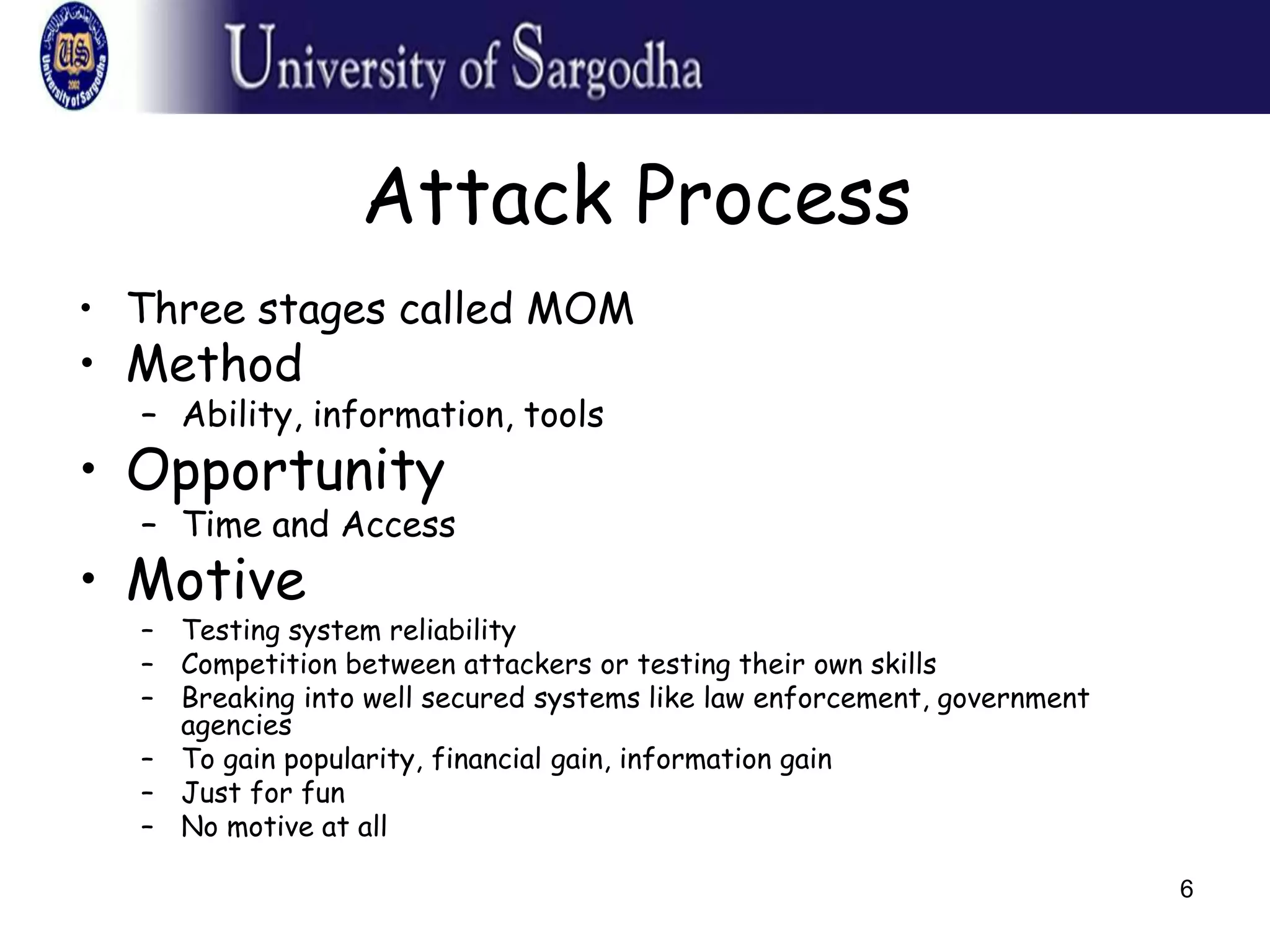
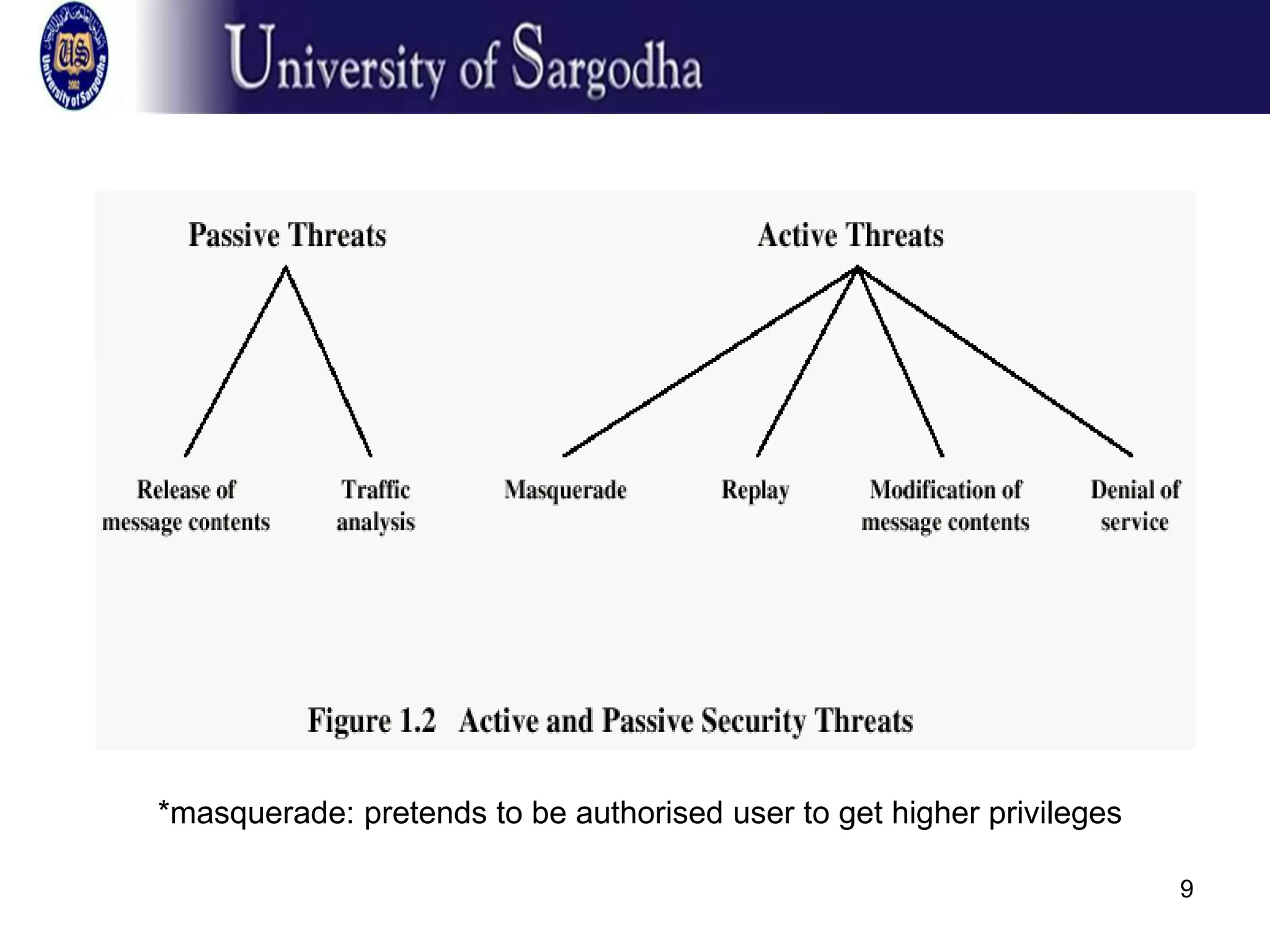
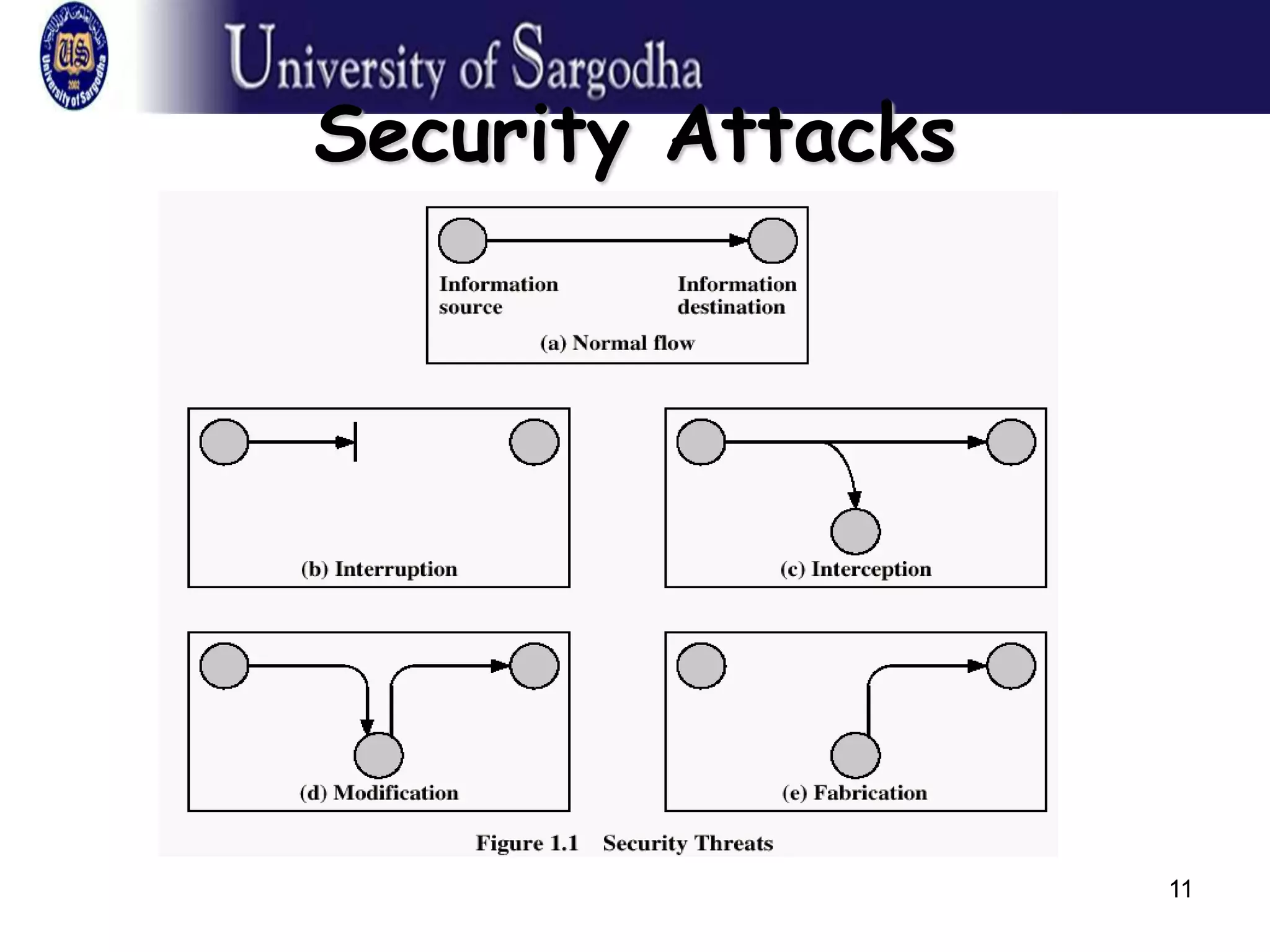
