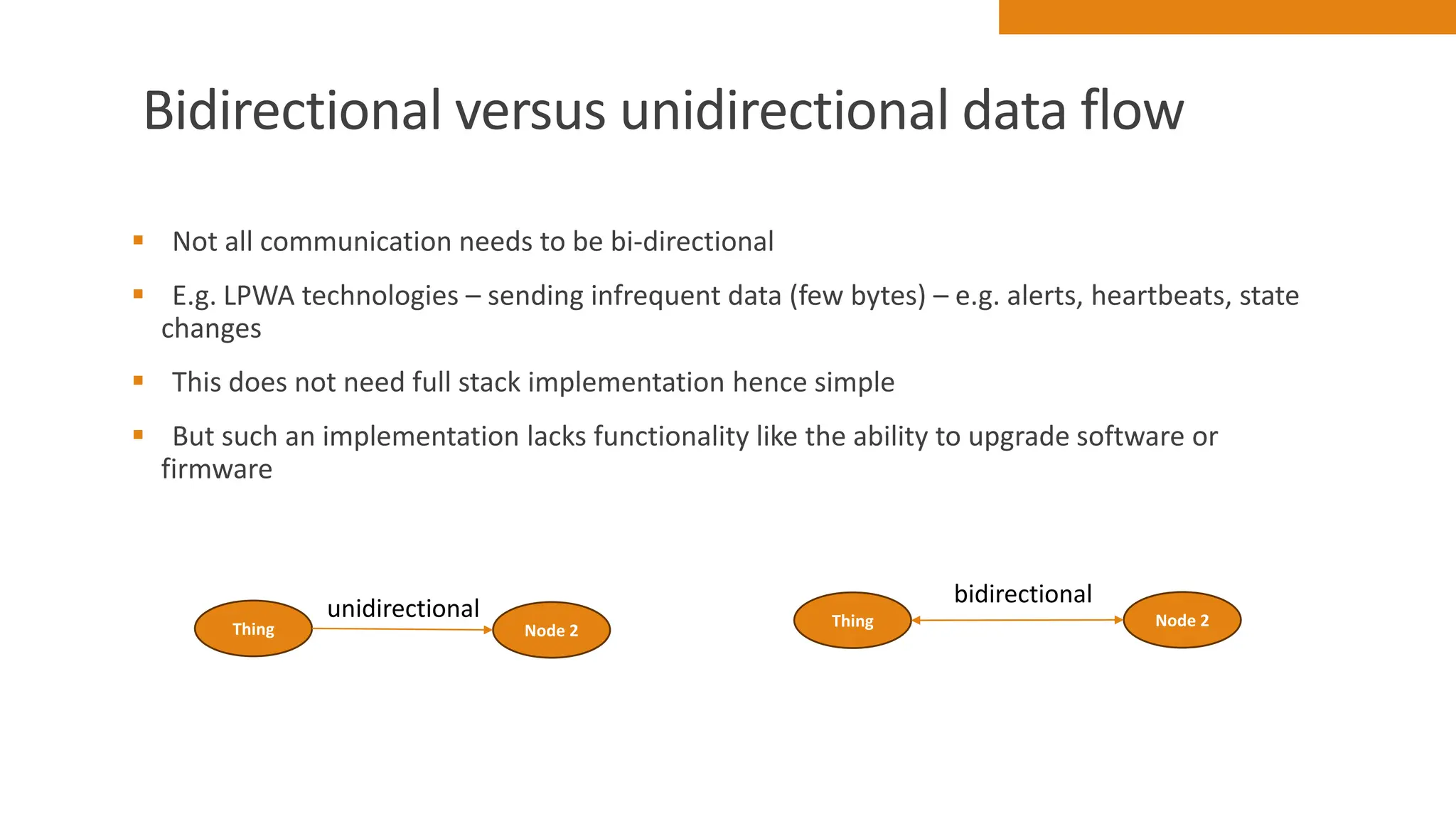
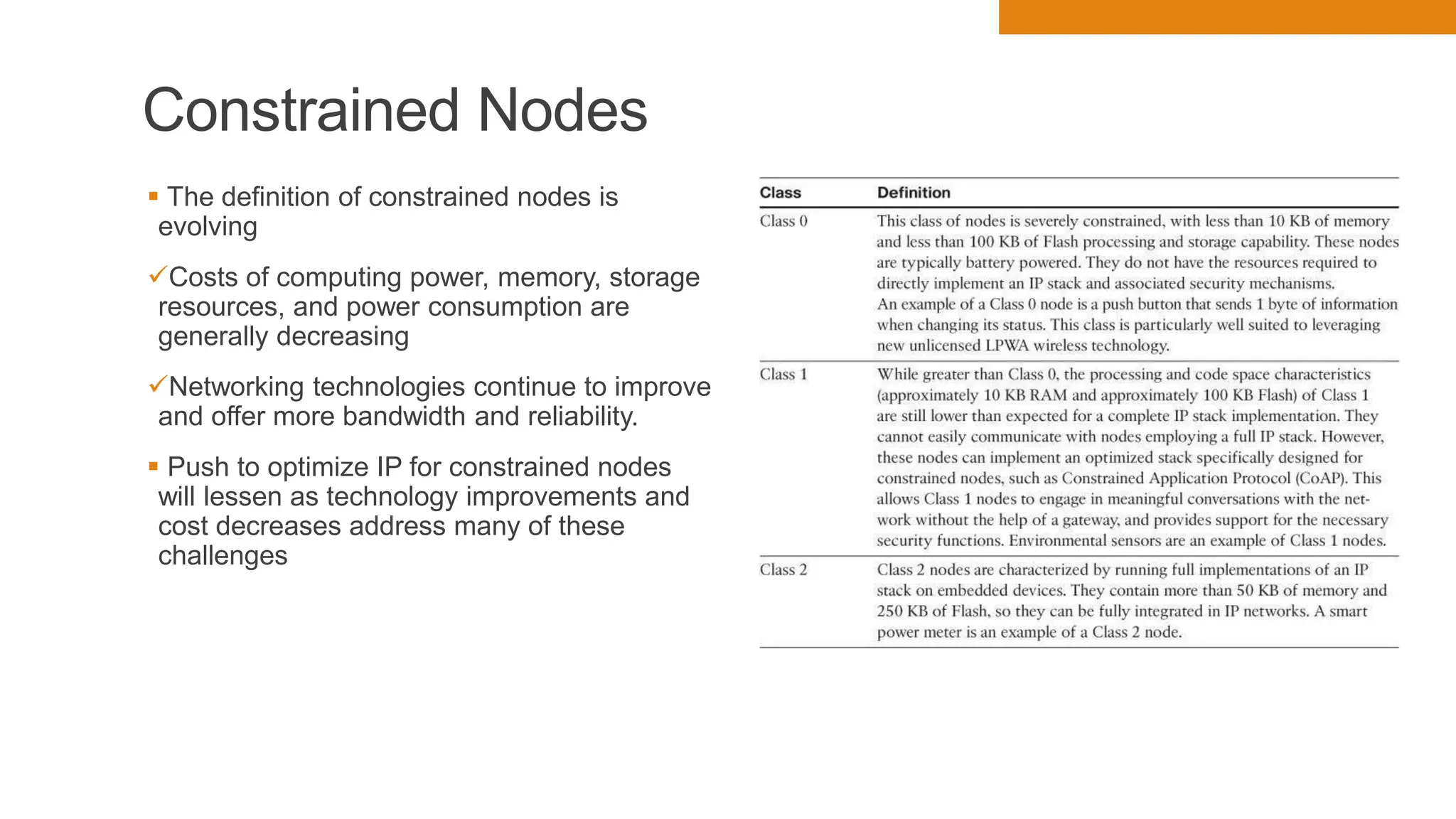
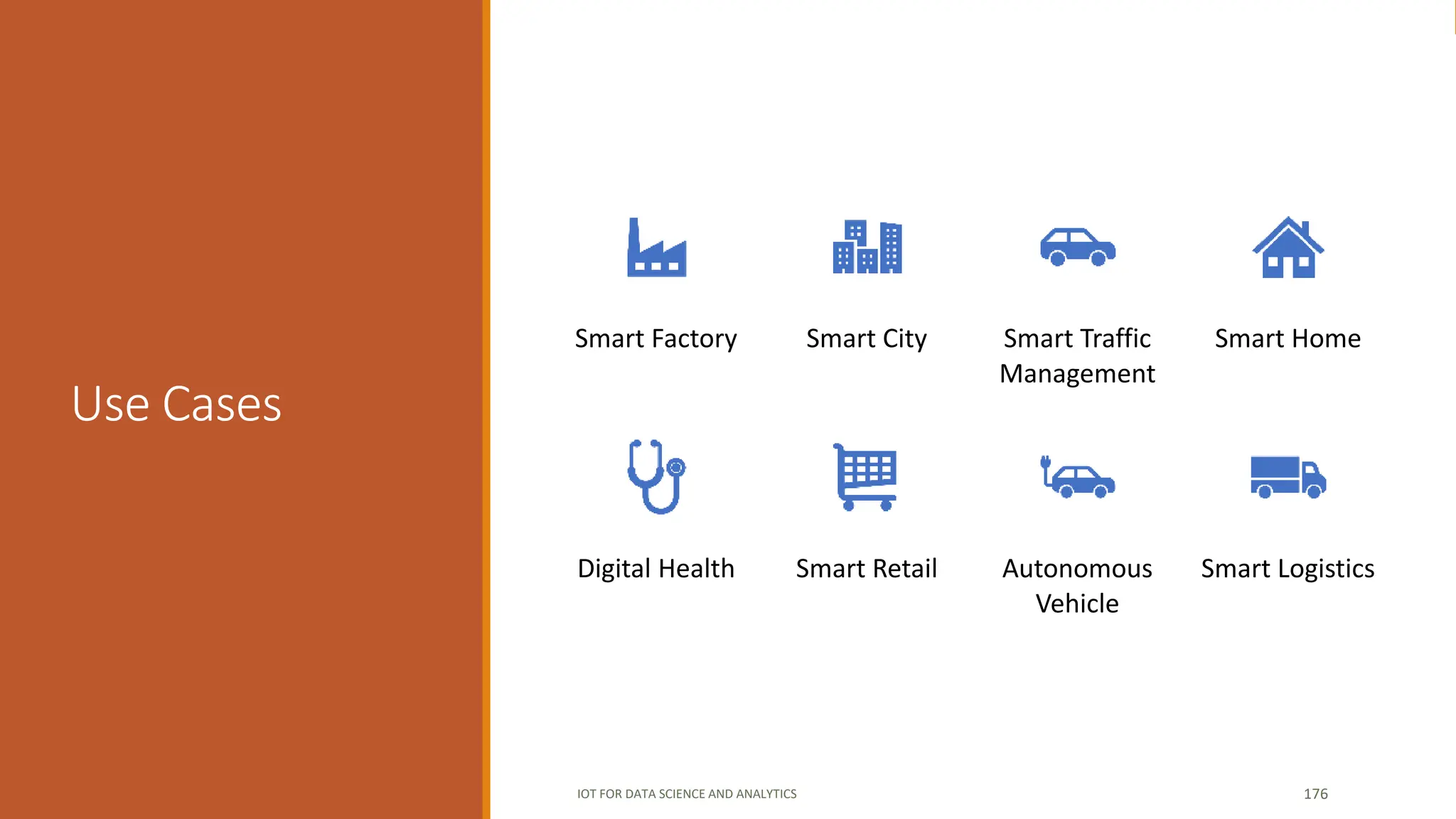
