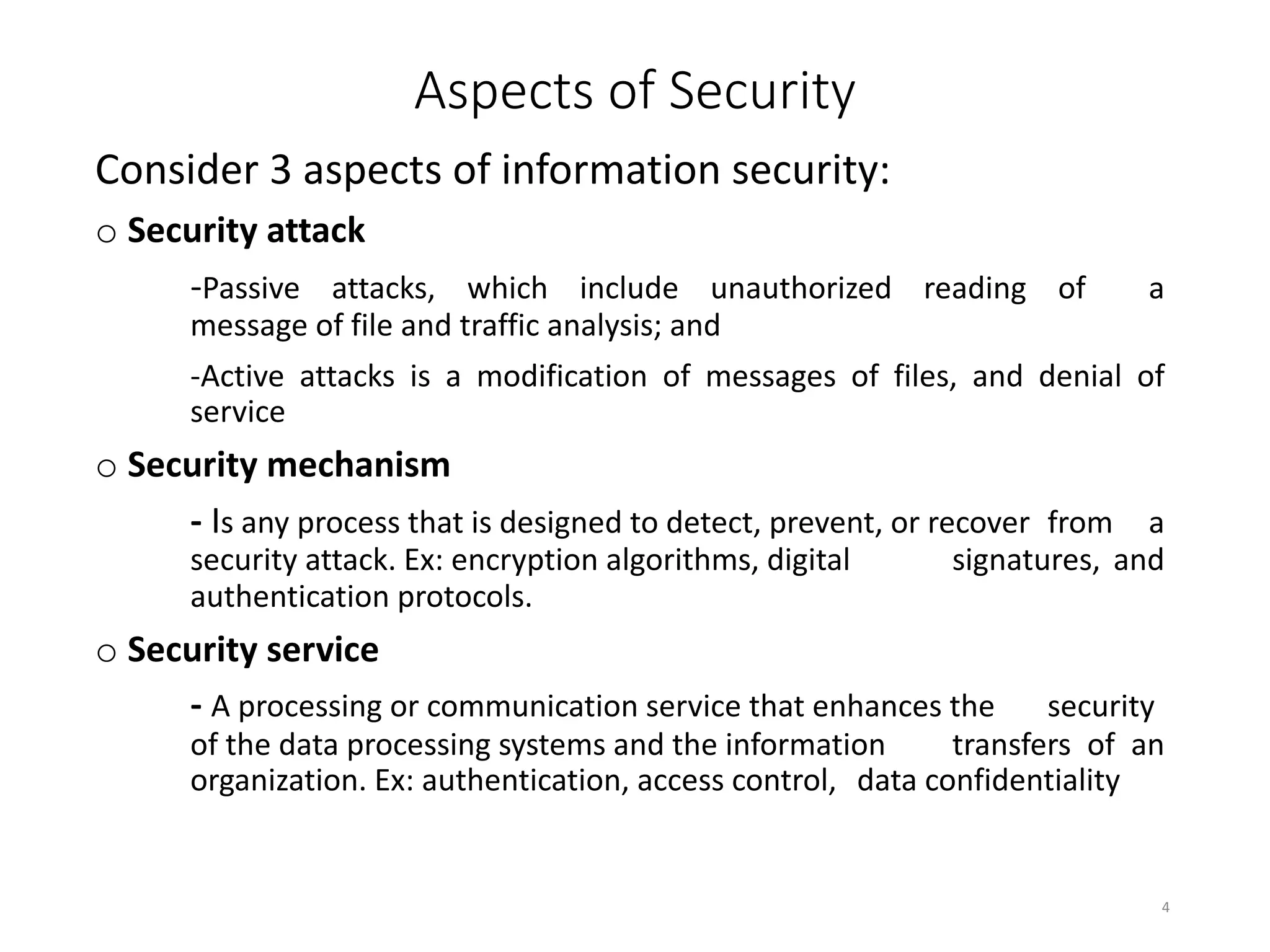
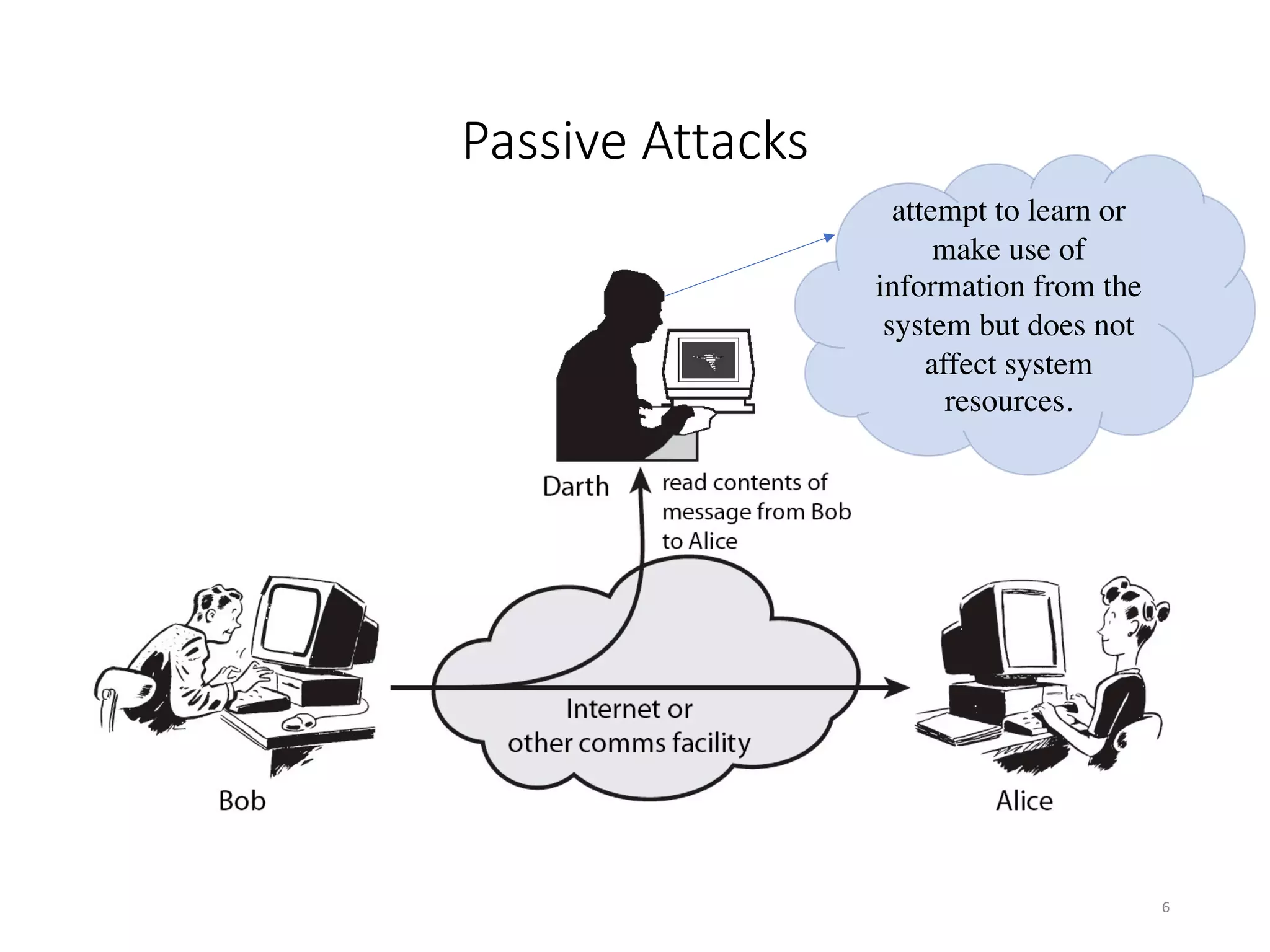
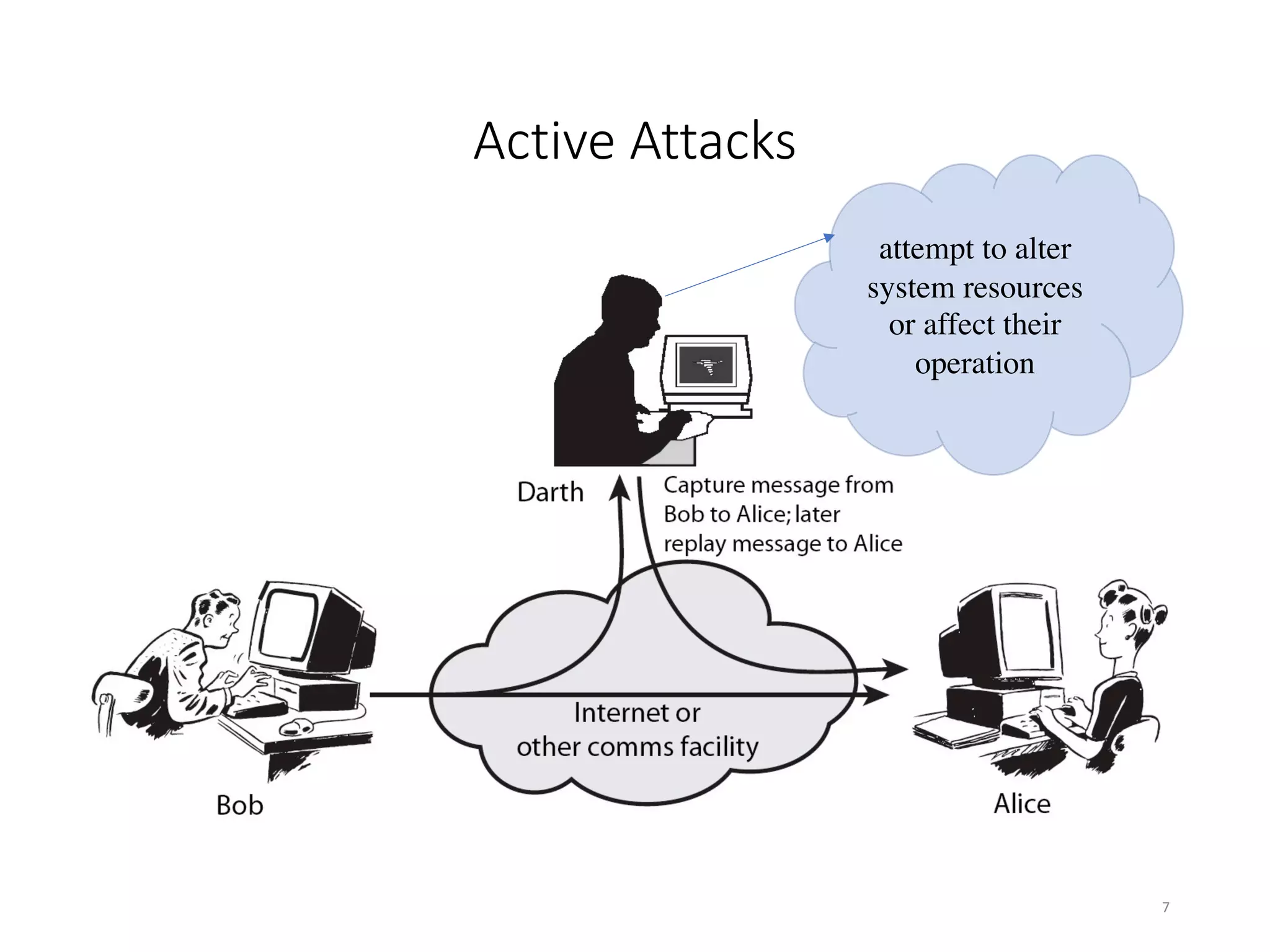
