Computer MCQ E-Book PDF Free Download for all Competitive Exams. Most important Objective type multiple choice Questions and answers in English. All MCQs collected from previous years question papers. Helpful MCQs for ISRO, DRDO CEPTAM, CURDE, GTRE SSC CGL, CHSL, HSSC CET, GATE, NAVY, ARMY, CRPF, MP PEB, Constable, Delhi Police, HTET, DSSSB, UPSSSC, COPA CEPTAM, RRB, Railway, CCC, JKSSB, Teacher, UPSC, SBI, Bank PO Clerk, CBSE, Computer Science, BCA, banking, Placement, CG Vyapam, MCQ Entrance, IBPS, IT, GD, RPF, NPTC, Haryana Group D, Defence, ITBP, RBI, LIC AAO, IDBI, PNB, NABARD, Apprentice, Online, Court, CPO, MTS, BSF, CISF, Home Guards, IB ACIO, Sub Inspector, Shikshak, KVS, PGT, NVS, NDA, Indian Coast Guard, BSF, Agniveer, CAPF, Airforce, FCI, UGC NET, NABARD, BOB, SEBI, Post Office, Havaldar, Metro, DMRC, IRDAI, ESIC, IOF, UPPCL, O Level, MTS, Data entry operator, PWD, PHED, Air India, BHEL, GAIL, NTPC, PGCIL, HSC, JOA IT, VAO, Beltron, OSAP IRB, CBI, OSSC, Viva Test Quiz and all other computer competitive exams. Beginners, Intermediate & Advanced Level.




![27 - Why to use fflush() library function?
A - To flush all streams and specified streams
B - To flush only specified stream
C - To flush input/output buffer
D - Invalid library function
Answer : A
Explanation: In C programming, the fflush() function writes any unwritten data in stream's buffer.
If, stream is a null pointer, fflush() function will flush all streams with unwritten data in the buffer.
int fflush(FILE *stream);
28 - According to ANSI specification, how to declare main () function with command-line
arguments?
A - int main(int argc, char *argv[])
B - int char main(int argc, *argv)
C -
int main()
{
Int char (*argv argc);
)
D - None of the above
Answer : A
Explanation: Some time, it becomes necessary to deliver command line values to the C
programming to execute the particular code when the code of the program is controlled from
outside. Those command line values are called command line arguments. The command line
arguments are handled by the main() function.
Declaration of main () with command-line argument is,
int main(int argc, char *argv[ ])
Where, argc refers to the number of arguments passed, and argv[ ] is a pointer array which points
to each argument passed to the program.
29) Study the following program:
main()
{printf("HEETSON");
main();}
What will be the output of this program?
a) Wrong statement
b) It will keep on printing HEETSON
c) It will print nothing
d) None of these
Ans. b
Explanation: In this program, the main function will call itself again and again. Therefore, it will
continue to print HEETSON.
30) . Which technology is used in Compact Disks?
a) Electro Magnetic
b) Laser
c) Mechanical
d) Electrical
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-5-2048.jpg)

![37. CD is a ______ storage device?
a) Primary
b) Secondary
c) Teritory
d) None of these
Ans. b
38. The 10’s complement of ‘(52520)_(10)’ is.
a) 48240 b) 47480 c) 47840 d) 48470
Ans. b
39. If a multiplexer has 16 input lines, how many selection lines would be necessaiy?
a) 16 b) 8 c) 4 d) 2
Ans. c
40. _____ is used to restore the contents of the cells in synchronous DRAM.
a) Sense amplifier b) Refresh counter c) Restorer d) Restore counter
Ans. a
41. If a block can be placed in a limited set of places in the cache, the cache is said to be
a) Fully associative b) Set associative c) Direct mapped d) Restricted mapped
Ans. b
42. The three main parts of the processor are _______ [SBI Clerk, 2012]
(a) ALU, Control Unit and Registers
(b) ALU, Control Unit and RAM
(c) Cache, Control Unit and Registers
(d) Control Unit, Registers and RAM
(e) RAM, ROM and CD-ROM
Ans. A
43. Which printer cannot print more than one character at a time ? [SSC, CHSL, 2012]
(a) Line (b) Daisy-wheel
(c) Laser (d) Dot-matrix
Ans. B
44. ________key is the example of Toggle key [IBPS Clerk, 2012]
(a) Alt
(b) Shift
(c) Control
(d) Escape
(e) Caps Lock
Ans. E
45. Video controller [IBPS Clerk, 2012]
(a) Controls the resolution of images on screen
(b) Controls the signals to be sent and received from processor for display
(c) Handles the entire electronic work behind the formation of images on the screen
(d) Is responsible for allocating pixels for formation of images
Ans. C](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-7-2048.jpg)
![46. Which of these is a point-and-draw device ? [IBPS PO, 2012]
(a) mouse
(b) scanner
(c) printer
(d) CD-ROM
(e) Keyboard
Ans. A
47. When a key is pressed on the keyboard, which standard is used for converting the keystroke into the
corresponding bits? [IBPS PO,2013]
(a) ANSI
(b) ASCII
(c) EBCDIC
(d) ISO
(e) None of the above
Ans. A
48. _______ devices convert human-understandable data and programs into a form that the computer can
process. [SBI PO, 2013]
(a) Printing
(b) Output
(c) Solid State
(d) Monitor
(e) Input
Ans. E
49. The CPU comprises of Control, Memory, and ________ units. [SBI PO,2013]
(a) Microprocessor (b) Arithmetic/Logic (c) Output (d) ROM (e) Input
Ans. B
50. A joystick is primarily used to/for ___________. [SBI PO, 2013]
(a) Control sound on the screen (b) Computer gaming (c) Enter text (d) Draw pictures (e) Print text
Ans. B
51. On the motherboard the connection points for chips are reffered to as
a) slots
b) sockets
c) ports
d) lines
Ans. B
52. The load instruction is mostly used to designate a transfer from memory to a processor register known as [IBPS
PO 2012]
a) accumulator
b) instruction register
c) program counter
d) memory address register
Ans. A
53. ‘C’ in CPU denotes
a) Common b) Central c) Convenient d) Computer
Ans. B](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-8-2048.jpg)
![54. Arithmetic logic unit and control sections have special purpose locations called [SBI Clerk 2012]
a) registers
b) RAM
c) BIOS
d) I/O
Ans. A
55. Internal memory in a CPU is nothing but
a) a set of registers b) a set of ALU c) microprocessor d) bus
Ans. A
56.The word ‘computer’ usually refers to the central processing unit plus
a) external memory b) internal memory c) input devices d) output devices
Ans. A
57. Which of the following is a part of central processing unit?
a) Printer b) Keyboard c) Mouse d) Arithmetic and logic unit
Ans. D
58. Control unit of a digital computer is often called the
a) clock b) nerve centre c) Both A and B d) IC
Ans. B
59. The central processing unit (CPU) in a computer consists of
a) input, output and processing b) control unit, primary storage and secondary storage
c) control unit, arithmetic logic unit, registers d) None of the above
Ans. C
60. A group of bits that tells the computer to perform a specific operation is known as
a) instruction code b) micro operation c) accumulator d) register
Ans. A
61. Which Microsoft-based technology was built to link desktop applications to the World Wide Web?
[A] Active Channel
[B] Active Desktop
[C] ActiveX
[D] None of the above
Correct Answer: C [ActiveX]
Explanation: ActiveX is a software framework created by Microsoft that adapts its earlier Component
Object Model (COM) and Object Linking and Embedding (OLE) technologies for content downloaded from a
network, particularly from the World Wide Web. It is used till IE11 but not Microsoft Edge.
62. Which among the following is the most common source of Viruses to the hard disk of your computer?
[A] Incoming Email [B] Outgoing Email [C] CD ROMs [D] Websites
Ans. a
63. Symantec is the maker of which among the following popular antivirus software?
[A] Norton
[B] BitDefender
[C] Avast
[D] McAfee VirusScan
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-9-2048.jpg)
![64. Which of the following lies within the CPU?
[A] Primary Memory
[B] Secondary Memory
Secondary Memory
[C] Mouse
[D] Keyboard
Ans. a
Explanation: All input data and instructions are stored in the memory which is of two types-primary
memory and the secondary memory. Primary memory resides within the CPU while the secondary
memory is external to it.
65. “Internet escrow ” is a term most commonly related to which of the following?
[A] E-commerce [B] Software Development
[C] Privacy Security [D] Database Management
Ans. a
Explanation: Escrow is a financial instrument whereby an asset is held by a third party on behalf of two
other parties that are in the process of completing a transaction. E commerce hold the asset of a merchant
before it is sold to a customer. So it is Internet escrow.
