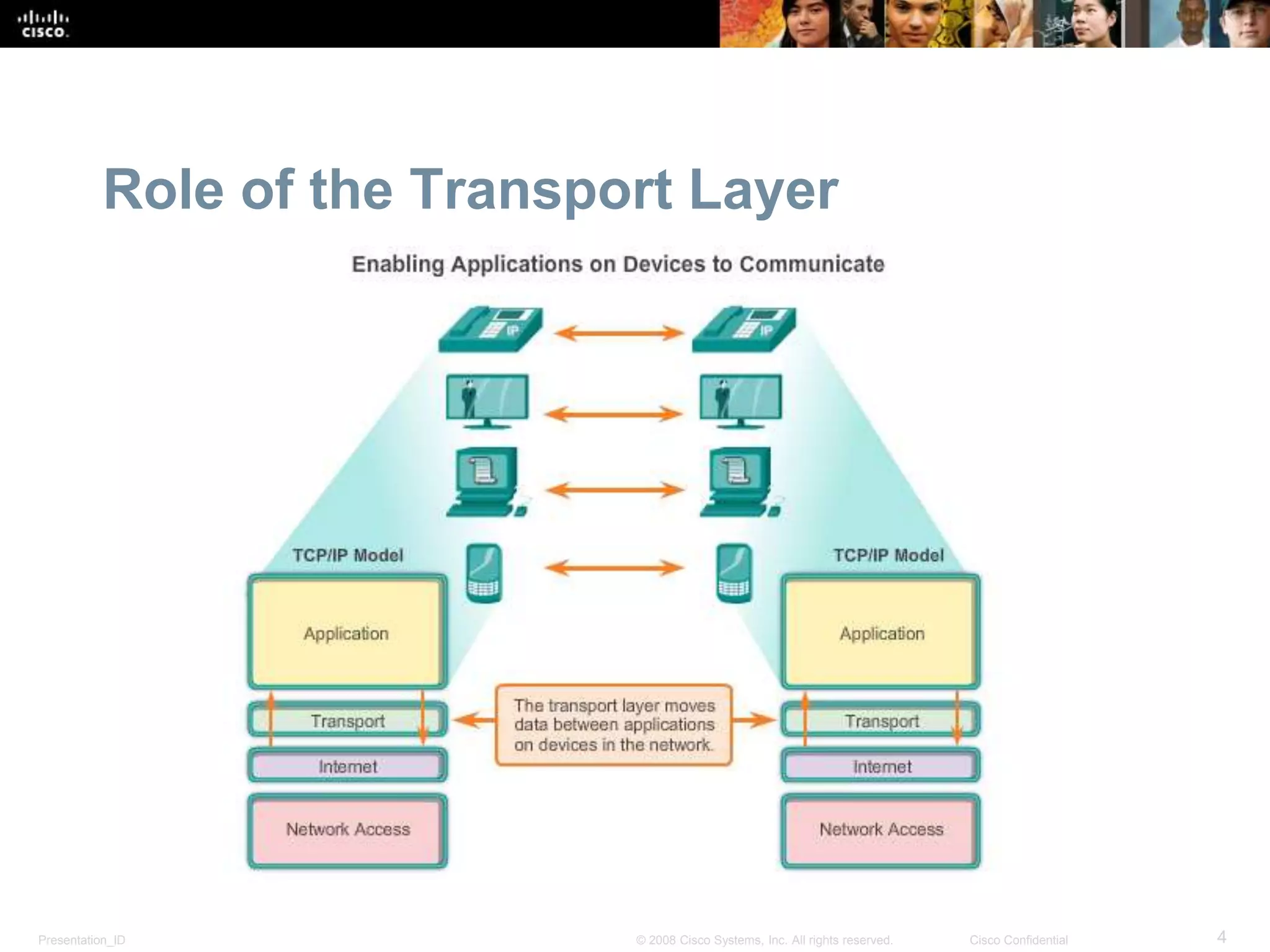
