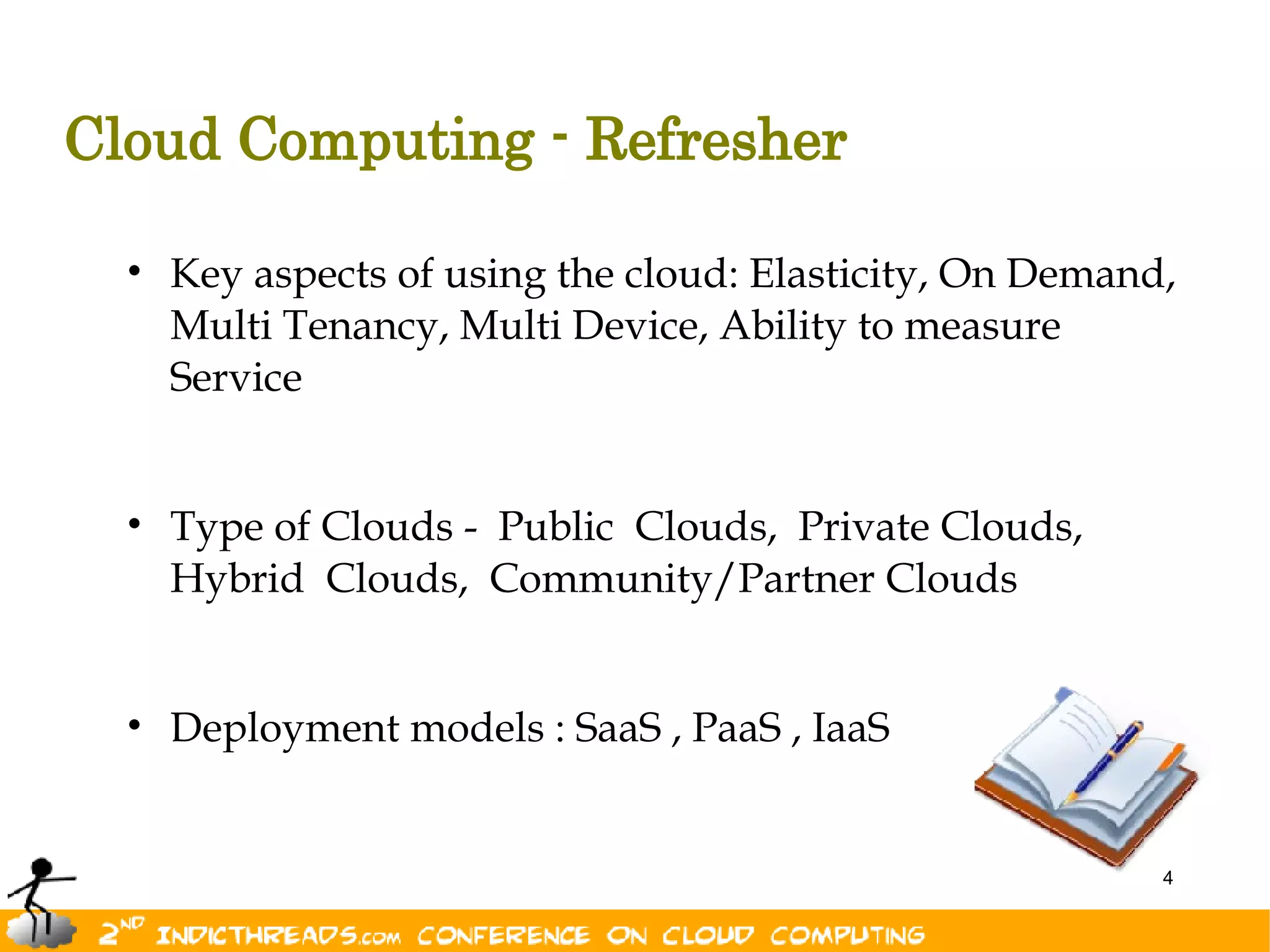
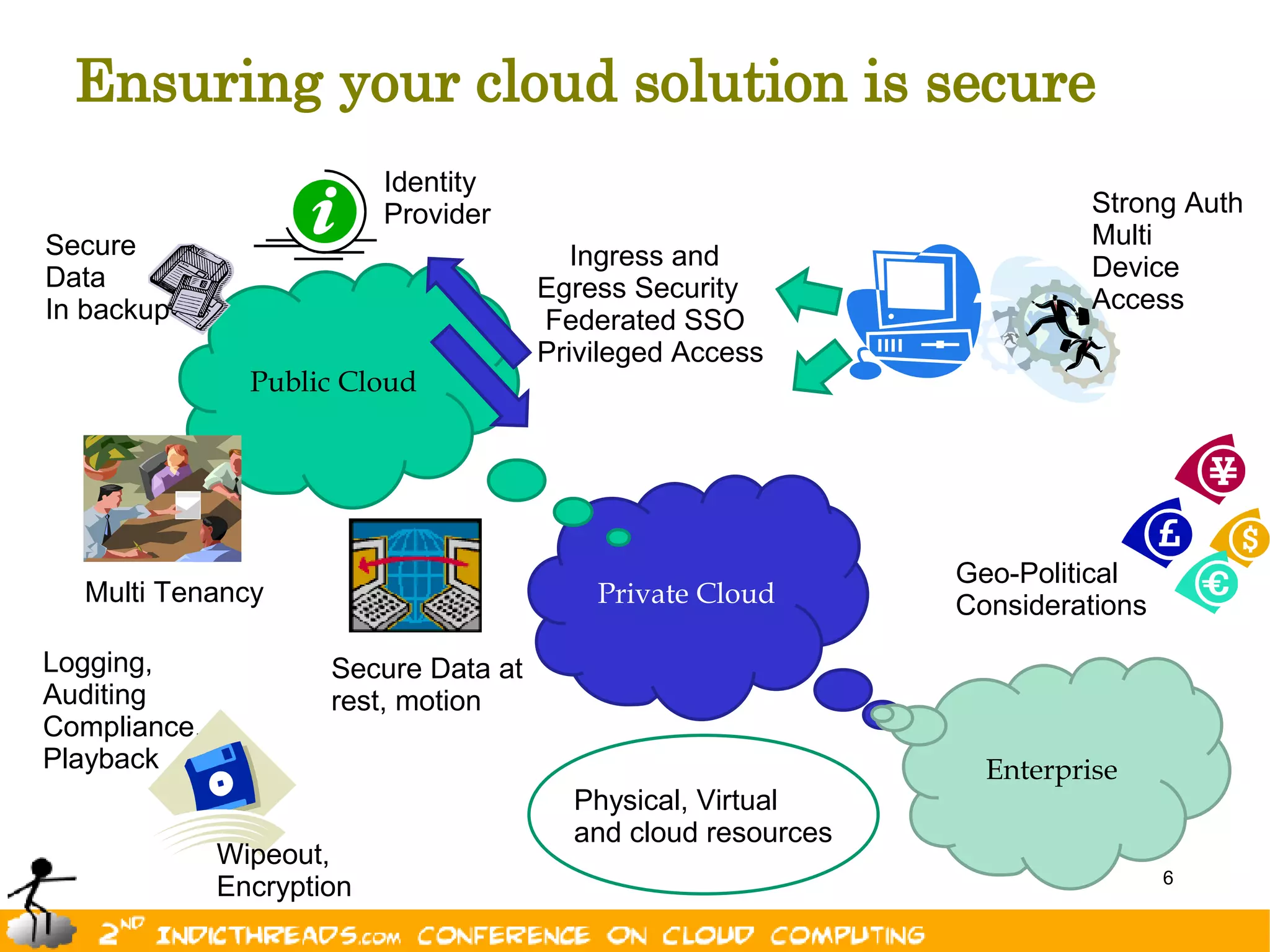
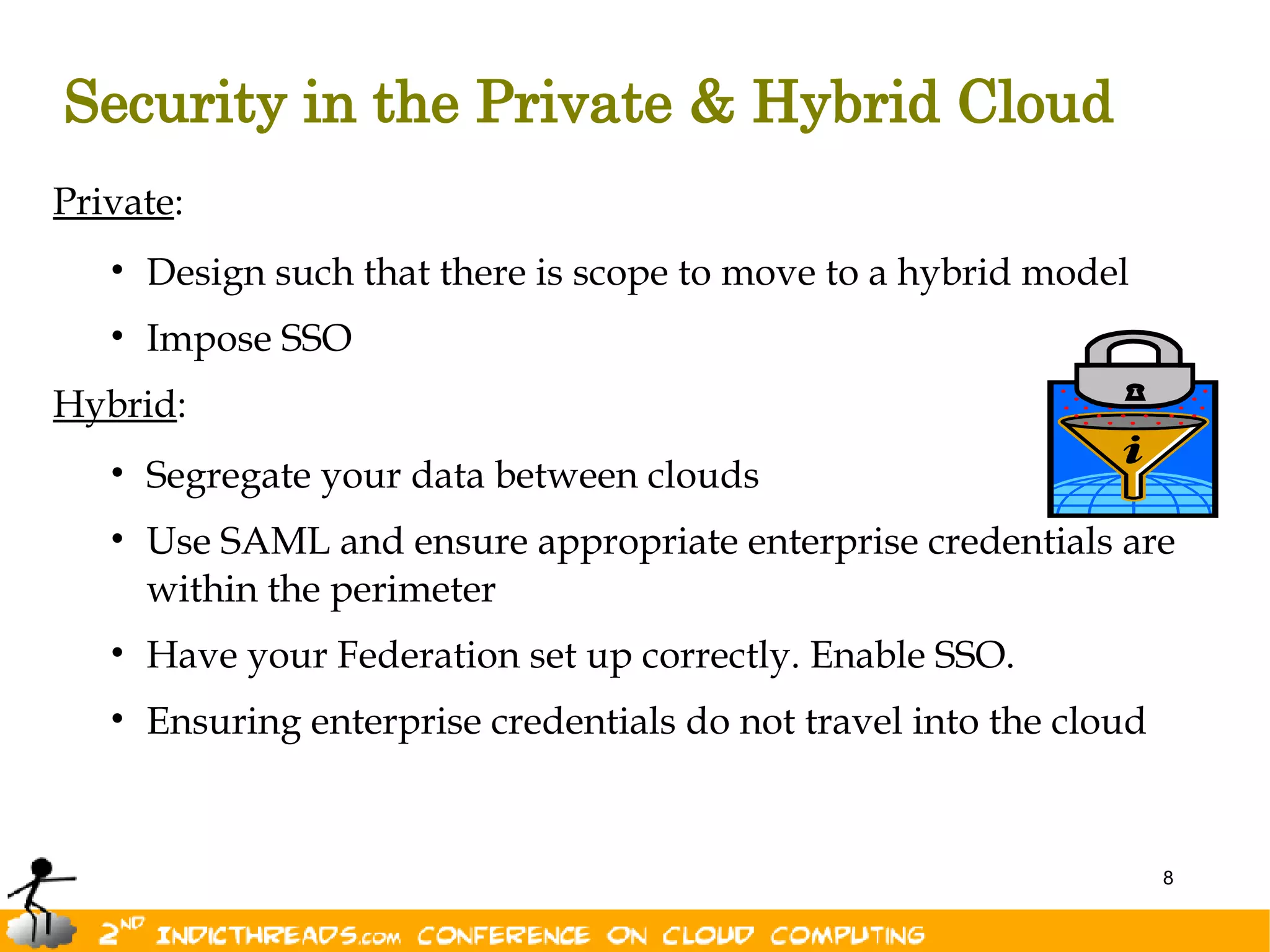
The document outlines key aspects of cloud security, including the importance of identity management, multi-factor authentication, and compliance across various cloud deployment models (public, private, hybrid). It highlights security considerations such as data protection, user management, and maintaining secure access across multiple devices. Ultimately, effective cloud security is essential for successfully leveraging cloud services.