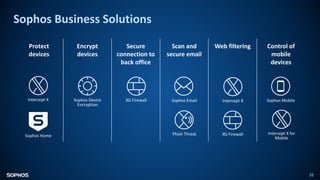
This document provides best practices for securing remote work during the coronavirus pandemic. It outlines 11 practices including making it easy for users to get started remotely, ensuring devices and systems are fully protected, encrypting devices where possible, and creating a secure connection back to the office. It also recommends securing email, enabling web filtering, using cloud storage safely, managing removable devices, controlling mobile devices, allowing security issue reporting, and being aware of "shadow IT" solutions. The document concludes by offering free cybersecurity resources from Sophos.