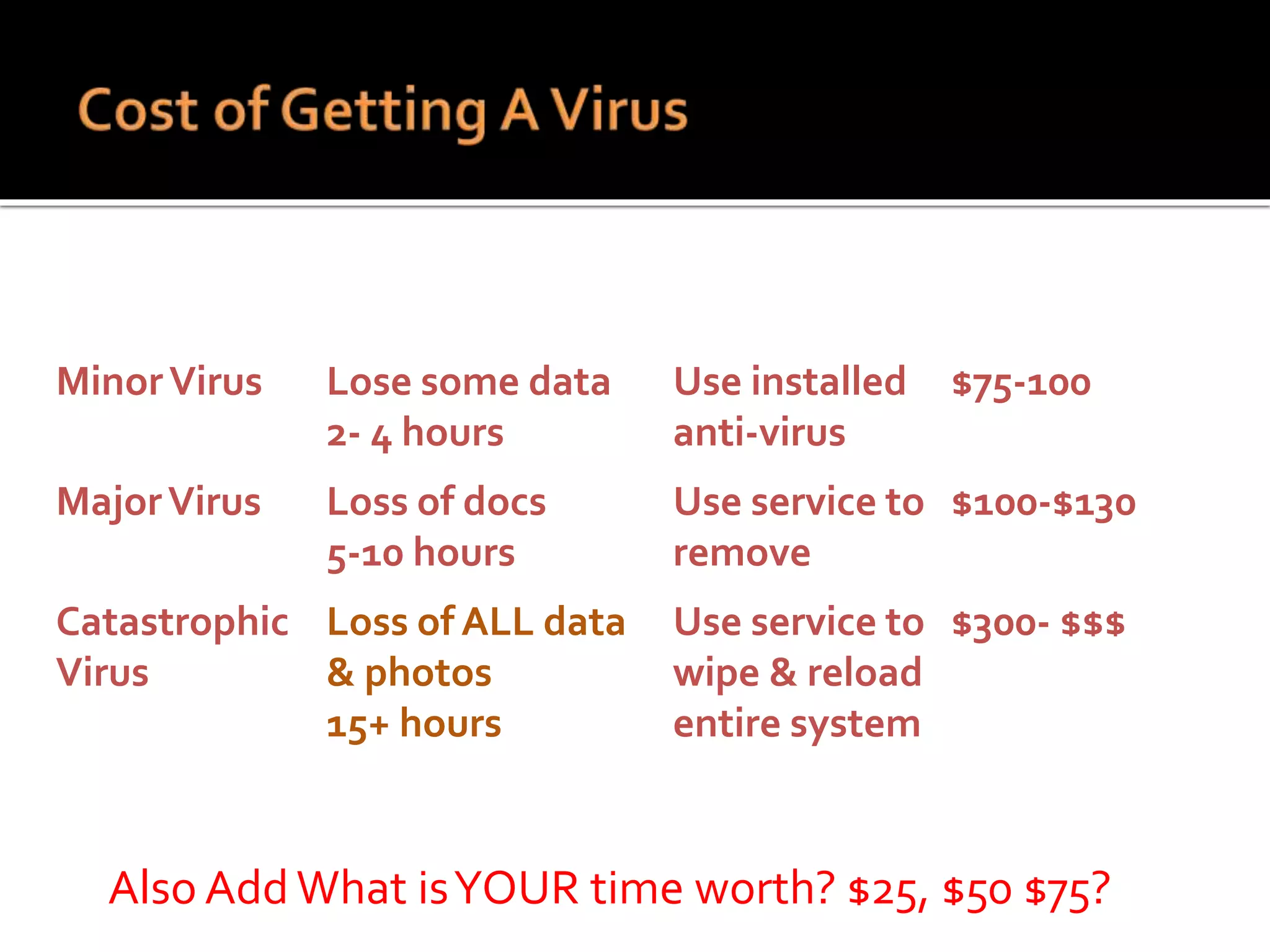
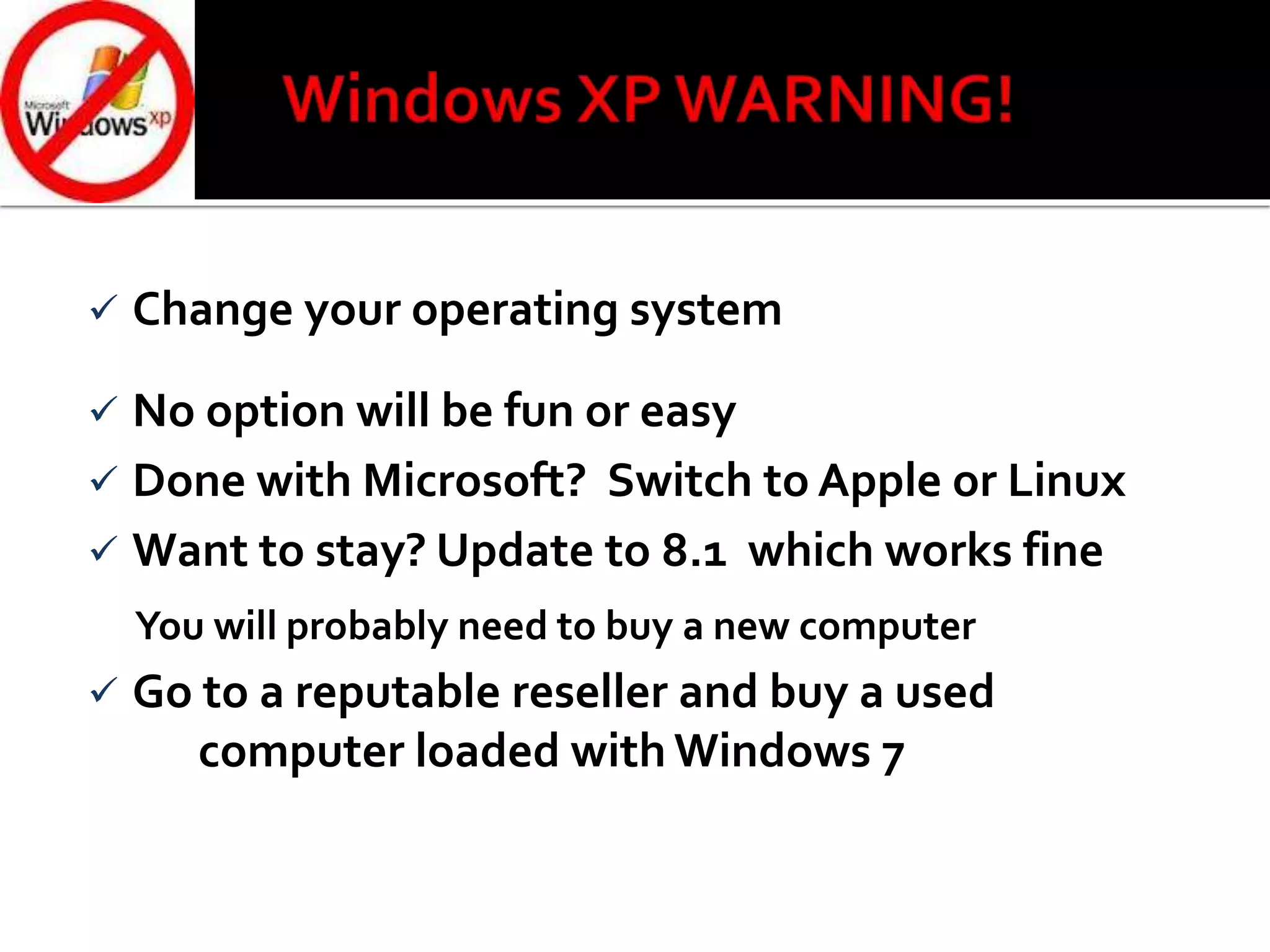
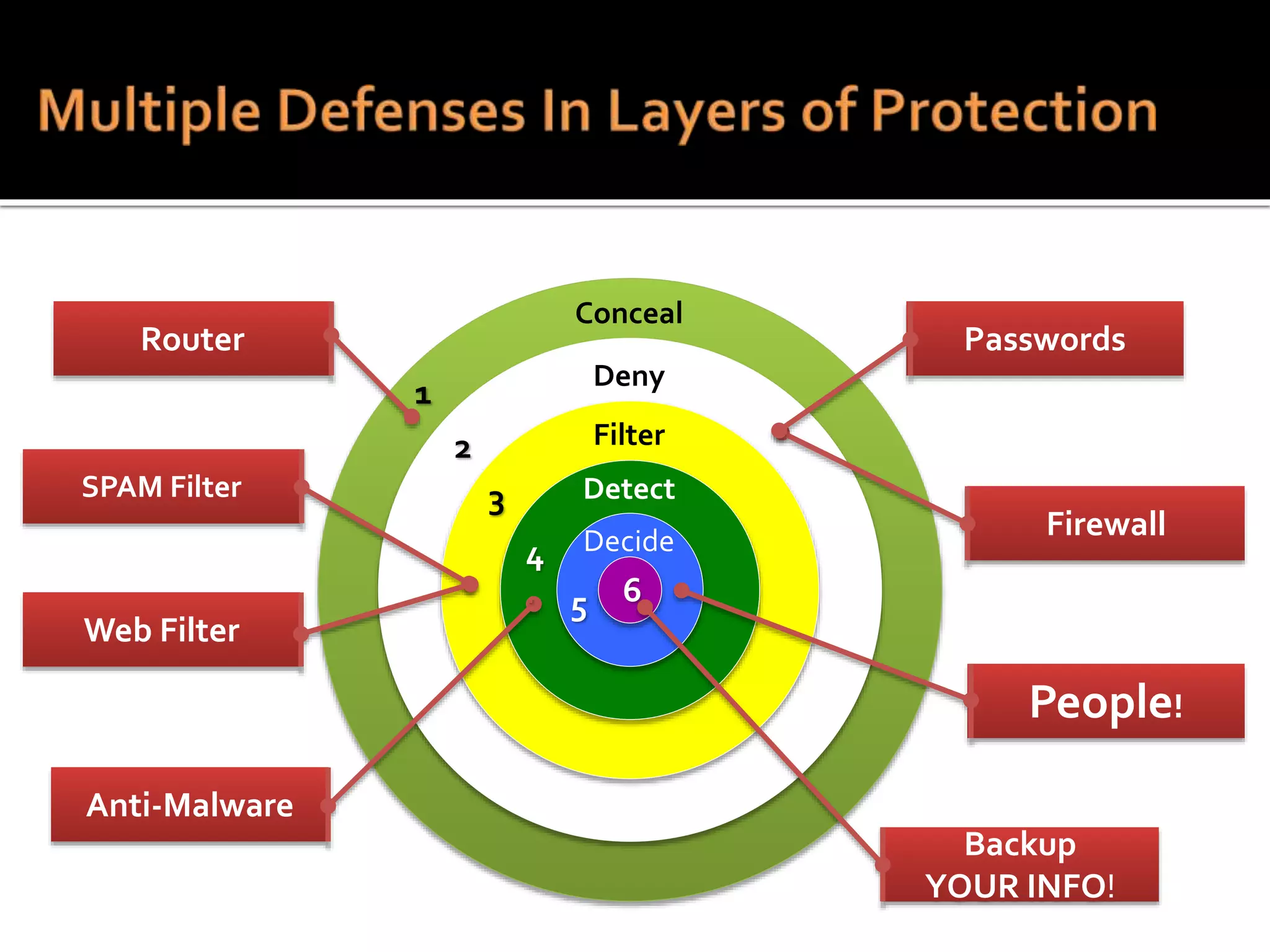
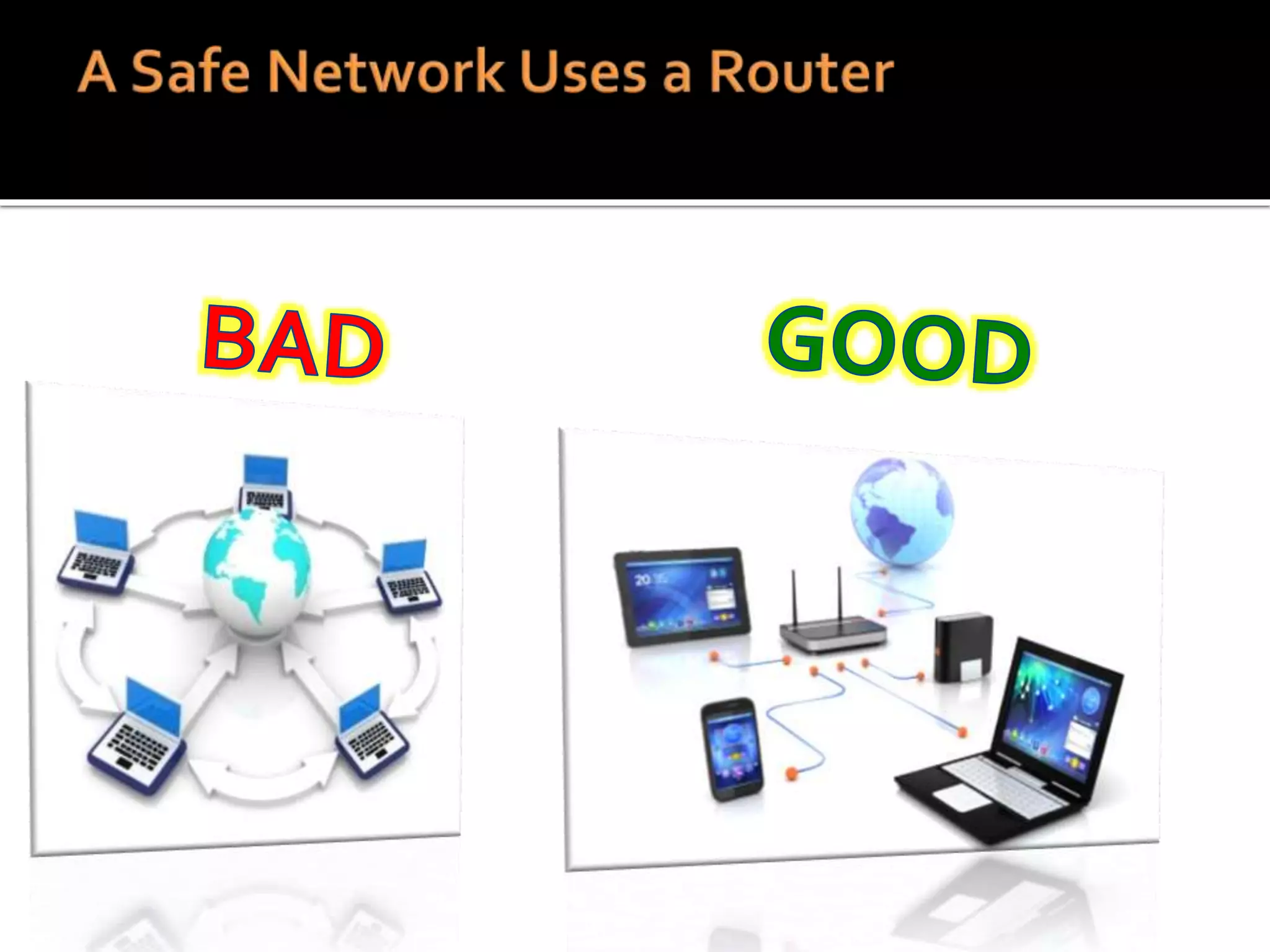
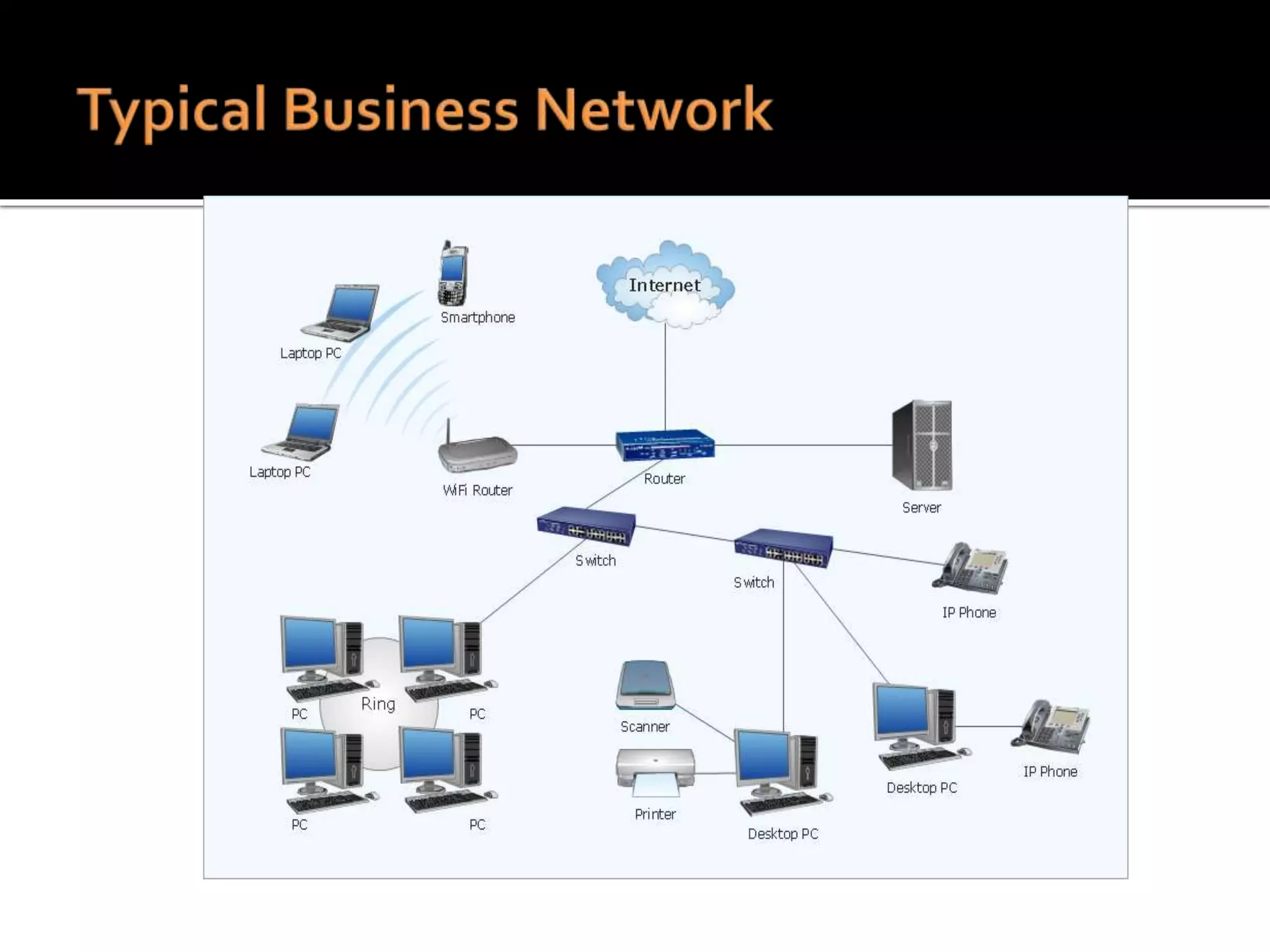
