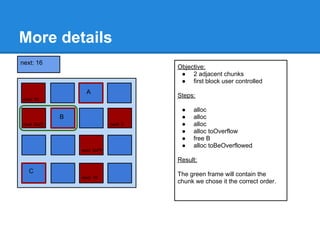
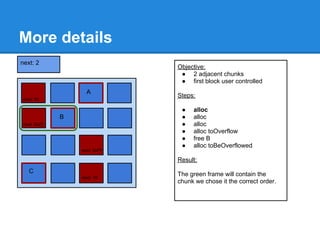
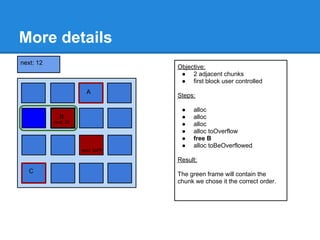
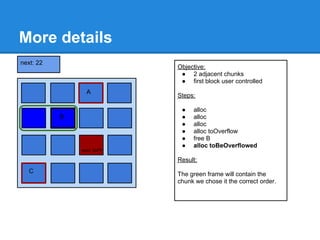
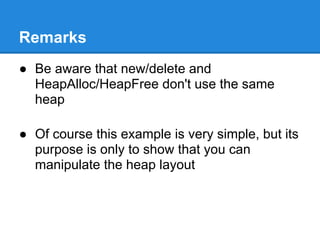
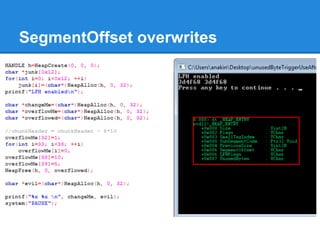
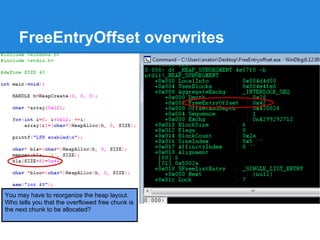
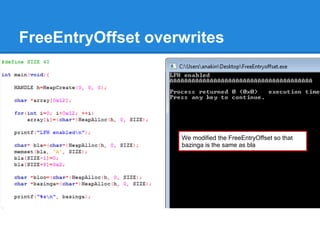
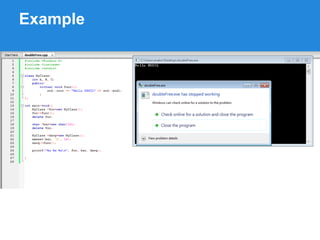
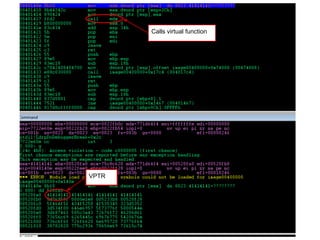
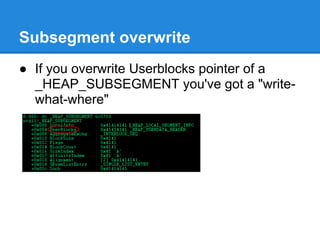
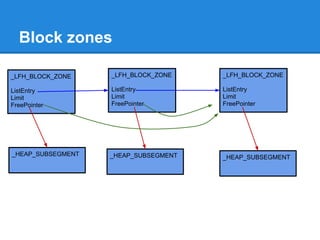
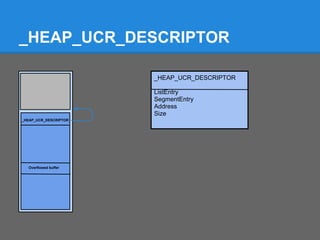
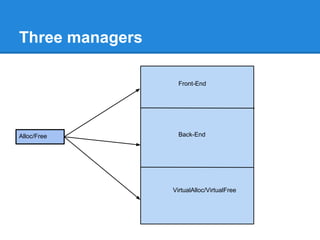
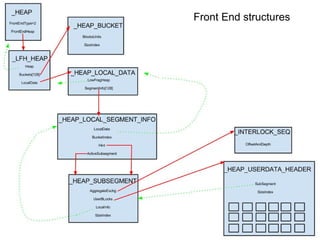
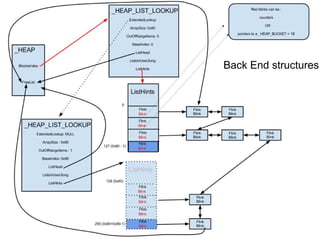
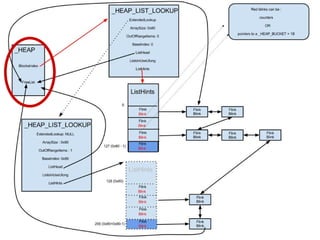
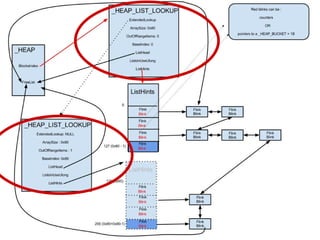
The document discusses the low fragmentation heap (LFH) used in Windows to improve memory allocation performance. It provides an overview of how the LFH works, including the different memory managers (front-end, back-end), data structures used, and the processes for allocating and deallocating memory. It then discusses techniques for exploiting the determinism of the LFH, such as heap feng shui to control memory layout, and overwriting fields to trigger memory corruption.





