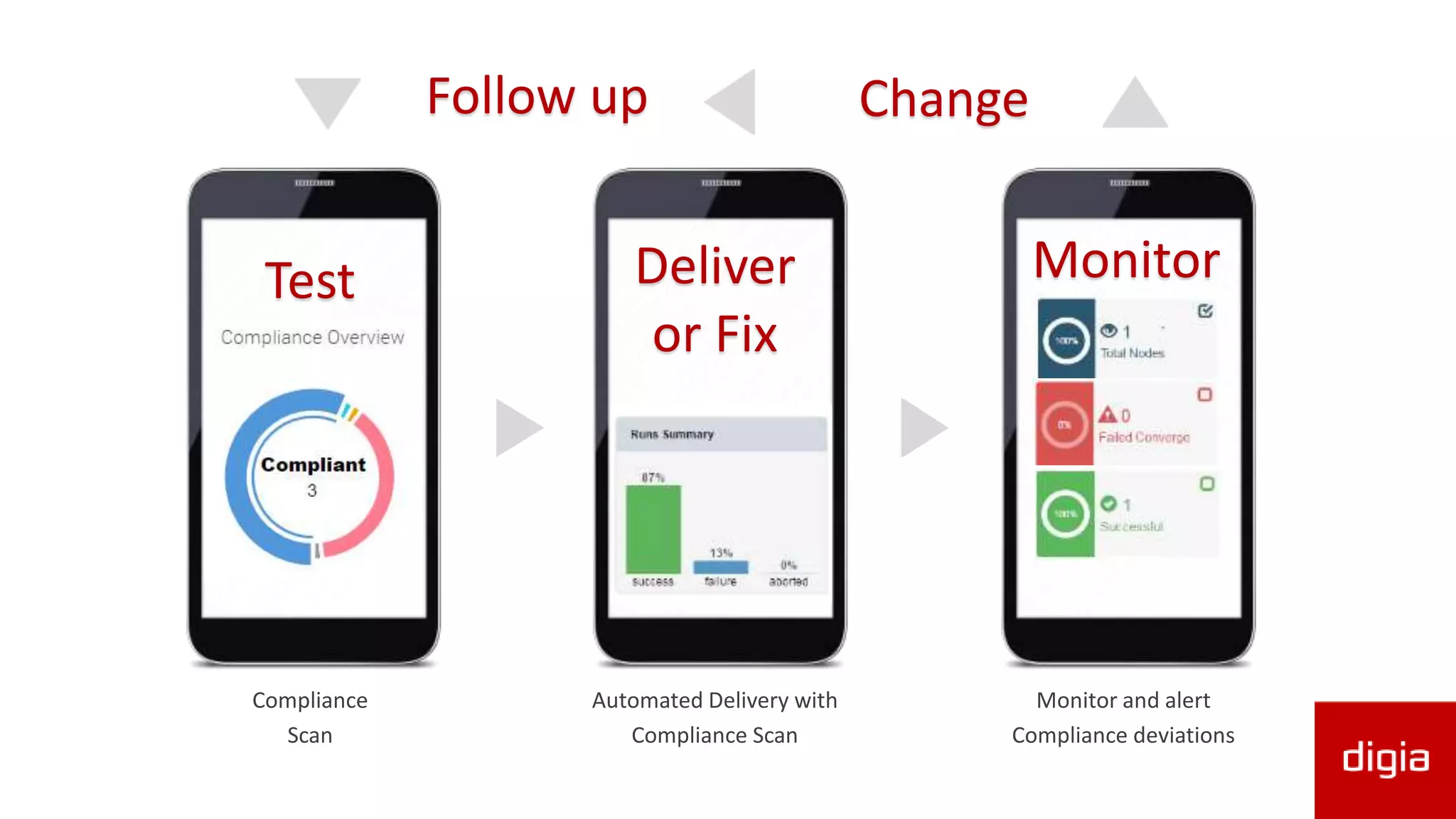
The document outlines the agenda for a DevOps and cybersecurity meetup held on September 14, 2016, featuring discussions on continuous compliance, GDPR, and data privacy. It emphasizes the importance of compliance in data management, identifying business risks, and the responsibilities of registry owners under new EU regulations. The document also highlights the need for automation in compliance processes and the significance of understanding data management practices to avoid pitfalls.