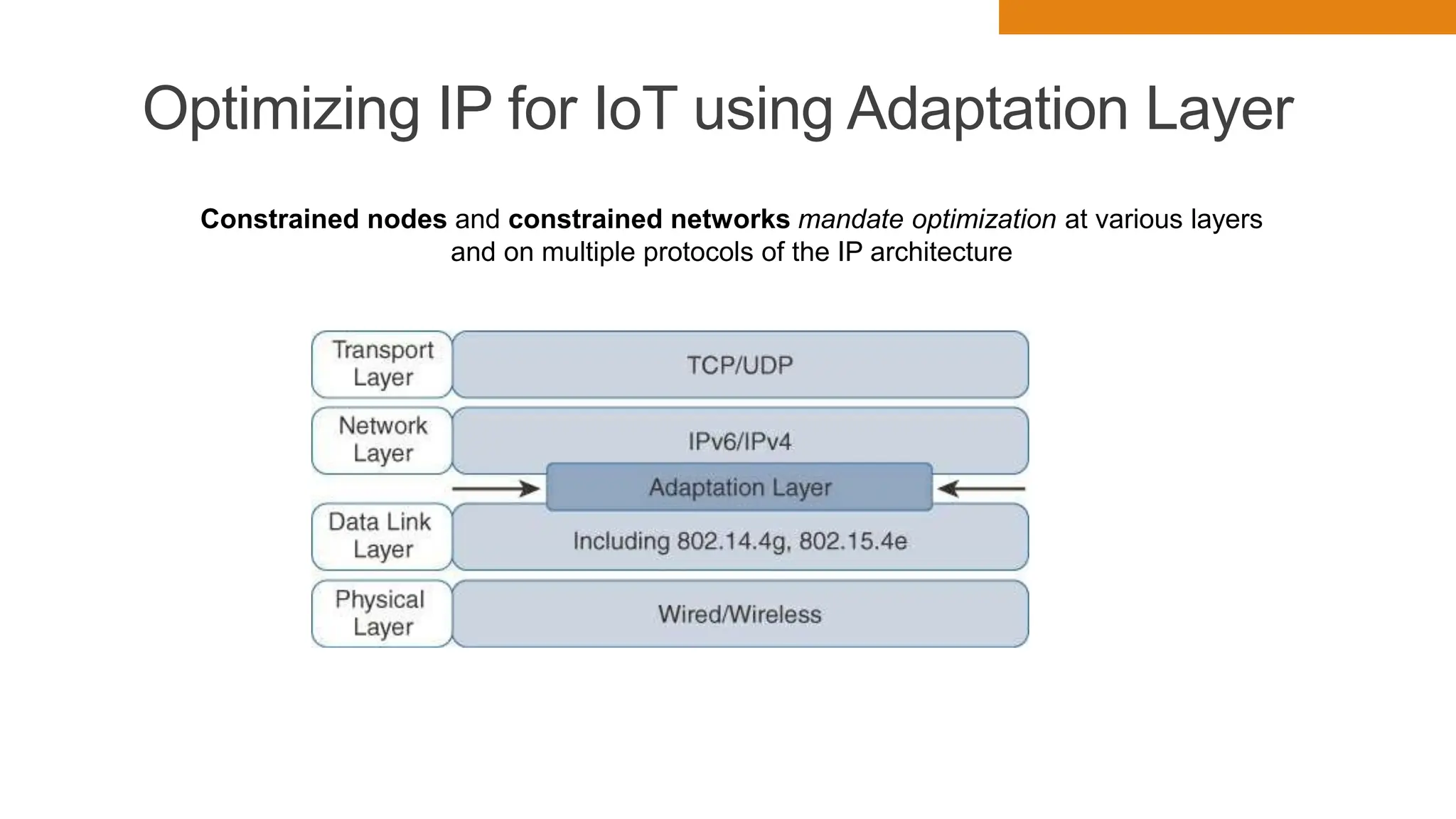
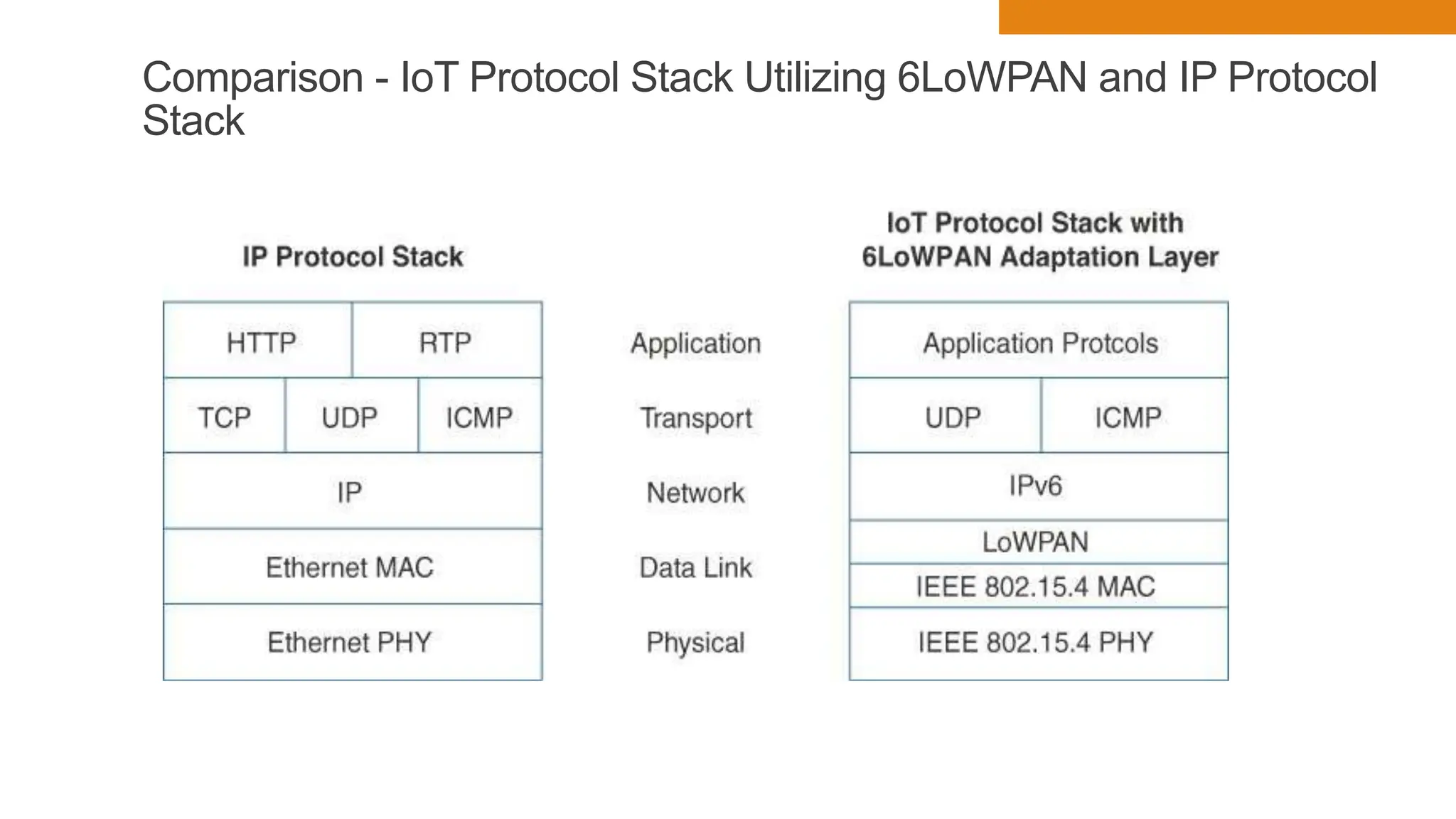
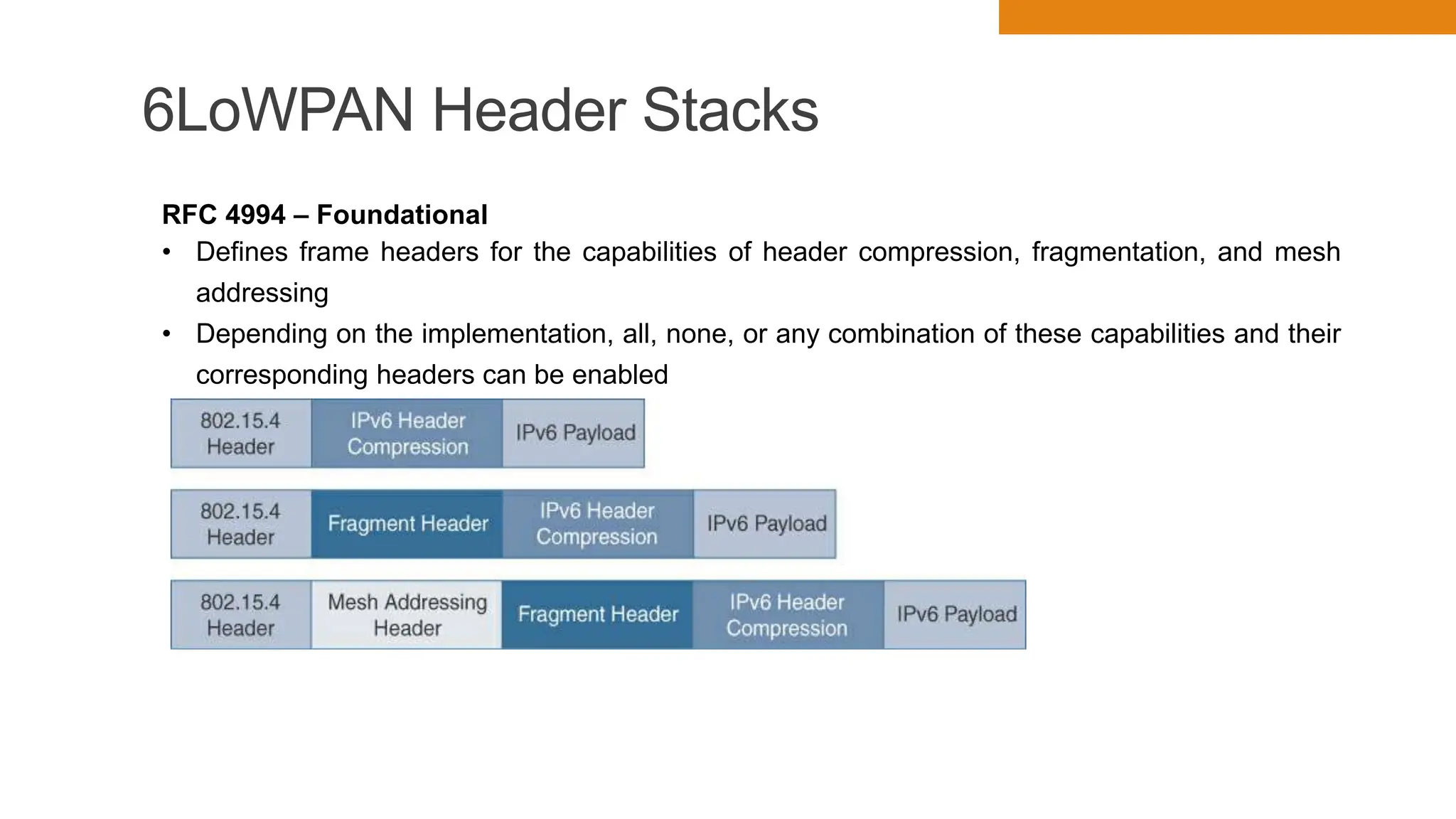