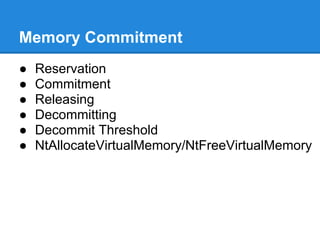


![Enabling the LFH
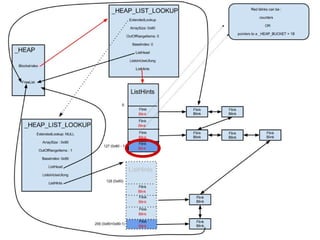
● When counter > 0x20:
○ RtlpGetLFHContext
○ Returns :
■ NULL if LFH has not yet been activated
■ _LFH_HEAP.bucket[size]
○ If context is null : set heap.CompatibilityFlags
○ If context not null : save _HEAP_BUCKET+1 in blink](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-13-320.jpg)


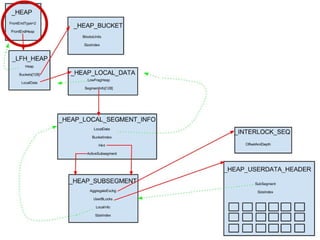
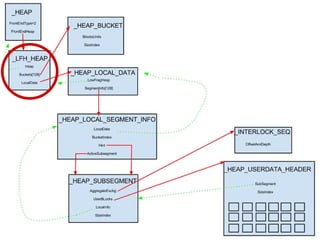
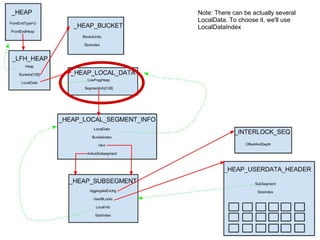
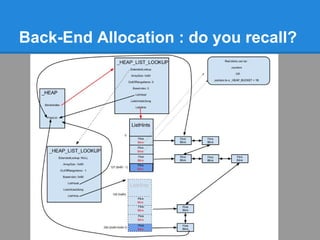
![_HEAP_BUCKET+1
sizeIndex
Flink
BLink
_HEAP_LOCAL_DATA
LowFragHeap
SegmentInfo[128]](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-24-320.jpg)
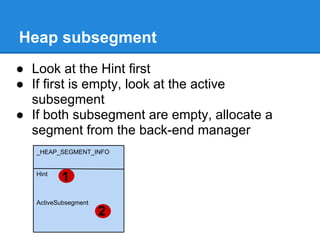

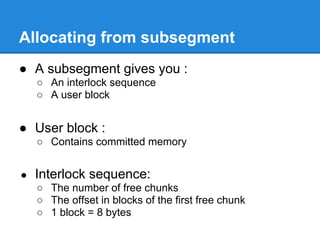

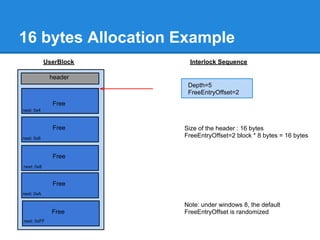
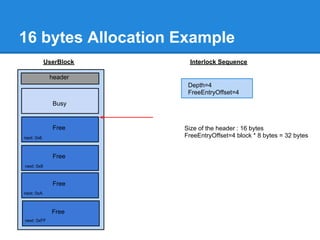

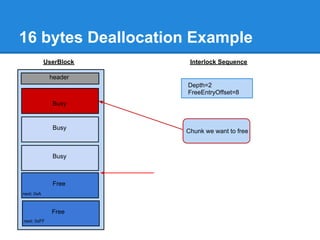
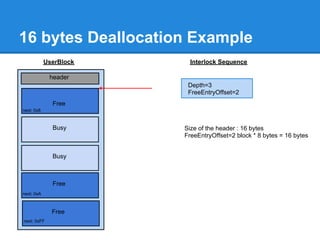
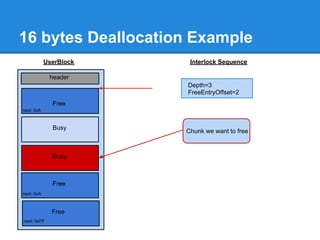
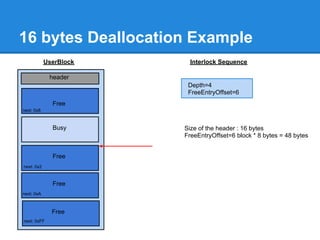

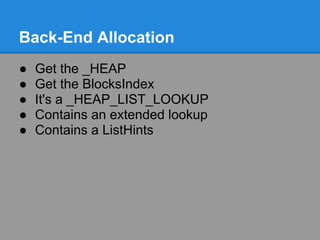
![Back-End Allocation
● Is chunkSize < ArraySize?
● If so, use this ListHints
● Otherwise if no extendedLookup:
○ use ListHints[ArraySize-1]
● If there is an extendedLookup
○ is chunkSize < extended.ArraySize?
● If so, use this ListHints
● Otherwise, use extended.ListHints[ArraySize-
1]](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-45-320.jpg)


