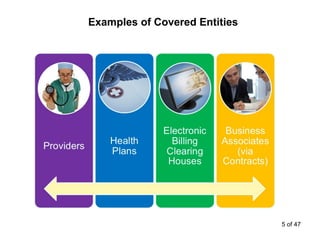
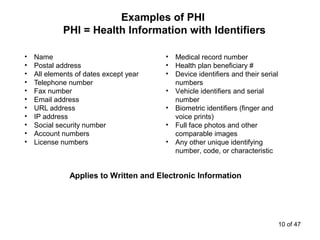
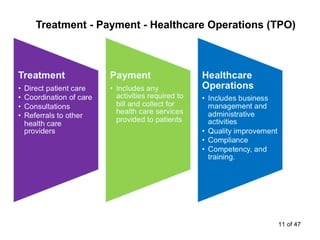
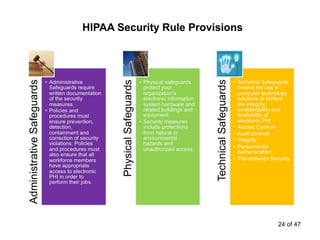
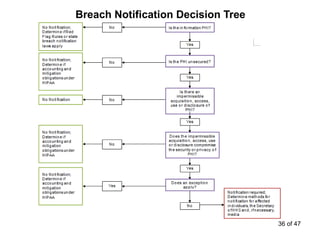
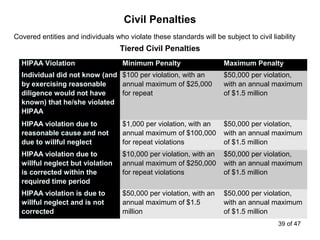
The document discusses the requirements of HIPAA for protecting patient privacy and securing their health information, including mandates for training and documentation, increased penalties for violations, and rights for patients to access electronic health records; it also outlines the entities covered by HIPAA, defines protected health information, and reviews standards for its use and disclosure for treatment, payment, and healthcare operations.