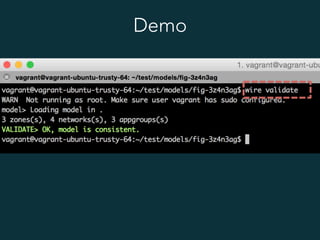
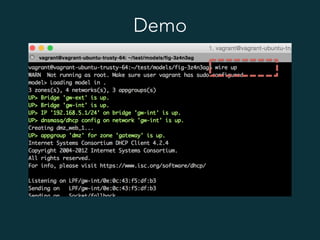
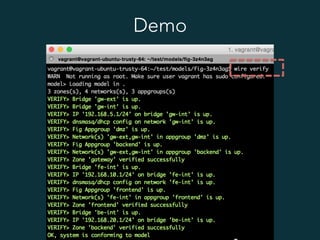
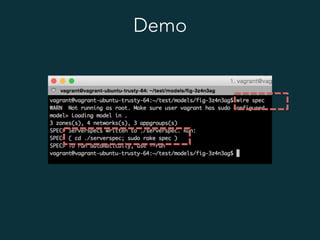
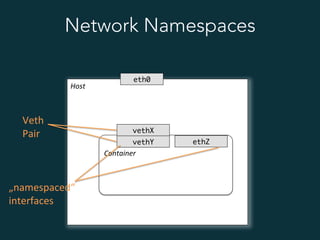
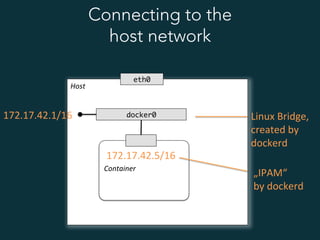
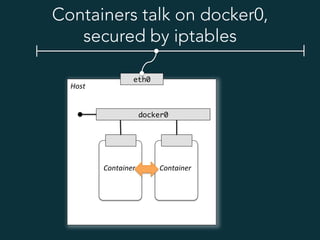
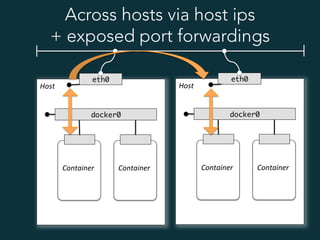
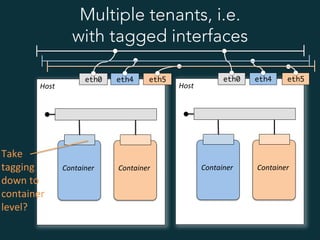
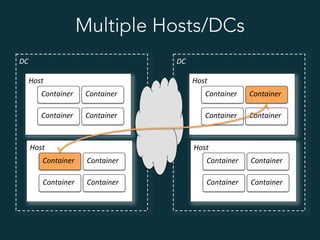
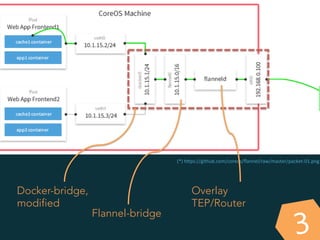
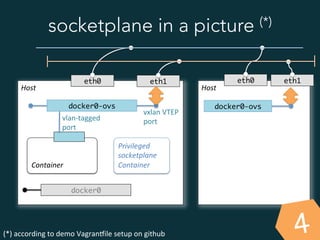
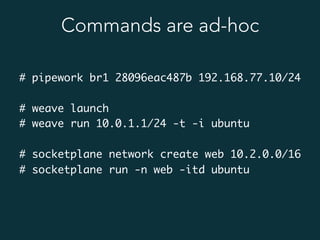
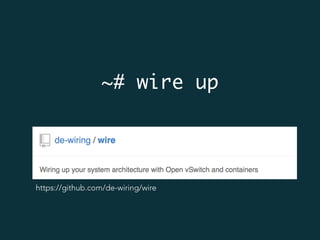
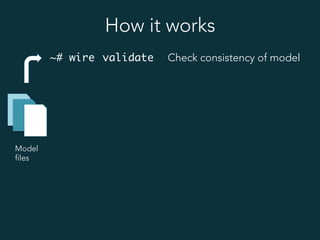
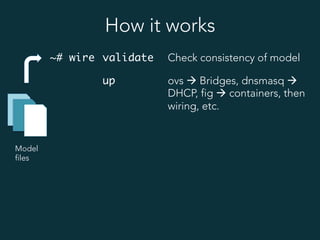
This document summarizes several popular Docker networking solutions including Pipework, Weave, Flannel, Socketplane, and Wire. Pipework provides low-level container networking and integration with existing infrastructure. Weave and Flannel provide overlay networking across hosts. Socketplane uses Open vSwitch and supports integration with existing Open vSwitch networks. Wire is a tool that models and automates multi-host Docker environments using configuration files to validate, deploy, and test networks and applications.













![Model
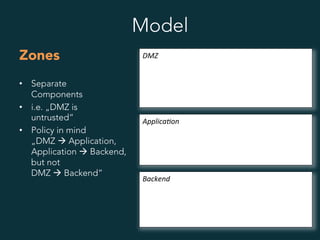
Networks
• Equals
Open vSwitch bridge
• Have names
network ranges
• Host may have an ip
on that network
• May be attached to
host interfaces
• May serve dhcp using
dnsmasq
DMZ
Applica8on
Backend
dmz-ext 10.0.1.0/24
dmz-int 10.0.2.0/24
App-int 10.1.0.0/16
be-int 10.37.15.0/24
(dhcp 10.37.15.[20..29])
10.1.1.15
10.37.15.1](https://image.slidesharecdn.com/dockerffmmeetup20150113networking-150126053405-conversion-gate01/85/Dockerffm-meetup-20150113_networking-32-320.jpg)