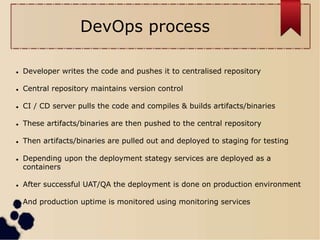
This document discusses DevSecOps and provides information about integrating security practices into the DevOps process. It describes how DevSecOps improves upon traditional DevOps by adding security checks to code, containers, and infrastructure. These checks help detect vulnerabilities, sensitive information, and non-compliance before code is deployed. The document also introduces the open-source auditing tool Lynis, which scans servers to identify vulnerabilities and compliance issues across the operating system, network settings, authentication methods, and more.















![Server Hardening
Open source audit tool – Lynis (2/3)
Installing & using Lynis
1] Create /etc/yum.repos.d/cisofy-lynis.repo
# vi /etc/yum.repos.d/cisofy-lynis.repo
and add
[lynis]
name=CISOfy Software - Lynis package
baseurl=https://packages.cisofy.com/community/lynis/rpm/
enabled=1
gpgkey=https://packages.cisofy.com/keys/cisofy-software-rpms-public.key
gpgcheck=1
priority=2
and save the file](https://image.slidesharecdn.com/devsecops-191007230831/85/DevSecOps-17-320.jpg)
![Server Hardening
Open source audit tool – Lynis (3/3)
Lynis (continued)
2] Update additional packages
# yum update ca-certificates curl nss openssl
3] Installing Lynis
# yum install lynis
3] Running audit
# lynis audit system](https://image.slidesharecdn.com/devsecops-191007230831/85/DevSecOps-18-320.jpg)
