The document provides an introduction to software testing and discusses:
1) The first computer bug was caused by a moth flying into the Mark II computer at Harvard in 1947.
2) Software bugs can have adverse effects such as deaths, injuries, financial losses, and privacy violations.
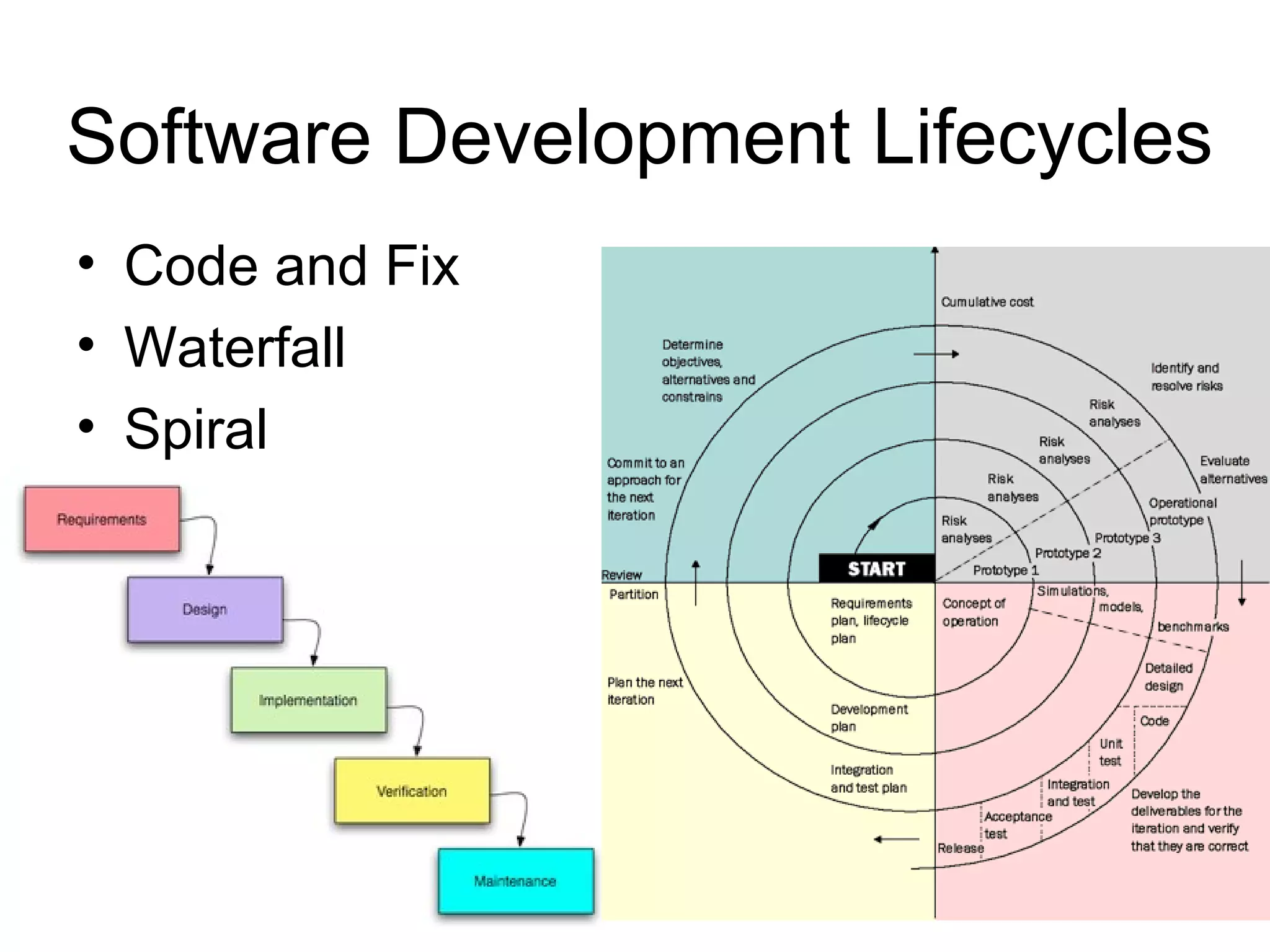
3) Most bugs stem from specification and design flaws rather than coding errors, and bugs found later in the development process are much more costly to fix.
4) The goal of software testing is to find bugs early in the development process and ensure they are fixed.
![Introduction to
Software Testing
[Reading assignment: Chapter 1, pp. 9-22]](https://image.slidesharecdn.com/introduction-160811053845/75/Introduction-to-software-testing-1-2048.jpg)






























![The Software
Development Process
[Reading assignment: Chapter 2, pp. 23-36]](https://image.slidesharecdn.com/introduction-160811053845/75/Introduction-to-software-testing-37-2048.jpg)