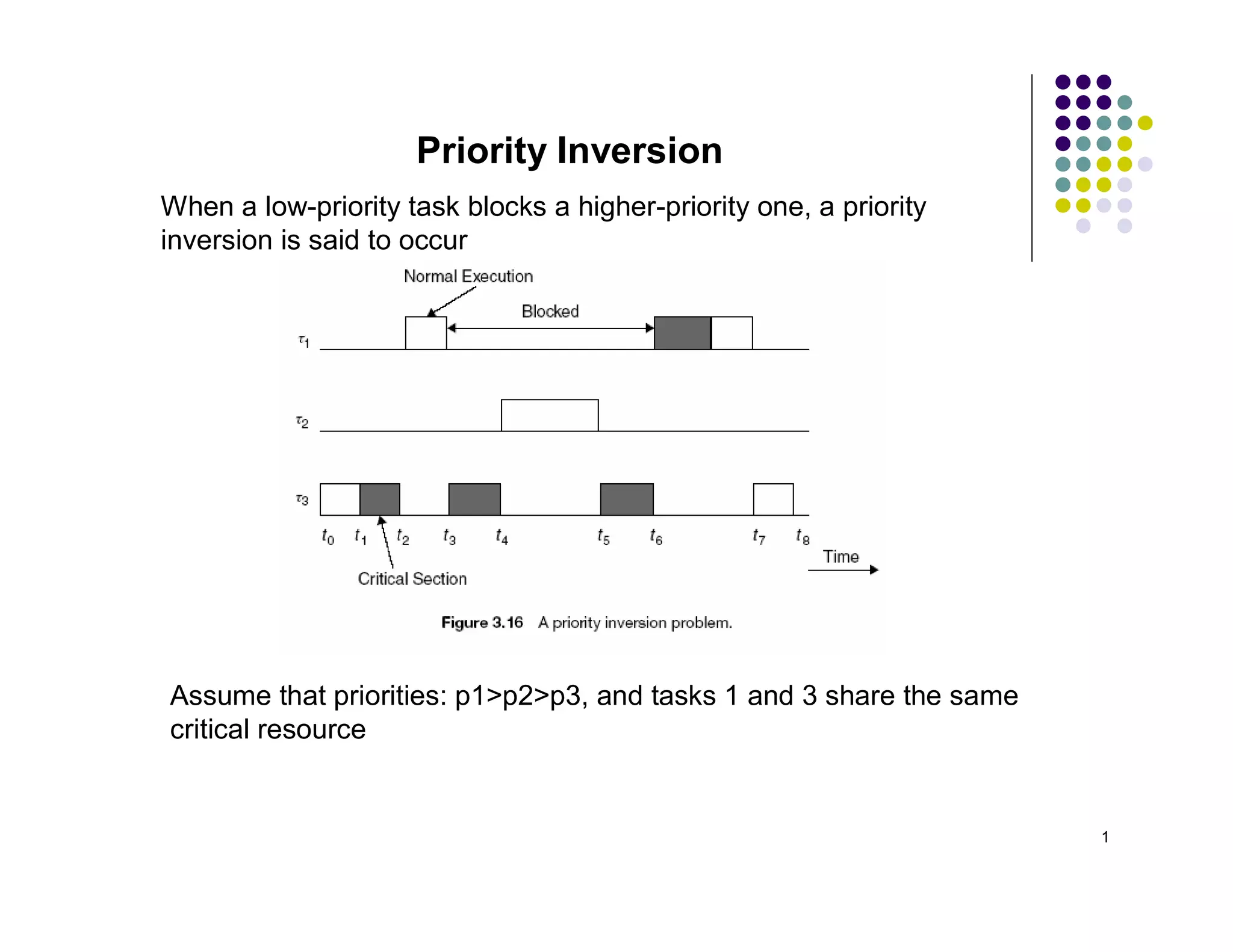
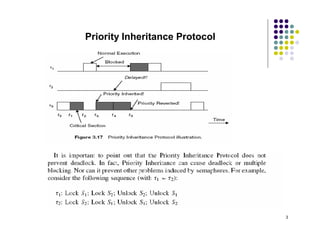
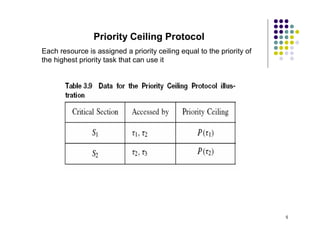
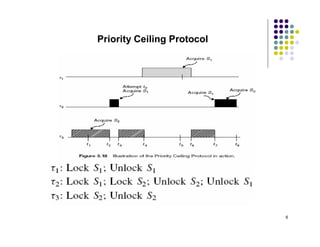
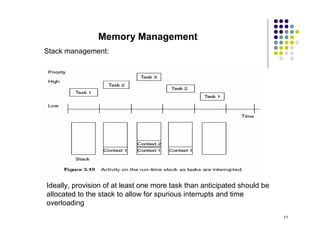
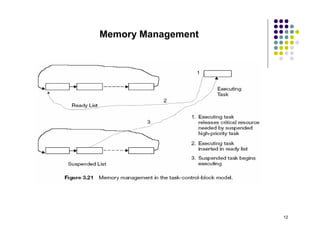
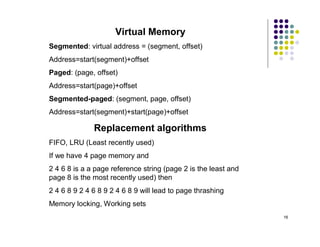
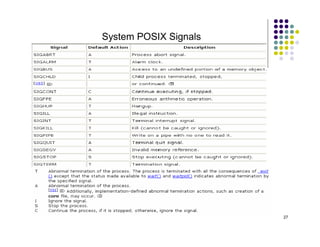
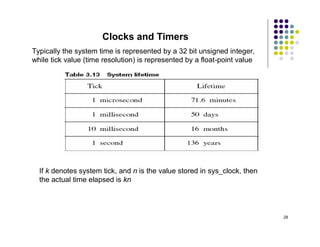
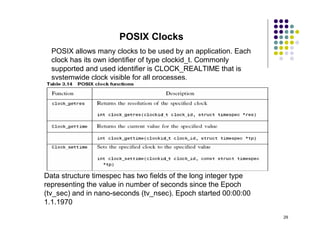
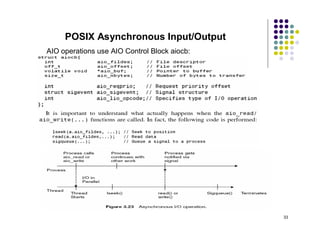
The document discusses several techniques for handling priority inversion in real-time operating systems:
1) The Priority Inheritance Protocol dynamically changes the priority of any task in a critical section to the priority of the highest task pending on the same critical resource.
2) The Priority Ceiling Protocol assigns each resource a priority ceiling equal to the priority of the highest priority task that can use it.
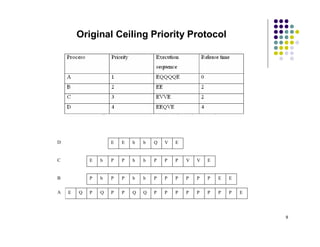
3) The Original Ceiling Priority Protocol assigns static default priorities and ceiling values to processes and resources, with processes able to lock resources only if their dynamic priority is higher than the ceiling.