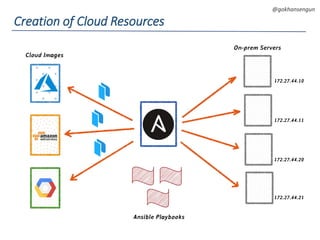
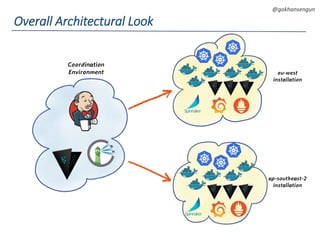
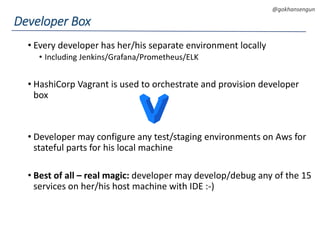
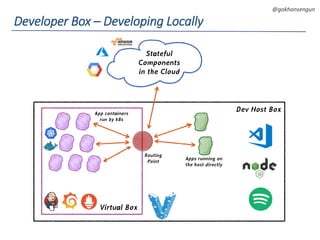
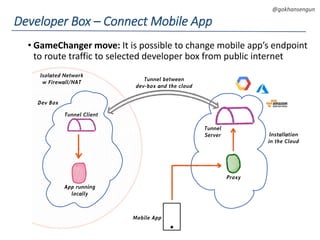
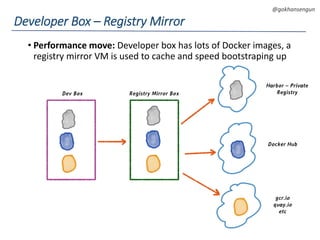
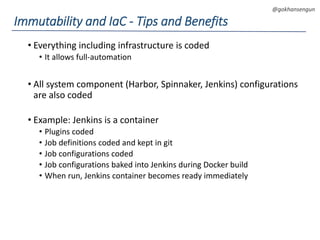
This document summarizes a talk about migrating a cloud native application running on AWS to Kubernetes. The application consisted of 15 microservices written in various languages and heavily using AWS services across 3 regions. The goals of the migration were to make the application cloud agnostic, improve developer experience, prevent single points of failure, and enable auto-scaling. Key aspects of the migration included containerizing services, using Kubernetes for orchestration, Terraform for infrastructure provisioning, and implementing immutable infrastructure with configuration and secrets management. A CI/CD pipeline was also established using Jenkins, Spinnaker, and other tools.