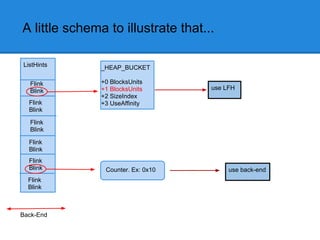
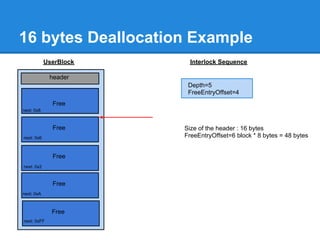
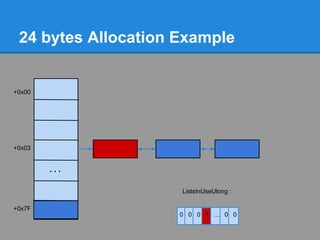
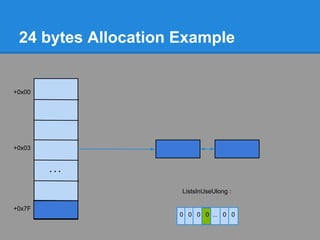
![24 bytes Allocation Example
The user requested 16 bytes.
16 bytes + 8 bytes of header = 24 bytes
3*8=24 bytes.
+0x00 Bitmap indicates that ListHints[3] contains free chunks
+0x03
...
ListsInUseUlong :
+0x7F
0 0 0 1 ... 0 0](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-48-320.jpg)
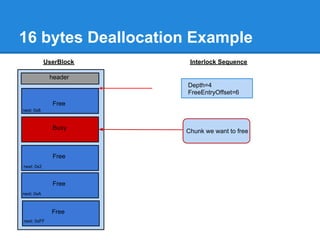
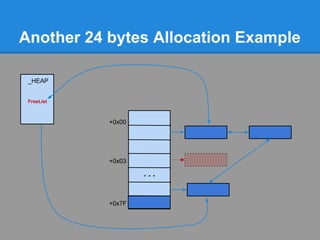
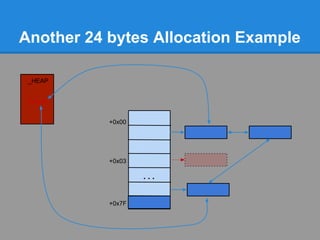
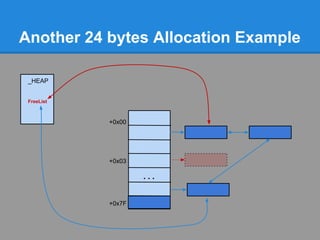
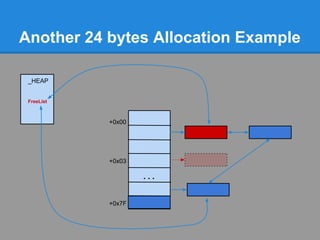
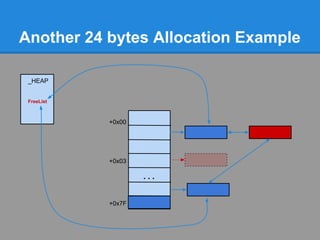
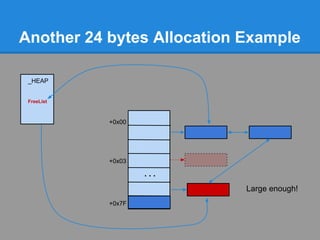
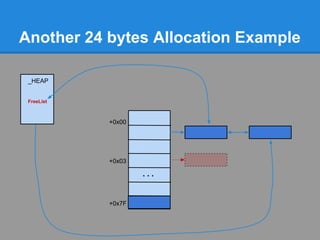
![Another 24 bytes Allocation Example
Problem : No chunk available at ListHints[3]
+0x00
+0x03
...
+0x7F](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-51-320.jpg)
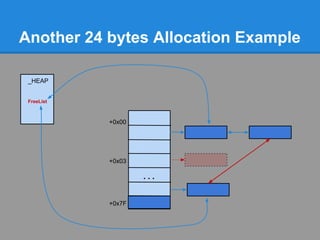


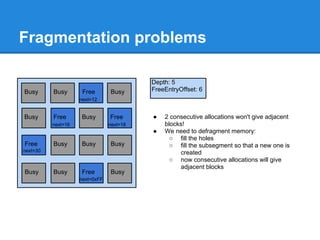
![Fragmentation problems
Enable the LFH
The next alloc will return the address of array2[0],
the second one will return the address of array2[4].
(LFH is kind of LIFO)
Defragment and allocate a new
subsegment
Now, the object is after our "user controlled" buffer](https://image.slidesharecdn.com/finallfhpresentation3-120605054130-phpapp01/85/Final-lfh-presentation-3-63-320.jpg)