66. In the Windows XP, what does XP stands for?
[A] Extra-Powerful [B] Experience
[C] Extended Platform [D] Experience Platform
Ans. b
Explanation: Windows XP is an operating system introduced in 2001. It is from Microsoft’s Windows. The
“XP” in Windows XP stands for eXPerience. Microsoft called the XP release its one of the most important
product.
67. V-RAM is used for access of the following?
[A] Video & Graphics
[B] Text & Images
[C] programs
[D] None of the above
Ans. a
Explanation: V-Ram is also known as video Ram. It is a dual ported variant of dynamic RAM. VRAM is
basically RAM integrated in a card for using it for storing graphical textures, 3D models temporary. It is
used for video access and graphics.
68. The word bandwidth is also used to mean ________?
[A] width of the data cable
[B] amount of data transferred
[C] number of the computers on a particular network
[D] none of the above
Ans. b
Explanation: Bandwidth refers to the amount of data that can be transmitted in a fixed amount of time.
For digital devices, the bandwidth is usually expressed in bits per second(bps) or bytes per second.
69. Which among the following is correct about 4GL?
[A] A computer brand [B] A software brand
[C] A software program [D] A programming language
Ans. d](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-10-2048.jpg)
![70. As a person working in internet banking environment, why you should be aware of the “Dictionary
attack”?
[A] It is used to inject worms or viruses in the system
[B] It is used to determine a password
*C+ It is used to access customer’s account by determining other details
[D] It is used for stealing info from the Credit Card
Ans. b
Explanation: A dictionary attack is a method of breaking into a password-protected computer or server. It
is done by systematically entering every word in a dictionary as a password. A dictionary attack is used as
an attempt to decrypt a message or document.
71. C is what kind of language?
a) An assembly language
b) A third generation high level language
c) A machine language
d) Future language
Ans. b
72. Identify the device through which data and instructions are entered into a computer?
a) Software
b) Output device
c) Input device
d) Heetson
Ans. c
73. Computer Monitor is also known as :
a) DVU
b) UVD
c) VDU
d) CCTV
Ans. c
74. Arrange in ascending order the units of memory TB, KB , GB, MB
a) TB > MB > GB > KB
b) MB > GB > TB > KB
c) TB > GB > MB > KB
d) GB > MB > KB > TB
Ans. c
75. Which one of these stores more data than a DVD?
a) CD Rom b) Floppy c) Blue Ray Disk d) Red Ray Disk
Ans. c
76. The output shown on the computer monitor is called
a) VDU b) Hard Copy c) Soft Copy d) Screen Copy
Ans. c
77. 8 Bits make up 1 _____
a) Byte
b) Megabyte
c) Kilobyte
d) None
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-11-2048.jpg)




![121. The ____ performs simple mathematics for the CPU.
(a) ALU (b) DIMM (c) BUS (d) Register (e) None of these
Ans. a
122. The ALU performs ____ operation.
(a) ASCII (b) Logarithm (c) Algorithm (d) Arithmetic (e) None of these
Ans. d
123. ALU stands for
(a) Algorithm and logarithm unit
(b) Arithmetic and logarithm unit
(c) Arithmetic and logical unit
(d) Algorithm and logical unit
(e) None of these
Ans. c
124. Which of the following is responsible for all types of calculations?
(a) ALU (b) Control Unit (c) Registers (d) BUS (e) None of these
Ans. a
125. The first computer architecture was introduced in [Allahabad Bank Clerk 2010]
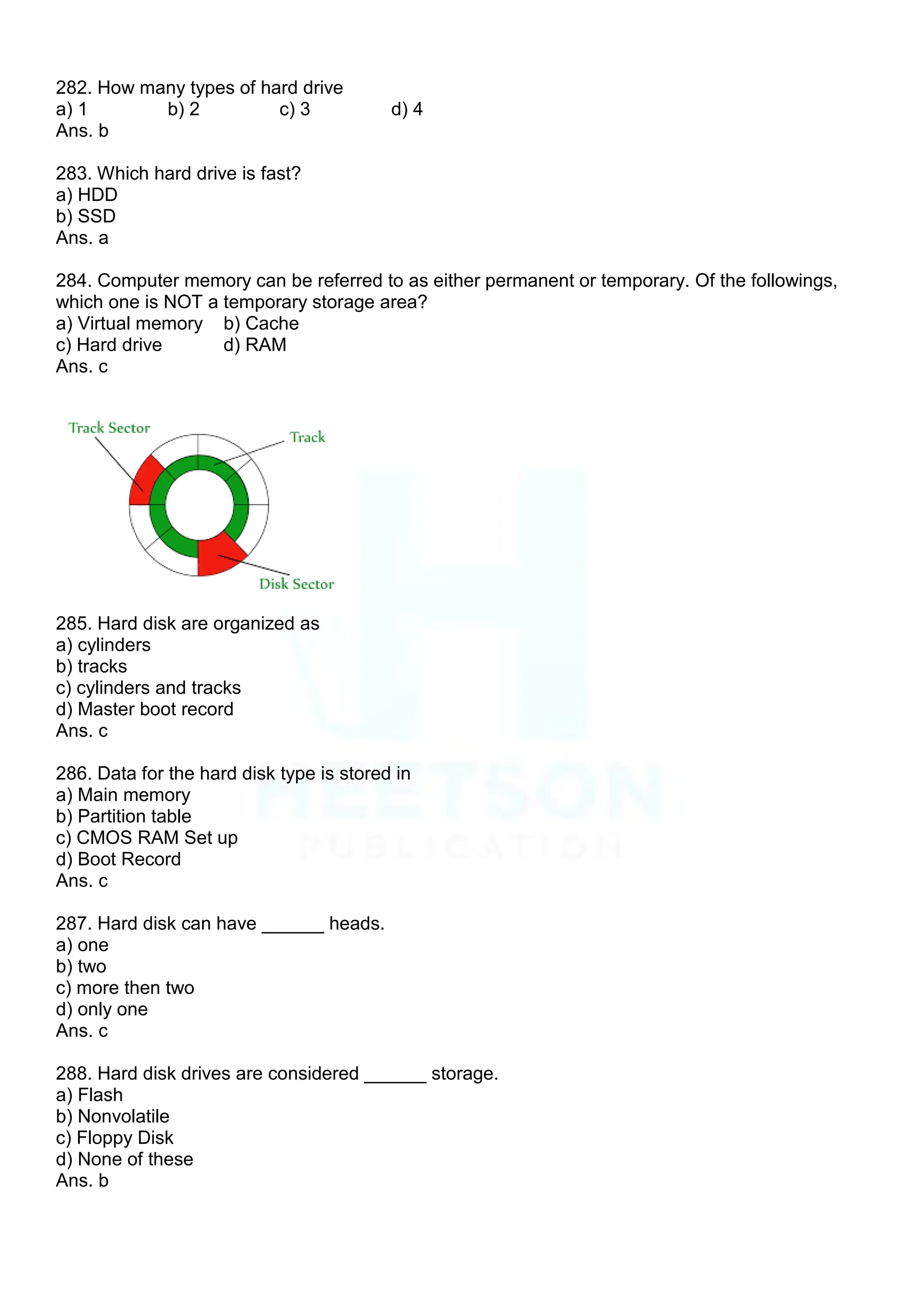
(a) 1970 (b) 1968 (c) 1971 (d) 1973 (e) 1972
Ans. a
126. Another word for the CPU is [Allahabad Bank Clerk 2010]
(a) microprocessor (b) execute (c) microchip (d) decode (e) None of these
Ans. a
127. The microprocessor of a computer [IBPS Clerk 2011]
(a) does not understand machine language
(b) understands machine language and high level language
(c) understands only machine language
(d) understands only high level languages
(e) understands only assembly language
Ans. c
128. The microprocessor is the brain of the computer and is also called a [Allahabad Bank PO 2011]
(a) microchip (b) macrochip (c) macroprocessor(d) calculator (e) None of these
Ans. a
129. A microprocessor with 12 address lines is capable of addressing [LIC Assistant Officer 2009]
(a) 1024 location (c) 4096 location (b) 2048 location (d) 64 location
Ans. c
130. The first microprocessor produced by Intel Corp and Texas instruments were used primarily to control
(a) calculators (b) cars (c) remotes (d) robotics (e) grinders
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-16-2048.jpg)
![131. It takes advantages of basic hardware and software security characteristics.
(1) System design (2) Data access control (3) System access control (4) None of these
Ans. 1
132. If you are allowing a person on the network based on the credentials to maintain the security of your network,
then this act refers to the process of [IBPS PO 2016]
(1) Authentication (2) Automation (3) Firewall (4) Encryption (5) None of these
Ans. 1
133. Cracked softwares are another source of
(1) E-mail attack (2) Virus attack (3) Trojan horse (4) All of these
Ans. 2
134. A malware is an
(1) program (2) hardware (3) a person (4) None of these
Ans. 1
135. It is a self-replicating program that infects computer and spreads by inserting copies of itself into other
executable code or documents.