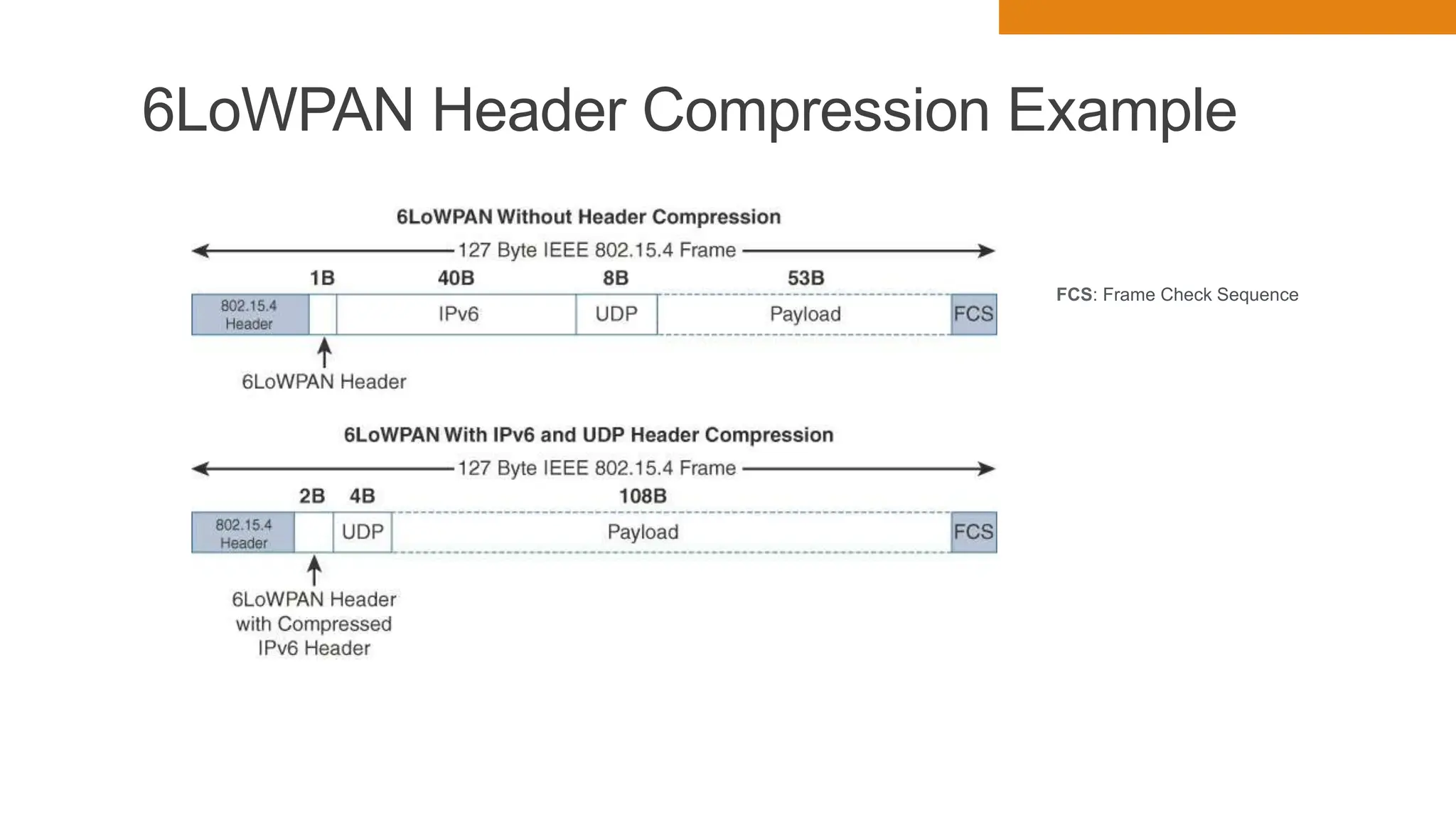
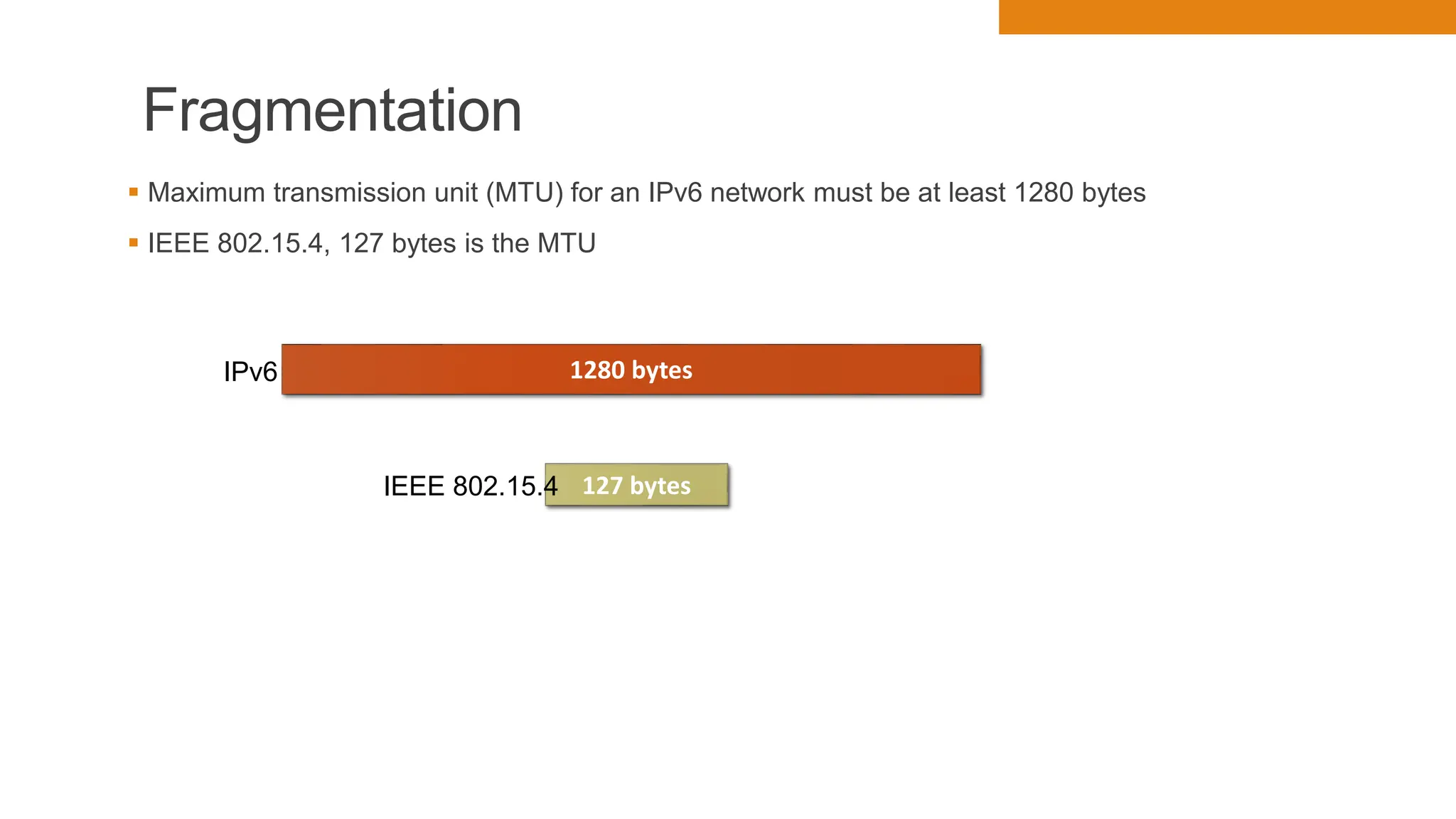
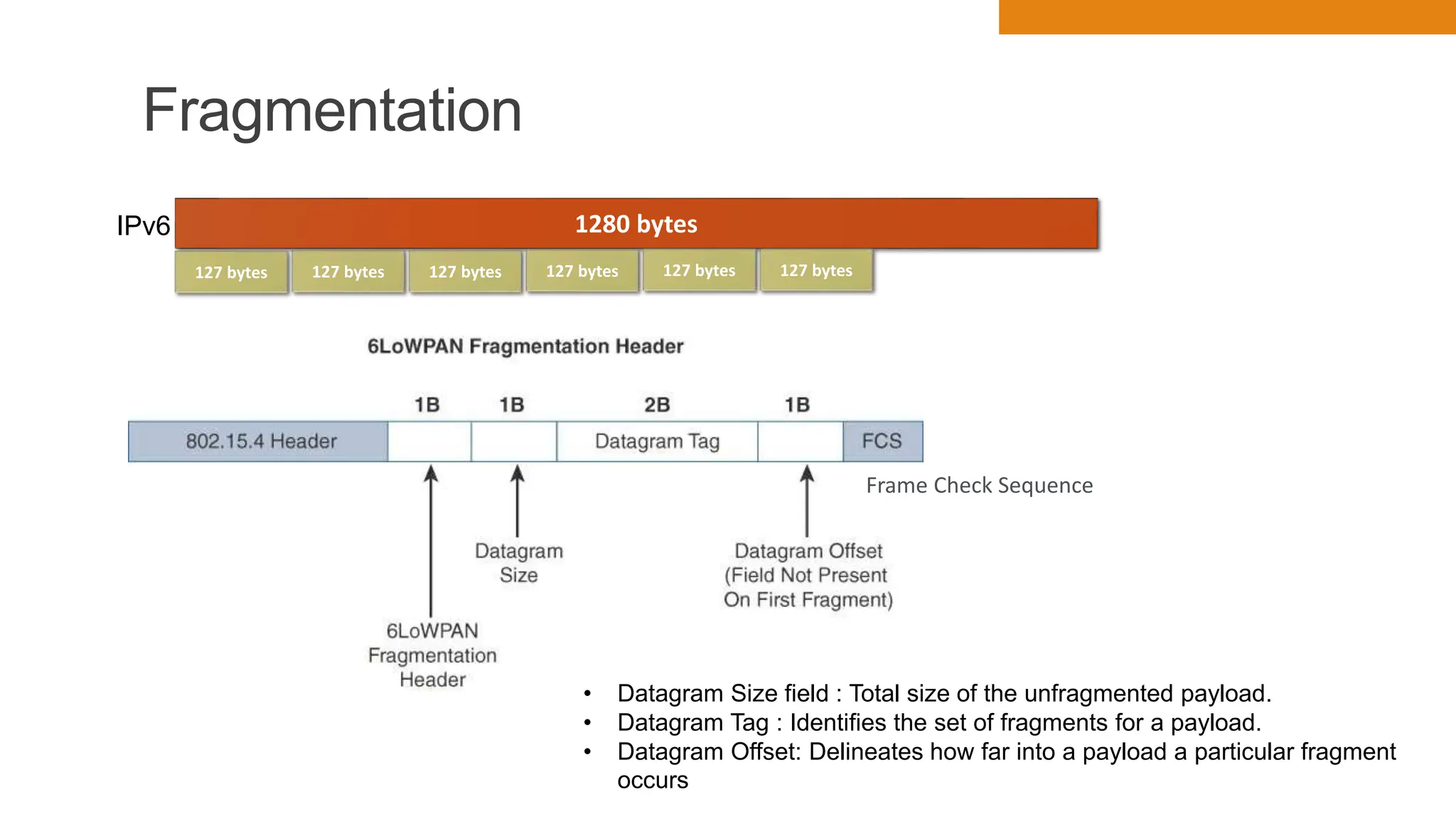
