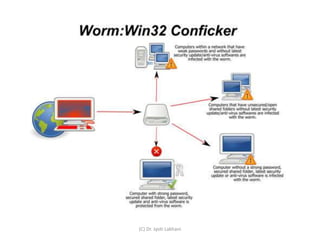
A computer worm is a standalone malware program that replicates itself and spreads to other computers by exploiting security vulnerabilities. It uses network resources to scan for vulnerable systems and transfer itself, potentially infecting many computers and overloading networks. Notable examples of worms include Morris worm, which disrupted computers on the early Internet in 1988, and Conficker, which infected over 9 million systems worldwide in 2008. Worms are generally more infectious than viruses due to their ability to spread autonomously across networks.