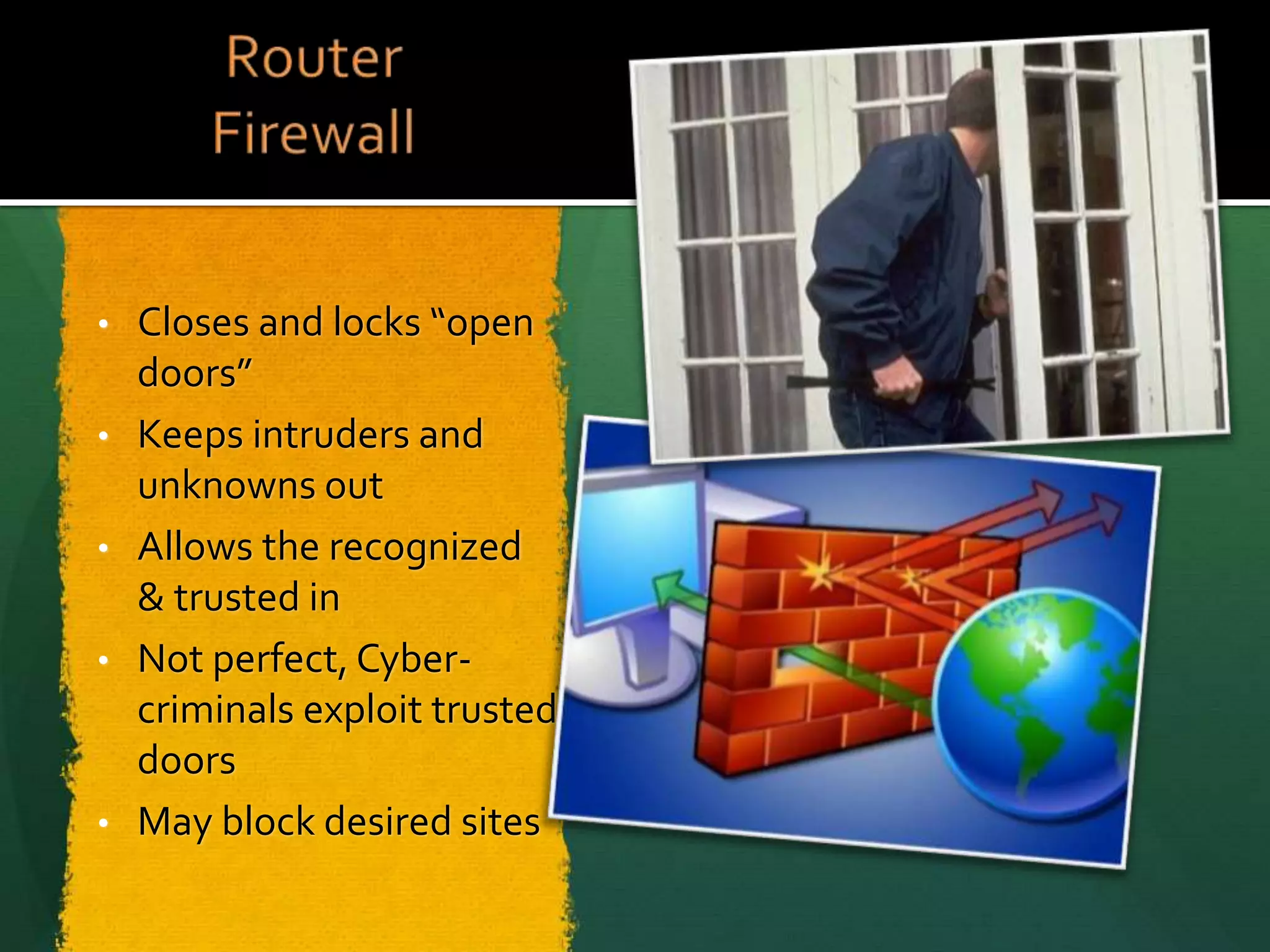
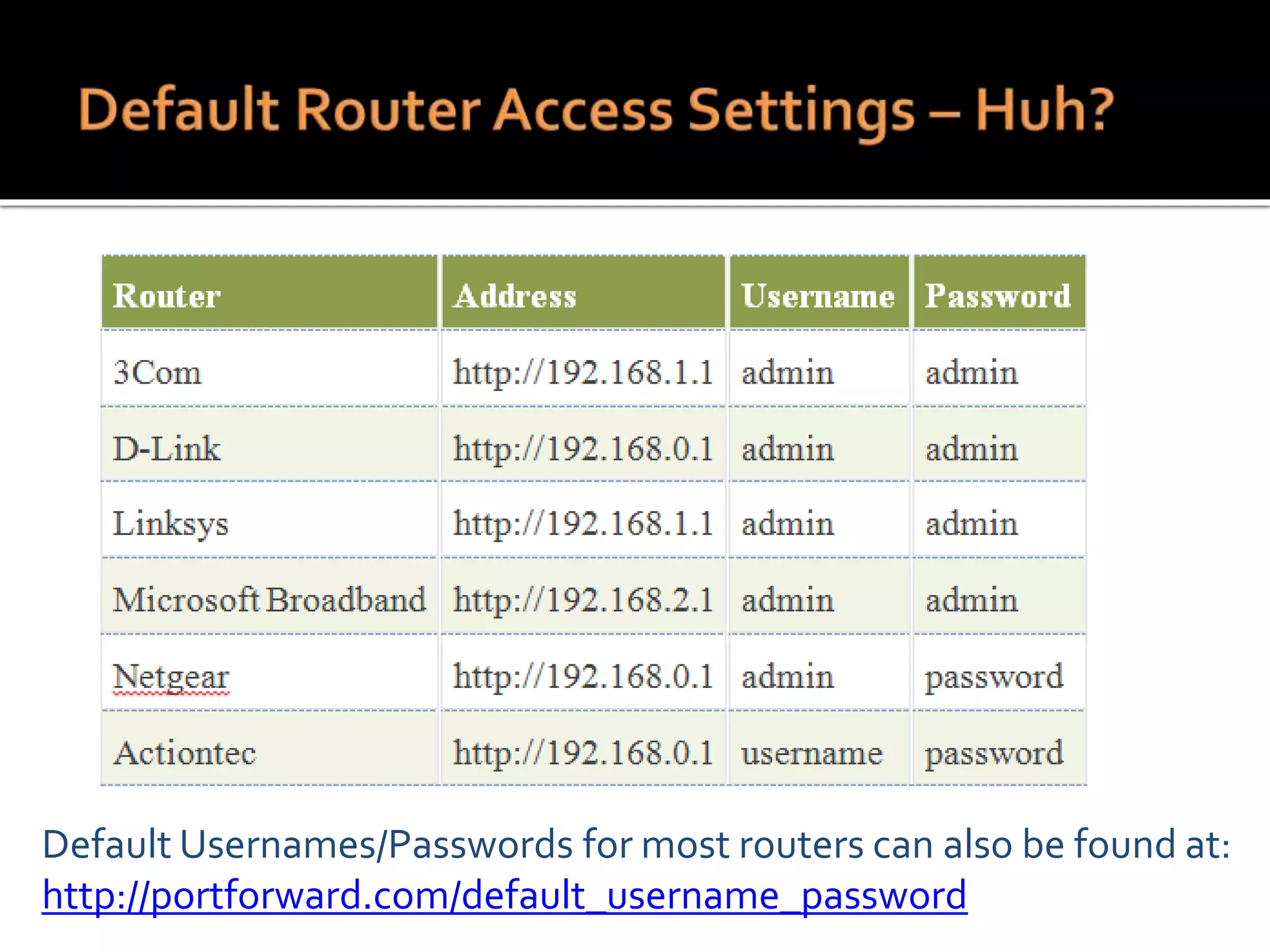
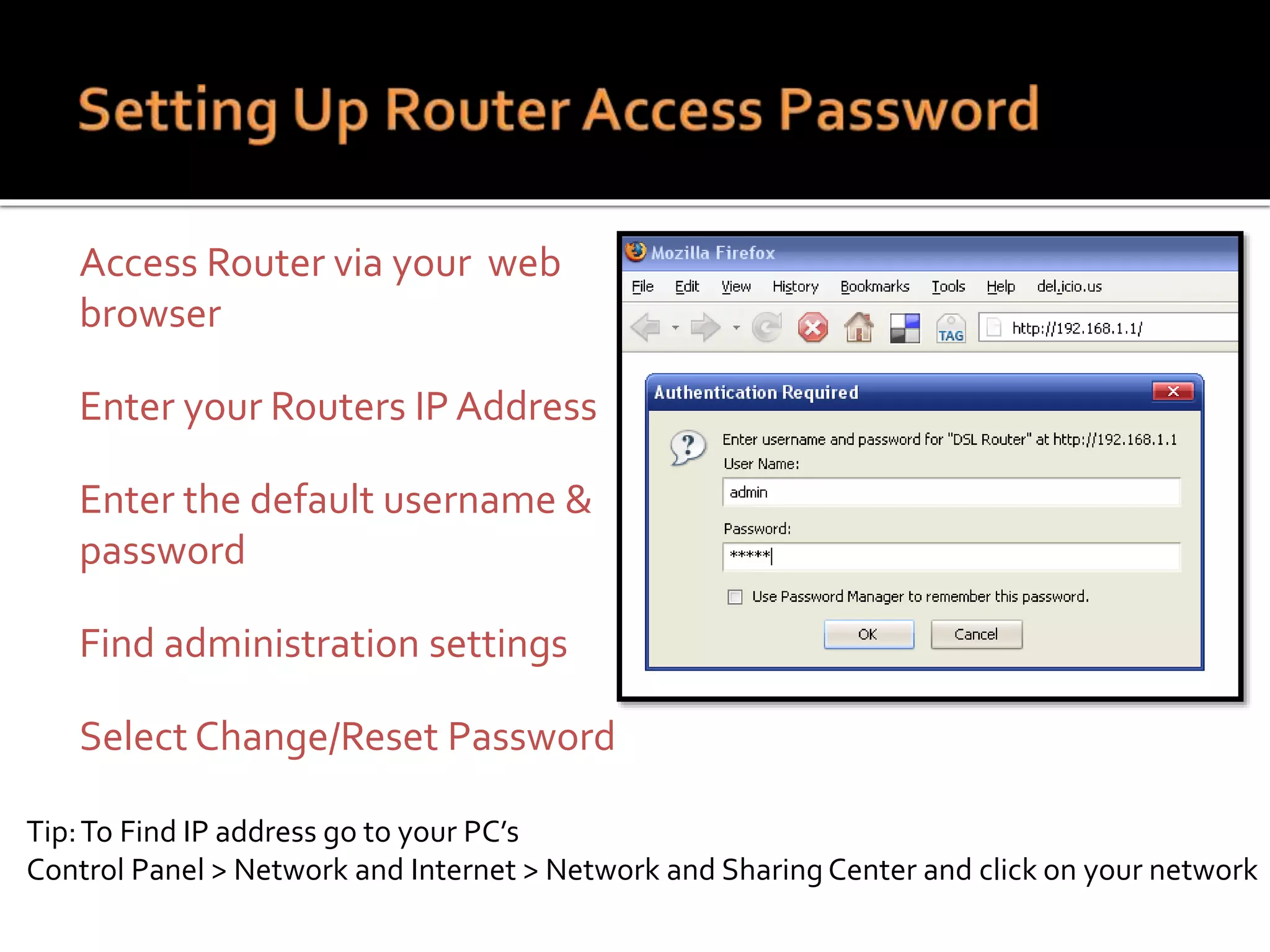
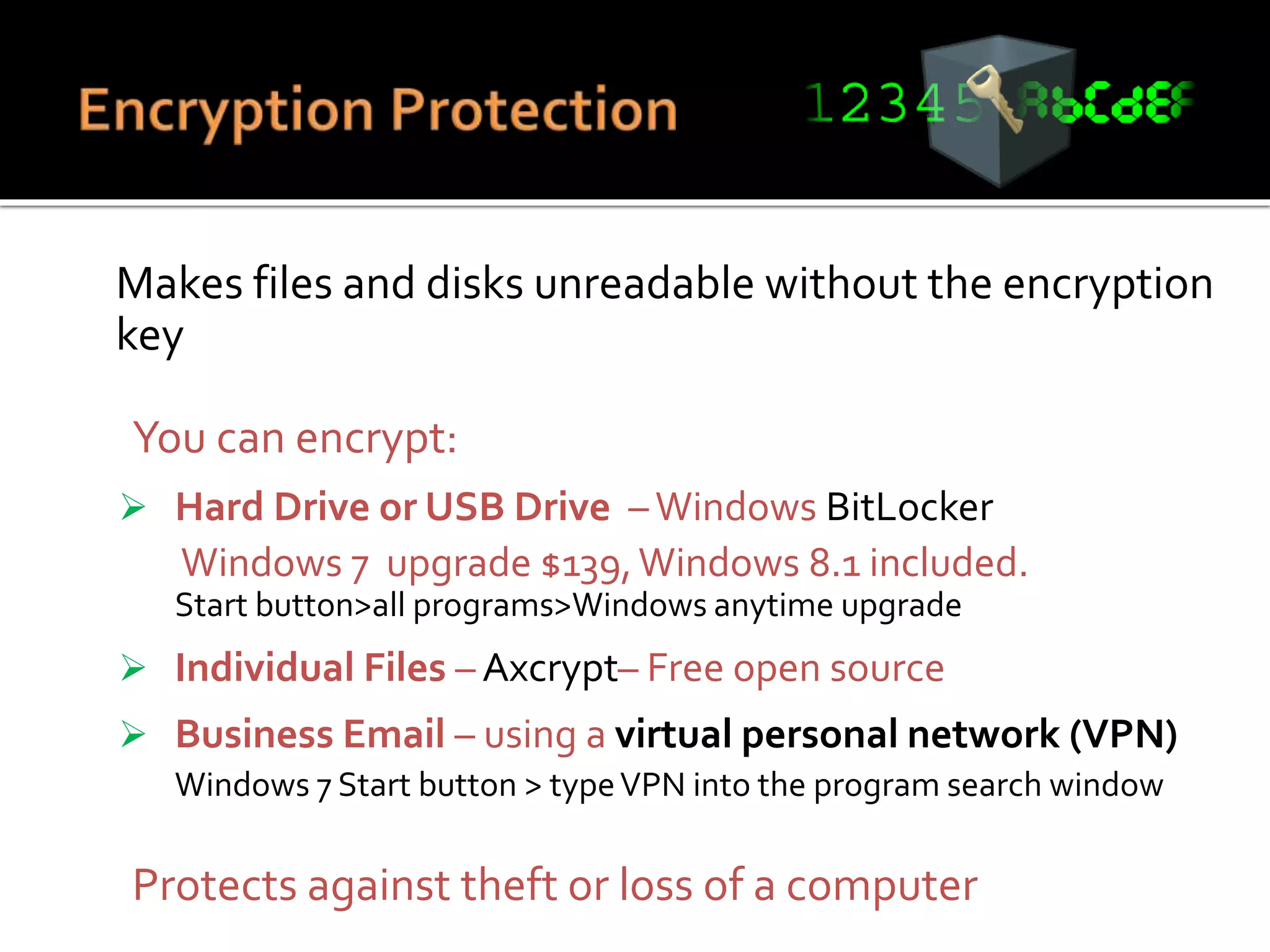
