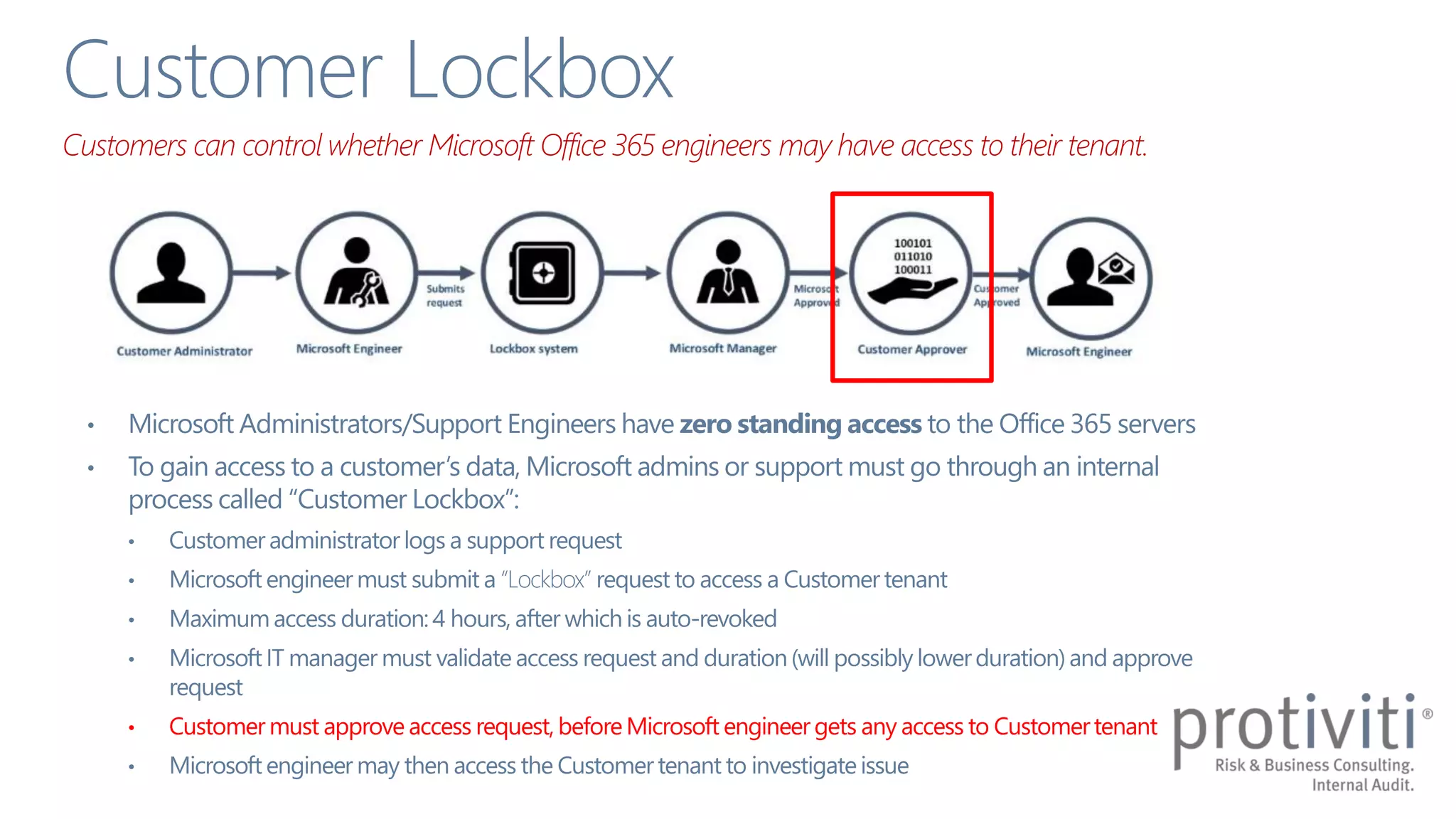
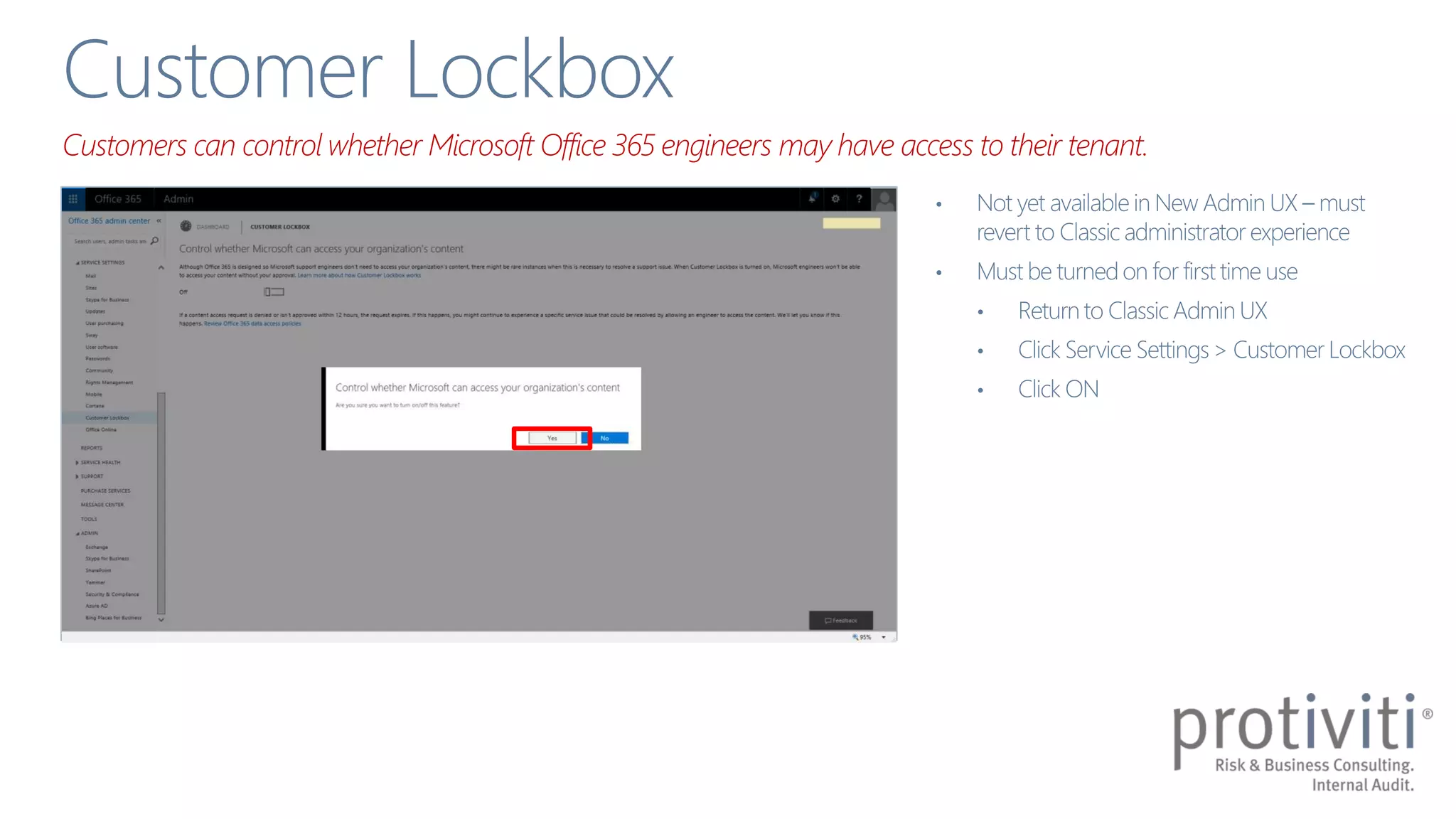
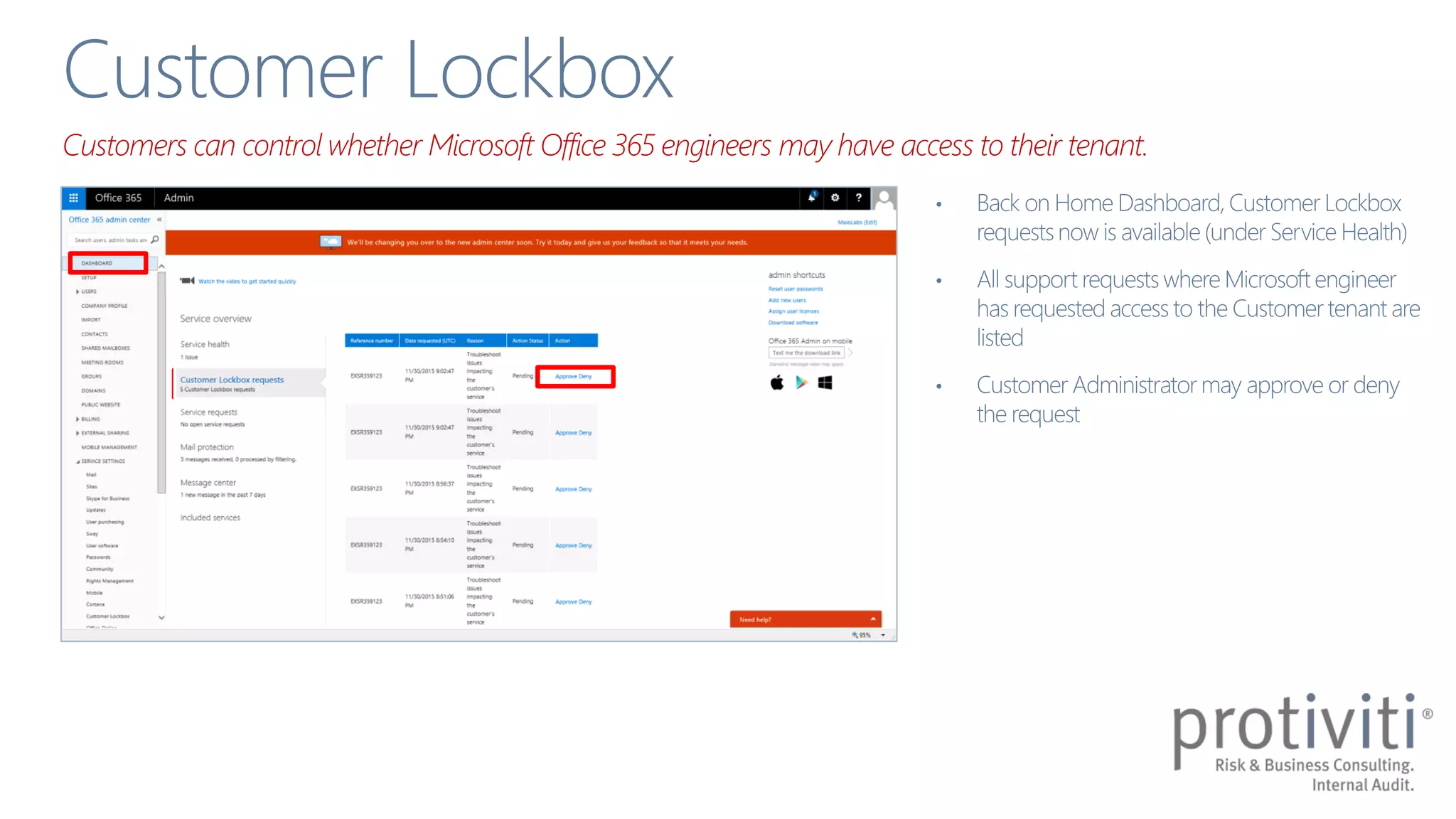
The document discusses the shared responsibility model for security and information protection in Office 365, emphasizing the importance of understanding both cloud provider and customer responsibilities. It outlines various security capabilities and features, such as permissions management, multi-factor authentication, and data loss prevention measures. Additionally, it highlights the need for strong information governance policies to effectively manage these responsibilities.