(1) Keylogger (2) Worm (3) Virus (4) Cracker
Ans. 3
136. A computer virus is
(1) deliberately created (2) created accidently (3) produced as result of some program error (4) All of the above
Ans. 1
137. Which of the following refers to dangerous programs that can be ‘caught’ of opening E-mail attachments and
downloading software from the Internet? [SBI PO 2014]
(1) Utility (2) Virus (3) Honey Pot (4) Spam (5) App
Ans. 2
138. A program designed to destroy data on your computer which can travel to ‘infect’ other computers is called a
[RBI Grade B 2012]
(1) disease (2) torpedo (3) hurricane (4) virus (5) infector
Ans. 4
139. Computer virus is [IBPS Clerk 2011]
(1) a hardware (2) windows tool (3) a computer program (4) a system software (5) None of the above
Ans. 3
140. Which among the following is related to the internet and mail?
(1) Boot-UP (2) Magnetic Tapes (3) Applications Software (4) Paging (5) Virus
Ans. 5
141. Computer servers are used in applications.
(a) online reservation of tickets
(b) e-commerce
(c) tracking of consignments
(d) all of them
Ans. d
142. Your operating system will detect and install the appropriate device drivers for this type of
device:
a) Plug and play b) Plug and go c) Plug and continue d) Plug and commence
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-17-2048.jpg)




![191. To perform calculation on stored data computer, uses ……… number system. [SBI Clerk 2009]
(1) decimal (2) hexadecimal (3) octal (4) binary
Ans. 4
192. The number system based on ‘0’ and ‘1’ only, is known as
(1) binary system (2) barter system (3) number system (4) hexadecimal system
Ans. 1
193. Decimal number system is the group of ............ numbers.
(1) 0 or 1 (2) 0 to 9 (3) 0 to 7 (4) 0 to 9 and A to F
Ans. B
194. A hexadecimal number is represented by
(1) three digits (2) four binary digits (3) four digits (4) All of these
Ans. B
195. A hexadigit can be represented by [IBPS Clerk 2012]
(1) three binary (consecutive) bits (2) four binary (consecutive) bits
(3) eight binary (consecutive) bits (4) sixteen binary (consecutive) bits
Ans. 4
196. What type of information system would be recognised by digital circuits?
(1) Hexadecimal system (2) Binary system (3) Both ‘1’ and ‘2’ (4) Only roman system
Ans. 3
197. The binary equivalent of decimal number 98 is [IBPS Clerk 2012]
(1) 1110001 (2) 1110100 (3) 1100010 (4) 1111001 (5) None of these
Ans. 3
198. What is the value of the binary number 101?
(1) 3 (2) 5 (3) 6 (4) 101
Ans. 2
199. The binary number 10101 is equivalent to decimal number .............
(1) 19 (2) 12 (3) 27 (4) 21
Ans. 4
200. To convert binary number to decimal, multiply the all binary digits by power of
(1) 0 (2) 2 (3) 4 (4) 6
Ans. 2
201. Data Manipulation language is used to create_____.
Ans. Object
202. Every record of Relation is called ______.
Ans. Tuple
203. Architecture of the database can be viewed as ______.
Ans. Three levels](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-23-2048.jpg)

![217. Dos 6.0 Developed in _______.
Ans. 1993
218. DOS 1.25 Developed in ______.
Ans. 1982
219. DOS 7.0 Developed in _______.
Ans. 1995 (This version is Part of MS window 95)
220. DOS 7.1 Developed in ________.
Ans. 1997
221. DOS OS Provide which type of Interface?
Ans. CLI or CUI (Command Line Interface or Character User interface)
222. How many wild card character in DOS?
Ans. Dos Provide Two wildcard character * and ?
( * means single character replacement and ? means any number of character)
223. What are internal commands?
Ans. Those commands that are loaded automatically in the memory when DOS is loaded into
memory during booting Process
224. What is Blocks in computer?
Ans. Every peripheral talks to the computer either one character at a time or in group of characters
called Blocks.
225.What is the name of hierarchical file system in DOS?
A Tree structure B Root structure
C Hybrid structure D Directory structure
Ans. b
226. DVD was invented and developed in year_____
a) 1985 b) 1995 c) 1975 d) 1998
Ans. b
227. Which of the following does not relate to Input Unit ? [SBI Clerk, 2012]
(a) If accepts data from the outside world.
(b) It converts data into binary code that is understandable by the computer
(c) It converts binary data into the human readable form that is understandable to the users.
(d) It sends data in binary form to the computer for further processing
(e) None of these
Ans. C
228. Which technology used in DVD to store information?
a) Optical data storage b) Radio technology
c) light wave technology d) microwave technology
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-25-2048.jpg)








![321. Time sharing became possible in _____ generation of computers. [SBI PO 2011]
a) First b) Second c) third d) fourth
Ans. B
322. Computer is a/an
a) battery b) electronic machine c) All of these d) None of these
Ans. B
333. Name the first general purpose electronic computer. [IBPS PO 2012]
a) ADVAC b) ADSAC c) UNIVAC d) EDVAC
Ans. C
324. Which is not the example of special purpose computer?
a) Automatic aircraft landing b) word processor c) multimedia computer d) All of the above
Ans. B
325._____ is not an E-Commerce application.
a) House banking b) Buying stocks c) Conductiong an auction d) Evaluating an employee
Ans. D
326. Computer’s basic architecture was developed by
a) John Von Neumann b) Charles Babbage c) Blaise Pascal d) Jordan Mure
Ans. A
327. In production of IC chip of computer, what is needed in the following?
a) Chromium b) Silocon c) Platinum d) Gold
Ans. B
328. First supercomputer developed in india is
a) PARAM b) Aryabhatt c) Buddha d) RAM
Ans. A
329. Computers that are portable and convenient to use for users who travel, are known as
a) supercomputers b) minicomputers c) mainframe computers d) laptops
Ans. D
330. Speed of first generation computer was in [IBPS Clerk 2012]
a) nano-second b) miliseconds
c) nano-mili seconds d) micro seconds
Ans. B
Explanation: The Processing speed of computers in first generation was measured in Milliseconds. And, We
might know that Millisecond is very slow than today's processing speed measurements. Because of not
having transistors in computers, The speed of computers was not measured in Hz.
331. Which of the following is NOT one of the four major data processing functions of a computer?
a) gathering data
b) processing data into information
c) analyzing the data or information
d) storing the data or information
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-36-2048.jpg)


![352. What is the size of float and double in Java?
a) 32 and 64 b) 32 and 32 c) 64 and 64 d) 64 and 32
Ans. a
353. Automatic type conversion is possible in which of the possible cases?
a) Byte to int b) Int to long c) Long to int d) Short to int
Ans. b
354. Find the output of the following code.
int Integer = 24;
char String = ‘I’;
System.out.print(Integer);
System.out.print(String);
a) Compile error b) Throws exception c) I d) 24 I
Ans. d
355. Select the valid statement.
a) char[] ch = new char(5) b) char[] ch = new char[5]
c) char[] ch = new char()d) char[] ch = new char[]
Ans. b
356. When an array is passed to a method, what does the method receive?
a) The reference of the array b) A copy of the array
c) Length of the array d) Copy of the first element
Ans. a
357. Select the valid statement to declare and initialize an array.
a) int[] A = {} b) int[] A = {1, 2, 3} c) int[] A = (1, 2, 3) d) int[][] A = {1, 2, 3}
Ans. b
358. Arrays in java are-
a) Object references b) objects c) Primitive data type d) None
Ans. b
359. When is the object created with new keyword?
a) At run time b) At compile time c) Depends on the code d) None
Ans. a
360. Identify the correct definition of a package.
a) A package is a collection of editing tools b) A package is a collection of classes
c) A package is a collection of classes and interfaces d) A package is a collection of interfaces
Ans. c
361. NaN stands for_________.
a) Nano b) NanTech c) Not a number d) New attacted Nematic
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-39-2048.jpg)



![395. Which character is used to represent parent directory in Linux?
A). B)..
C)~ D)*
Ans. b
396.Which character is used to redirect output in to an existing file in Linux?
A >
B >>
C <
D <<
Ans. b
397.Which one of the following is the directory separator in Linux?
A /
B
C //
D
Ans. a
398.Which character is used to represent a range of values in Linux?
A ( )
B [ ]
C { }
D <>
Ans. b
399.Which character redirects the output of one command to another in Linux?
A . dot
B | pipe
C : colon
D ; semicolon
Ans. b
400.Which Linux command list the content of all sub directory?