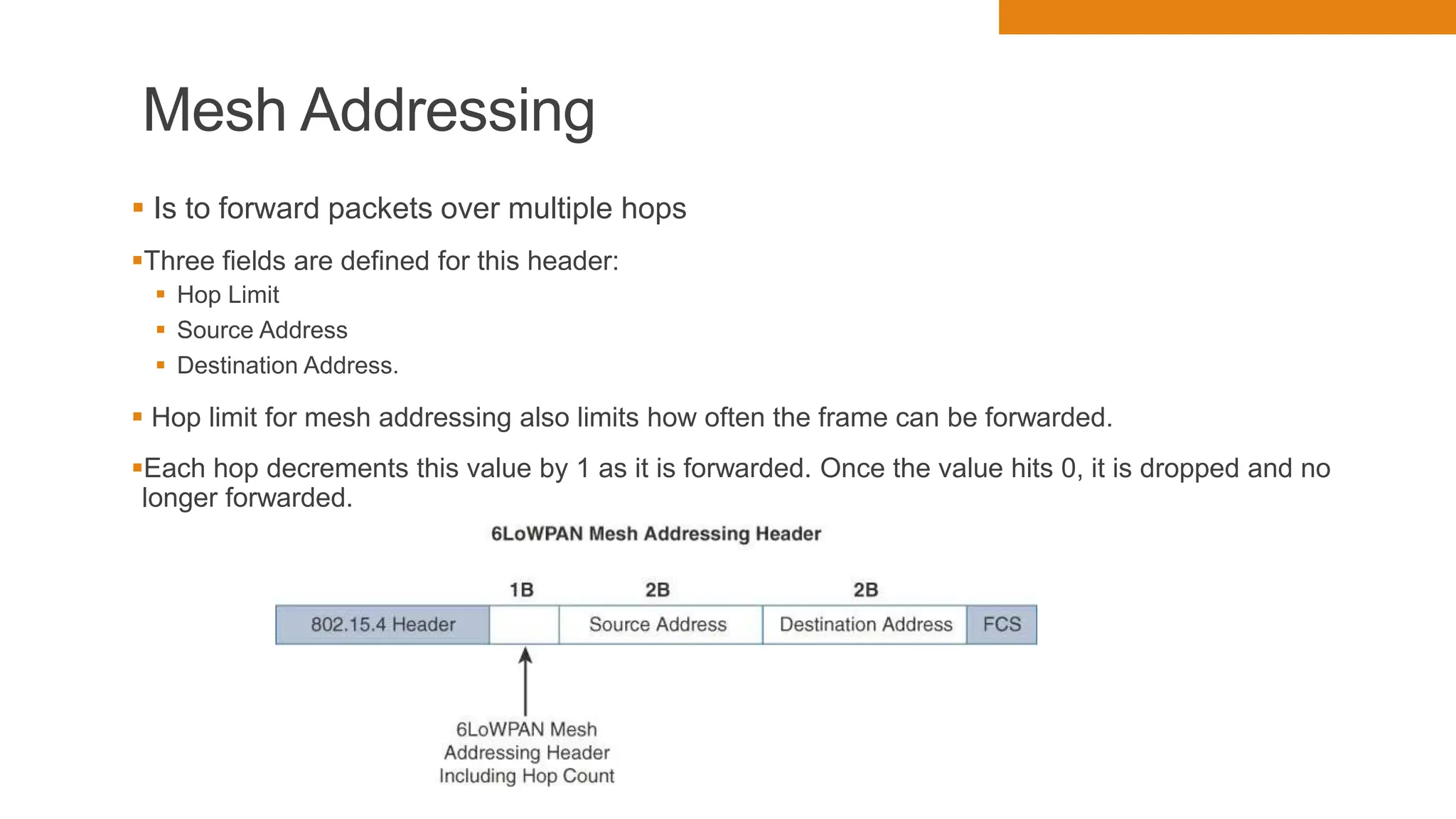
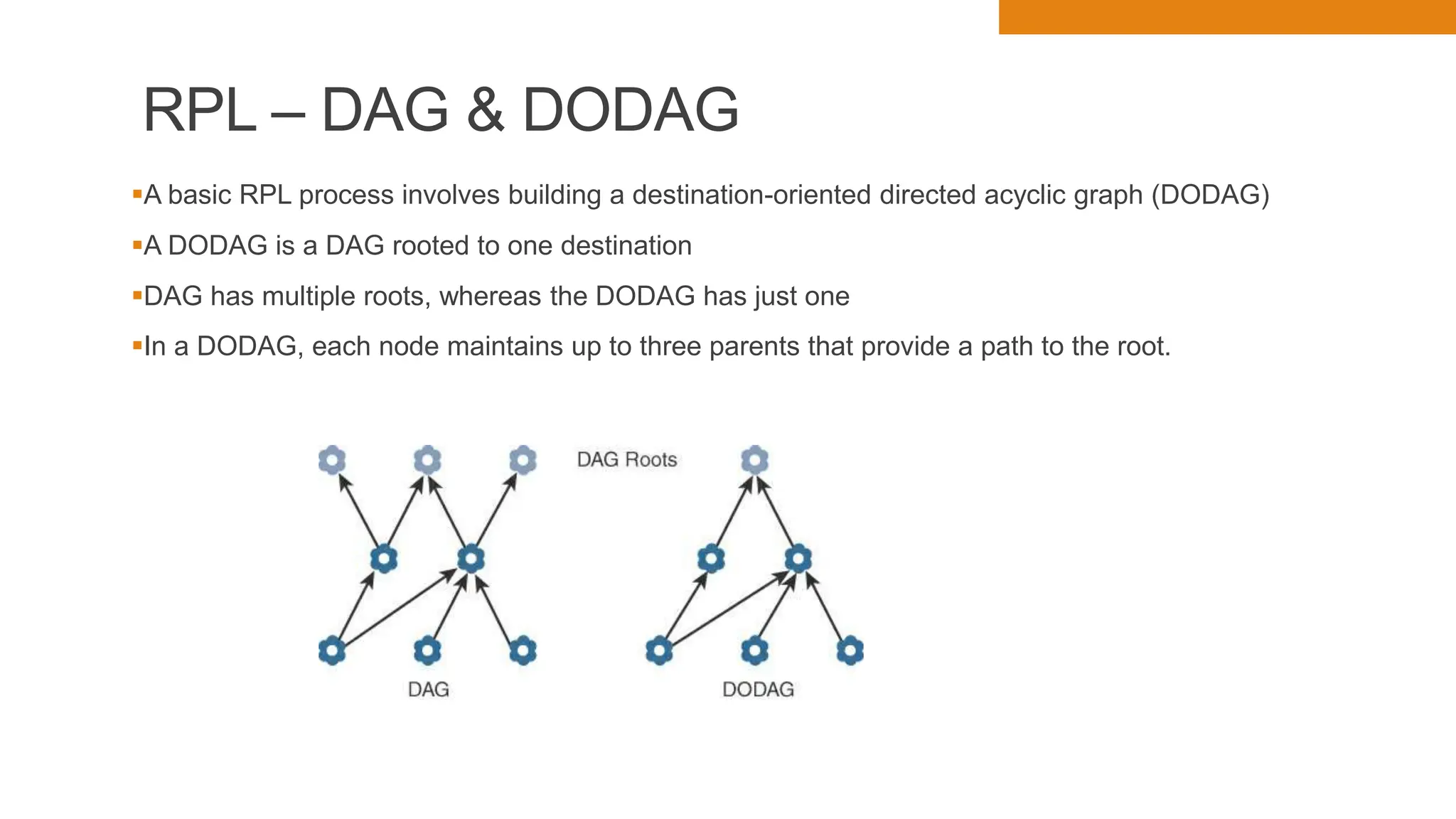
The document discusses key concepts in connecting smart objects for IoT applications. It describes sensors, actuators, and smart objects. Sensor networks such as wireless sensor networks are explained. Important criteria for connecting smart objects are discussed, including range, frequency bands, power consumption, topology, and constraints of devices and networks. Major connectivity technologies are also introduced, such as IEEE 802.15.4, LoRaWAN, NB-IoT, and others. The role of IP as the network layer for IoT is outlined.