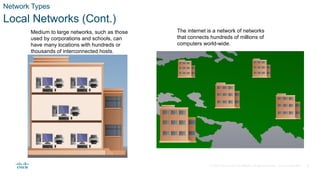
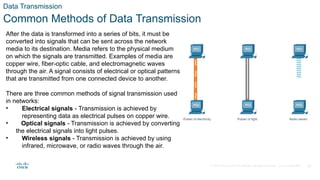
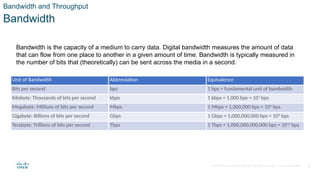
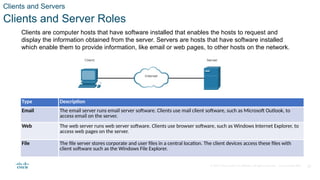
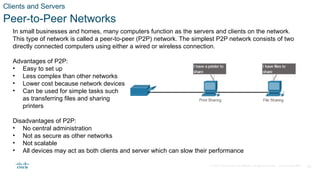
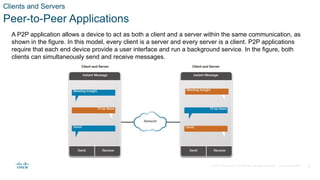
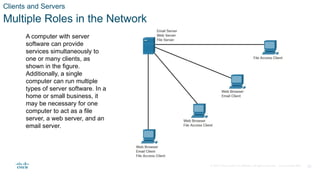
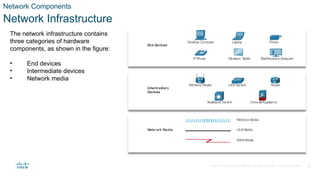
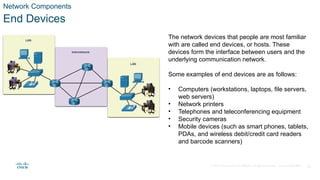
The document outlines the fundamentals of network communication, detailing types of networks, data transmission methods, bandwidth, and the roles of clients and servers. Key concepts include the definitions of various connected devices, the nature of data types (volunteered, observed, inferred), and significant factors affecting network throughput. It also emphasizes the necessary components of network infrastructure, categorizing them into end devices, intermediate devices, and network media.