A ls ~ B ls * /
C ls / D ls ../
Ans. b
401. Cache memory is used as a ___________memory.
a) primary b) secondary c) territory d) Scratch
Ans. d
402. MSB stands for_____.
a) mobile source bit b) most significant bit c) module significant bit d) more social bit
Ans. b
403. LSB stands for______.
a) local Heetson bit b) local significant bit
c) least significant bit d) large significant
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-43-2048.jpg)
![404. _____ can be treated as the waiting room for the computers processor.
Ans. RAM
405. _______ store data or information temporarily and pass it on as directed by the control unit.
Ans. Register
406. Common type of storage devices are_____
Ans. Optical
407. _____ files contains permanent data and gets updated during the processing of Transactions.
Ans. Master
408. ______ helps to protect Floppy disks from data getting accidentally erased.
Ans. Write Protect notch
409. _____ memory is having more memory addresses than are physically available.
Ans. Virtual
410. A ______ is a location for storing files on your computer.
Ans. Directory
411. A collection of related information sorted and dealt with as a unit is a [SBI Clerk, 2009]
(a) disk (b) data (c) file (d) floppy (e) None of these
Ans. B
412. Reusable optical storage will typically have the acronym——— [SBI Clerk, 2009]
(a) CD (b) DVD (c) ROM (d) RW (e) None of these
Ans. C
413. The most common type of storage devices are— —— [SBI Clerk, 2009]
(a) persistent (b) optical (c) magnetic (d) flash (e) None of these
Ans. B
414. During the –– portion of the Information Processing Cycle, the computer acquires data from some
source. [SBI Clerk, 2009]
(a) storage and output (b) storage (c) input (d) output (e) None of these
Ans. C
415. The contents of ____ are lost when the computer turns off. [IBPS PO, 2011]
(a) storage (b) input (c) output (d) memory (e) None of these
Ans. D
416. A DVD is an example of a(n) [IBPS PO, 2011]
(a) hard disk
(b) optical disc
(c) output device
(d) solid-state storage device
(e) None of these
Ans. B](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-44-2048.jpg)
![417. Which of the following are advantages of CDROM as a storage media? [IBPS PO, 2011]
(a) CD-ROM is an inexpensive way to store large amount of data and information.
(b) CD-ROM disks retrieve data and information more quickly than magnetic disks do.
(c) CD-ROMs make less errors than magnetic media.
(d) All the above
(e) None of these
Ans. A
418. Which of the following is billionth of a second? [SBI PO, 2011]
(a) Gigabyte (b) Terabyte (c) Nanosecond (d) Microsecond (e) Terasecond
Ans. C
419. The time for the actual data transfer after receiving the request for data from secondary storage is
referred to as the disk’s *IBPS Clerk,2011]
(a) transfer time (b) movement time (c) access time (d) data input time (e) None of these
Ans. C
420. The following computer’s memory is characterised by low cost per bit stored [IBPS Clerk, 2011]
(a) Primary
(b) Secondary
(c) Hard Disk
(d) All of these
Ans. B
421. FPGA means
a) Field Programmable Gate Array
b) Forward Programmable Gate Array
c) Forward Parallel Gate Array
d) Field Parallel Gate Array
Ans. a
422. Which language could be used for programming an FPGA.
a) Verilog
b) VHDL
c) Both A and B
d) Heetson
Ans. c
423. What is mean by ALU
a) Arithmetic logic upgrade b) Arithmetic logic unsigned
c) Arithmetic Local unsigned d) Arithmetic logic unit
Ans. d
424. In 8085 microprocessor, the RST6 instruction transfer programme execution to following
location
a) 0030H b) 0024H c) 0048H d) 0060H
Ans. a
425. HLT opcode means
a) load data to accumulator b) store result in memory
c) load accumulator with contents of register d) end of program
Ans. d](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-45-2048.jpg)

















![598. Which modulation mechanism is used in Bluetooth technology to transform bits to a signal?
a) ASK
b) PSK
c) OPSK
d) GFS
Ans. d
599. SEAL (Simple and Efficient Adaptation Layer) is associated with which AAL sub layer of ATM technology?
a) AAL1
b) AAL2
c) AAL3/4
d) AAL5
Ans. d
600. What is the Weight of standard size DVD?
a) 16 grams (0.56 oz)
b) 25 grams (2 oz)
c) 30 grams (3 oz)
d) 32 grams (0.95 oz)
Ans. a
601. Which of the following contains specific rules and words that express the logical steps of an
algorithm? [IBPS Clerk 2014]
(1) Programming language (2) Syntax (3) Programming structure (4) Logical chart (5) Flow chart
Ans. 3
602. A factor in the selection of source language is
(1) programmer skill (2) language availability (3) program compatibility with other software (4) All of the
above
Ans. 3
603. Machine language [SBI PO 2013]
(1) is the language in which programs were first written
(2) istheonlylanguageunderstoodbythecomputer
(3) differs from one type of computer to another
(4) All of the above (5) None of the above
Ans. 4
604. Each model of a computer has a unique
(1) assembly of a computer (2) machine language (3) high level language (4) All of the above
Ans. 2
605. The language which can be relocated easily is
(1) Machine language (2) Assembly language (3) Low level language (4) Middle level language
Ans. 2
606. Which language is CPU dependent ?
(1) C (2) Assembly (3) Java (4) All except Java
Ans. 2](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-63-2048.jpg)















![755. Which key combination is used to minimize all open windows and displays in the screen?
Ans. Windows key + D
756. How many users can access a share folder simultaneously from a Windows XP machine?
a) 8 b) 9 c) 10 d) Unlimited
Ans. c
757. Which of the following windows do not have start button
a) Windows Vista b) Windows 7 c) Windows 8 d) Windows 95
Ans. c
758. Which of the following Operating systems is better for implementing a Client Server network
a) MS DOS b) Windows 95 c) Windows 98 d) Windows 2000
Ans. d
759. Which one is the latest release of Windows Client Operating system?
a) Windows XP b) Windows 7
c) Windows 8 d) Windows 10
Ans. d
760. Which function key needs to be press during reboot to enter in Safe Mode of a Windows
machine?
Ans. F8
761. Microsoft 10 was launched in the year _____. [DRDO GTRE 2017]
a) 2013 b) 2014 c) 2016 d) 2015
Ans. d
762. Which of the following is true for testing and debugging? [DRDO CVRDE 2017]
a) Testing checks for logical errors in the programs, while debugging is a process of correcting those errors in the
program.
b) Testing and debugging indicate the same thing.
c) Testing detects the syntax errors in the program while debugging corrects those errors in the program.
d) All of the above
Ans. a
763. Computer systems that store instructions and data without any differences and data from the same memory
unit are based on _____ structure. [DRDO CVRDE 2017]
a) Harvard b) Babbage
c) Knuth d) Von-Neumann
Ans. d
764. In the screen is maximized, then the maximize button will be temporarily replaced by the _____ button. [DRDO
GTRE 2017]
a) Close
b) Open
c) Re-store
d) Minimize
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-79-2048.jpg)
![765. Which of the following is not a ‘over write’ virus ? [RRB Ranchi Asst. Loco Pilot]
a) Trj. Reboot
b) Meve
c) Way
d) Trivial.88.D
Ans. b
766. Which of the following are machine level languages? [ISRO Satelite Centre Bengaluru]
a) C++ b) Java c) Python d) None of these
Ans. d
767. Program Counter (PC) register stores the-
a) Address of the first memory block
b) Address of the last memory block
c) Address of the next instruction to be executed
d) Size of the primary memory
Ans. c
768. Which of the following function(s) is/are provided by operating system? [RRB Ranchi Asst. Loco Pilot]
a) Process management b) Security Management
c) File management d) All of these
Ans. d
769. ____ was the first computer language developed for electronic computer in 1949? [RRB Ajmer Asst. Loco Pilot]
a) Short code
b) FORTRAN
c) COBOL
d) Pascal
Ans. a
770. How many layers are there in TCP/IP Model? [Indian Ordnance Factory]
a) 2
b) 4
c) 5
d) 7
Ans. b
771. Program that duplicate the functionality of one system on another system is known as [RRB Chandigarh Asst.
Loco Pilot]
a) Emulators
b) Simulators
c) Evaluators
d) PCB
Ans. a
772. Which of the following is an application protocol? [RRB Ahamadabad Asst. Loco Pilot]
a) HTTP b) TCP c) IP d) UDP
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-80-2048.jpg)
![773. Which among them is not an example of mobile operating system? [RRB Chandigarh Asst. Loco Pilot]
a) Android b) Bada
c) Fedora d) Symbian
Ans. c
774. Which of the following is included in Paragraph Formatting in a word processor? [RRB Ahmadabad Asst. Loco
Pilot]
a) Subscript b) Font
c) Underline colour d) Line spacing
Ans. d
775. To declare the version of XML, the correct syntax is:
a) ? xml version =’1.0’/
b) ? xml version =”1.0”/
c) * xml version =’1.0’/
d) /xml version = ‘1.0’/
Ans. b
776. On which of the following storage media, storage of information is organized as a single continuous spiral
groove?