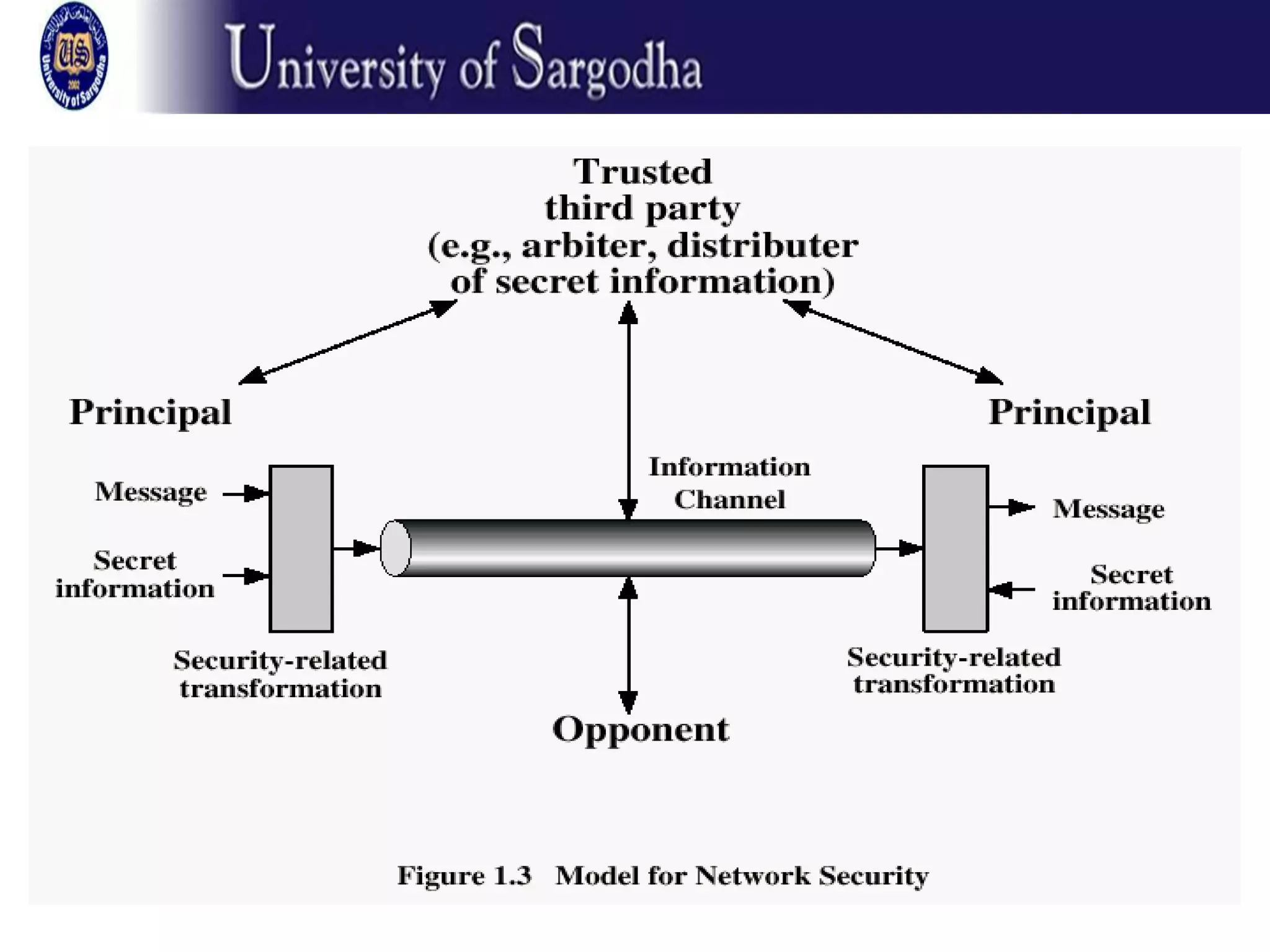
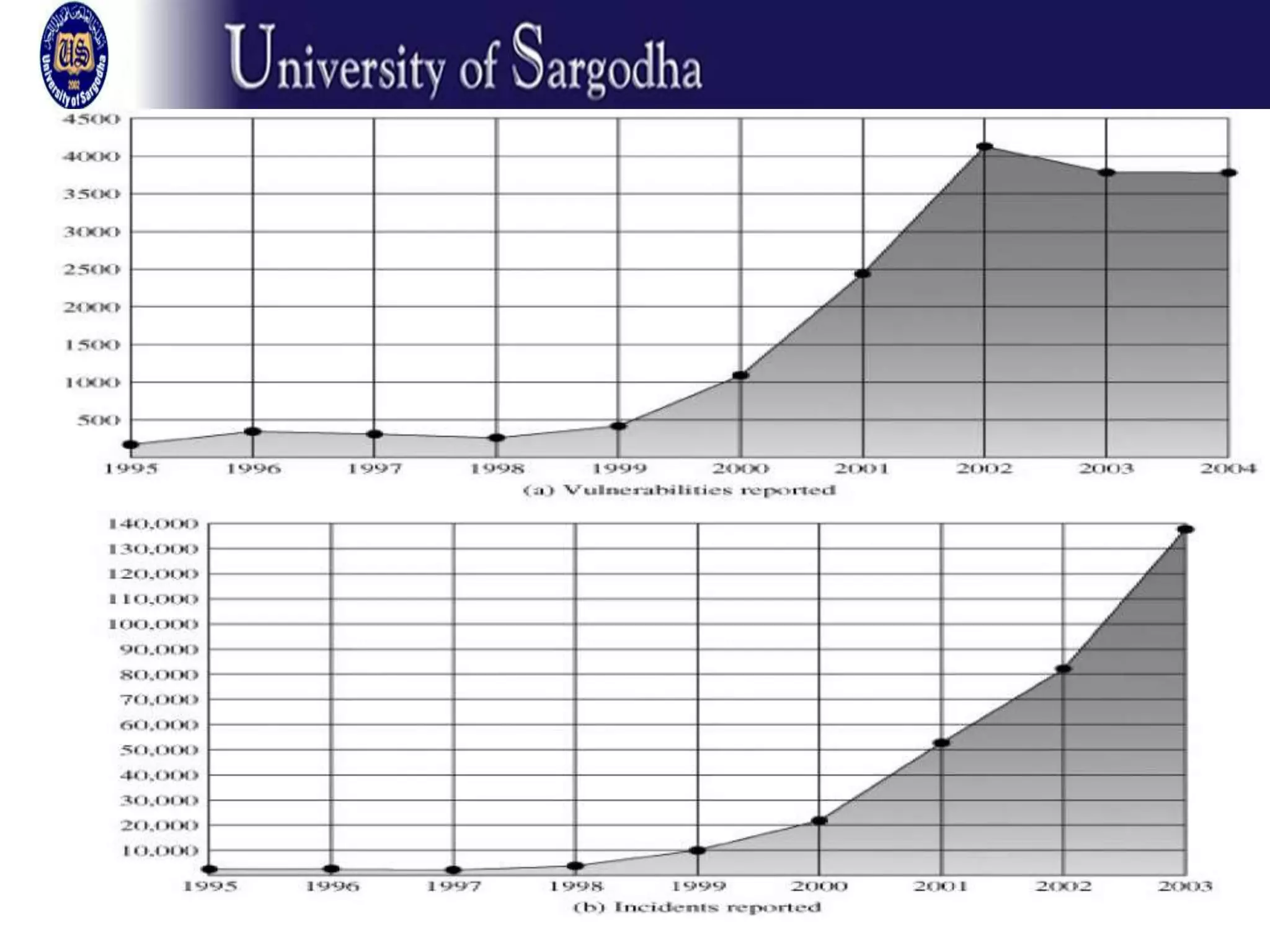
This document provides an overview of network security. It discusses security attacks like passive attacks (eavesdropping) and active attacks (modifying data). It outlines security services like confidentiality, authentication, integrity, non-repudiation, and access control. It also discusses methods of defense against attacks, including encryption, software/hardware controls, security policies, and physical controls. The document defines key security terms and concepts.


![3
Security?
