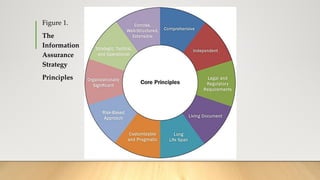
The document provides an overview of information assurance concepts and strategies. It discusses developing an information assurance strategy based on 10 core principles including being comprehensive, independent, compliant with legal requirements, and risk-based. It also covers information assurance concepts such as the CIA triad of confidentiality, integrity and availability, and defense-in-depth approach using segmentation and multiple layers of security controls. The document emphasizes that information assurance is important for protecting critical assets, meeting compliance requirements, and gaining a competitive advantage.