a) RAM
b) Floppy disk
c) Hard disk
d) CD-ROM
Ans. d
777. The addressing mode used in an instruction of the from ADD X,Y is:
a) Absolute
b) Indirect
c) Immediate
d) Index
Ans. d
778. What is garbage collection in the context of java?
a) The operating system periodically deletes all of the Java files available on the system.
b) When all references to an object are gone, and then the memory use by the object is automatically reclaimed.
c) Any java package imported in a program and not being used is automatically deleted.
d) The java virtual machine (JVM) checks the output of any java program and delete anything that does not make
sense at all
Ans. b
779. Which of the following represents the life-cycle of software development?
a) Analysis – design – coding – testing- operation and maintenance
b) Analysis – Design – Coding – Operation and maintenance – testing
c) Design – Analysis – Coding – testing – operation and maintenance
d) Design – analysis – coding – operation and maintenance – testing
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-81-2048.jpg)

![796. A register in the microprocessor that keeps track of the answer or result of any arithmetic or logic operation is
the _.
a) Stack pointer
b) Instruction pointer
c) Program counter
d) Accumulator
Ans. d
797. Which of the following is true to define a variable for ASP?
a) DIM b) Sets c) $ d) Var
Ans. a
798. ______ is an intermediate storage are used for data processing during the extract, transform and load process
of data warehousing.
a) Buffer b) Virtual memory c) Staging area d) inter-storage area
Ans. c
799. Which of the following Java statements declare and allocate a 2 dimensional array of integers with four rows
and five columns?
a) int array [4][5]; b) int array [][]==new int [4][5];
c) int array [5][4]; d) int array [][]=new int [5][4]
Ans. b
800. In ____ all the logic are implemented using registors and transistors.
Ans. Resistor and Transistor logic
801. _____ logic family implements the logic gates using MOSFET devices
Ans. MOS logic
802. For which logic gate, the output is “true” if either, but not both, of the inputs are “true”.
Ans. XOR
803. The ____ latch is hazard free.
Ans. Earle Latch
804. The flag size of an HDLC frame is ______.
Ans. 8 bits
805. Contents of one disk to another disk can be done using the command ____
Ans. DISK COPY
806. The assembler takes as its source code in _____ language program.
Ans. Assembly
807. In computer graphics, digital differential analyzer is used for ______ of lines, triangles and polygons.
Ans. Rasterization](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-84-2048.jpg)


![840. The _____ layer provides link between two directly connected nodes.
Ans. Data Link layer
841. Data items that cannot be divided are called as _____.
Ans. Elementary items
842. In MIMD, each processor is connected to its _____ immediate neighbors.
Ans. Four
843. A _____ is a general reusable solution to a commonly occurring problem in Software design.
Ans. Design Pattern
844. _____ is the allocation of a Computer’s processor power to specific tasks.
Ans. Scheduling
845. In, a physical contact is required to be established with the actuator of it, to make/break a connection.
a) proximity switch
b) limit switch
c) relay switch
d) all the above
Ans. b
846. -(i) CDMA uses spread spectrum technology
(ii) GSM Stands for Global System for Mobile
(iii) GSM uses TDMA
A:- (i) and (ii) are correct B:- (i) and (iii) are correct
C:- (ii) and (iii) are correct D:- (i),(ii) and (iii) are correct
Ans. d
847. Why is a trailer often added to the end of a frame in the data link layer?
a) Flow control b) Error Control
c) Addressing d) Access control
Ans. B
848. How many bytes are used in an Ethernet physical address?
a) 6
b) 4
c) 2
d) 8
Ans. a
849. DVD refers to [SSC MTS 2013]
a) Digital video developer
b) Digital video device
c) Digital video disc
d) None of the above
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-87-2048.jpg)
![850. The steps and tasks needed to process data, such as responses to questions or clicking an icon, are called
a) instructions
b) the operating system
c) application software
d) the system unit
Ans. a
851. A linker program
a) places the program in the memory for the purpose of execution
b) relocates the program to execute from the specific memory area allocated to it
c) links the program with other programs needed for its execution
d) interfaces the program with the entities generation its input data
Ans. c
852. Which of the following system software resides in main memory always? [IBPS Clerk 2011]
a) Text editor
b) Assembler
c) Linker
d) Loader
Ans. d
853. Coral Ventura, Illustrator are the examples of
a) Word processing b) Graphic c) Multimedia d) DTP
Ans. d
854. DirectX is a [RBI Grade B 2013]
a) computer part
b) a user interface
c) operating system
d) software that drives graphic software
Ans. d
855. Which type of software is used in organisations to keep track of products in stocks?
a) Enterprise Resource Planning (ERP) software
b) Payroll Software
c) Human resource planning software
d) Accounting software
e) Inventory management software
Ans. e
856. Text editor is a/an [RBI Grade B 2013]
a) application software
b) system software
c) utility software
d) all purpose software
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-88-2048.jpg)
![857. The primary purpose of the Windows operating system is
a) to make the most efficient use of the computer hardware
b) to allow people to use the computer
c) to keep systems programmer’s employed
d) to make computers easier to use
Ans. d
858. Every computer has a(n) ____ many also have _____ [RBI Grade B 2014]
a) Operating system, a client system b) operating system, instruction sets
c) application programs, an operating system d) operating system, application programs
Ans. d
859. When a file contains instructions that can be carried out by the computer, it is often called a(n) ____ file.
a) data
b) information
c) executable
d) application
Ans. c
860. Grouping and processing all of a firm’s transactions at one time, is called [IBPS Clerk 2011]
a) a database management
b) a real time system
c) batch processing
d) on-time system
Ans. c
861. ____ is a feature for scheduling and multi-programming to provide an economical interactive system of two or
more users. [IBPS Clerk 2012]
a) Time sharing b) Multisharing
c) Time tracing d) Multiprocessing
Ans. a
862. The first graphical user interface was designed by
a) Apple Inc.
b) Microsoft
c) Xerox Corporation
d) None of these
Ans. c
863. In 1973, Xerox PARC developed the Alto personal computer. It had a bitmapped screen, and was the first
computer to demonstrate the desktop metaphor and graphical user interface (GUI).
Restart of computer is called _____ when computer is already ON.
a) cold booting
b) warm booting
c) shut down
d) logging off
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-89-2048.jpg)
![864. Which of the following is the latest version of MS Windows?
a) Windows 7
b) Windows 8
c) Windows 14
d) Windows 8.2
Ans. b
Explanation: Windows 8 is a major release of the Windows NT operating system developed by Microsoft. It was
released to manufacturing on August 1, 2012 and Windows 10 was launched in 2015.
865. The purpose of DISKCOPY command is to [RBI Grade B 2014]
a) format the disk if it is not formatted before a write operation is initiated on it
b) overwrite the existing contents of the destination disk as it copies the new information to it
c) make an exact copy of a floppy disk
d) all of the above
Ans. d
866. In DOS, the DIR command is used to [SSC CGL 2013]
a) display content of a file
b) delete file
c) display list of files and sub-directories
d) copy files
Ans. c
867. A factor in the selection of source language is
a) programmer skill
b) language availability
c) program compatibility with other software
d) all of the above
Ans. c
868. Language which can easily interact with the hardware are called
a) High level languages b) Low level language
c) Middle level language d) All of the above
Ans. b
869. ____ Serves as the bridge between raw hardware and programming layer of a computer system.
a) Medium level language b) Low level language
c) High level language d) Both 1 and 2
Ans. a
Explanation: Medium-level language (MLL) is a computer programming language that interacts with the
abstraction layer of a computer system. Medium-level language serves as the bridge between the raw hardware
and programming layer of a computer system.
870. Which of the following is a machine independent program?
a) High level language b) Low level language
c) Assembly language d) Machine language
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-90-2048.jpg)
![871. Main application area of ALGOL is
a) General
b) Scientific
c) Engineering
d) Commercial
Ans. b
Explanation: ALGOL is short for algorithmic language. It is a family of portable programming languages for scientific
computations that had a strong influence on other languages.
