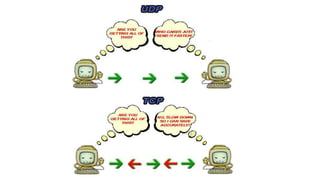
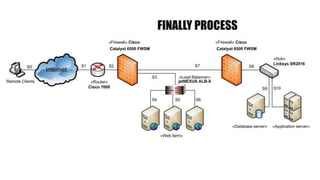
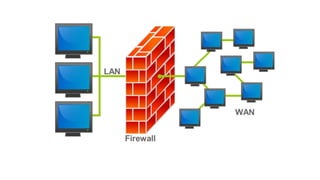
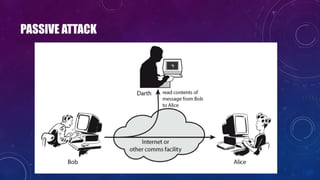
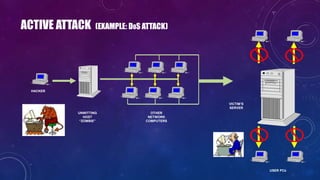
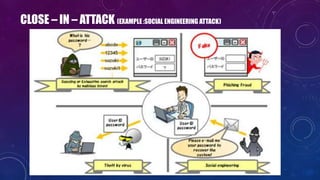
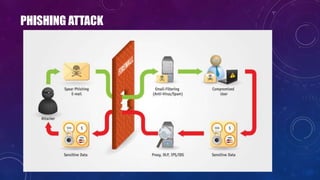
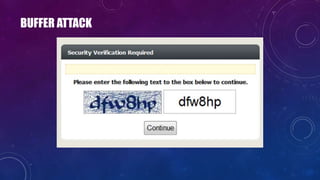
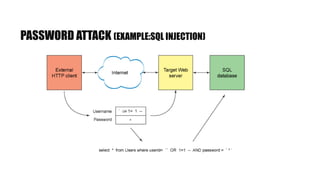
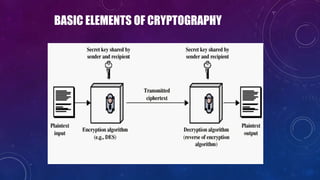
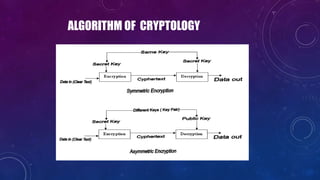
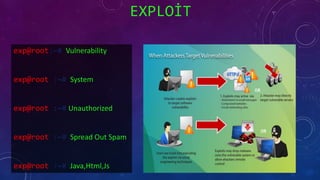
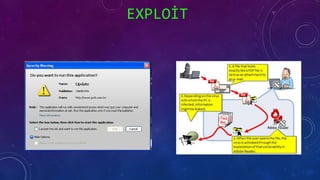
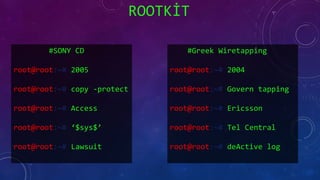
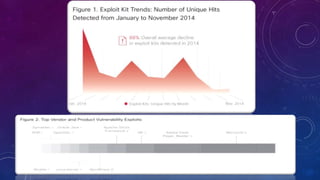
The document discusses e-security and covers several topics including network system structure, types of attacks, cryptography, and malware. It describes the OSI model layers, common attacks like passive attacks and buffer overflows. It also explains cryptography concepts such as encryption algorithms, digital signatures, and how cryptography provides confidentiality, integrity, authentication and non-repudiation. Different types of malware are defined like exploits, worms, rootkits, trojans, adware and spyware along with examples.