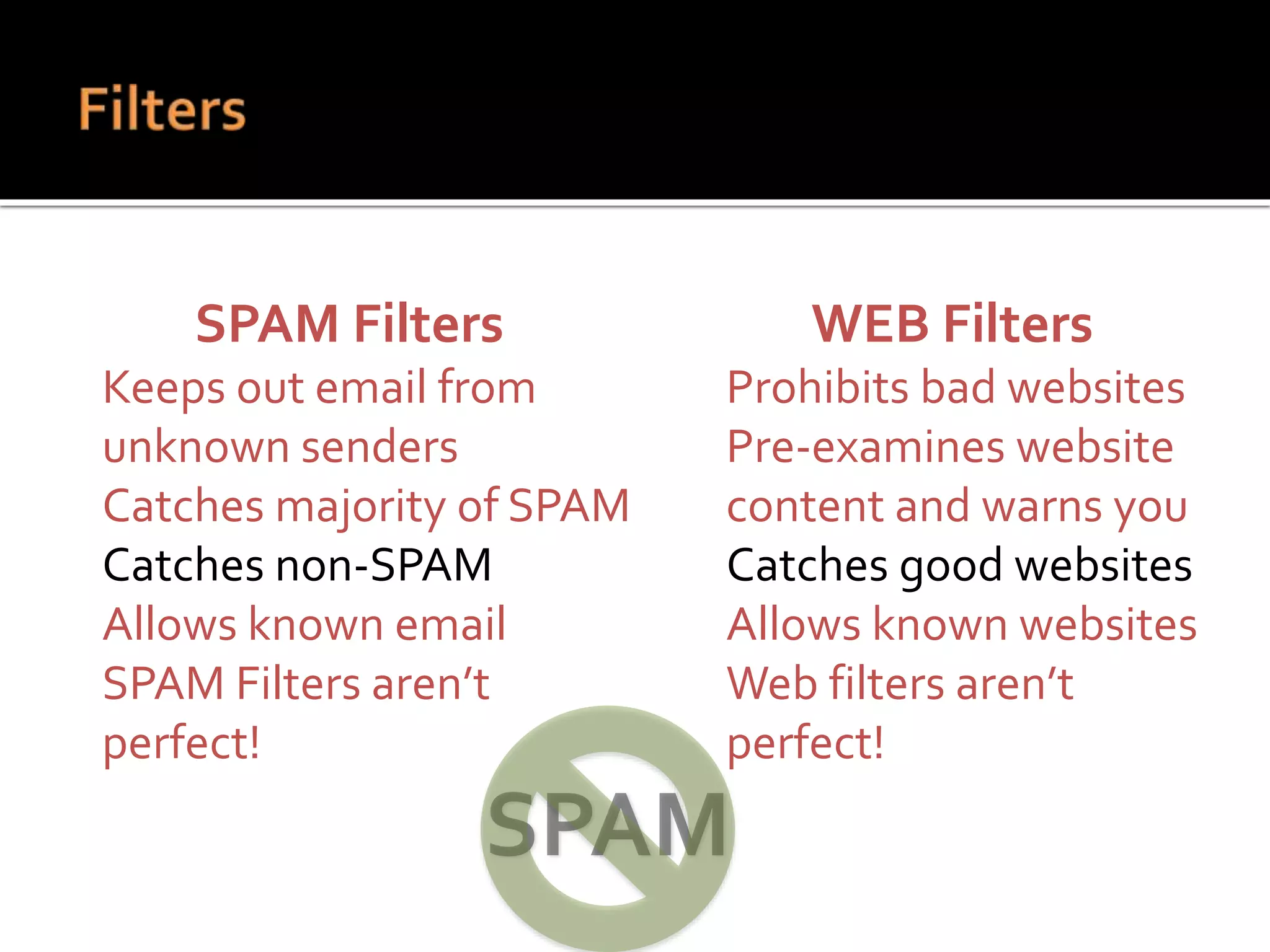
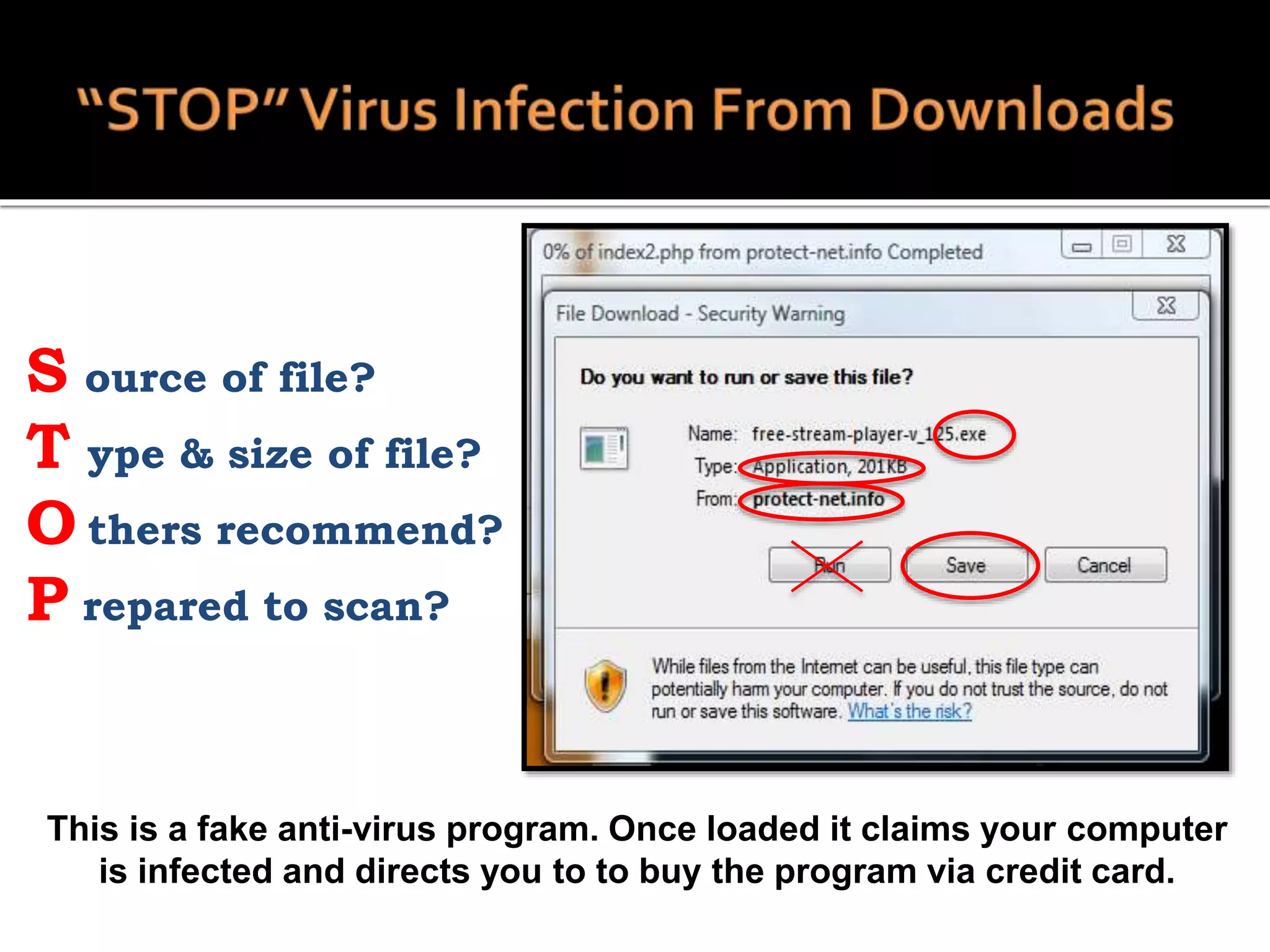
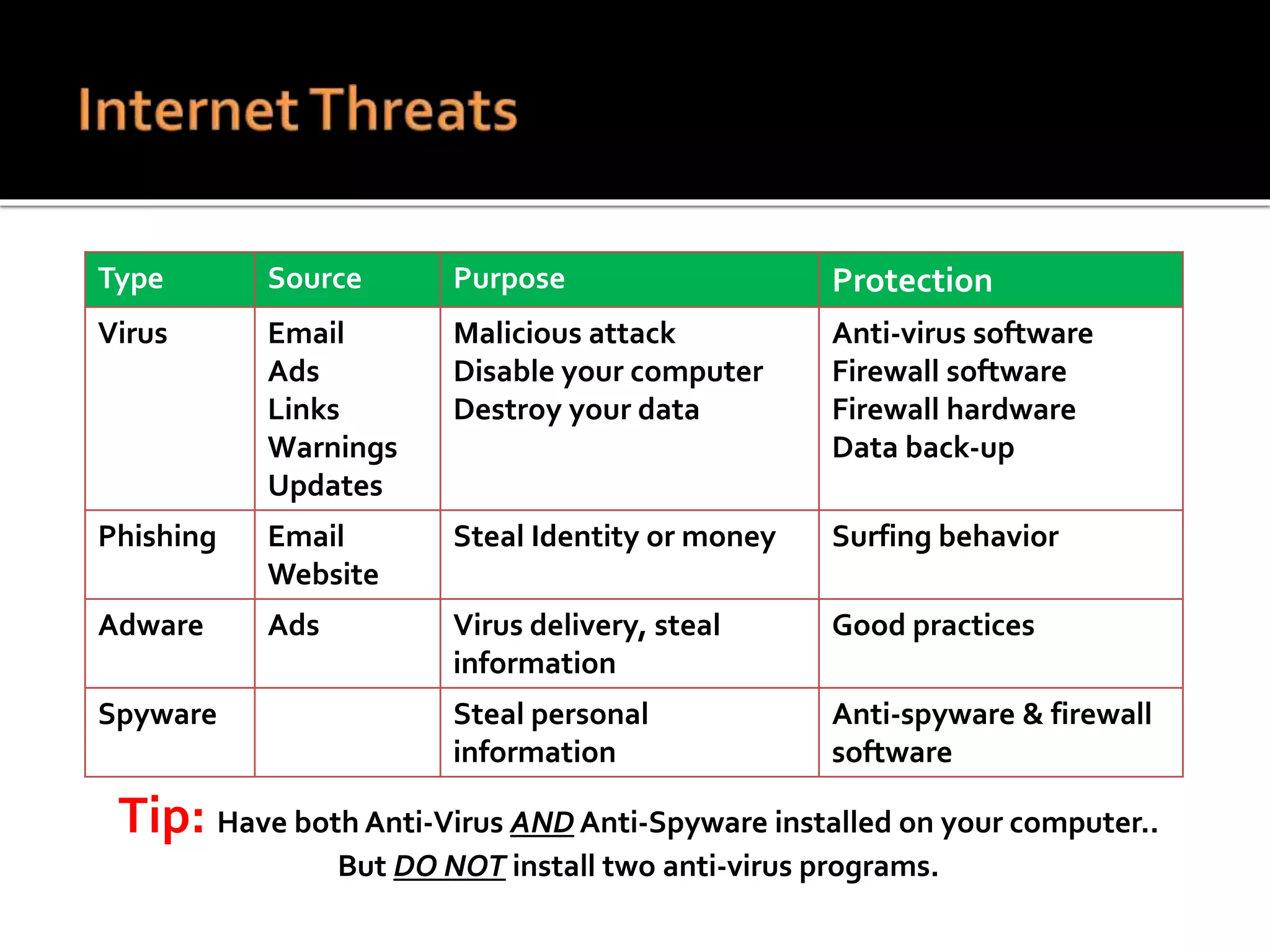
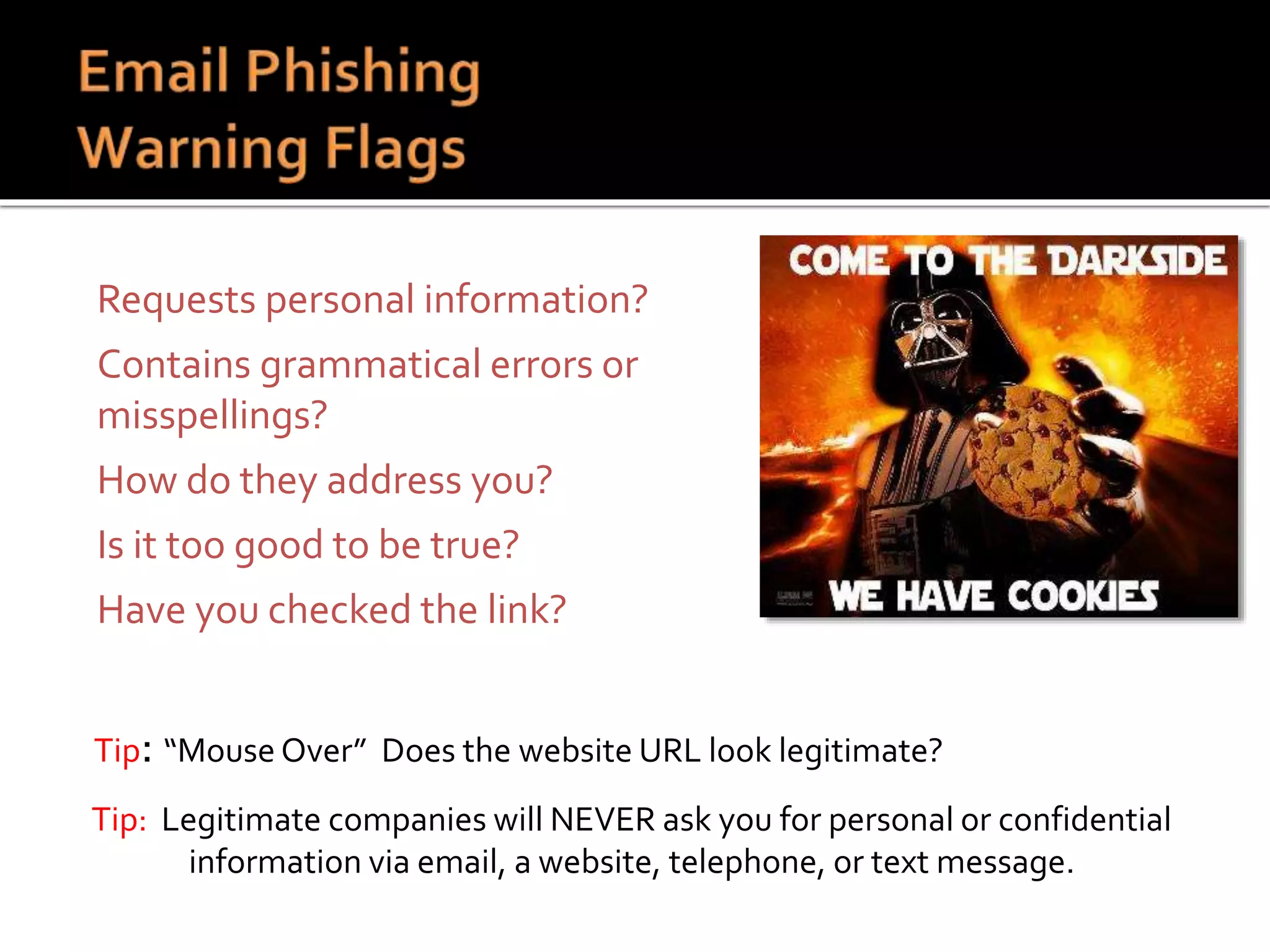
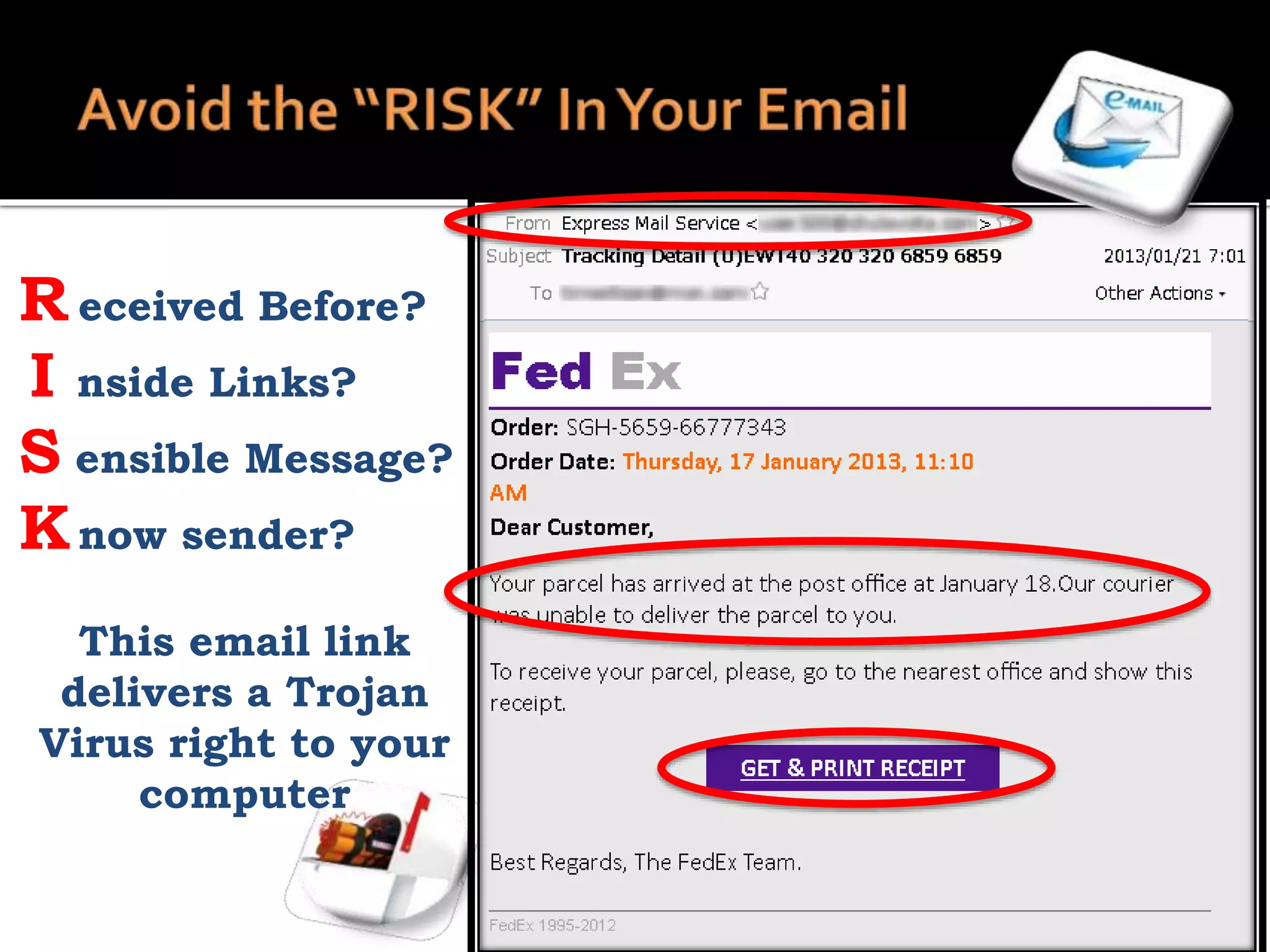