872. LISP is designed for
a) Artificial intelligence
b) GUI
c) CUI
d) Optical fibre
Ans. a
Explanation: Lisp is a family of programming languages with fully parenthesized prefix notation. Originally specified
in 1958, Lisp is the second-oldest high-level programming language still in common use. Only Fortran is older, by one
year. Lisp's ability to compute with symbolic expressions rather than numbers makes it convenient for artificial
intelligence (AI) applications. While it isn't as popular as C, Python or Perl, Lisp is still used for AI programming as
well as several other functions.
873. Which of the following is not characteristic of COBOL?
a) It is a very standardised language
b) It is a very efficient in terms of coding and execution
c) It had limited facilities for mathematical notation
d) It is very readable language
Ans. b
Explanation: COBOL (Common Business Oriented Language) is an easy-to-learn language that can be compiled and
executed on a variety of computers. It supports a wide syntax vocabulary and features an uncluttered coding style.
Business-oriented capabilities. COBOL's advanced file handling capabilities enable it to handle huge volumes of data.
874. Which of the following is not a computer language? [SBI PO 2014]
a) BASIC
b) COBOL
c) LOTUS
d) FORTRAN
Ans. c
Explanation: Lotus 1-2-3 is a discontinued spreadsheet program from Lotus Software. It was the first killer
application of the IBM PC, was hugely popular in the 1980s.
875. Translator program used in assembly language is called [SBI Clerk 2012]
a) Compiler
b) Interpreter
c) Translation
d) Assembler
Ans. d](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-91-2048.jpg)
![876. Windows XP released in
a) 2000
b) 1998
c) 1999
d) 2001
Ans. d
877. In the split window mode, one title bar looks darker than the other, because [RBI Grade B 2012]
a) Darker title bar shows window not in use
b) Darker title bar shows active window
c) Darker title bar shows unavailable window
d) Both ‘1’ and ‘2’
Ans. b
878. Which of the following refers to the rectangular area for displaying information and running programs? [SBI PO
2013]
a) Desktop
b) Dialog box
c) Menu
d) Window
Ans. d
879. Which of the following are lists of commands that appear on the screen? [IBPS Clerk 2015]
a) GUIs b) Icons
c) Menus d) Windows
Ans. c
880.The extension of paint file is/are
a) .png b) .jpg
c) .bmp d) All of these
Ans. d
881. When embedding object into document, one of the following occurs [RBI Grade B 2014]
a) embedded object becomes a part of the document
b) embedded object remains outside object to the document, but loaded with document
c) Both becomes a zip file
d) Both ‘1’ and ‘2’
Ans. b
882. A ___ is an additional set of commands that the computer displays after you make a selection from main menu.
[SBI Clerk 2009]
a) dialog box
b) sub menu
c) menu selection
d) All of these
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-92-2048.jpg)
![883. In order to choose the font for a sentence in a word document [IBPS Clerk 2011]
a) select font in the format menu
b) select font in the Edit menu
c) select font in the tools menu
d) select font in the view menu
Ans. a
884. Which of the following is not a font style?
a) Bold b) Italic c) Regular d) Superscript
Ans. d
885. Auto-text can be used to insert ____ in document. [RBI Grade B 2014]
a) Text b) Graphics c) Either 1 or 2 d) Both ‘1’ and ‘2’
Ans. d
886. In Word, you can force a page break [IBPS PO 2011]
a) by positioning your cursor at the appropriate place and pressing the F1 key
b) by positioning your cursor at the appropriate place and pressing the Ctrl + Enter
c) by using the insert/section break
d) by changing the font size of your document
Ans. c
887. Where you can find the horizontal split bar on MS-Word screen?
a) On the left of horizontal scroll bar
b) On the right of horizontal scroll bar
c) On the top of the vertical scroll bar
d) On the bottom of vertical scroll bar
Ans. c
888. Which of the following is not available on the ruler of MS-Word screen?
a) Left indent b) Right indent
c) Centre indent d) All of these
Ans. c
889. You specify the save details of your file in the [RBI Grade B 2013]
a) “Save as a file” dialog box
b) “Save the file as” dialog
c) “File save” dialog box
d) Any of ‘1’ and ‘2’
Ans. a
890. Magnifier button is available on [RBI Grade B 2014]
a) Print Preview toolbar
b) Standard toolbar
c) Formatting toolbar
d) Both ‘A’ and ‘B’
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-93-2048.jpg)
![891. Which command is used to calculate total characters in a cell? [RBI Grade B 2014]
a) Len b) Length c) Mid d) Sid
Ans. a
Explanation: LEN returns the number of characters in a text string. LENB returns the number of bytes used to
represent the characters in a text string.
892. The function TODAY( ) in Excel, enters the current [RBI Grade B 2014]
a) System time in a cell
b) System date and time in a cell
c) System date only
d) Time at which the current file was opened
Ans. d
893. =Sum(B1:B10) is an example of a
a) function
b) formula
c) cell address
d) value
Ans. b
894. In Excel, an active cell can be represented by
a) 4A
b) A4
c) A$4
d) $A$4
Ans. b
895. Cell address $A4 in a formula means it is a
a) mixed cell reference
b) absolute cell reference
c) relative cell reference
d) All of the above
Ans. a
Explanation: A mixed cell reference is either an absolute column and relative row or absolute row and relative
column. When you add the $ before the column letter you create an absolute column or before the row number you
create an absolute row. For example, $A1 is absolute for column A and relative for row 1, and A$1 is absolute for
row 1 and relative for column A. If you copy or fill the formula across rows or down columns, the relative references
adjust, and the absolute ones don’t adjust.
896. In a worksheet in MS-Excel, what is short-cut key to hide entire row? [SBI PO 2014]
a) Ctrl + 2
b) Ctrl + 9
c) Ctrl + N
d) Ctrl –
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-94-2048.jpg)
![897. To select entire row, which shortcut is used? [SBI PO 2014]
a) Shift + Space b) Ctrl + Space c) Alt + Space d) None of these
Ans. a
898. Which of the following bypasses the print dialog box when printing individual slides or an entire presentation?
a) File, Print preview b) Print button c) File, Print d) Ctrl + P
Ans. d
899. How many types of relationships are there in MS-Access?
a) 3 b) 4 c) 5 d) 6
Ans. a
900. What is the default size of the data type in MS-Access? [SBI Clerk 2010]
a) 50 b) 60 c) 70 d) 80
Ans. a
901. We can’t make query by Insert menu? *RBI Grade B 2013+
a) True
b) False
c) Cannot say
d) Sometimes
Ans. a
902. The cardinality property of a relation, refers to the
a) number of database b) number of columns
c) number of rows d) number of tables
Ans. c
Tip: cardinality of a relationship is the number of tuples (rows) in a relationship.
903. What is the overall term for creating, editing, formatting, storing, retrieving a text document? [IBPS PO 2012]
a) Word processing
b) Spreadsheet design
c) Web design
d) Database management
Ans. d
904. In which, the database can be restored up to the last consistent state after the system failure?
a) Backup
b) Recovery
c) Redundancy
d) Security
Ans. b
905. A collection of conceptual tools for describing data, relationships, semantics and constraints is referred to as
[IBPS Clerk 2012]
a) E-R model b) Database
c) Data Model d) DBMS
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-95-2048.jpg)
![906. ____ means that the data contained in a database is accurate and reliable.
a) Data redundancy b) Data integrity c) Date reliability d) Data consistency
Ans. b
907. Which of the following contains data descriptions and defines the name, data type and length of each field in
the database?
a) Data dictionary b) Data table c) Data record d) Data field
Ans. a
908. Which database language is used to access data in existing database?
a) DDL b) DML c) DCL d) None of these
Ans. b
Tip: Data Manipulation Language (DML) is a set of special commands that allows us to access and manipulate data
stored in existing schema objects
909. An E-R diagram is a graphic method of presenting [IBPS Clerk 2011]
a) Primary keys and their relationships
b) Primary keys and their relationships to instances
c) entity classes and their relationships
d) entity classes and their relationships to primary keys
Ans. c
910. In an E-R diagram, an entity set is are represented by
a) rectangle
b) square
c) ellipse
d) triangle
Ans. a
911. In E-R diagram, relationship type is represented by [IBPS Clerk 2012]
a) ellipse
b) dashed ellipse
c) rectangle
d) diamond
Ans. d
912. _____ is the transmission of data between two or more computers over communication links.
a) Communication
b) Networking
c) Data communication
d) Data networking
Ans. c
913. Communication channel having _____ types.
a) 1 b) 2 c) 3 d) 4
Ans. c (simplex, half-duplex, and full-duplex)](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-96-2048.jpg)
![914. Which of the following is the fastest communication channel?
a) Radio wave b) Microwave
c) Optical fibre d) All are operating at nearly the same propagation speed
Ans. b
Explanation: A microwave is the fastest communication channel whereas optical fiber is a way of transferring data
not a way of communication. Microwave is a line-of-sight wireless communication technology that uses high
frequency beams of radio waves to provide high speed wireless connections that can send and receive voice, video,
and data information.
