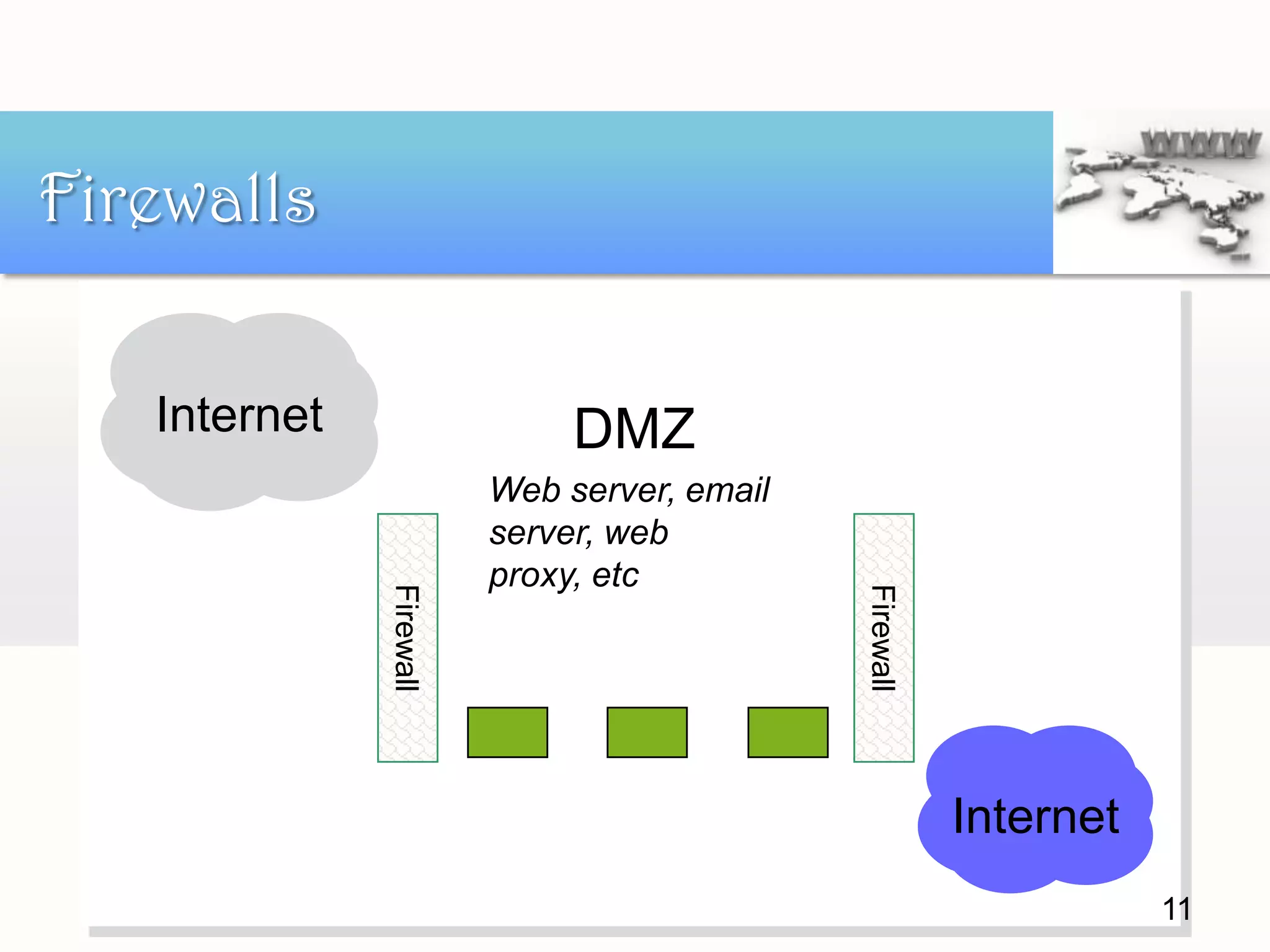
This document discusses internet security. It defines security as freedom from risk or danger and safety. It also discusses why security is needed, such as to protect financial information, medical records, and trade secrets. Those at risk include financial institutions, internet service providers, government agencies, and anyone on a network. Common security attacks are discussed like packet sniffing, firewalls, and social engineering. Countermeasures to these threats include encryption, access control with firewalls, education, and monitoring who has access to resources. In conclusion, while many solutions exist, humans remain vulnerable to manipulation and it is important to stay aware of latest security issues.