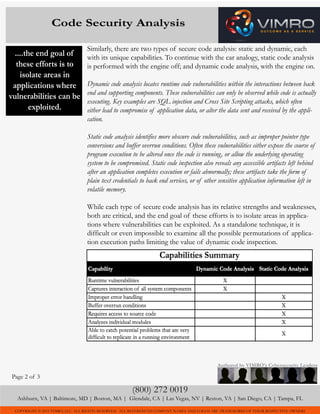
Static and dynamic code analysis are both critical for cybersecurity but analyze code in different ways. Static code analysis examines code without it being executed to find obscure vulnerabilities, while dynamic analysis tests executing code to discover runtime issues. The document recommends first using static analysis on individual code modules, then performing dynamic analysis once modules are combined into a full application. Conducting both types of analysis is important to fully isolate exploitable vulnerabilities.