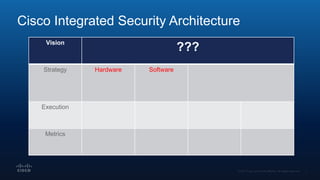
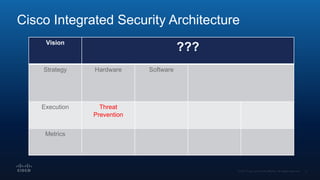
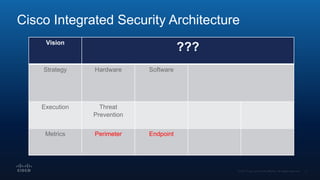
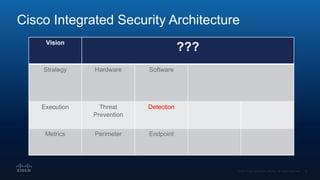
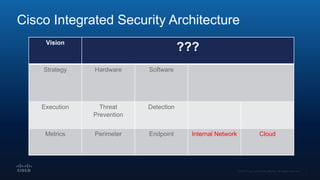
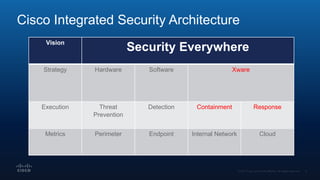
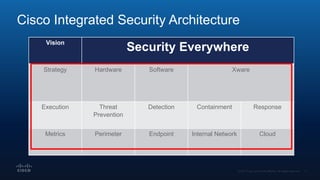
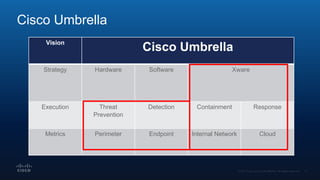
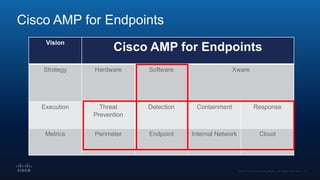
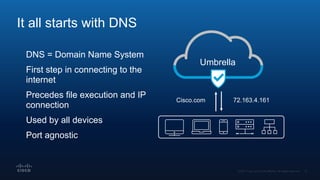
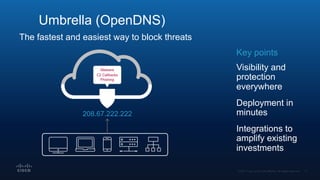
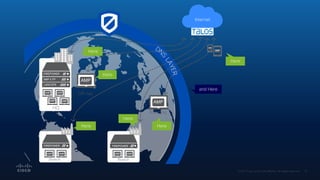
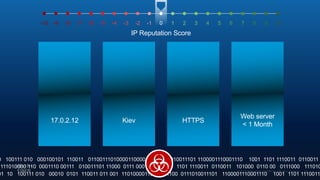
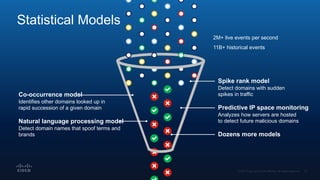
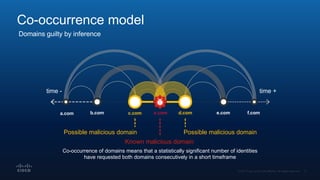
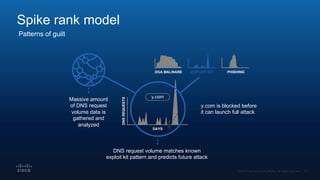
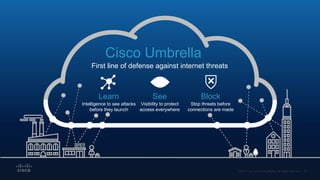
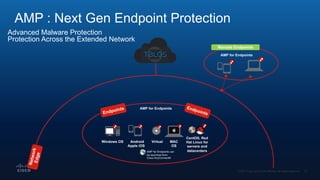
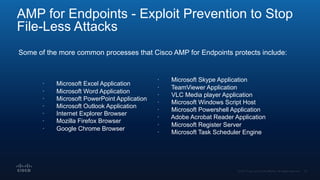
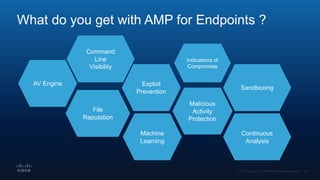
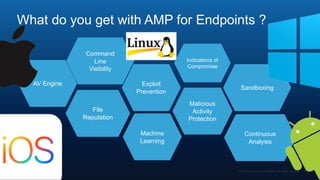
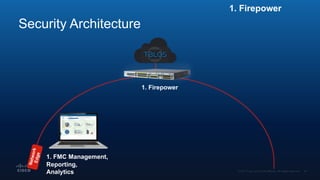
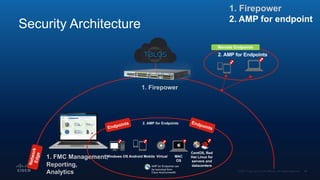
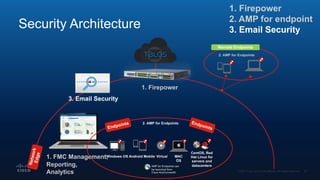
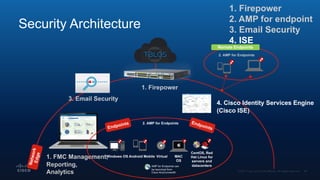
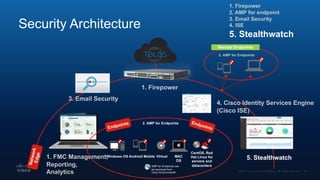
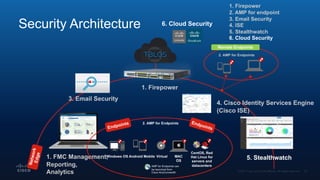
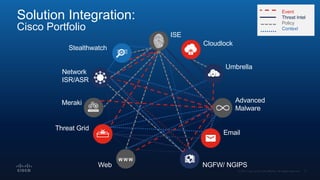
The document outlines Cisco's multi-layer security architecture focusing on real-time threat detection and remediation strategies. It emphasizes the importance of next-gen endpoint protection, such as Cisco AMP, which combines machine learning and behavior analytics to defend against advanced threats like ransomware and file-less attacks. The materials also discuss the necessity of visibility across networks and endpoints, leveraging Cisco Umbrella and other tools to enhance security in increasingly perimeter-less corporate environments.