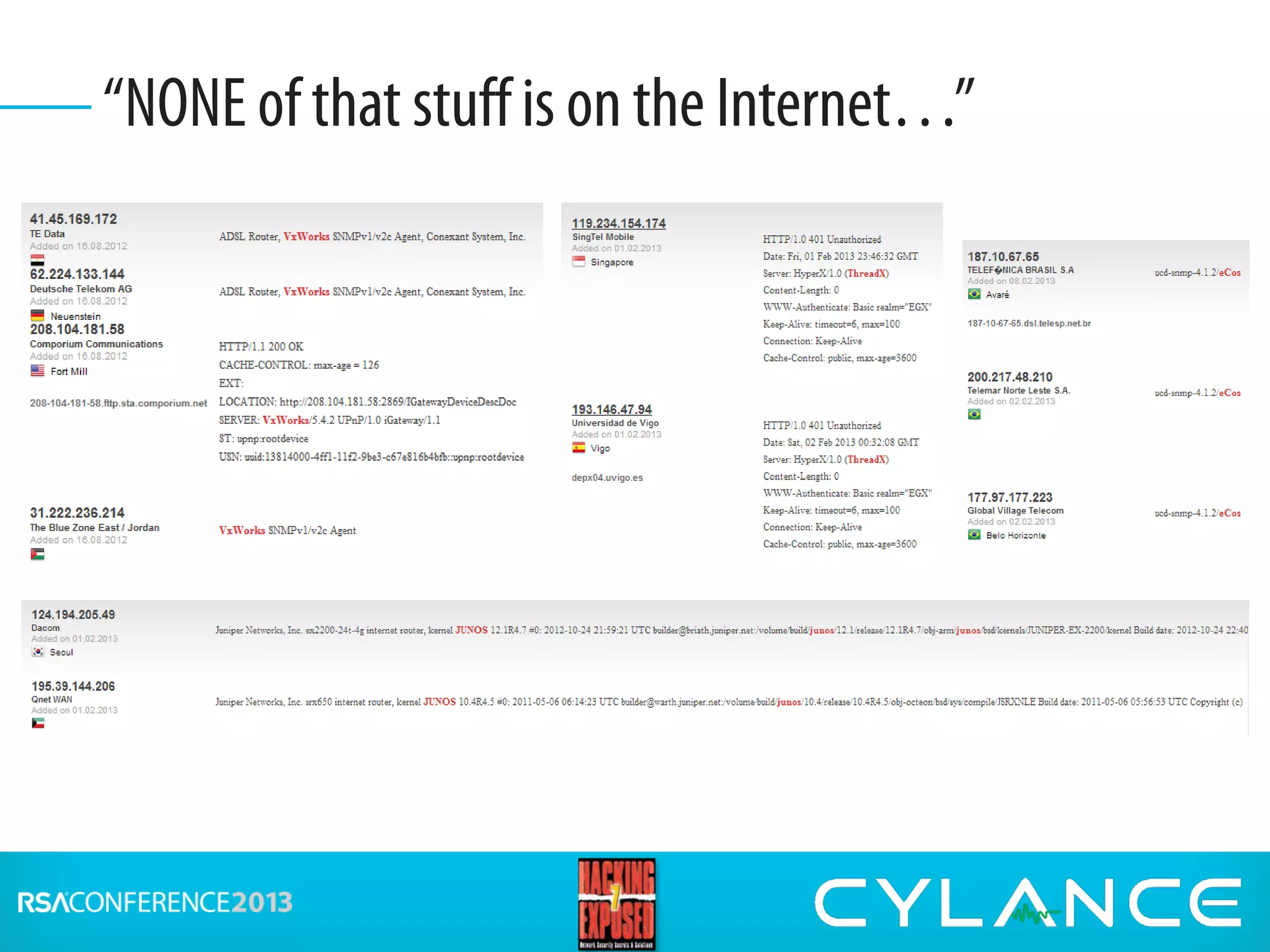
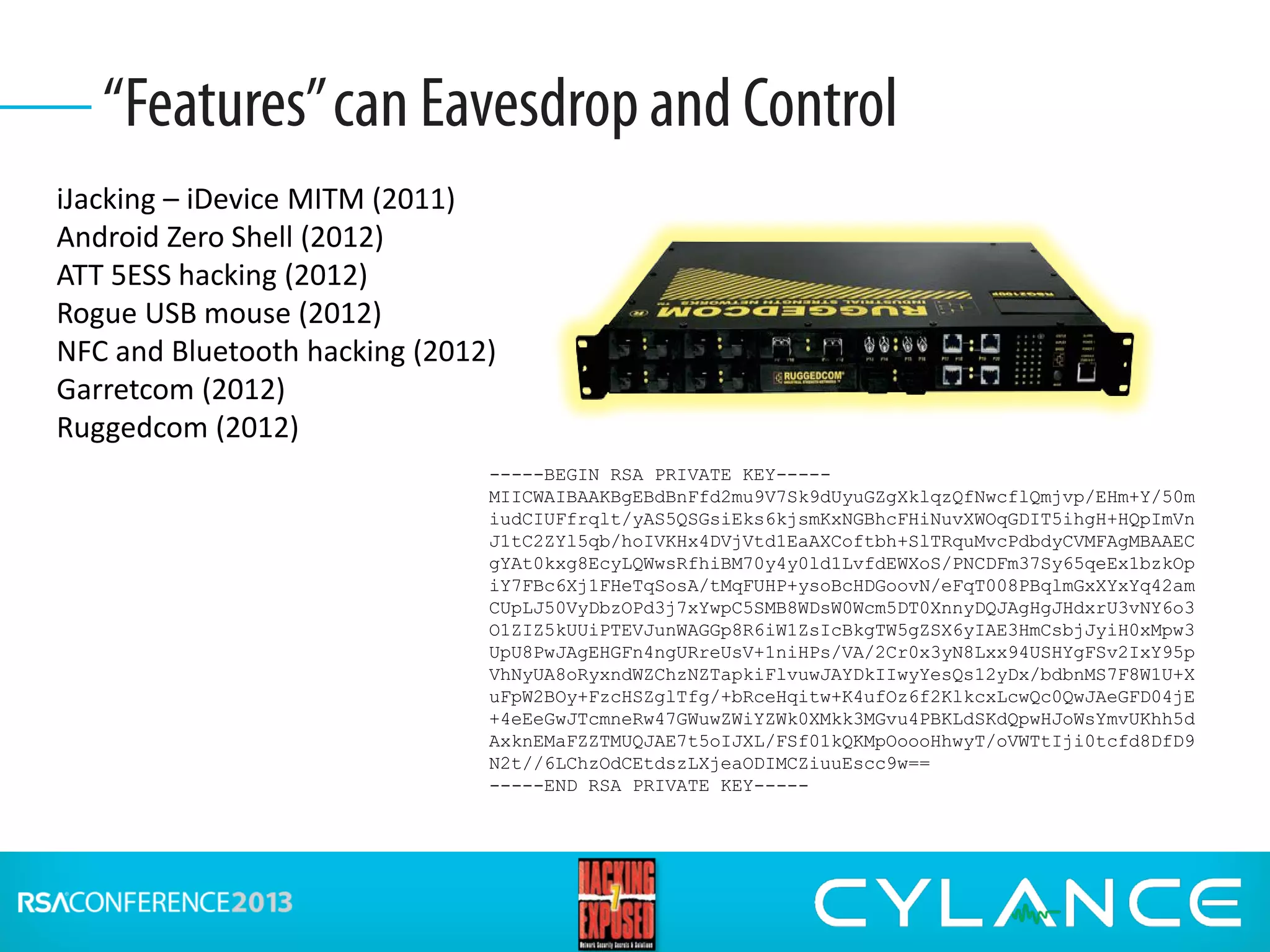
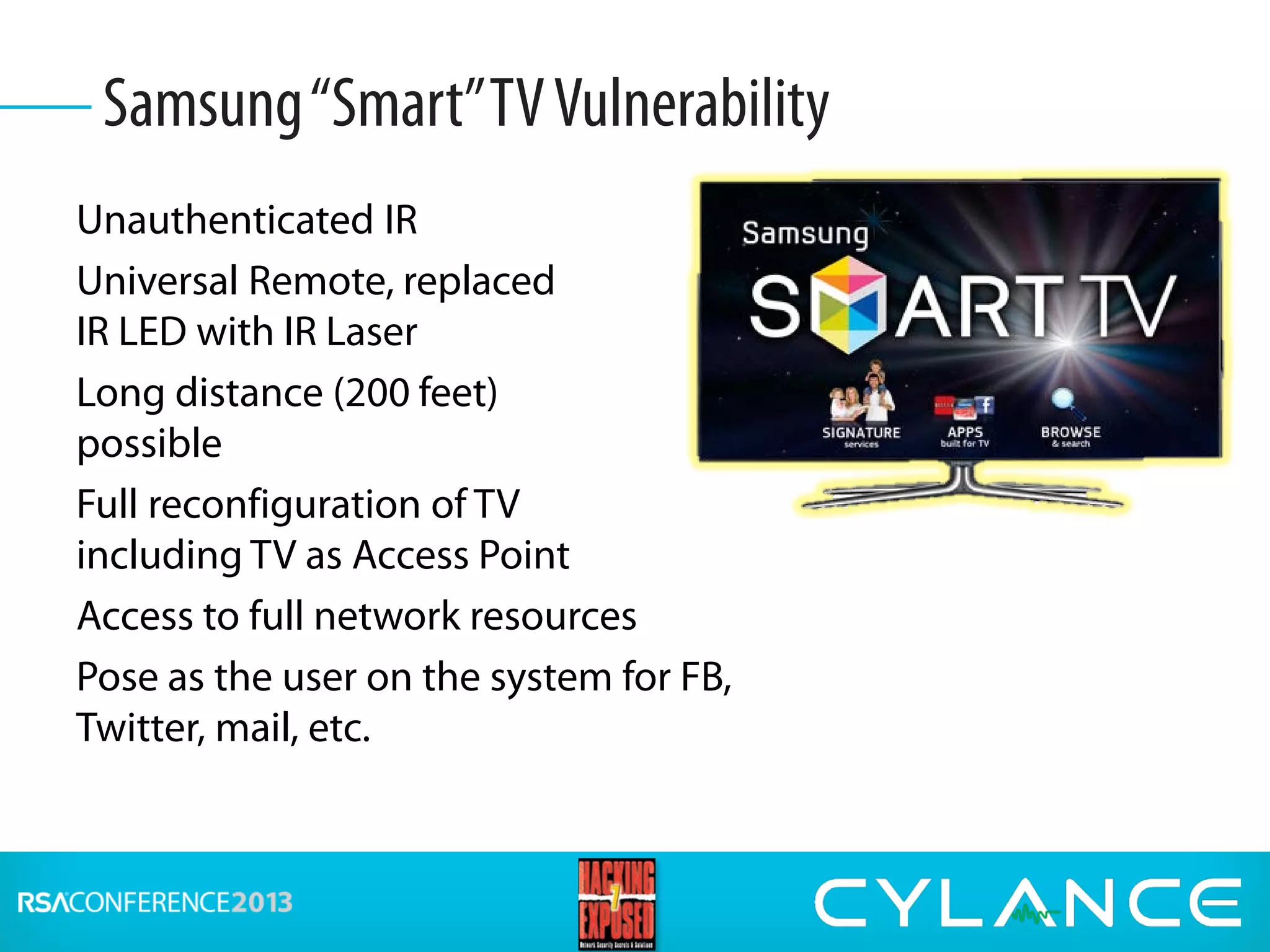
