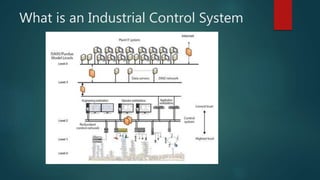
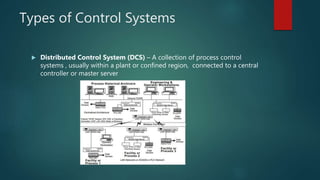
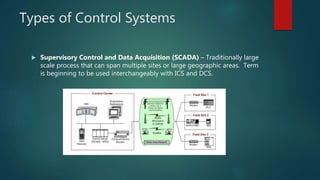
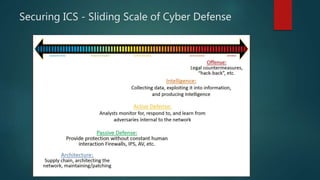
Chad Hunter presented on industrial control systems (ICS) networks. He discussed common ICS components like PLCs, RTUs, and HMIs. Types of control systems include process control, DCS, and SCADA. ICS networks differ from IT networks in prioritizing availability over confidentiality and integrity. Major ICS threats discussed included Stuxnet, Havex, BlackEnergy, CRASHOVERRIDE, and TRITON. Securing ICS involves whitelisting, configuration management, reducing attack surface, network segmentation, authentication, and monitoring as outlined in the DHS Seven Steps framework.