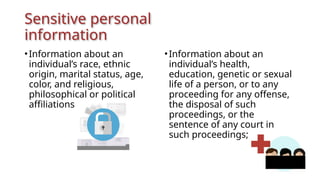
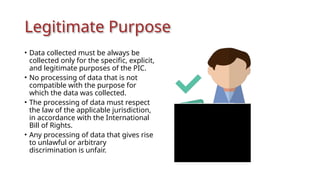
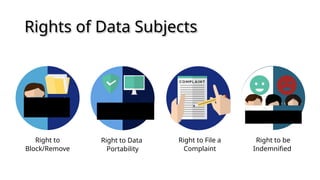
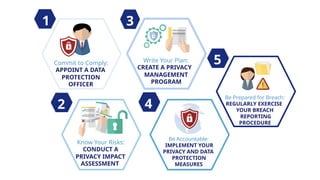
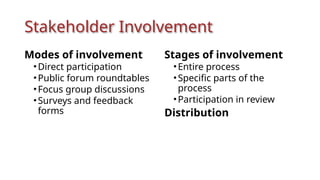
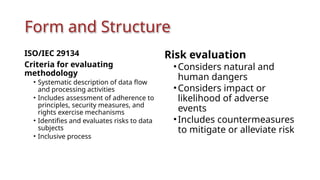
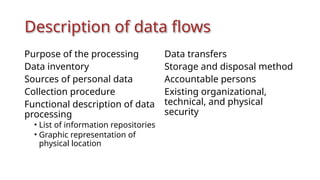
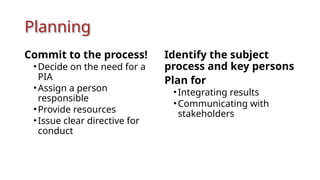
The document outlines a technical learning session on data privacy and protection held on April 17-18, 2018, focusing on the laws, principles, and compliance requirements associated with data privacy in the Philippines. It covers key topics such as personal and sensitive data definitions, the importance of consent, rights of data subjects, and conducting privacy impact assessments. Emphasizing the significance of a structured privacy management program, it provides guidelines for organizations on mitigating risks associated with data processing and the necessary technical provisions for protecting personal data.