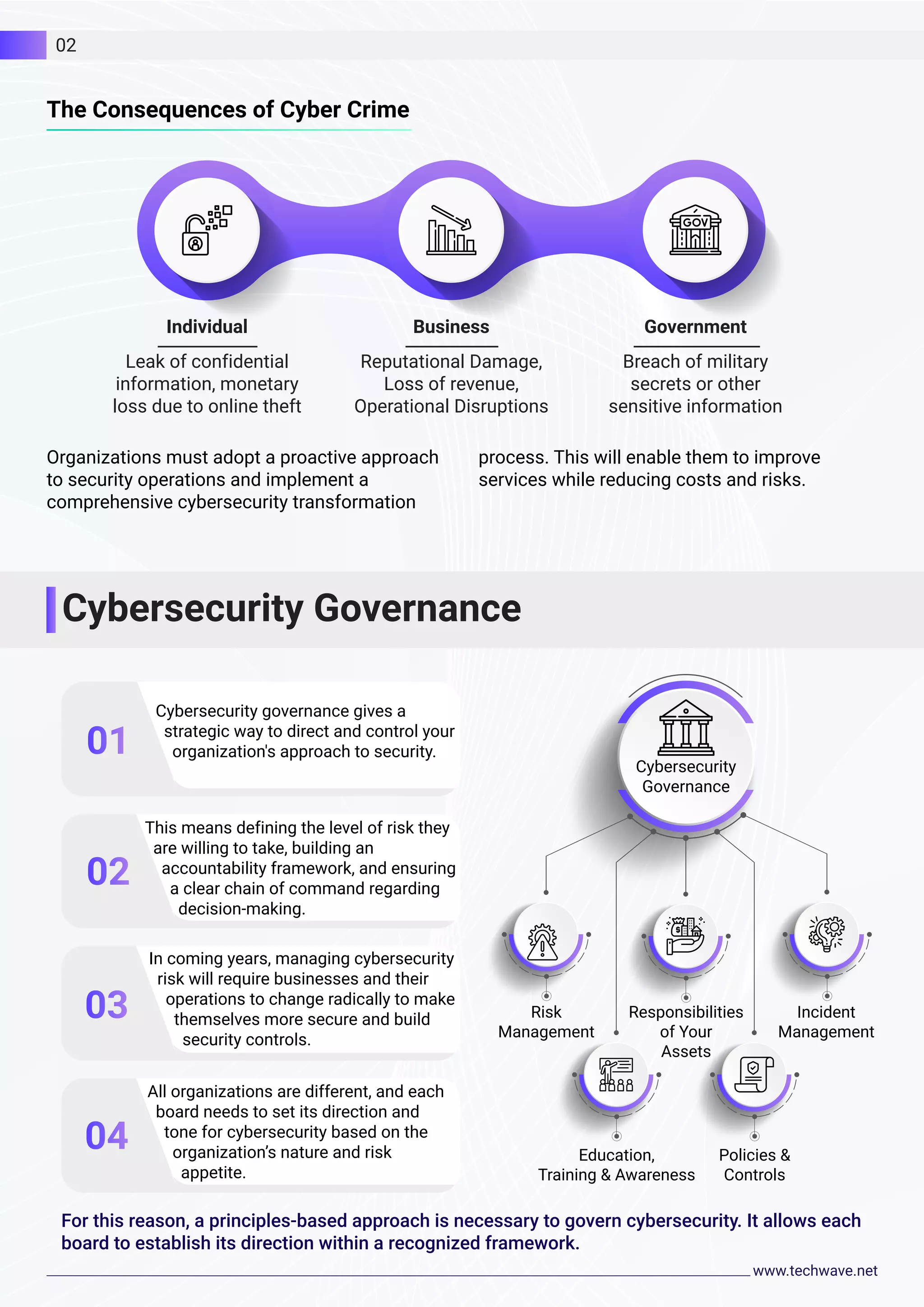
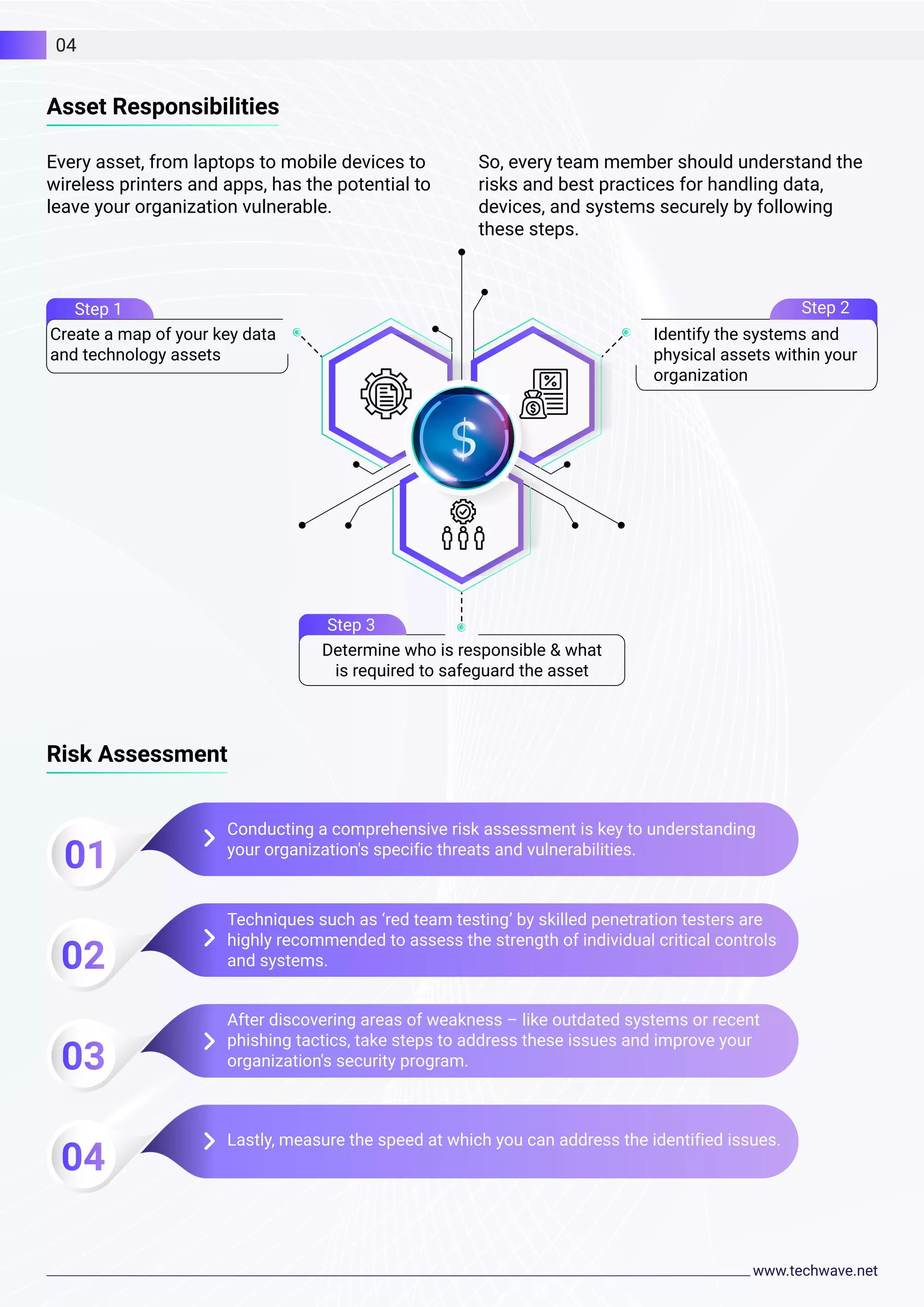
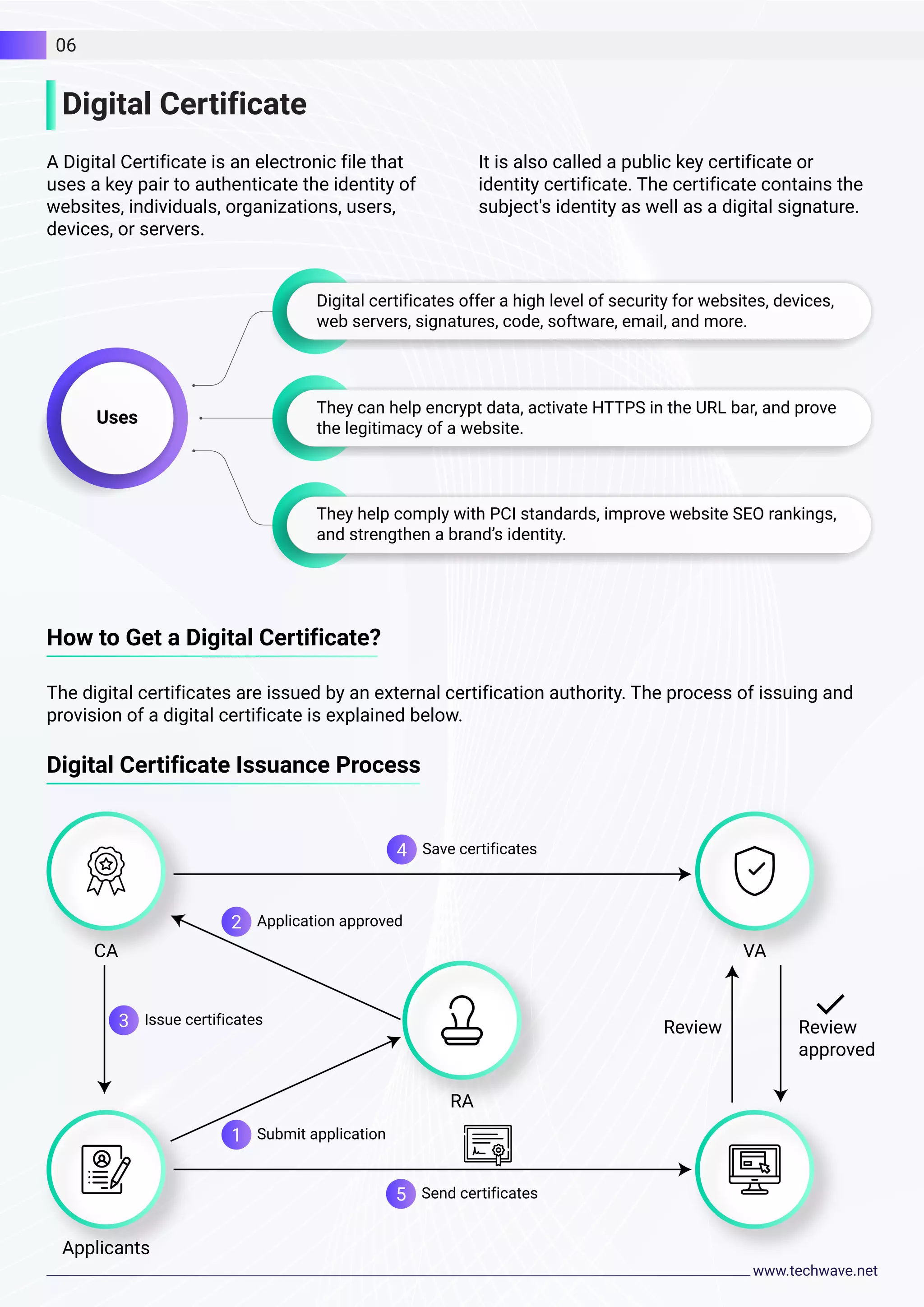
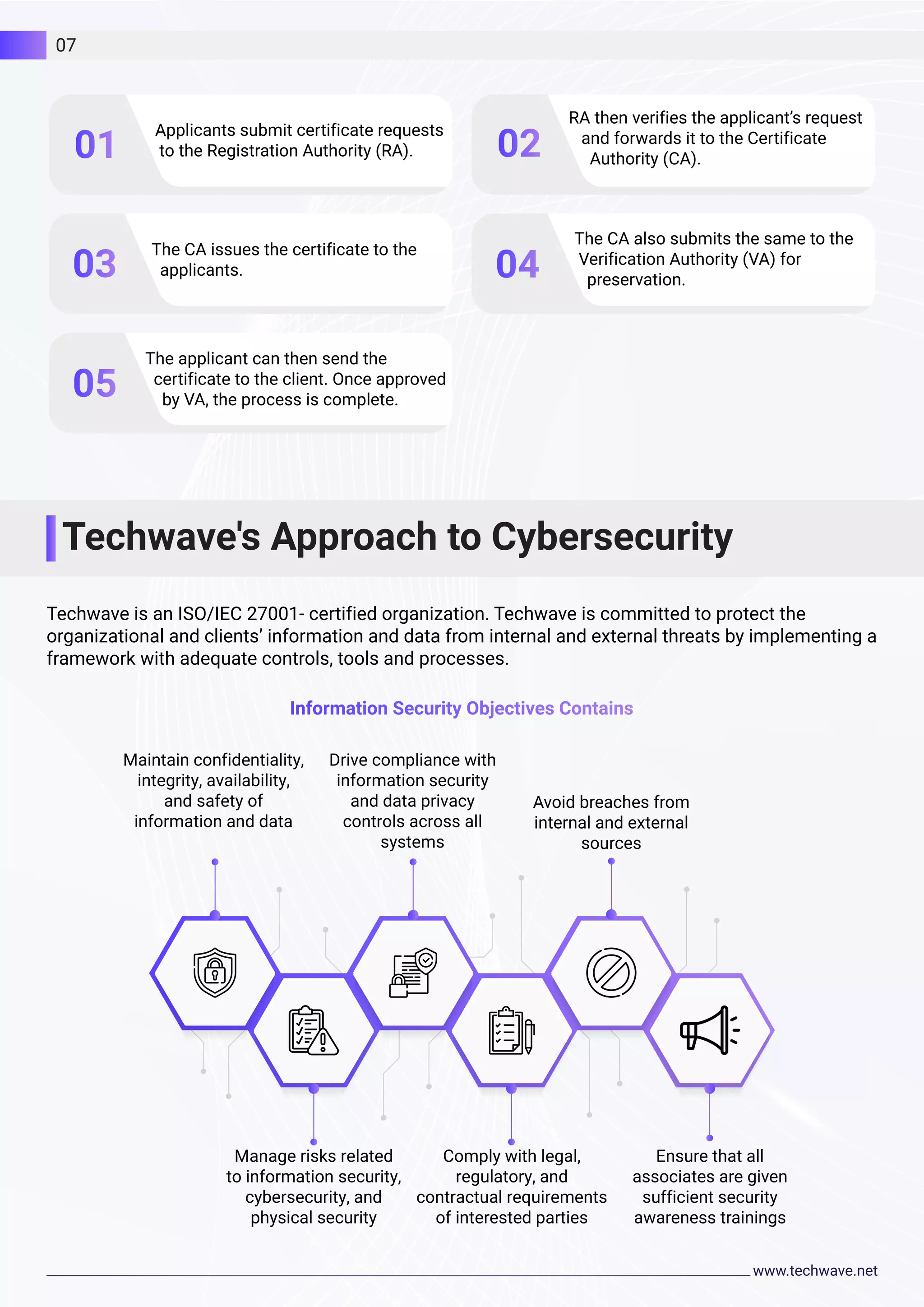
The document discusses cybersecurity and Techwave's approach. It notes that cyber attacks are a threat to businesses and their privacy. Techwave provides cybersecurity tools and technologies to help organizations stay protected. Their solutions include a defense-in-depth strategy with multiple security layers, digital certificates for authentication, and comprehensive security assessments and plans. Techwave aims to maintain data security, manage risks, avoid breaches, and ensure compliance.