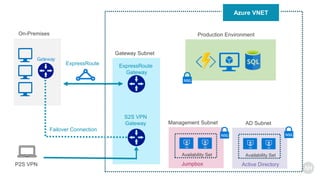
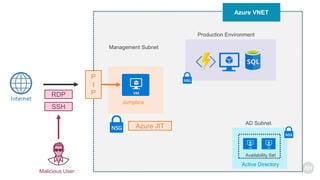
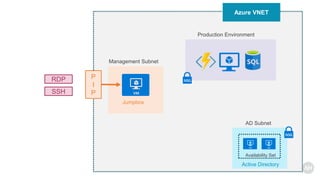
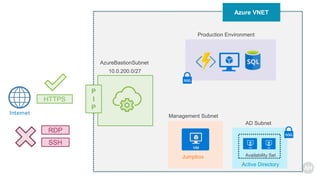
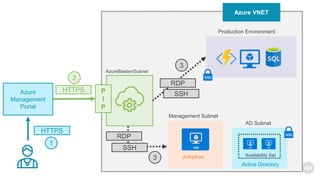
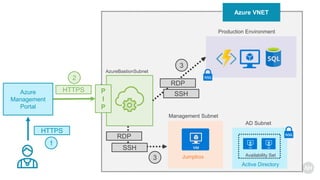
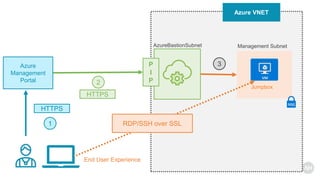
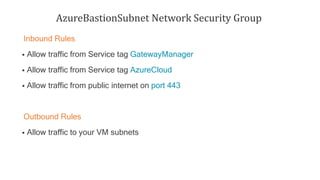
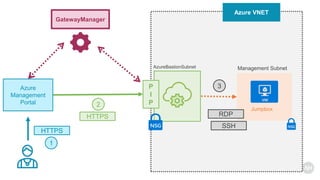
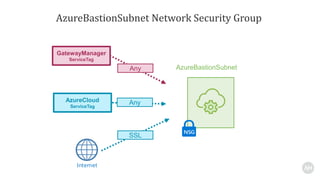
Azure Bastion is a fully managed PaaS service that allows secure RDP/SSH connectivity to virtual machines via the Azure portal without requiring public IP addresses. Each virtual network needs a Bastion host for this secure connection, which operates over SSL through specific network security group rules. The document provides resources and guides for creating and managing an Azure Bastion host.