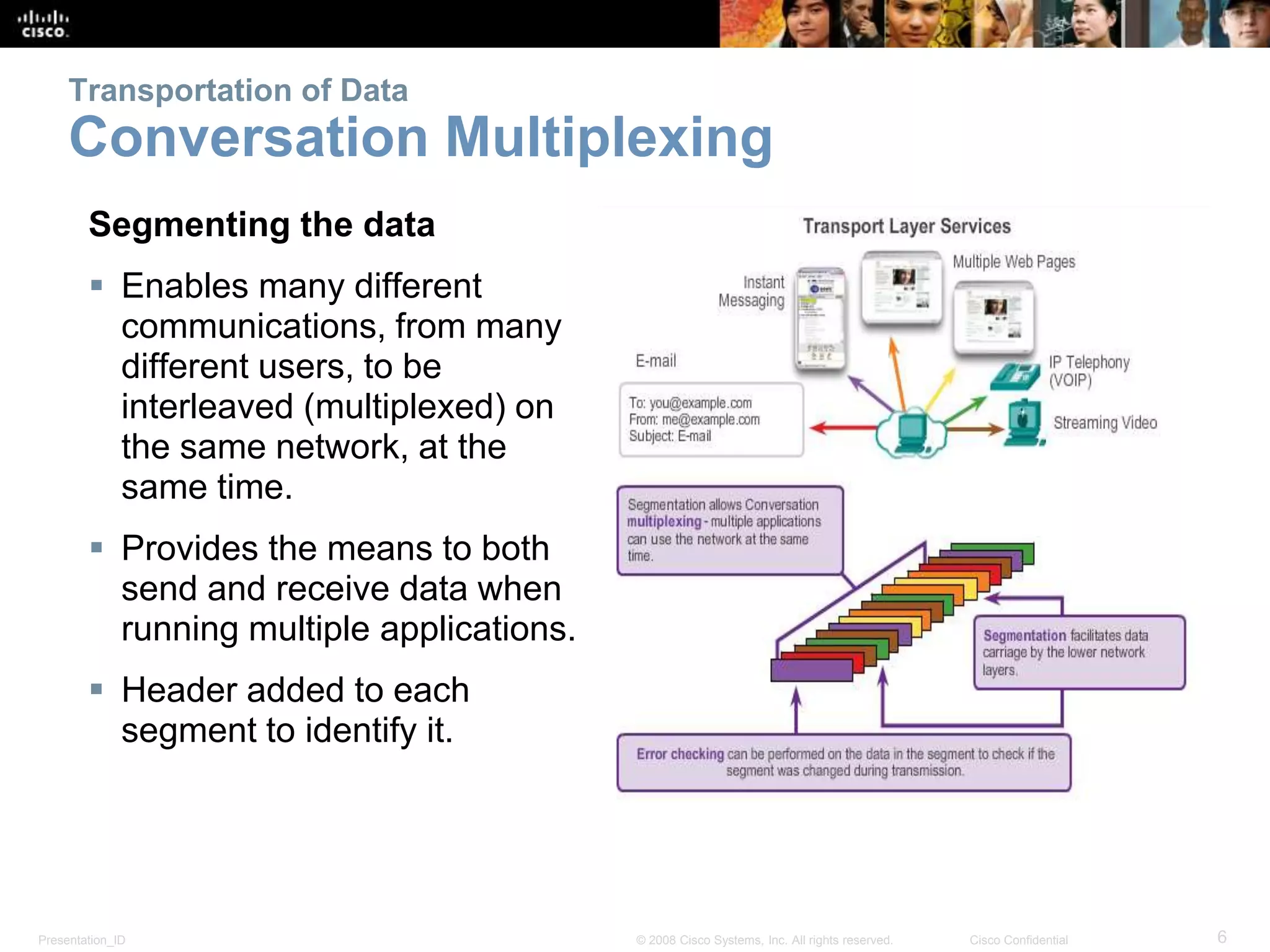