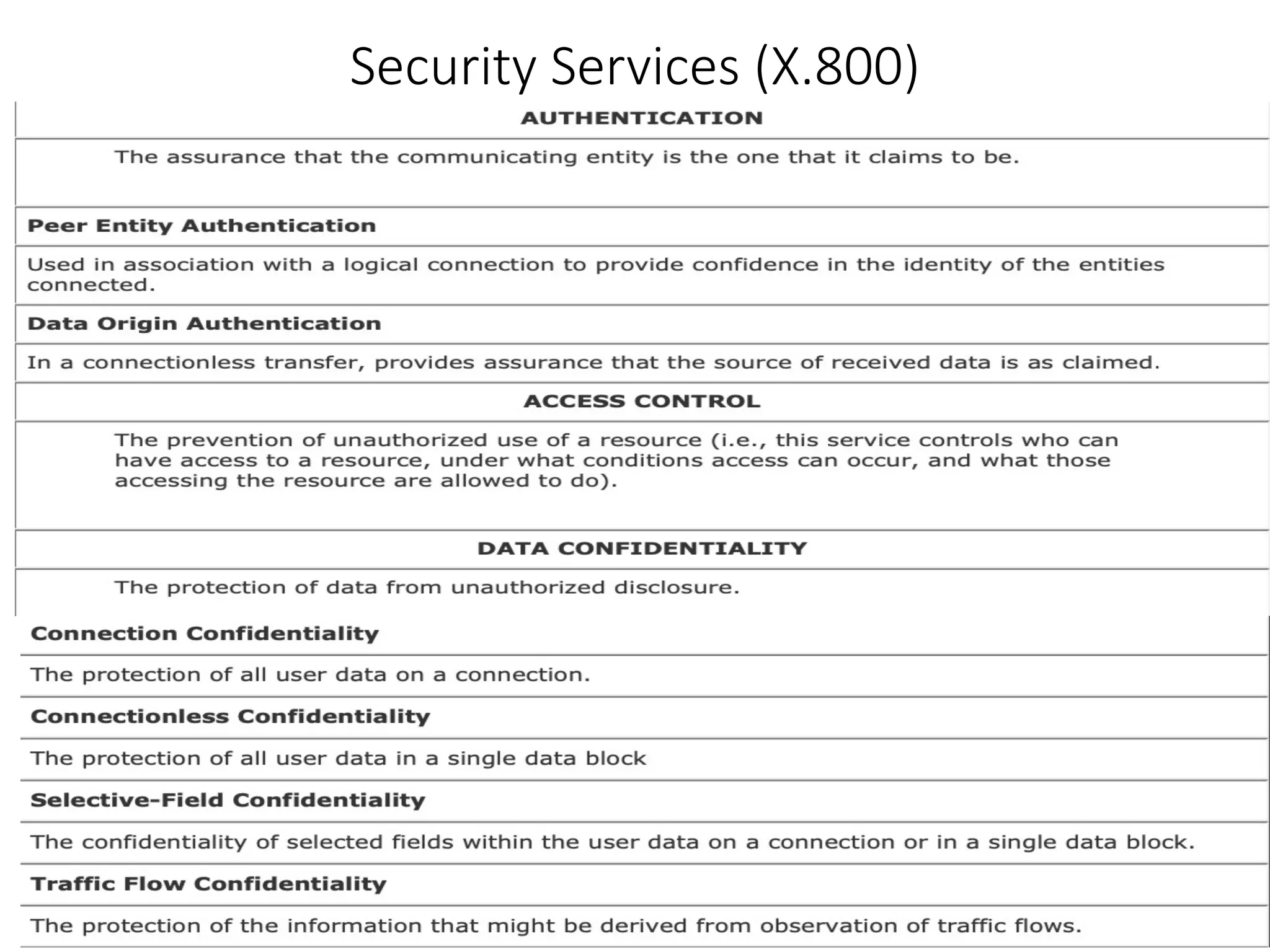
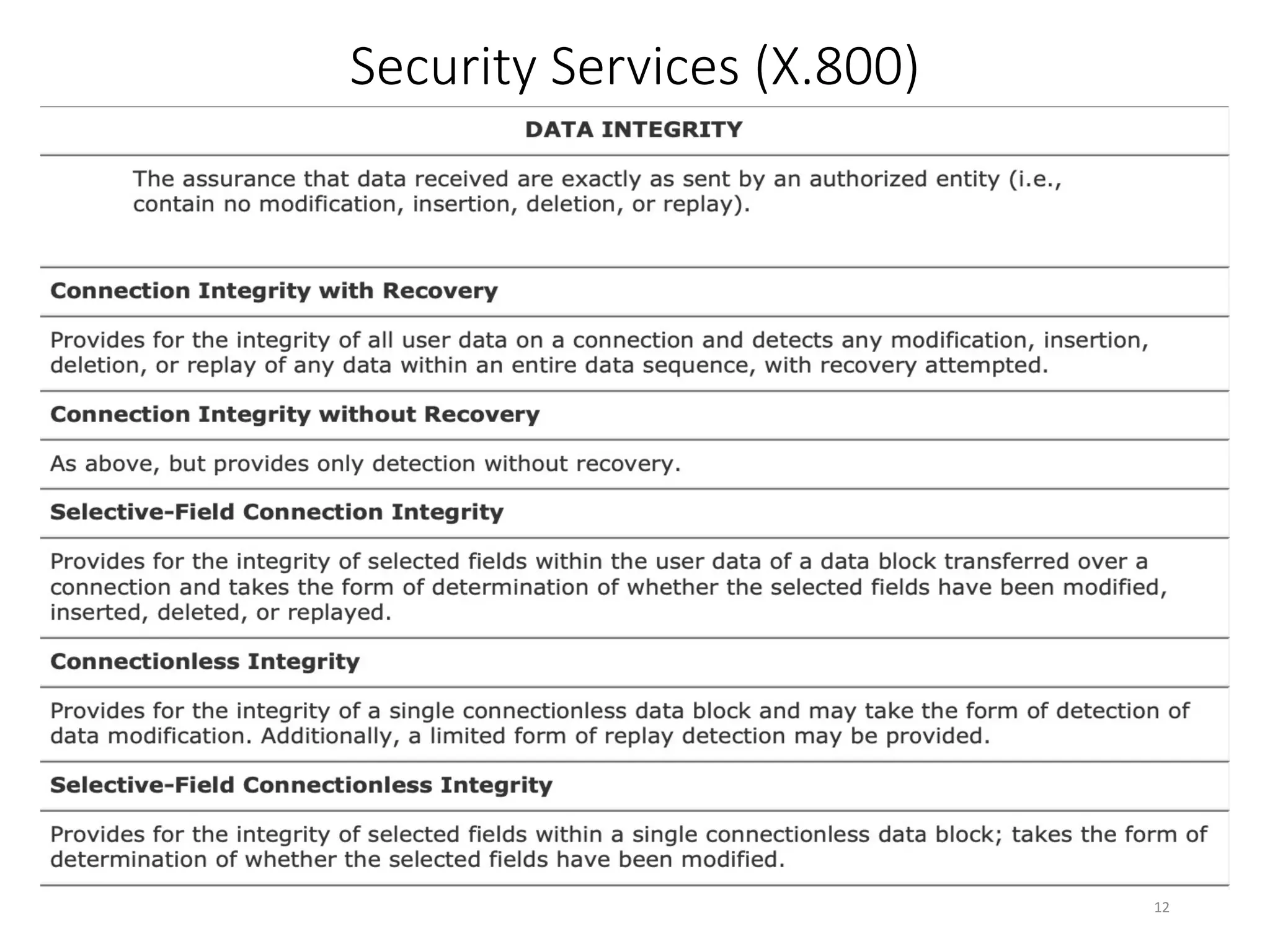
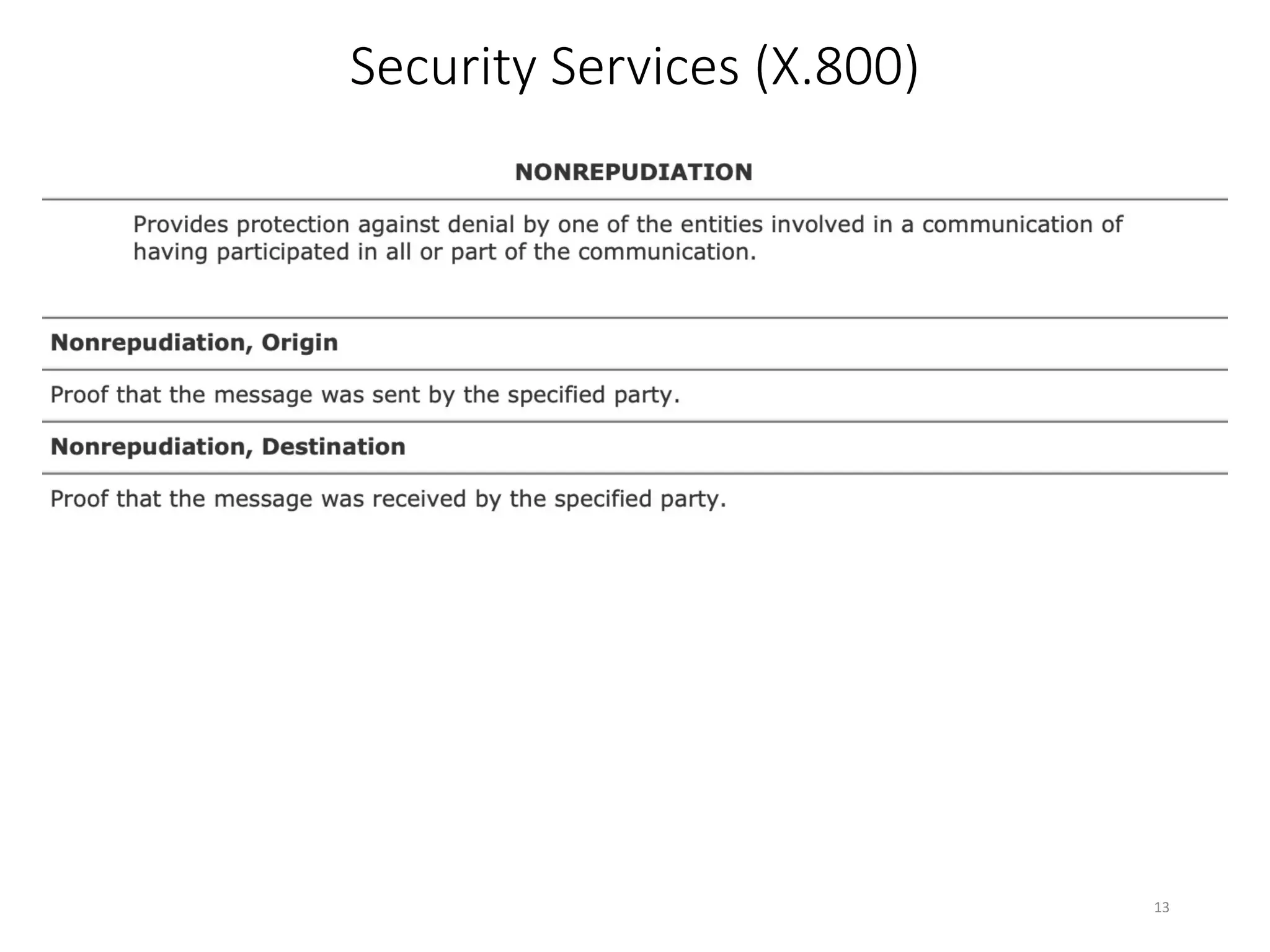
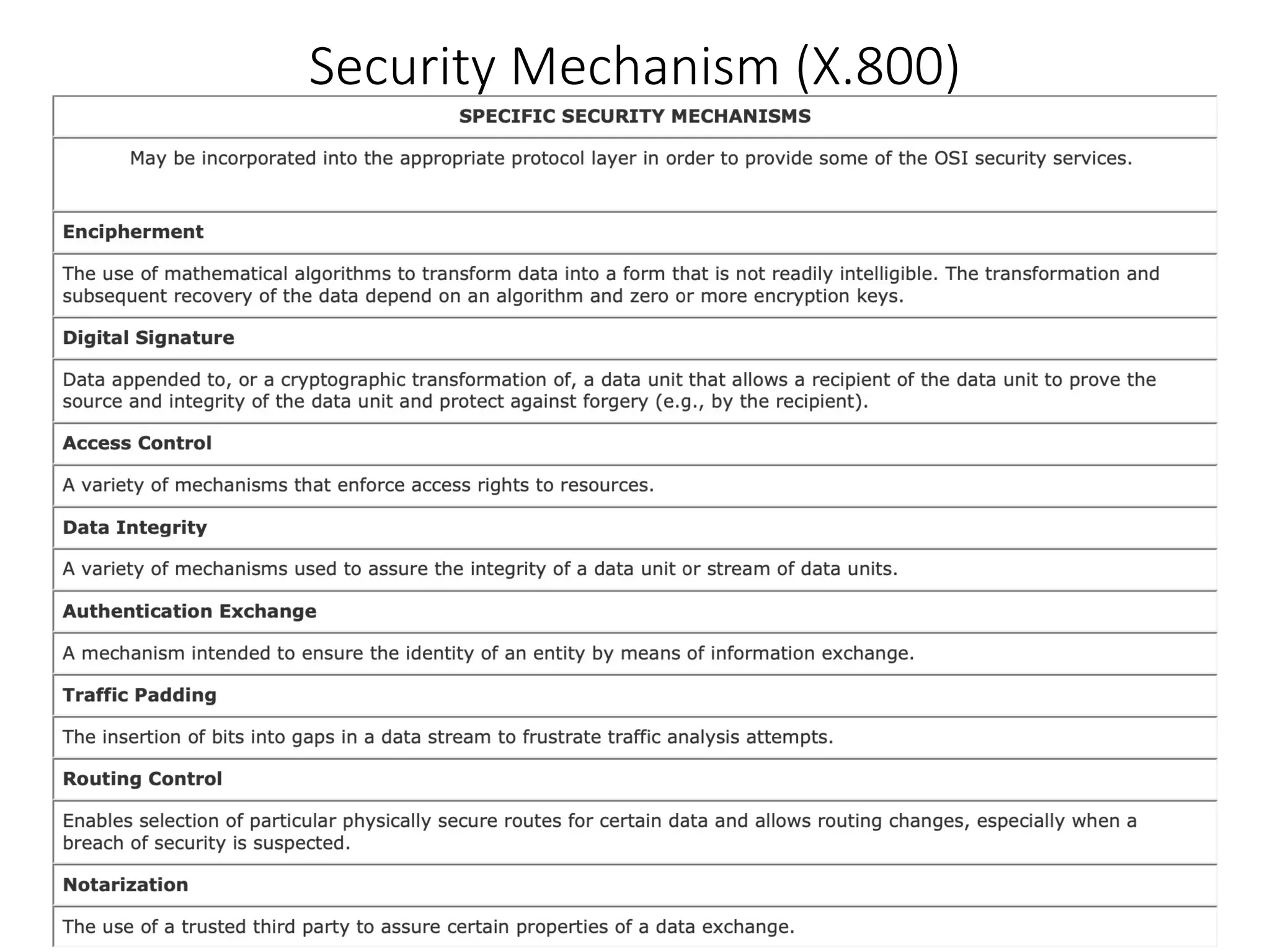
