HendricksERD
•Download as DOCX, PDF•
0 likes•81 views
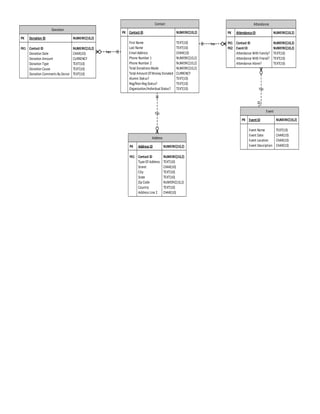
This document outlines the structure of tables for a database to track donations, contacts, addresses, attendance, and events. The Donation table tracks donation details and is linked to the Contact table by a foreign key. The Contact table stores contact details. The Address table links contacts to their addresses. The Attendance table links contacts to events they attended. The Event table stores event details.
Report
Share
Report
Share
Recommended
More Related Content
Viewers also liked
Viewers also liked (7)
Análisis de las complementariedades en la ocupación. Una perspectiva microeco...

Análisis de las complementariedades en la ocupación. Una perspectiva microeco...
More from Kunal Sharma
More from Kunal Sharma (6)
Impact of Current Technology on Information Agencies

Impact of Current Technology on Information Agencies
Improving the Wi-Fi in the Carrier Dome Feasibility Report

Improving the Wi-Fi in the Carrier Dome Feasibility Report
HendricksERD
- 1. Donation PK Donation ID NUMERIC(10,2) FK1 Contact ID NUMERIC(10,2) Donation Date CHAR(10) Donation Amount CURRENCY Donation Type TEXT(10) Donation Cause TEXT(10) Donation Comments By Donor TEXT(10) Contact PK Contact ID NUMERIC(10,2) First Name TEXT(10) Last Name TEXT(10) Email Address CHAR(10) Phone Number 1 NUMERIC(10,2) Phone Number 2 NUMERIC(10,2) Total Donations Made NUMERIC(10,2) Total Amount Of Money Donated CURRENCY Alumni Status? TEXT(10) Reg/Non-Reg Status? TEXT(10) Organization/Individual Status? TEXT(10) Address PK Address ID NUMERIC(10,2) FK1 Contact ID NUMERIC(10,2) Type Of Address TEXT(10) Street CHAR(10) City TEXT(10) State TEXT(10) Zip Code NUMERIC(10,2) Country TEXT(10) Address Line 2 CHAR(10) Attendance PK AttendanceID NUMERIC(10,2) FK1 Contact ID NUMERIC(10,2) FK2 EventID NUMERIC(10,2) Attendance With Family? TEXT(10) Attendance With Friend? TEXT(10) Attendance Alone? TEXT(10) Event PK EventID NUMERIC(10,2) Event Name TEXT(10) Event Date CHAR(10) Event Location CHAR(10) Event Description CHAR(10) has has has has