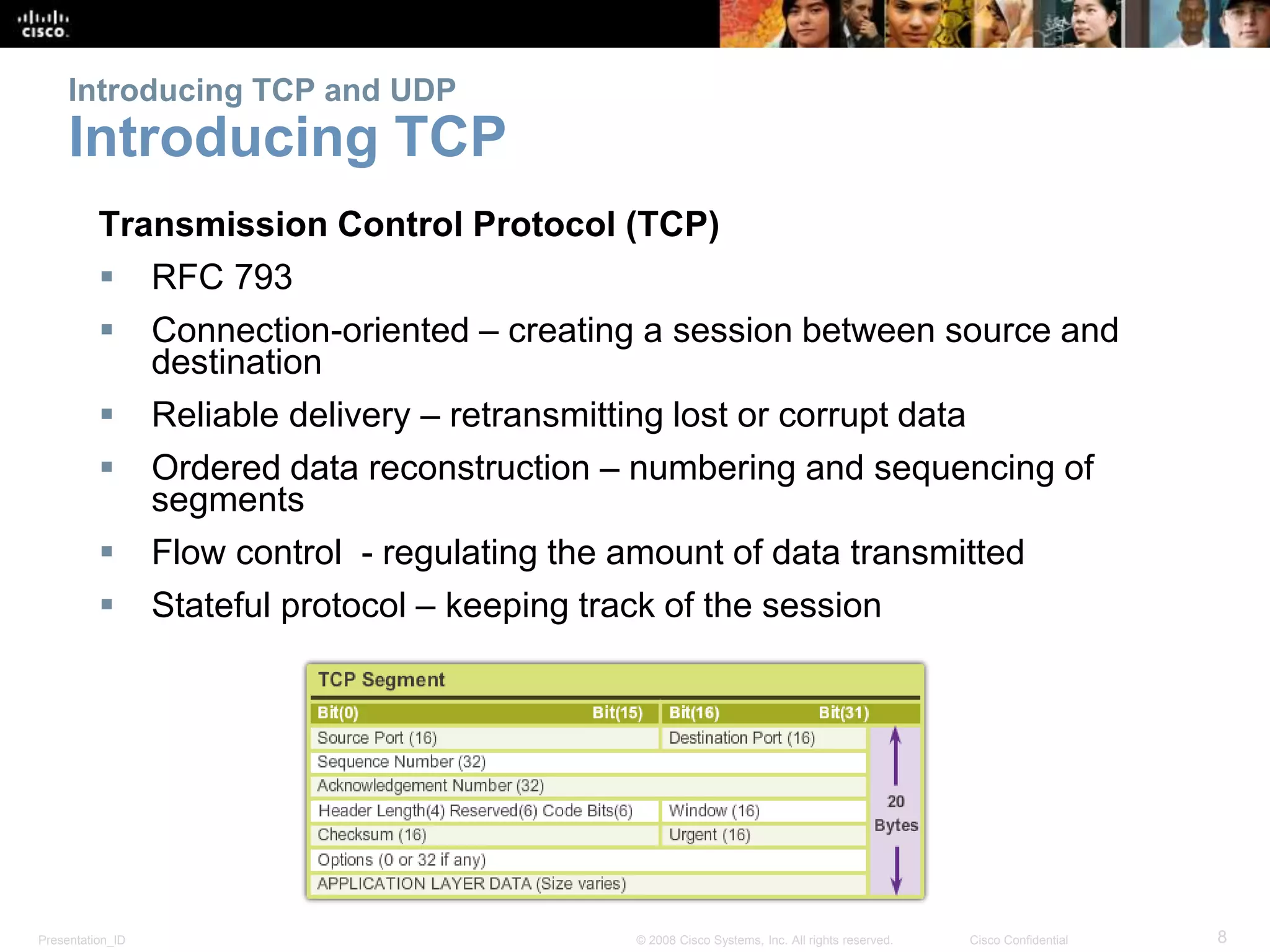