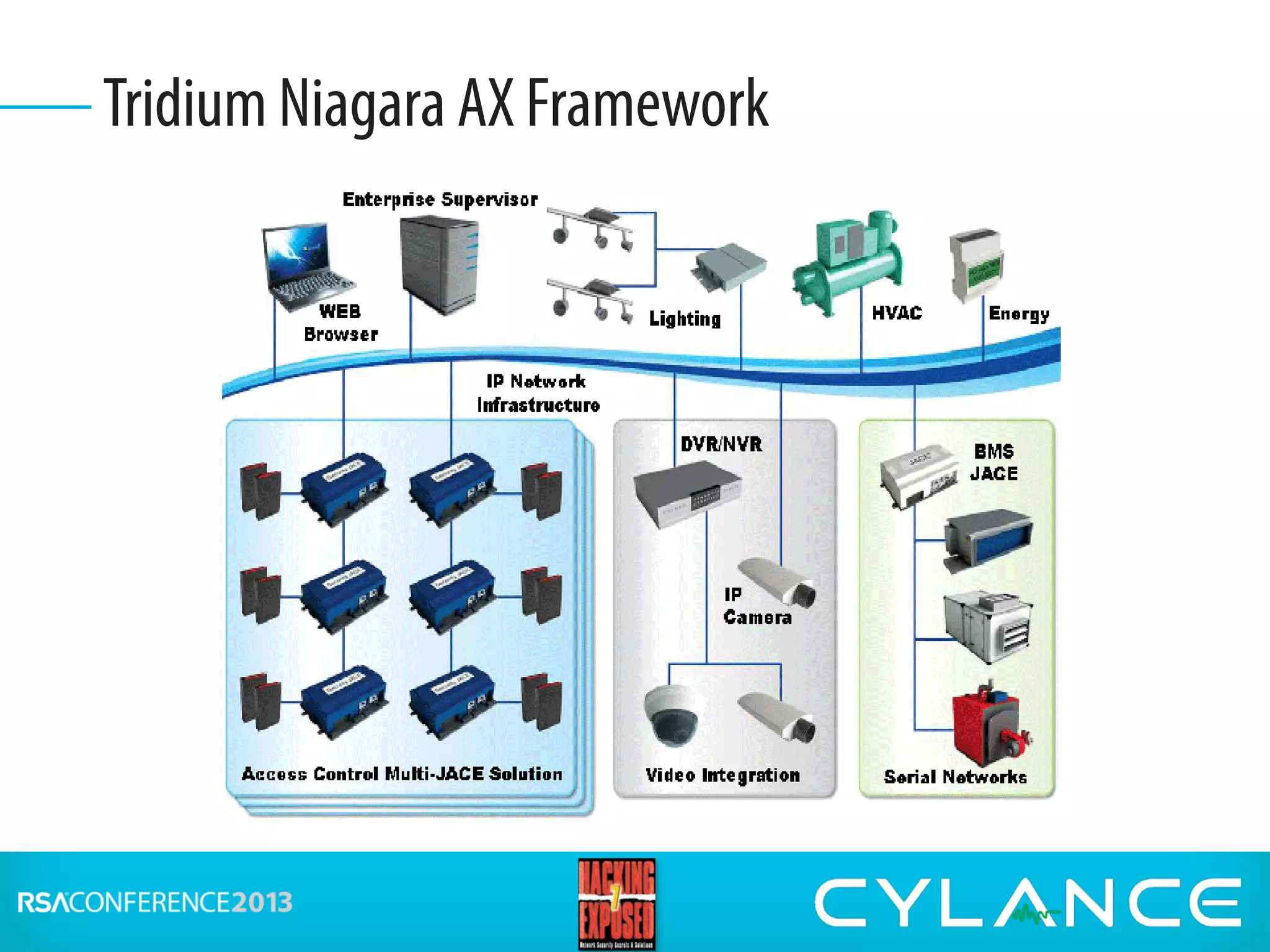
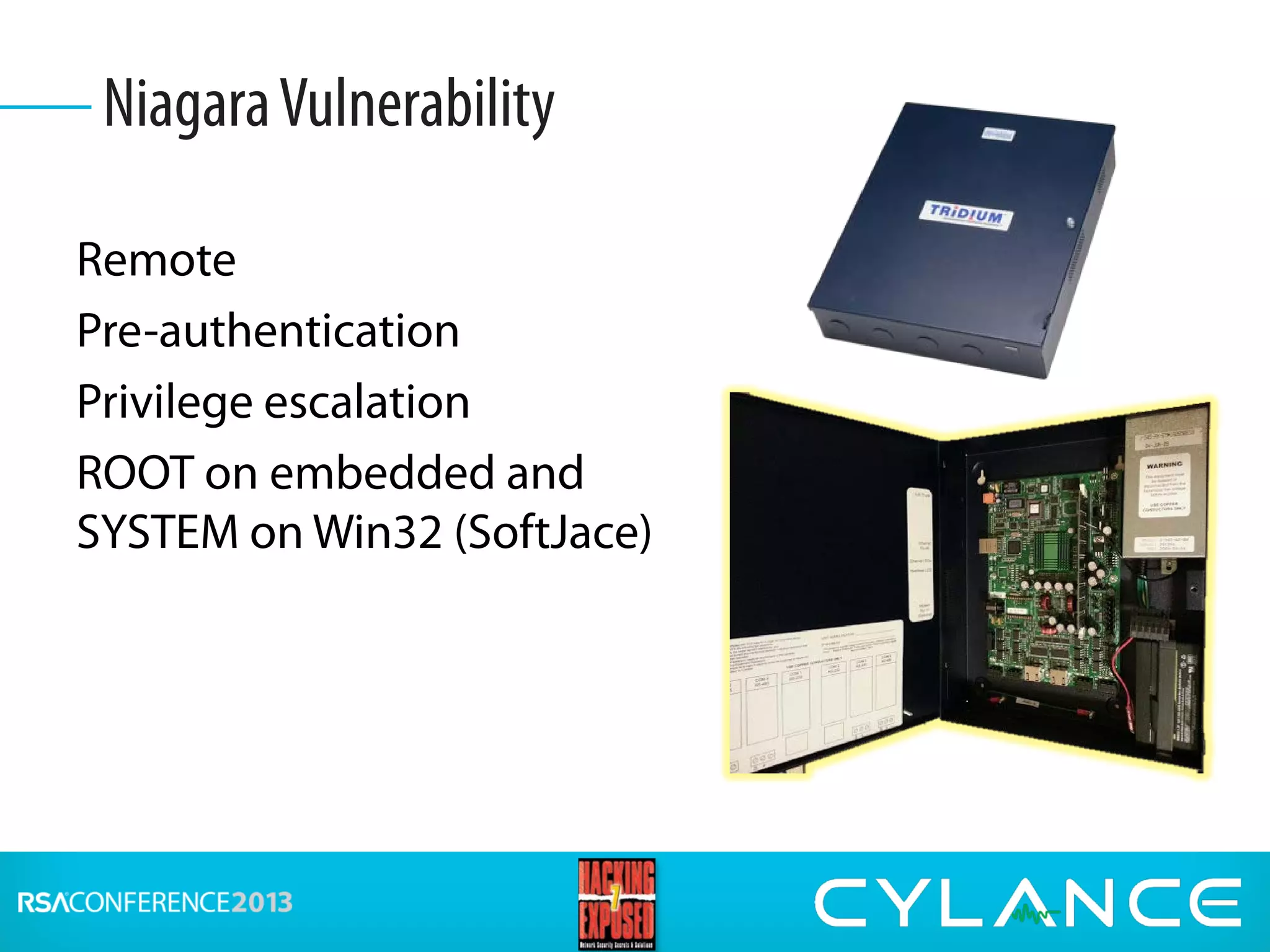
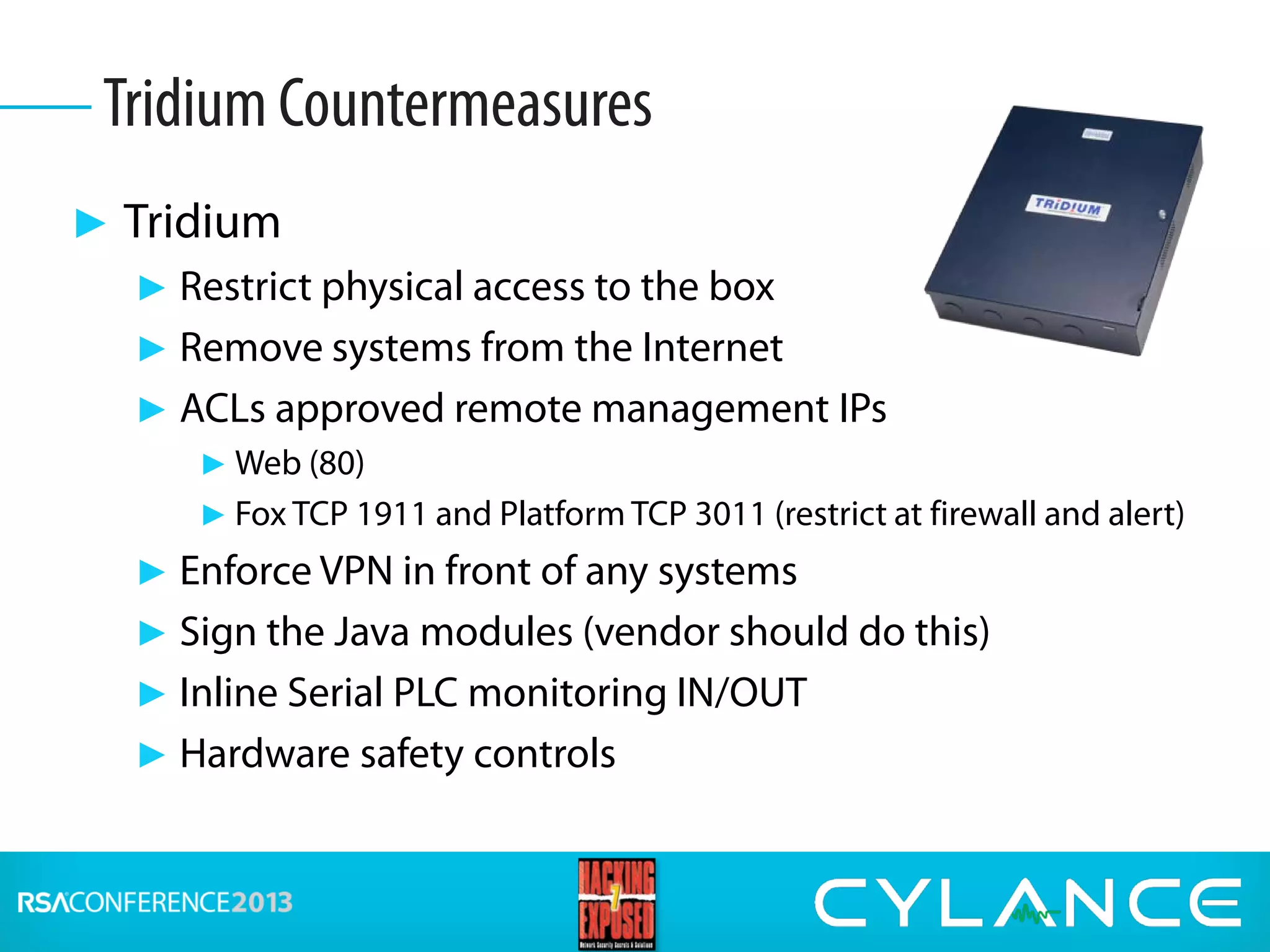