915. What do we call a network whose elements may be separated by some distance? It usually involves two or
more network and dedicated high speed telephone lines. [SBI Clerk 2015]
a) LAN b) WAN c) URL d) Server
Ans. a
916. Ethernet, token ring and token bus are types of [SBI Associates 2012]
a) WAN b) LAN c) Communication channels d) Physical media
Ans. b
917. _____ allows LAN users to share computer programs and data.
a) Communication server
b) Print server
c) File server
d) All of the above
Ans. c
Tip: A file server is a computer containing files available to all users connected to a local-area network (LAN). In
some LANs, a microcomputer is designated as the file server, while in others it is a computer with a large disk drive
and specialized software.
918. Which of the following items is not used in Local Area Network (LANs)? [SSC CGL 2012]
a) Interface card
b) Cable
c) Computer
d) Modem
Ans. d
919. P2P is a _____ application architecture. [IBPS Clerk 2012]
a) client/server b) distributed
c) centralised d) 1-tier
Ans. a
Explanation: In a peer-to-peer (P2P) network, each computer acts as both a server and a client—supplying and
receiving files—with bandwidth and processing distributed among all members of the network. Such a decentralized
network uses resources more efficiently than a traditional network and is less vulnerable to systemic failure.
920. In OSI network architecture, the routing is performed by [IBPS Clerk 2012]
a) Network layer b) Data link layer
c) Transport layer d) Session layer
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-97-2048.jpg)
![921. How many bits are there in the Ethernet address? [SBI Clerk 2011]
a) 64 bits b) 48 bits c) 32 bits d) 16 bits
Ans. b
Explanation: The Ethernet address is 48 bits long and normally displayed as 12 hexadecimal digits. The MAC address
is often referred to as the Ethernet Address on an Ethernet network.
922. An IP address is ____ bit address [SSC CGL 2017]
a) 8 bit b) 16 bit
c) 32 bit d) 64 bit
Ans. c
Explanation: An IPv4 address is 32 bits. An IP Address is shown as 4 decimal numbers representing 4 bytes: d.d.d.d
where d = decimal number (0 - 255). High order bits are the network identifier and lower order bits are the host
identifier.
923. The ____ service allows a group of Internet users to exchange their views on some common topic.
a) nicnet
b) milnet
c) telnet
d) usenet
Ans. d
Explanation: Usenet is a worldwide distributed discussion system available on computers. It was developed from the
general-purpose Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Ellis conceived the
idea in 1979, and it was established in 1980.
924. The ____ uses an addressing schema known as URL indicate the location of files on the web. [SSC CGL 2017]
a) Java Script b) World Wide Web c) SQL d) String
Ans. b
925. Which of the following is most commonly used to identify returns visitors to a website?
a) logged-in visitors b) digital certificates
c) electronic time stamping d) cookies
Ans. d
926. Cracked software are another source of
a) E-mail attack
b) Virus attack
c) Trojan horse
d) All of these
Ans. b
927. A computer virus is
a) deliberately created
b) created accidently
c) produced as result of some program error
d) All of the above
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-98-2048.jpg)
![928. The first PC virus was developed in
a) 1980 b) 1984 c) 1986 d) 1988
Ans. c
Explanation: Brain is the industry standard name for a computer virus that was released in its first form on 19
January 1986, and is considered to be the first computer virus for the IBM Personal Computer and compatibles.
929. What is a person called who uses a computer to cause harm to people or destroy critical systems? [IBPS Clerk
2014]
a) Cyber Terrorist
b) Black-hat-Hacker
c) Cyber Cracker
d) Hacktivist
Ans. c
Tip: computer cracker as "an individual who attempts to access computer systems without authorization. These
individuals are often malicious, as opposed to hackers, and have many means at their disposal for breaking into a
system."
930. A firewall operated by [SBI Clerk 2010]
a) The pre-purchase phase
b) isolating intranet from extranet
c) screening packets to/from the network and provide controllable filtering of network traffic
d) All of the above
Ans. c
931. Which of the following a computer’s memory, but unlike a virus, it does not replicate itself? *SBI PO 2011+
a) Trojan Horse b) Logic bomb c) Cracker d) Firewall
Ans. b
Explanation: A logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious
function when specified conditions are met. For example, a programmer may hide a piece of code that starts
deleting files, should they ever be terminated from the company.
932. What will you insert, when you need to see all the information from two tables on one form?
a) A page break
b) A subform
c) A linked command button
d) All of the above
Ans. b
Explanation: A subform is a form within a form. It is generally used whenever you want to display data from
multiple tables where there is a one-to-many relationship. For example, you would use a subform if you wanted to
display an order with the order details.
933. To select several cells or ranges that are not touching each other, what would you do while selecting?
a) Hold down the Ctrl key
b) Hold down the Shift key
c) Hold down the Alt key
d) Hold down Ctrl + Shift key
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-99-2048.jpg)

![942. Internet requires
a) an international agreement to connect computers
b) a local area network
c) a commonly agreed set of rules to communicate between computers
d) a world wide web
Ans. c
943. Which of the following is billionth of a second?
a) Gigabyte
b) Terabyte
c) Nanosecond
d) Microsecond
Ans. c
Explanation: A nanosecond (ns) is a unit of time in the International System of Units (SI) equal to one billionth of a
second, that is, 1⁄1 000 000 000 of a second, or 10−9
seconds.
944. In an ER diagram, attributes are represented by
a) rectangle b) square c) ellipse d) triangle
Ans. c
Explanation: Attributes are included to include details of the various entities that are highlighted in a conceptual ER
diagram. Attributes are characteristics of an entity, a many-to-many relationship, or a one-to-one relationship.
945. Which is a shortcut key to insert a new worksheet in MS-Excel?
a) Ctrl + W b) Ctrl + n c) Ctrl + 1w d) Shirt + F11
Ans. d
Tip: Shift+F11 inserts a new worksheet. Alt+F11 opens the Microsoft Visual Basic For Applications Editor, in which
you can create a macro by using Visual Basic for Applications (VBA). F12 Displays the Save As dialog box
946. Which of the following machines is called a smart machine? [Cyber Olympiad 2014]
a) Mobile phones b) Television c) Computer d) Microwaves
Ans. c
947. Which of the following jumbled words can complete the sentence given below?
Computer is a _____ machine.
a) Digir
b) Budm
c) Lows
d) Marts
Ans. d
Tip: This is an character arranging question from reasoning. After arrange the word “Marts” we make “Smart”.
948. What is common between Man and Computer?
a) Both can get tired
b) Both can draw and calculate
c) Both can take decisions
d) Both can show emotions
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-101-2048.jpg)

![956. Program promised by publisher but never released –
a) Vaporware b) Shareware c) Software d) Mindware
Ans. a
Tip: software or hardware that has been advertised but is not yet available to buy, either because it is only a concept
or because it is still being written or designed.
957. Computer derives its name from the word _____ which means calculation. [Bank Clerk 2008]
a) Computare
b) Calcite
c) Calculator
d) Both (A) and (B)
Ans. a
Tip: The word 'compute' comes from the Latin word computare, meaning "arithmetic, accounting, reckoning".
958. Computer gathers data, which means that they allow users to ____ data. [Bank Clerk 2010]
a) present b) input c) output d) store
Ans. b
959. The word ‘Abacus’ was derived from the greek word _____, which means a table or a board covered with dust.
a) Abax b) Addition c) Abqua d) Substraction
Ans. a
960. Antikythera mechanism was mainly used to perform
a) addition b) multiplication and division c) astronomical calculation d) logarithm
Ans. c
Tip: The Antikythera mechanism is an Ancient Greek hand-powered orrery, described as the oldest example of an
analogue computer used to predict astronomical positions and eclipses decades in advance.
961. Rabdologia was the technology used for calculation purpose introduced in
a) 1917
b) 1901
c) 1617
d) 1801
Ans. c (Rabdology Book written by John Napier)
962. Napier’s bones performs
a) addition and subtraction
b) multiplication and division
c) only addition
d) Both (A) and (B)
Ans. b
963. Pascaline is also known as [BOB Assistant 2009]
a) mechanical machine
b) adding machine
c) division machine
d) difference machine
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-103-2048.jpg)
![964. _____ was the first digital mechanical calculator, which was designed to perform addition, subtraction,
multiplication and division. It can also extract square root by a series of repeated addition.
a) Punch card system
b) Pascaline
c) Stepped reckoner
d) ABC Computer
Ans. c
Tip: The stepped reckoner or Leibniz calculator was a mechanical calculator invented by the German mathematician
Gottfried Wilhelm Leibniz around 1672 and completed in 1694. The name comes from the translation of the German
term for its operating mechanism, Staffelwalze, meaning "stepped drum".
