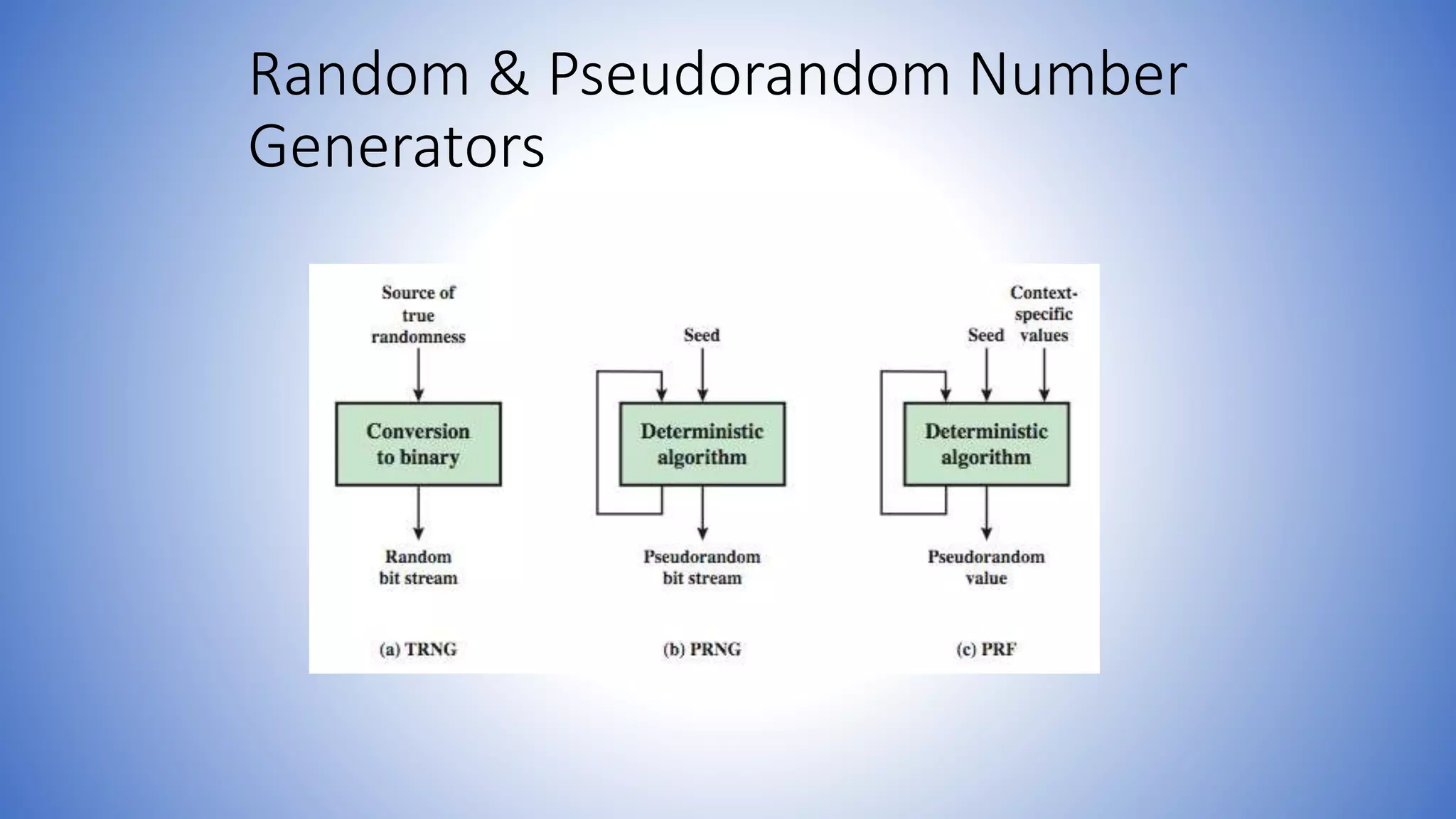
The document discusses the importance of random numbers in cryptography and network security, highlighting their applications such as session key generation and authentication protocols. It explains the distinction between true random number generators and pseudorandom number generators, emphasizing that the latter, though deterministic, should pass tests of randomness to be secure. Additionally, it outlines the requirements for effective pseudorandom number generation, including unpredictability and secure seed characteristics.