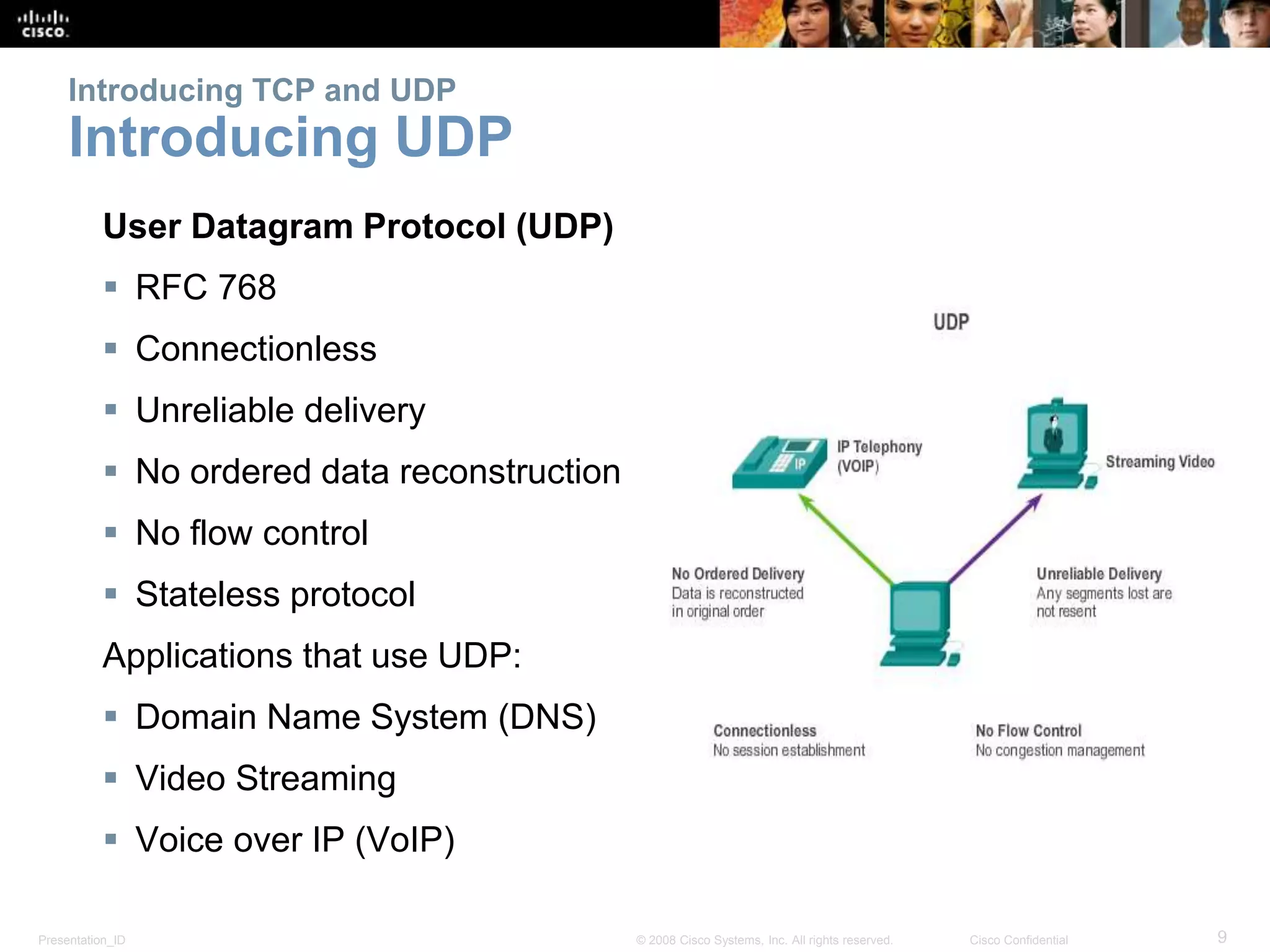