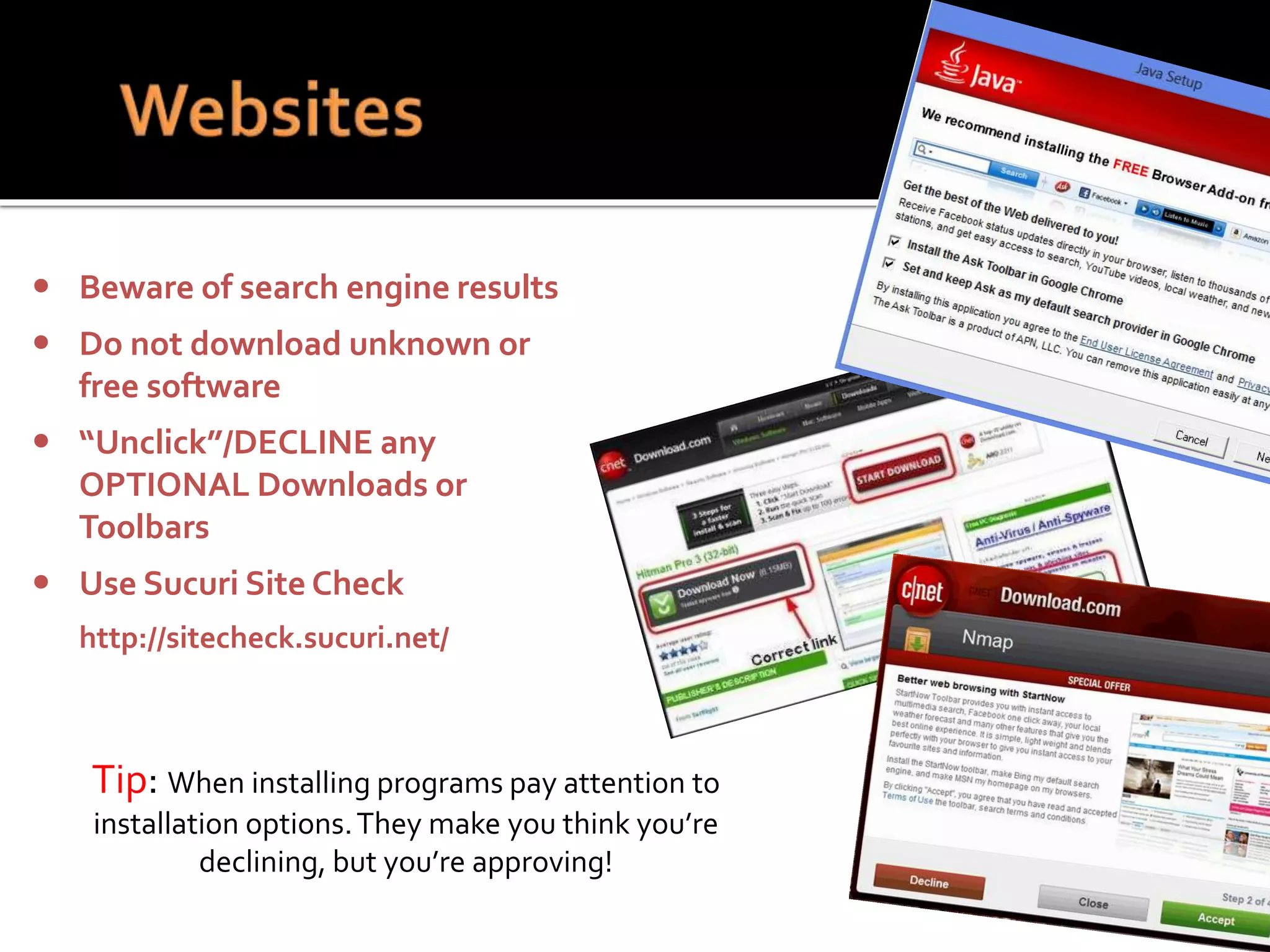
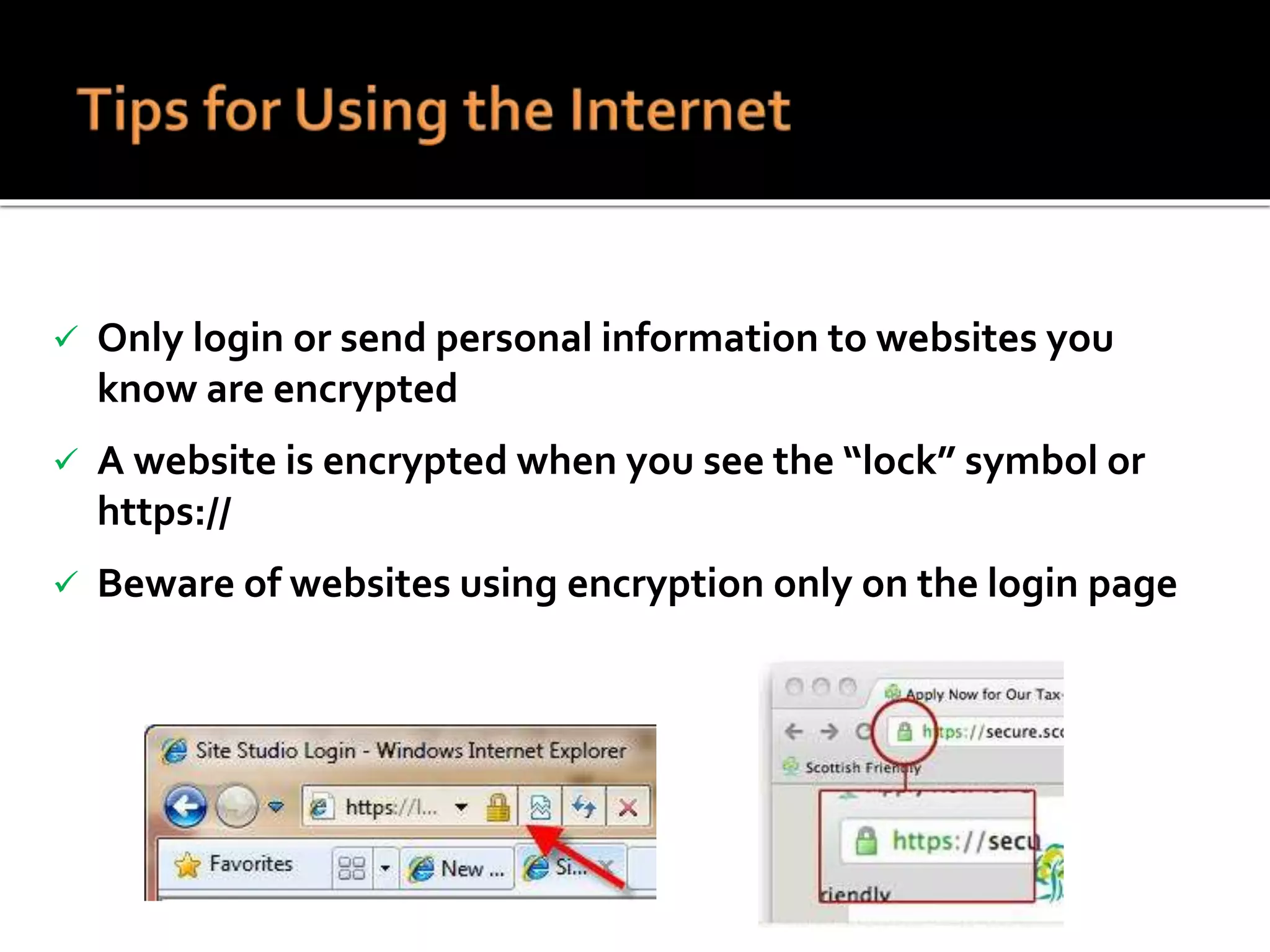
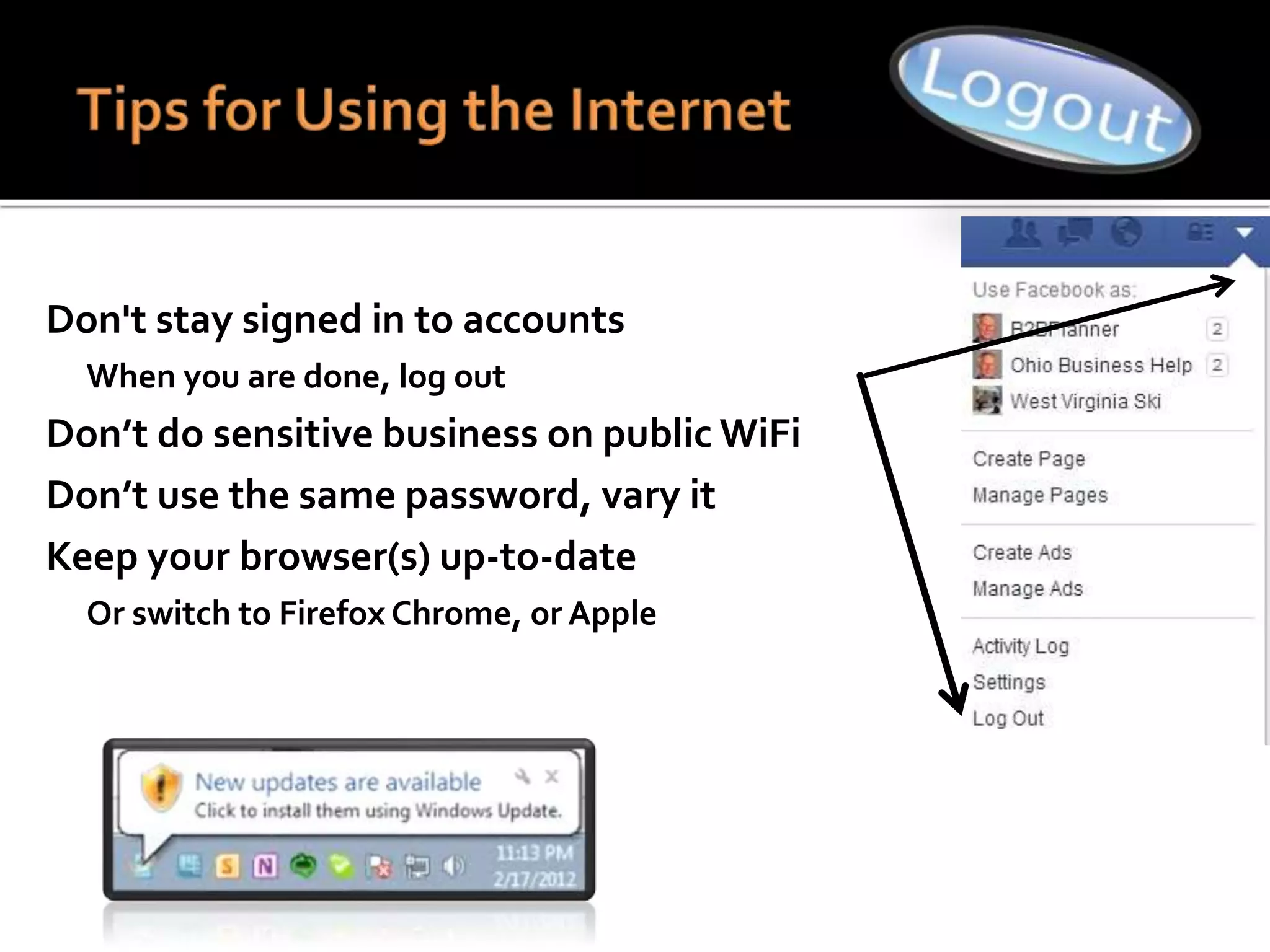
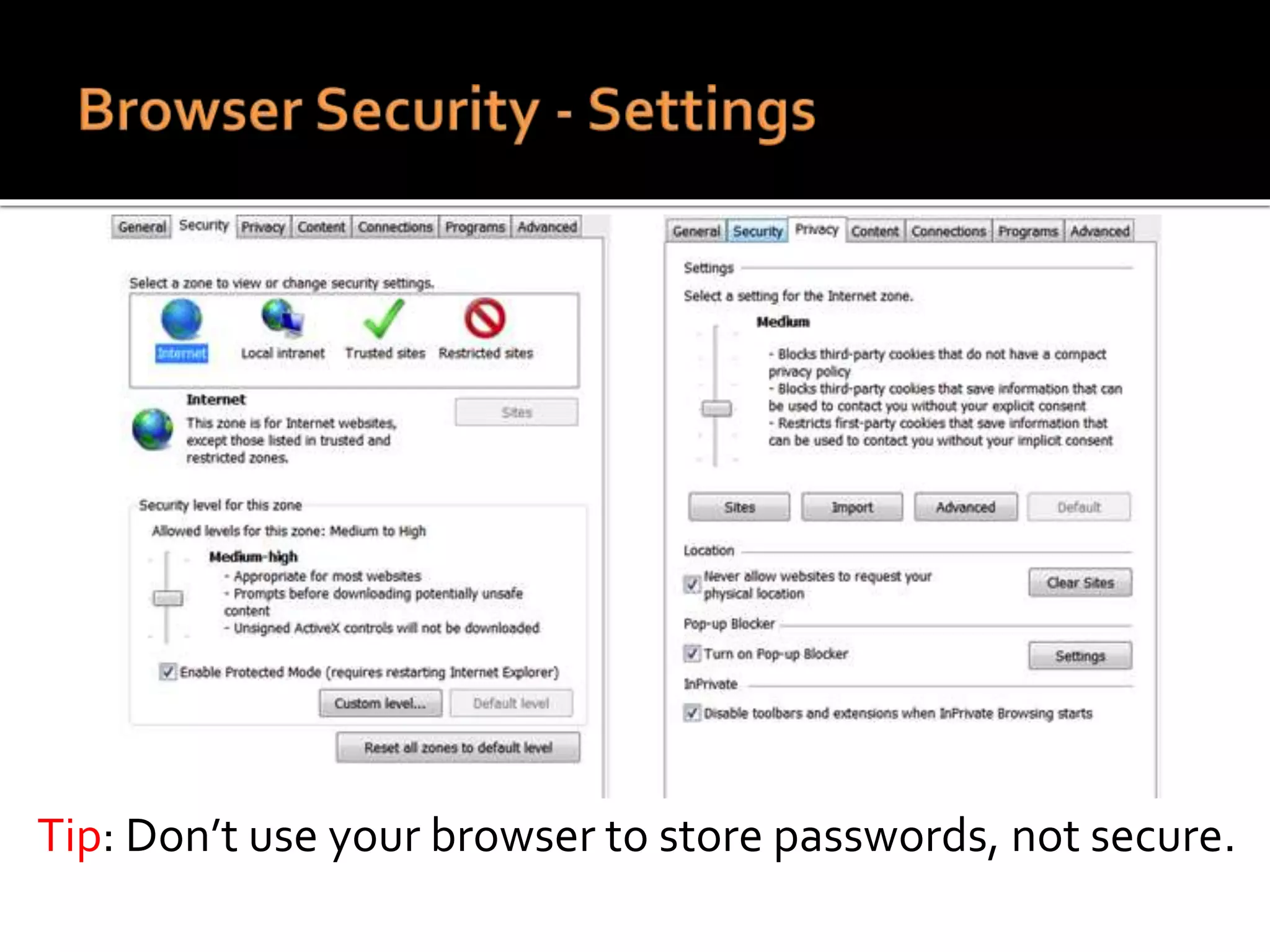