965. The first mass-produced mechanical calculating device was
a) Pascaline b) Arithmometer c) Punch card d) Mark-1
Ans. b
Tip: The arithmometer, invented by Charles Xavier Thomas de Colmar in 1820, was the first commercially successful
calculating machine capable of performing addition, subtraction, multiplication and division.
966. What do you mean by Jacquard loom? [SBI PO 2011]
a) A bird found in Japan
b) A weaving machine used punched cards
c) The first computer controlled loom
d) A machine for writing match tables
Ans. b
967. The first electro-mechanical computer MARK-1 invented by
a) John W Mauchly b) Atanasoff-Berry
c) Howard Aiken d) Clifford Berry
Ans. c
Explanation: The Harvard Mark I, or IBM Automatic Sequence Controlled Calculator, was a general-purpose
electromechanical computer used in the war effort during the last part of World War II. One of the first programs to
run on the Mark I was initiated on 29 March 1944 by John von Neumann.
968. Which of the following computer system introduced the idea of binary calculation?
a) ABC computer
b) Colossus
c) ENIAC
d) EDSAC
Ans. a
Tip: The Atanasoff–Berry computer was the first automatic electronic digital computer in 1937.
969. The first electronic digital computer contained? [SBI PO 2008]
a) Electronic valves b) Vaccum tubes
c) Transistors d) Semiconductor memory
Ans. a
970. In second generation, which type of memory was used to store data? [IBPS RRB 2011]
a) Paper tapes b) Magnetic drum c) Magnetic core d) Magnetic tape
Ans. c](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-104-2048.jpg)
![971. In which generation did multi-programming start? [SBI Clerk 2010]
a) First generation b) Second generation
c) Third generation d) Fourth generation
Ans. c
972. Oracle was introduced in
a) first generation b) second generation c) third generation d) fourth generation
Ans. d
973. A micro computer can be defined as
a) a small, low-cost digital computer b) which consists of a microprocessor
c) a storage unit and input/output channel d) all of the above
Ans. d
974. Which of the following is the smallest computer? [SBI Clerk 2011]
a) Notebook b) Laptop c) Desktop d) Workstation
Ans. a
975. Which was the world’s first mini computer?
a) PDP-I b) PDP-II c) IBM System/36 d) VAX 11/780
Ans. a
Tip: The PDP-1 (Programmed data processor-1) is the first computer in Digital Equipment Corporation's PDP series
and was first produced in 1959. It is famous for being the computer most important in the creation of hacker culture
at Massachusetts Institute of Technology, BBN and elsewhere.
976. Which organisation developed a SAGA-220 super computer in 2011?
a) C-DAC b) FCC c) ISRO d) BARC
Ans. c
Tip: SAGA-220 (Supercomputer for Aerospace with GPU Architecture-220 teraflops) is a supercomputer built by the
Indian Space Research Organisation (ISRO).
977. What is an embedded system? [IOB PO 2011]
a) A program that comes wrapped in a box
b) A program that is permanently part of a computer
c) A computer that is part of a large computer
d) A computer and software system that controls a machine or appliance
Ans. d
978. Which characteristic of computer distinguishes it from electronic calculators? [Allahabad Bank PO 2011]
a) Accuracy b) Storage c) Versatility d) Automatic
Ans. b
Tip: Computer can store data but calculator does not.
979. Which of the following does not describe one or more characteristic(s) of a computer?
a) Electronic b) External storage
c) Stored program d) Program modification at execution
Ans. d](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-105-2048.jpg)
![980. The proper definition of a modern digital computer is [SBI PO 2010]
a) an electronic automated machine that can solve problem involving words and numbers
b) a more sophistic and modified electronic pocket calculator
c) any machine that can perform mathematical operations
d) a machine that works on binary code
Ans. d
981. Computer system are comprised of
a) hardware, programs, information, people and networks
b) hardware, software, procedure, network and people
c) hardware, programs, information, people and procedure
d) hardware, programs, processors, procedures, networks and people
Ans. c
982. Which of the following program is not a utility? [DRDO GTRE 2017]
a) Editor b) Debugger c) Spooler d) None of these
Ans. c
Explanation: The Spooler is a special process that manages access to printers by multiple users. For most users, the
function of the Spooler is transparent. They generate a job for a printer and go to the printer to pick up the output. The
Spooler permits users to continue working without waiting for a print job to finish printing.
Utility Program: A program that performs a specific task related to the management of computer functions, resources, or
files, as password protection, memory management, virus protection, and file compression.
983. A Common LED is made up of – [DRDO 2008]
a) Intrinsic Semiconductor b) Direct Semiconductor
c) Degenerate semiconductor d) Indirect Semiconductor
Ans. b
984. GSM system uses TDMA with – [DRDO 2008]
a) 32 users per channel b) 16 users per channel
c) 8 users per channel d) 4 users per channel
Ans. c
985. In the register indirect addressing mode of 8085 microprocessor, data is stored – [DRDO 2008]
a) At the address contained in the register pair b) In the register pair
c) In the accumulator d) In a fixed location of the memory
Ans. a
986. What is the keyboard shortcut for opening a new tab in the Google chrome web browser for windows? [DRDO
CVRDE 2017]
a) Alt + N b) Ctrl + T c) Alt + Ctrl + T d) Alt + T
Ans. b
987. For which one of the following ultraviolet light is used to erase the stored contents? [DRDO 2008]
a) PROM
b) EPROM
c) EEPROM
d) PLA
Ans. b](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-106-2048.jpg)
![988. In 8085 microprocessor, the accumulator is a – [DRDO 2008]
a) 4 bit register b) 8 bit register c) 16 bit register d) 32 bit register
Ans. b
989. Which of the following memory has highest access speed? [DRDO CVRDE 2017]
a) Hard Disk b) RAM c) ROM d) Cache Memory
Ans. d
990. The multiple access communication scheme in which each user is allocated the full available channel spectrum
for a specific duration of time is known as – [DRDO 2008]
a) CDMA b) FDMA c) TDMA d) MC-CDMA
Ans. a
991. Thermal printer uses _____ coated paper, which turns black when heat is applied. [DRDO CVRDE 2017]
a) Chromium b) Bisphenol-A c) Nickel d) Toner powder
Ans. b
992. Natural language understanding is used in: [DRDO CURDE 2017]
a) natural language interfaces b) natural language front ends
c) text understanding systems d) all of the above
Ans. d
993. The device used in the third generation computers is _____ (DRDO GTRE 2017)
a) Vacuum tubes b) Transistors c) Integrated Circuit d) VLSI
Ans. c
994. Which of the following GUI component user should choose one or more options from one set allow? [DRDO
CVRDE 2017]
a) Radio Button b) Dropdown list c) Check box d) Text Box
Ans. c
995. Which of the following/statement are correct? (DRDO, CVRDE 2017)
(i) Access to primary memory is more than the access time of secondary memory.
(ii) For the same storage capacity, DRAM is cheaper than SRAM.
a) only (i) b) Both (i) and (ii) c) Only (ii) d) Both are wrong
Ans. c
996. Which of the following is an example of High speed microprocessor? (DRDO GTRE 2017)
a) Pentium b) C.D. Rom c) Keyboard d) Printer
Ans. a
997. _____ gave stored program concept in which program and data to be processed are stored in the same
memory. [DRDO CVRDE 2017]
a) John Von Neumann b) Alan Turing c) Charles Babbage d) Bill Gates
Ans. a](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-107-2048.jpg)
![998. In a desktop computer the board containing micro-processor, RAM and other components is called ______
board. (DRDO GTRE 2017)
a) Graphics b) Motherboard c) White d) Black
Ans. b
999. Program counter (PC) register is an integral part of: [DRDO CVRDE 2017]
a) Hard Disk b) RAM c) Cache memory d) CPU
Ans. d
1000. The set of wires, connecting the microprocessor and the main memory, through which the data flows is called:
[DRDO GTRE 2017]
a) Memory
b) Data wire
c) Database
d) Databus
Ans. d
Computer Best MCQ E-Book for all Competitive Exams [9000+ Exam Question in English]
Rs.25/-
Computer Best MCQ E-Book for all Competitive Exams (2400+ Exam Question in Hindi)
Rs.19/-
HEETSON
Telegram https://t.me/Heetson_Official
WhatsApp Channel
/heetsoniti
/heetsoniti
WhatsApp: 8901025610](https://image.slidesharecdn.com/computermcqquestionbankinenglishforallcompetitiveexams-heetsonpublication-251002031533-732432bc/75/Computer-MCQ-Question-Bank-in-English-for-all-Competitive-Exams-Heetson-Publication-108-2048.jpg)