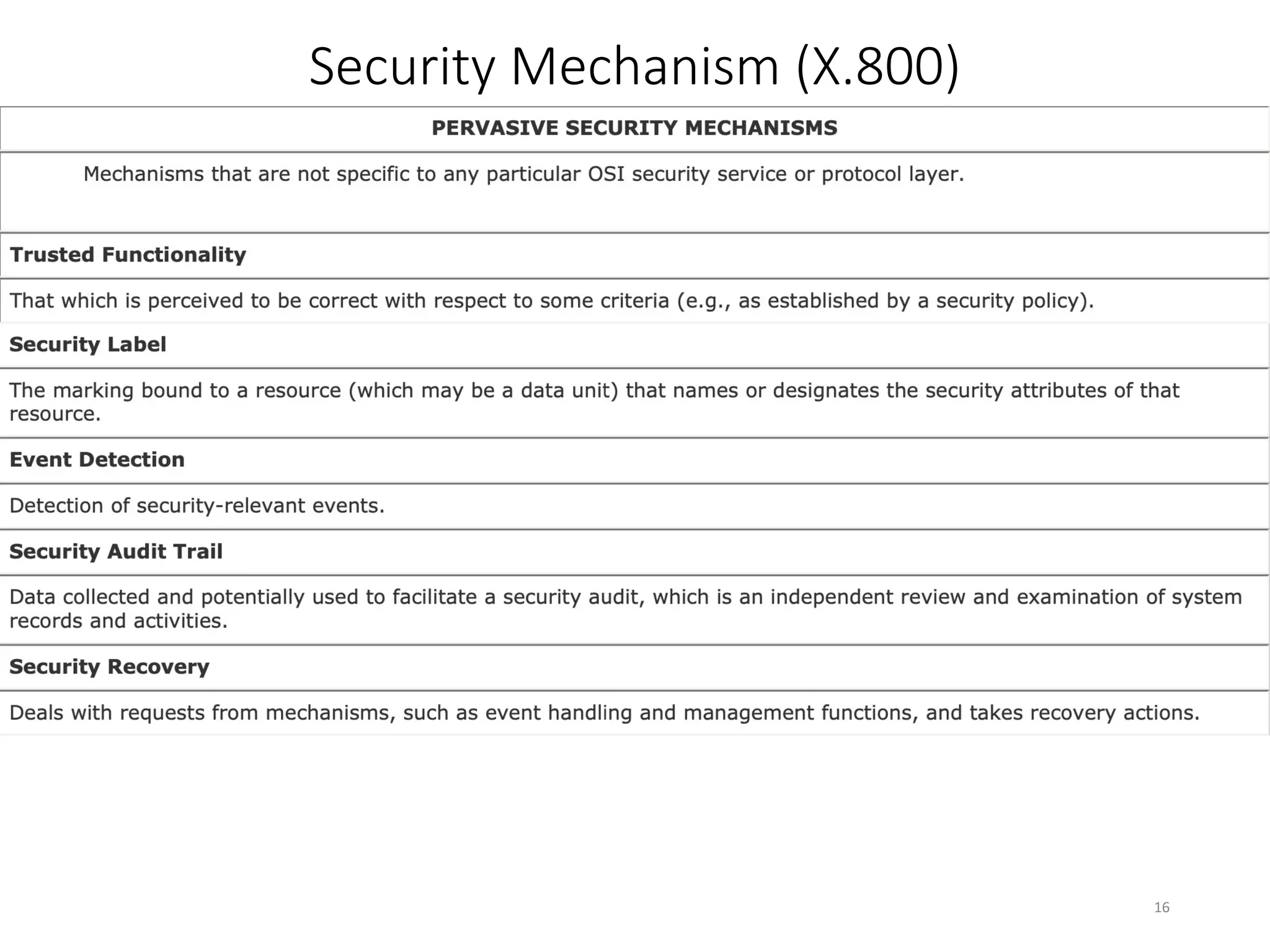
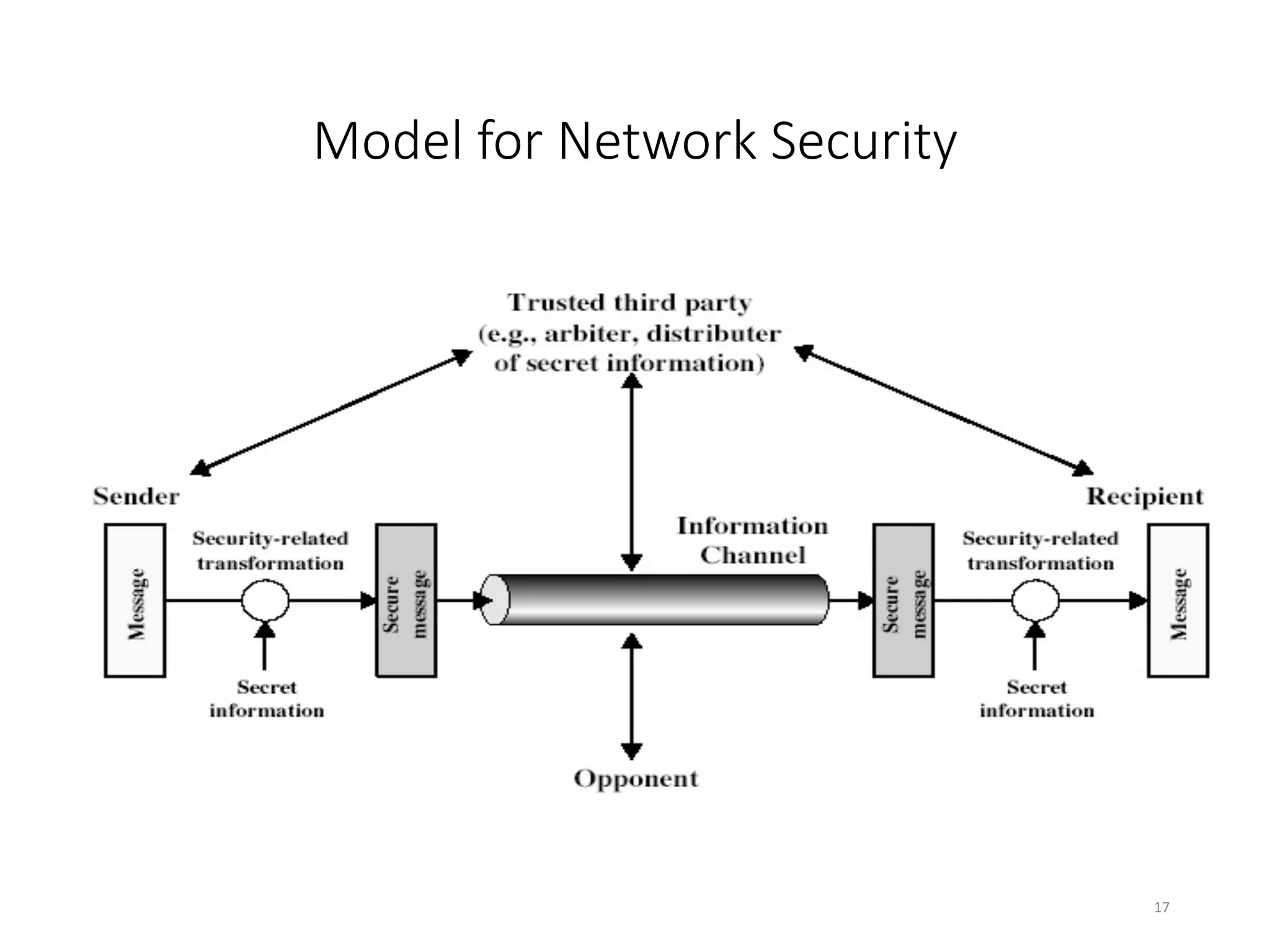
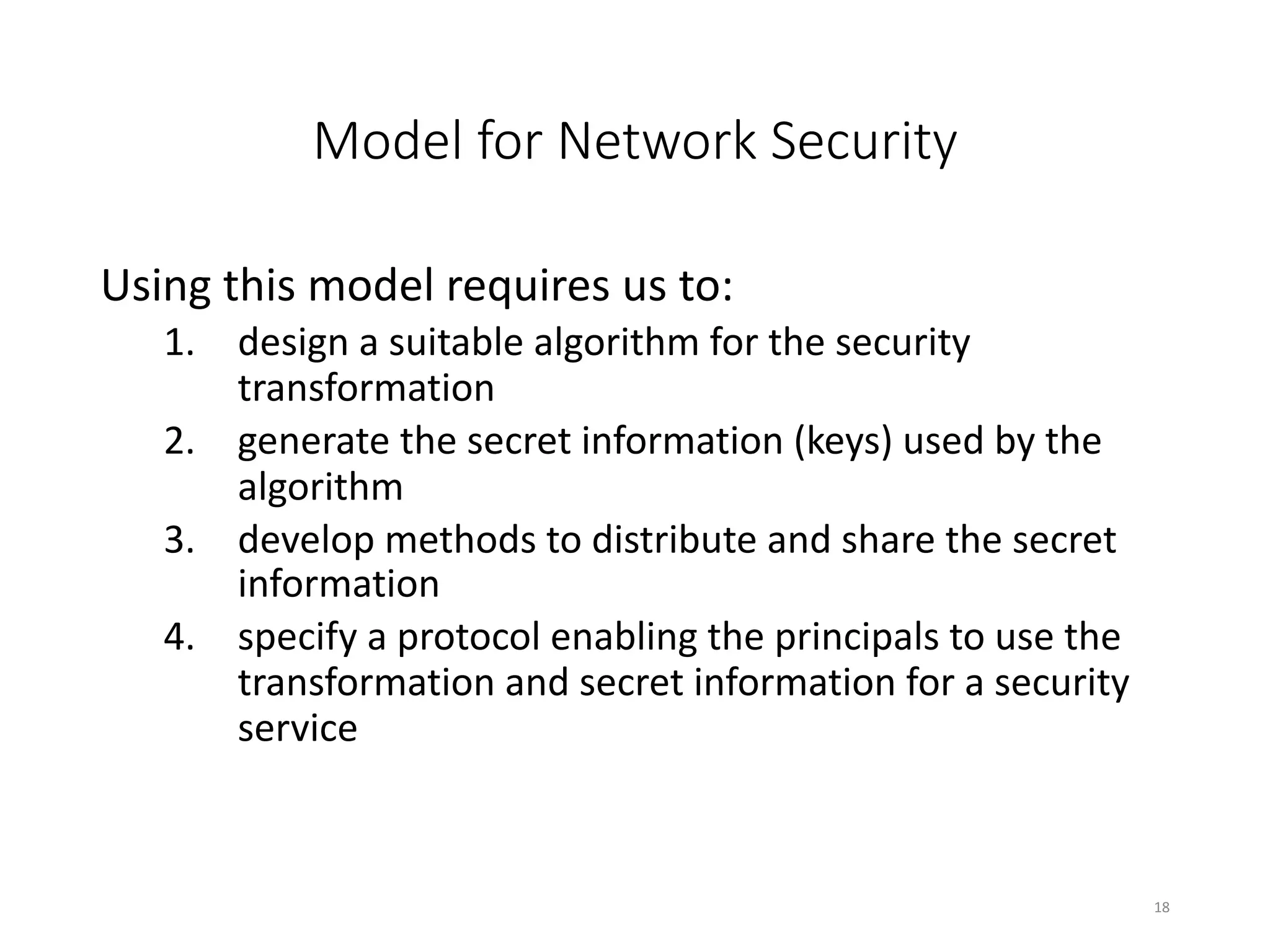
This document discusses cryptography and network security. It defines key terms like computer security, network security, and internet security. It outlines three aspects of information security: security attacks, security mechanisms, and security services. Security attacks can be passive like unauthorized reading or active like modifying messages. Security mechanisms detect, prevent, or recover from attacks using things like encryption and authentication. Security services provided by protocols include authentication, access control, confidentiality, integrity, and non-repudiation. The document presents models for providing network security and implementing security services.