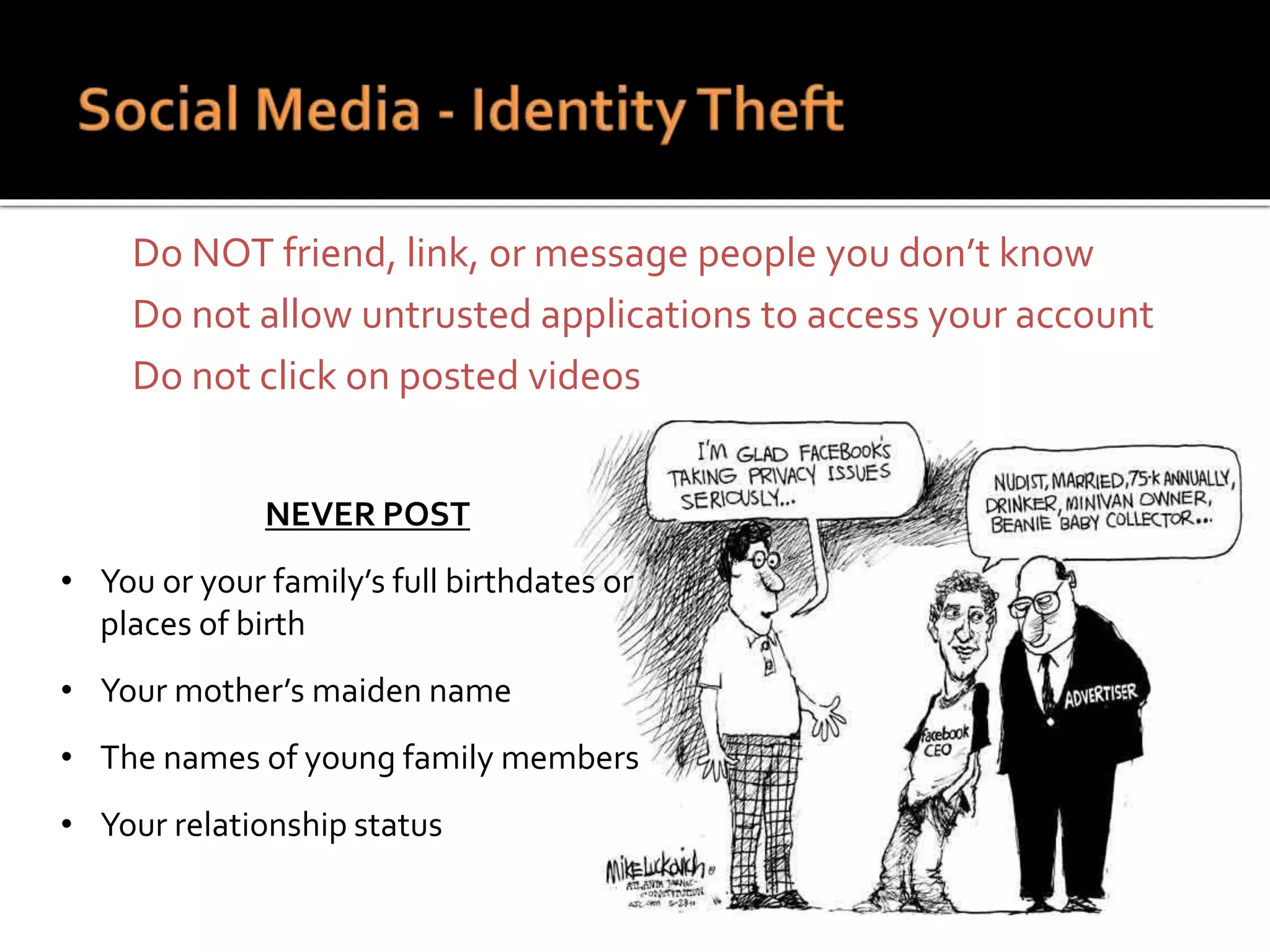
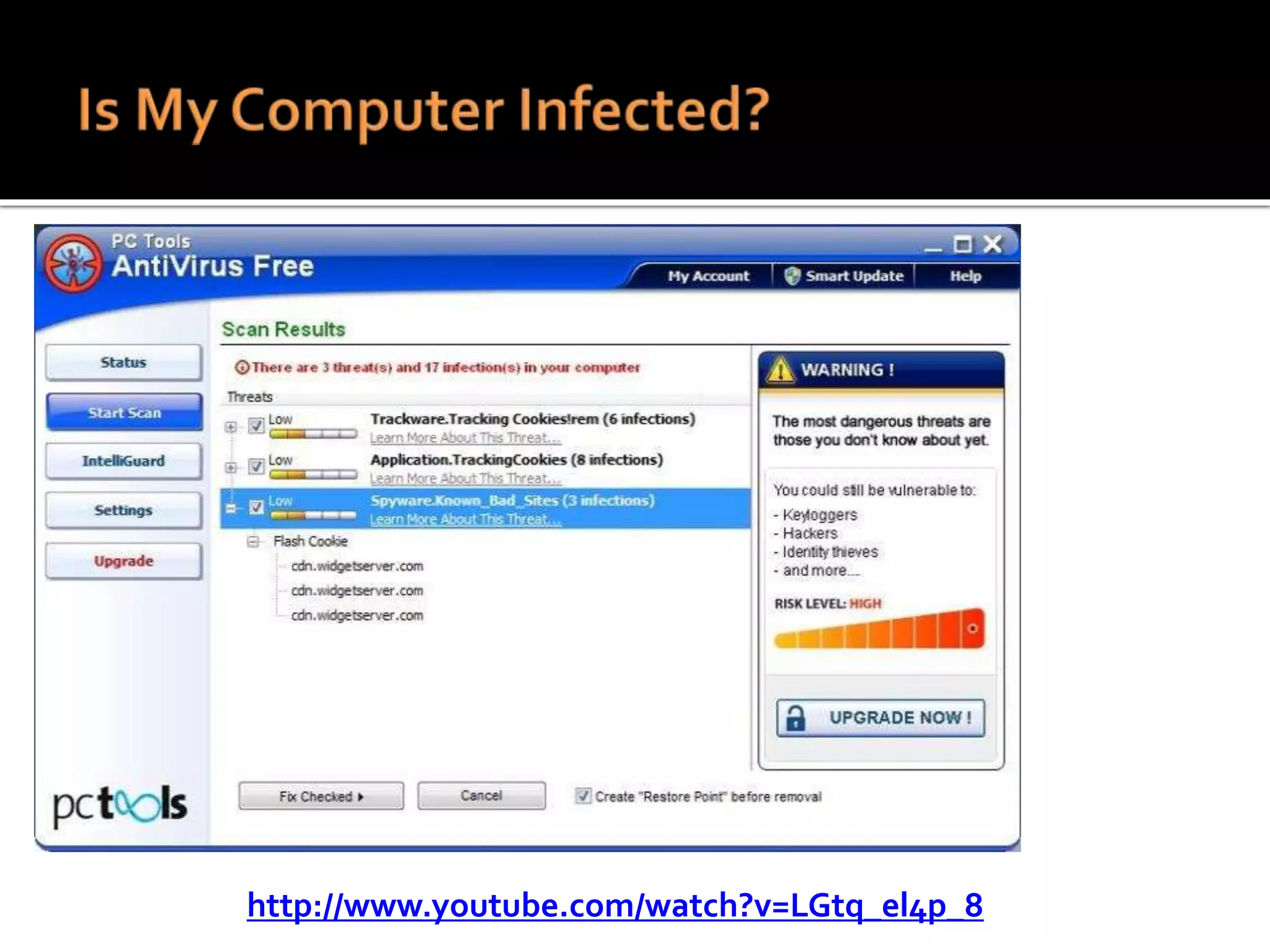
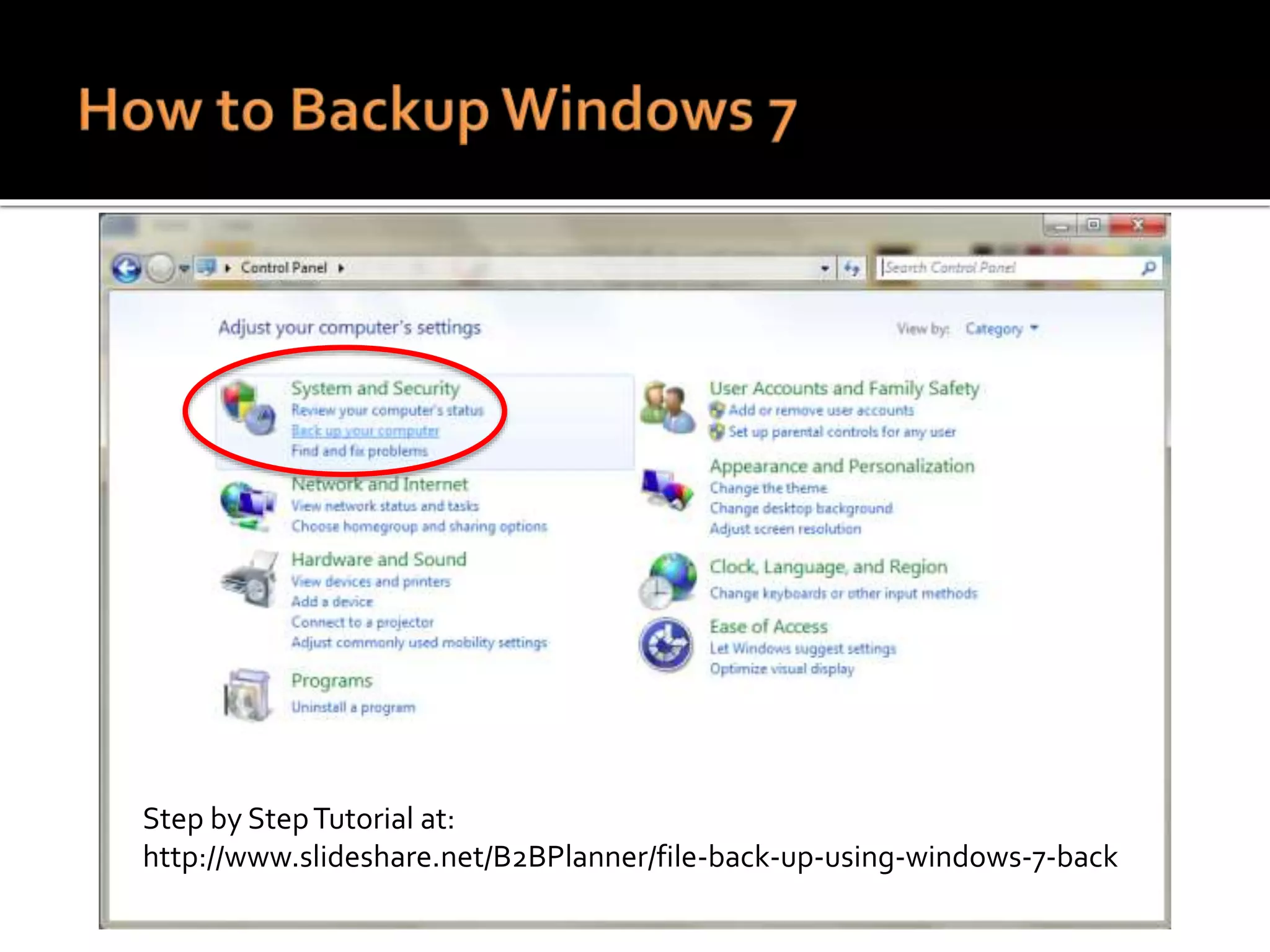
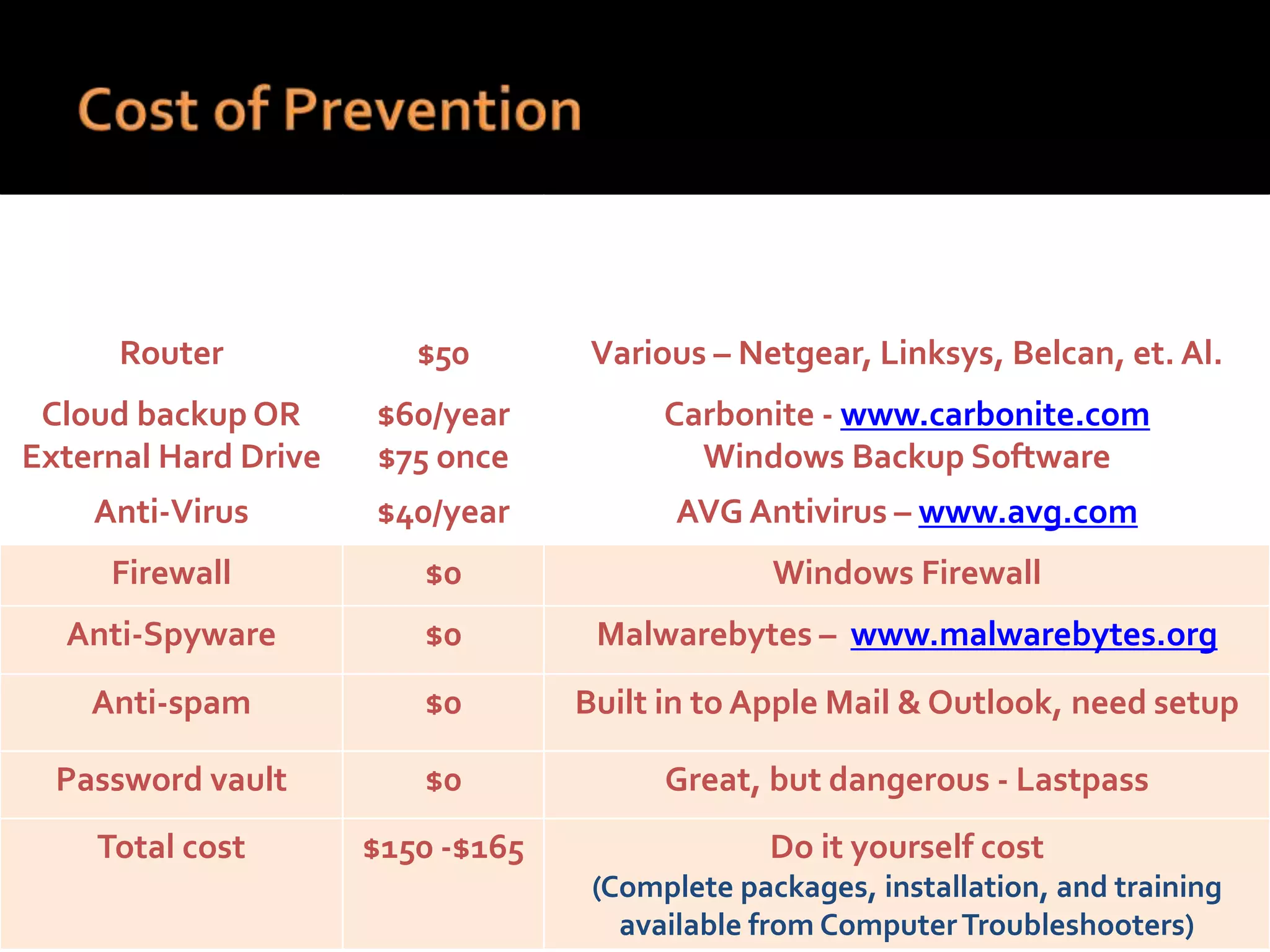
This document summarizes a cyber security workshop covering various topics to help small businesses protect themselves from cyber threats. The workshop will take place on June 26 from 8-10 AM at the Madison Lakes Training & Conference Center in Dayton, OH. It will provide mentoring and training to business owners on topics like starting up a business, growing an existing business, and improving performance. Mentoring is free and seminars have a small or no charge. The document then introduces the speakers and their backgrounds and qualifications to discuss cyber security topics. [END SUMMARY]