• COMPUTER SECURITY
• The protection afforded to an automated
information system in order to attain the
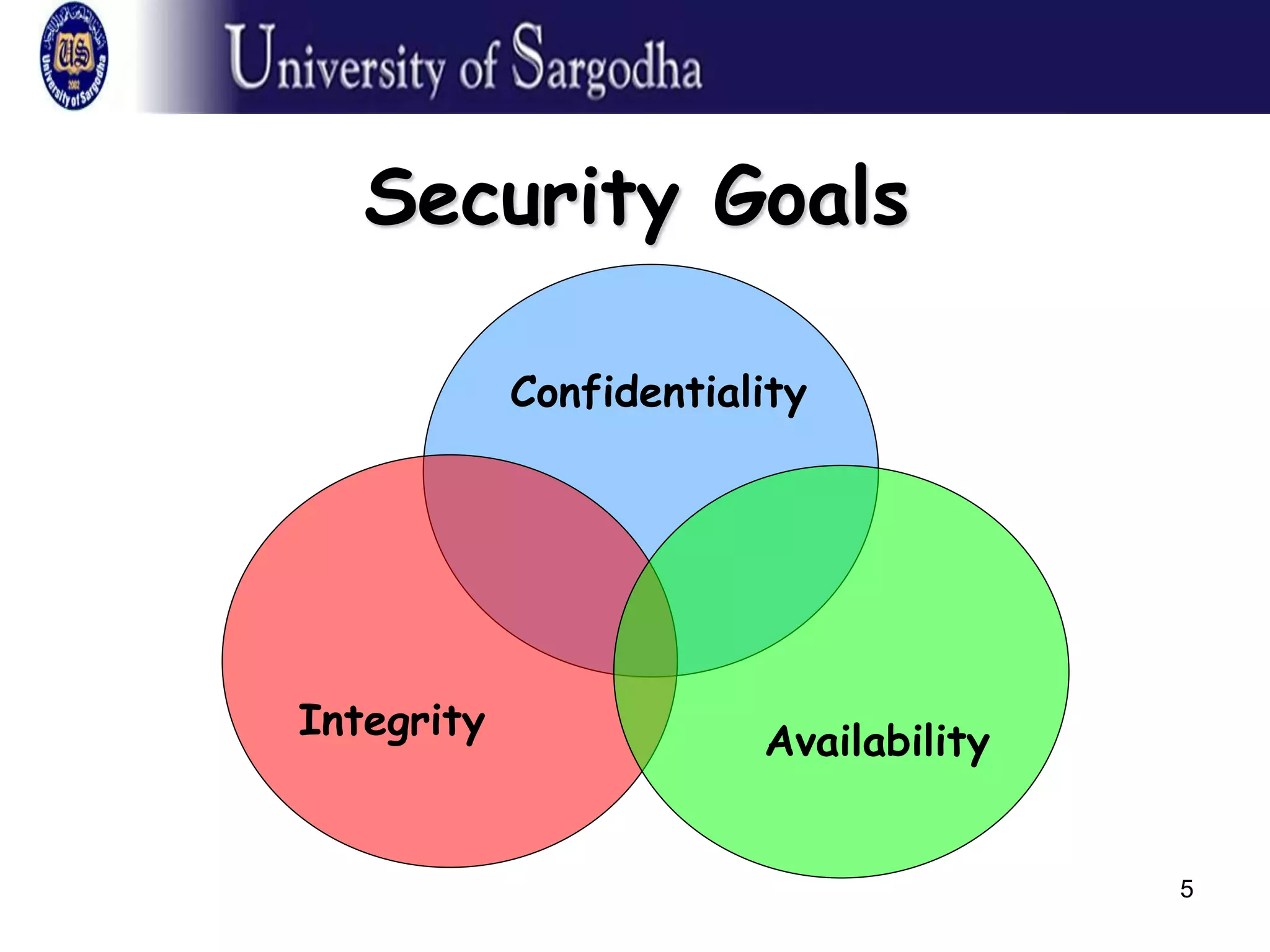
applicable objectives of preserving the integrity,
availability, and confidentiality of information
system resources (includes hardware, software,
firmware, information/ data, and
telecommunications).
(The NIST Computer Security Handbook [NIST95])](https://image.slidesharecdn.com/ns1-150126141452-conversion-gate02/75/Chapter-1-Overview-of-Network-Security-3-2048.jpg)