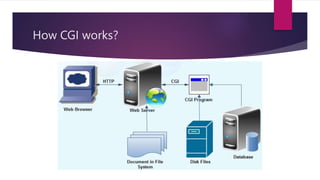
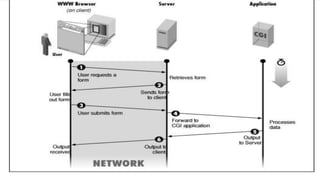
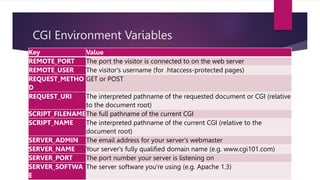
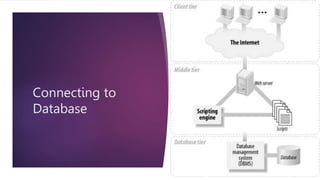
The document discusses Common Gateway Interface (CGI) which enables web browsers to submit forms and connect to programs on a web server. It describes how CGI works and its features such as being a well-defined standard that allows scripts to be written in languages like Perl and C. Advantages are listed like ease of performing advanced tasks while disadvantages include overhead from loading programs for each page load. The document also covers CGI environment variables, connecting to databases, server-side security issues, cyber attacks, safe security practices, and email security.