This document summarizes key topics from a lecture on security engineering:
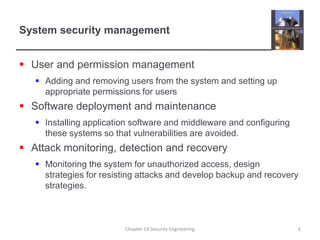
1. It discusses security engineering and management, risk assessment, and designing systems for security. Application security focuses on design while infrastructure security is a management problem.
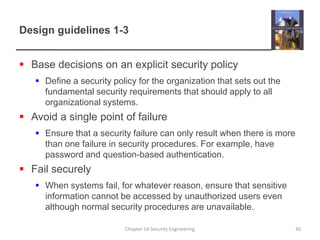
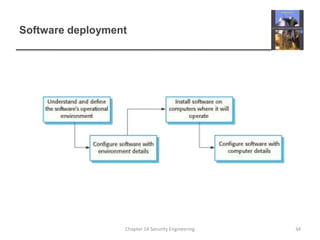
2. It outlines guidelines for secure system design including basing decisions on security policies, avoiding single points of failure, balancing security and usability, validating all inputs, and designing for deployment and recoverability.
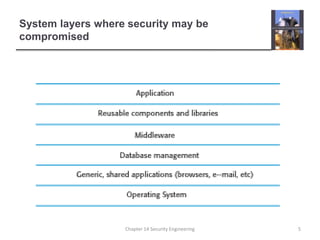
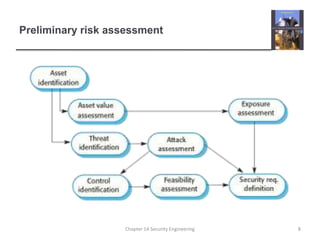
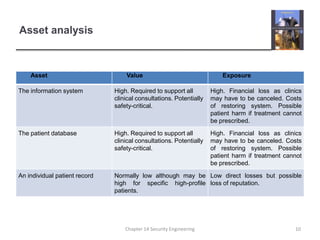
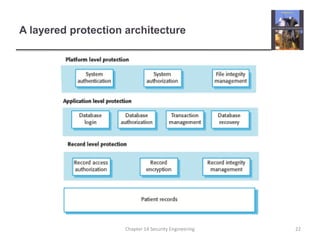
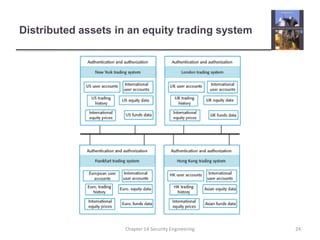
3. It also covers risk management, assessing threats, and designing architectures with layered protection and distributed assets to minimize the effects of attacks.