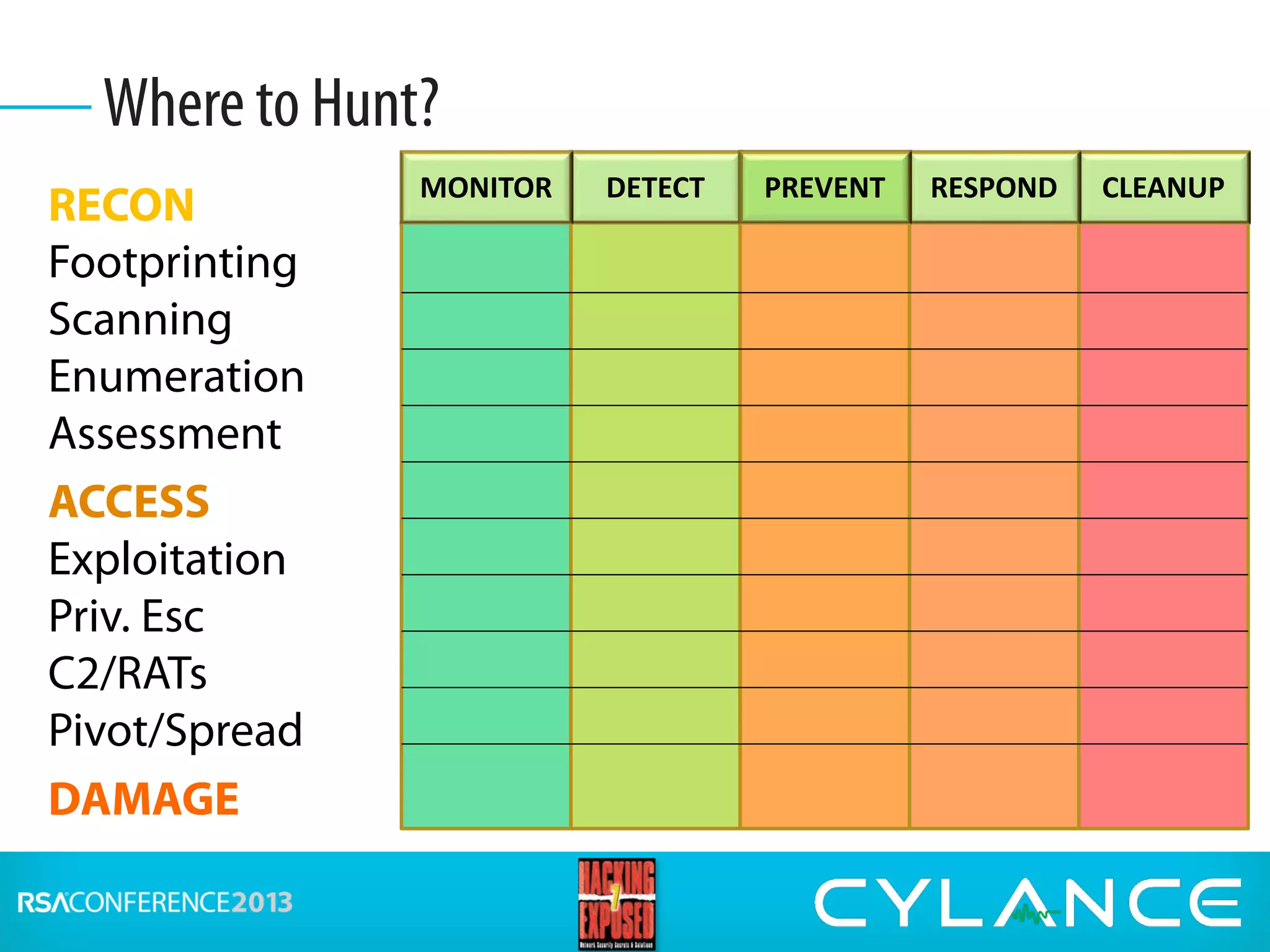
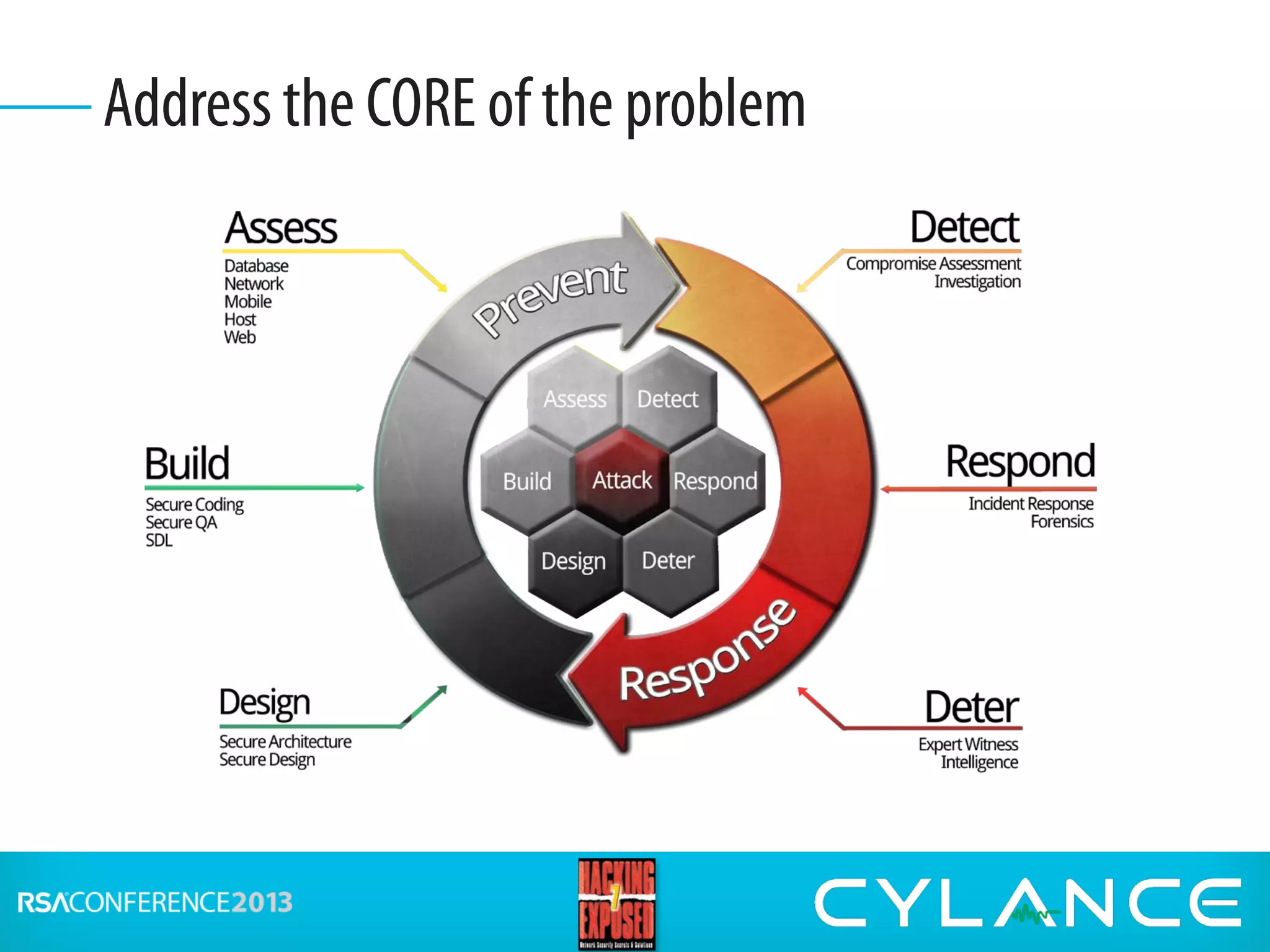
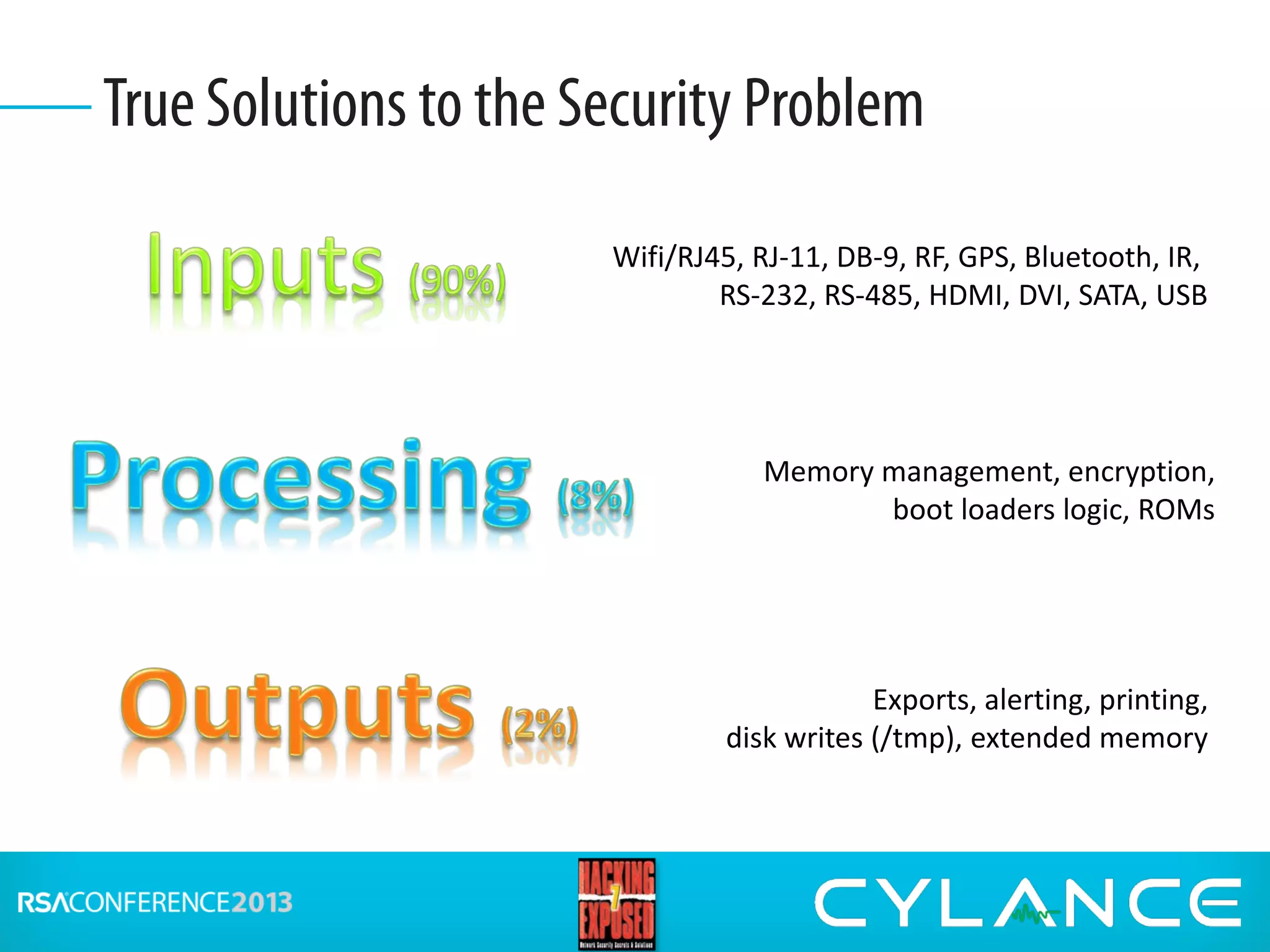
Stuart McClure, CEO of Cylance Inc., gave a presentation on securing embedded systems and devices. He began by noting the vast number of embedded systems worldwide that were designed without security. He then demonstrated live hacks against a Samsung smart TV, a Tridium building management system, and an electronic lockbox. To conclude, he discussed countermeasures organizations can implement to prevent attacks on embedded systems, such as disabling unnecessary ports, patching vulnerabilities, restricting physical and remote access, and using firewalls, IDS systems and encryption.