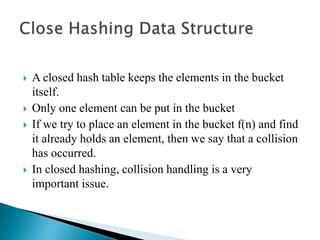
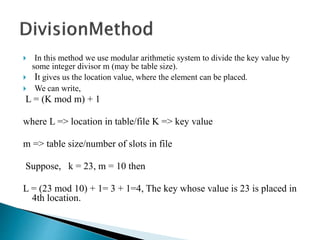
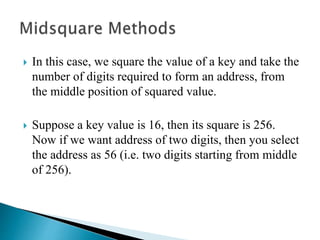
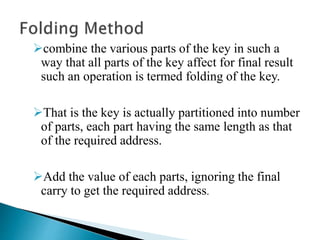
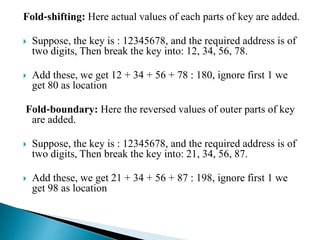
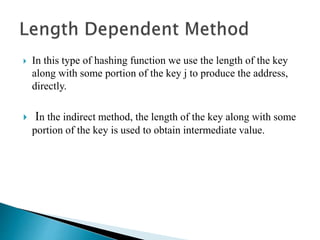
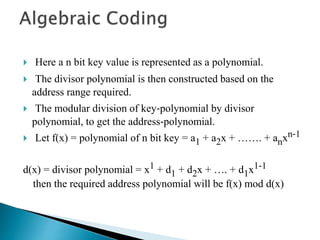
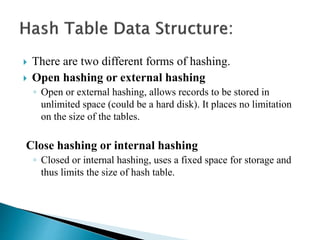
The document discusses different techniques for storing and searching data, including sequential search, binary search, and hashing. It provides details on open hashing and closed hashing, describing that closed hashing stores elements within buckets and can cause collisions when multiple elements are mapped to the same bucket. The document also outlines characteristics of good hash functions and different hashing methods like division, mid-square, folding, digit analysis, length dependent, algebraic coding, and multiplicative hashing.


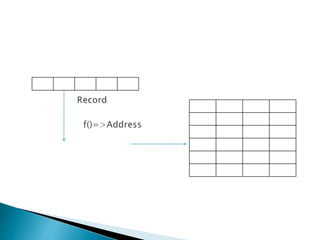
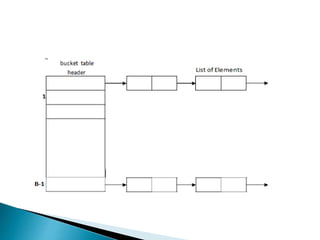
![ The basic idea is that the records [elements] are
partitioned into B classes, numbered 0,1,2 … B‐l
A Hashing function f(x) maps a record with key n to an
integer value between 0 and B‐l.
Each bucket in the bucket table is the head of the linked list of
records mapped to that bucket.](https://image.slidesharecdn.com/hashing-1-161128063336/85/Hashing-1-5-320.jpg)