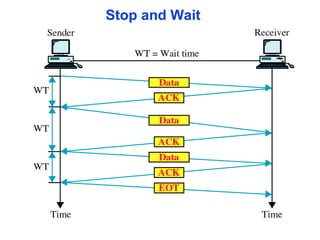
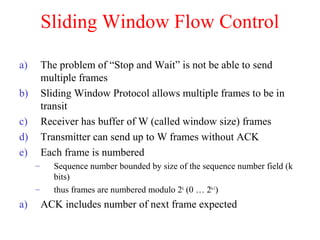
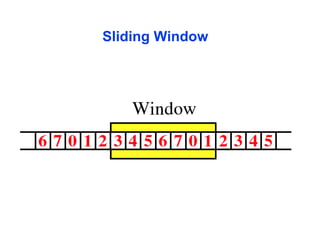
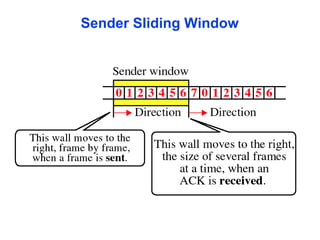
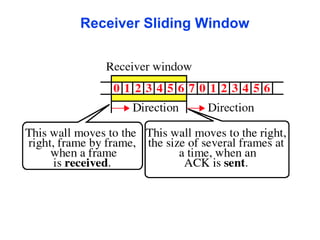
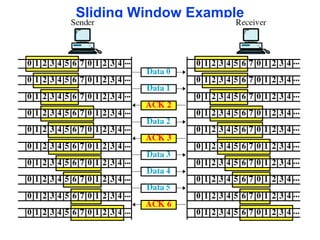
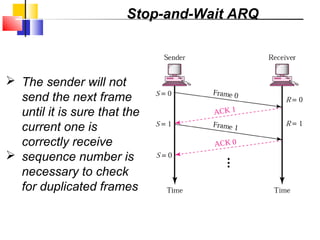
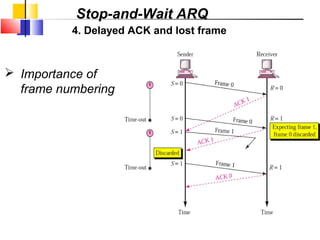
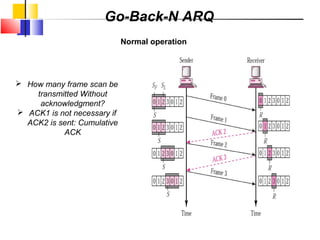
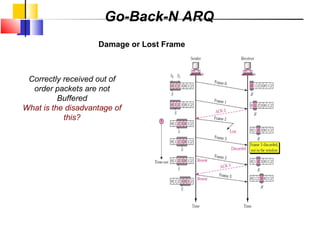
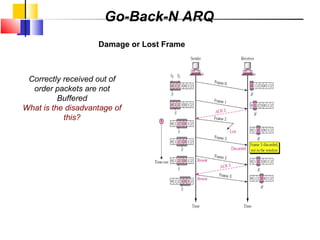
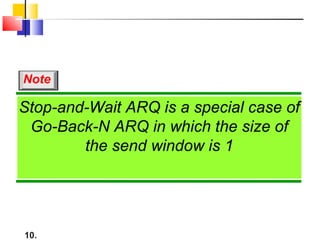
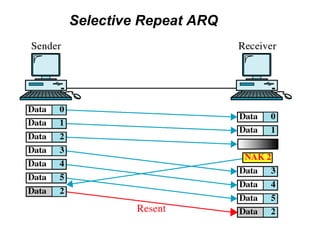
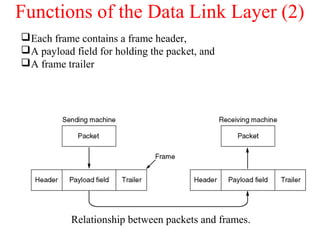
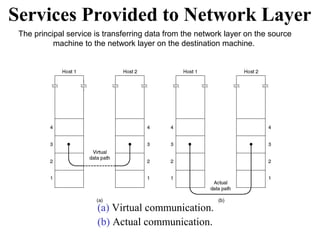
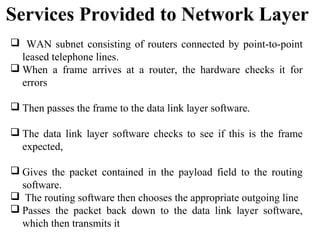
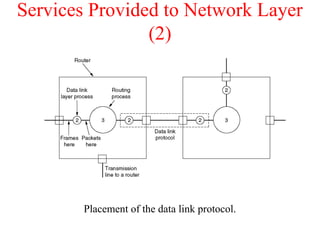
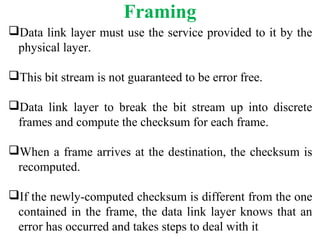
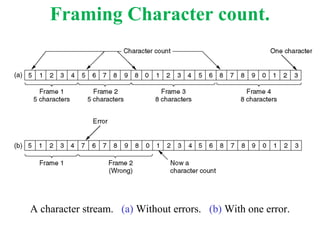
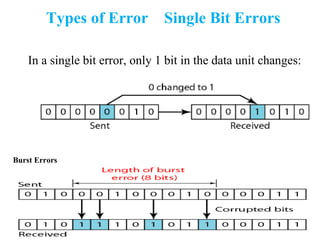
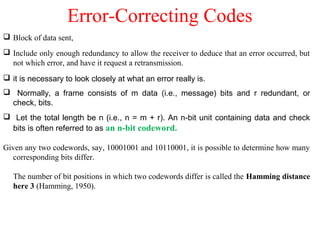
The document outlines the functions and responsibilities of the data link layer, including services provided to the network layer such as framing, error control, and flow control. It discusses various techniques for framing and error detection, including bit and byte stuffing, as well as error-correcting codes like Hamming codes. Additionally, it describes flow control methods such as stop-and-wait ARQ, go-back-N ARQ, and selective repeat ARQ, emphasizing their roles in ensuring reliable data transmission.










![Lecture 4: 9-6-01 23
CRC Example
Want:
D.2r XOR R = nG
equivalently:
D.2r = nG XOR R
equivalently:
if we divide D.2r by G,
want reminder Rb
R = remainder[ ]
D.2r
G
10111010011](https://image.slidesharecdn.com/chapter-4datalinklayer-180908074442/85/Chapter-4-data-link-layer-23-320.jpg)