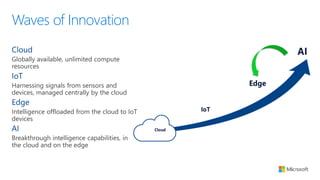
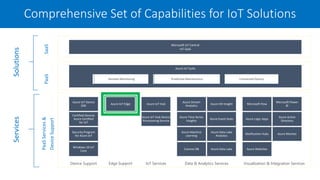
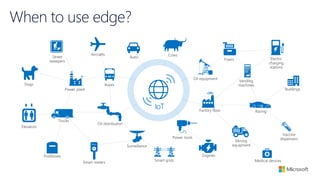
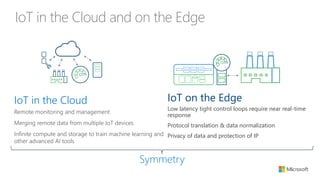
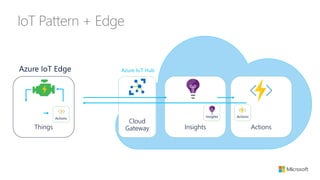
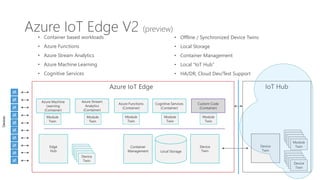
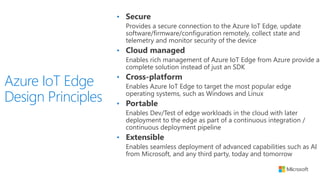
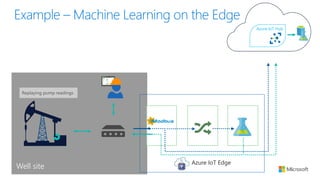
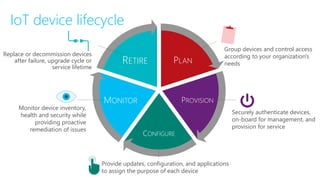
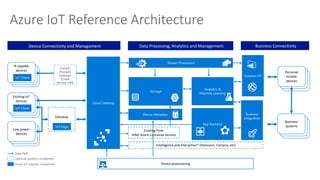
The document discusses the integration of IoT Edge within the IoT framework, emphasizing the capabilities of Azure's various services for data management, analytics, and device support. It highlights the importance of real-time processing, security, and device lifecycle management in deploying IoT solutions. Furthermore, it outlines design principles and operational patterns for effectively utilizing Azure IoT Edge.