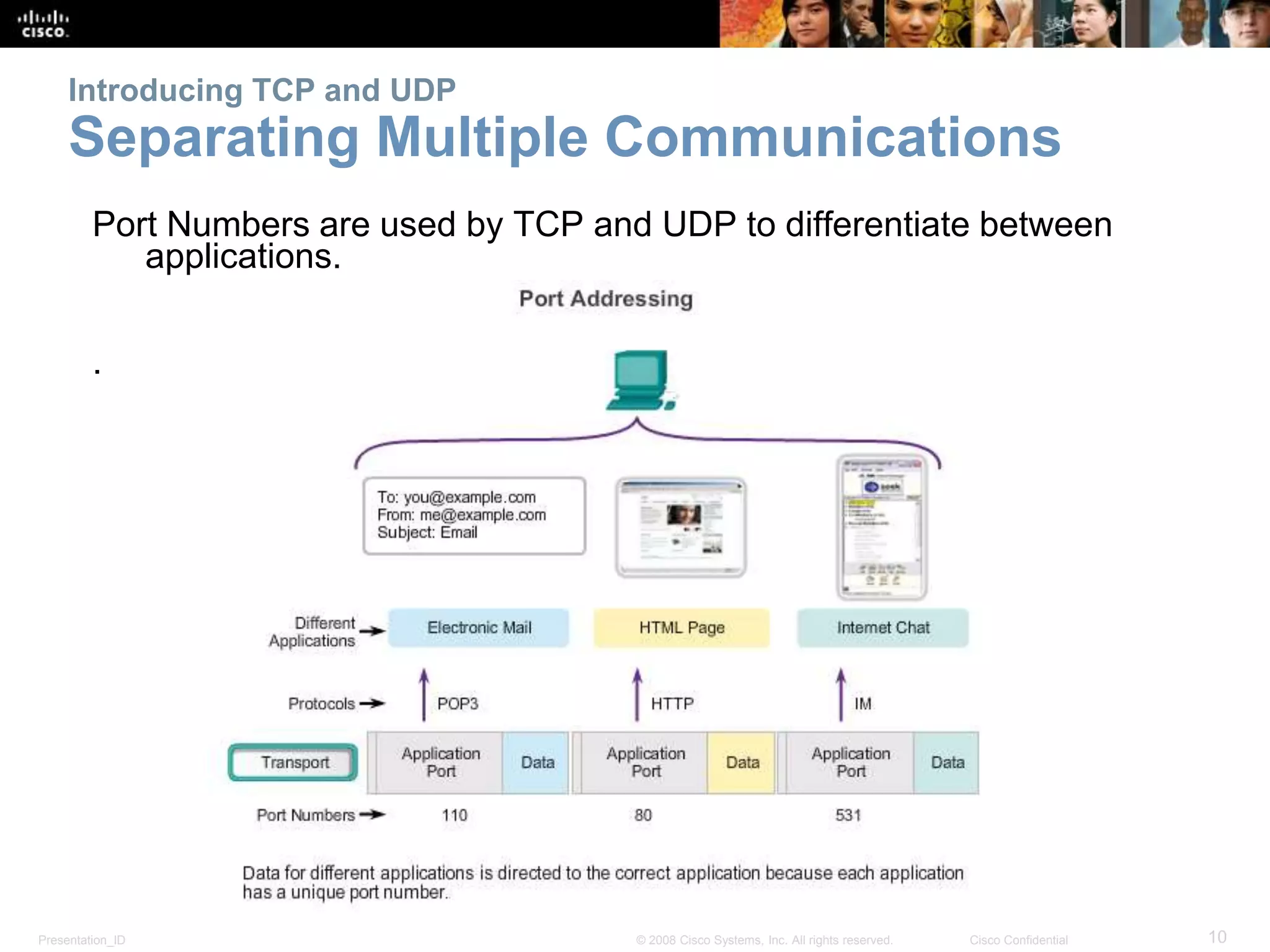
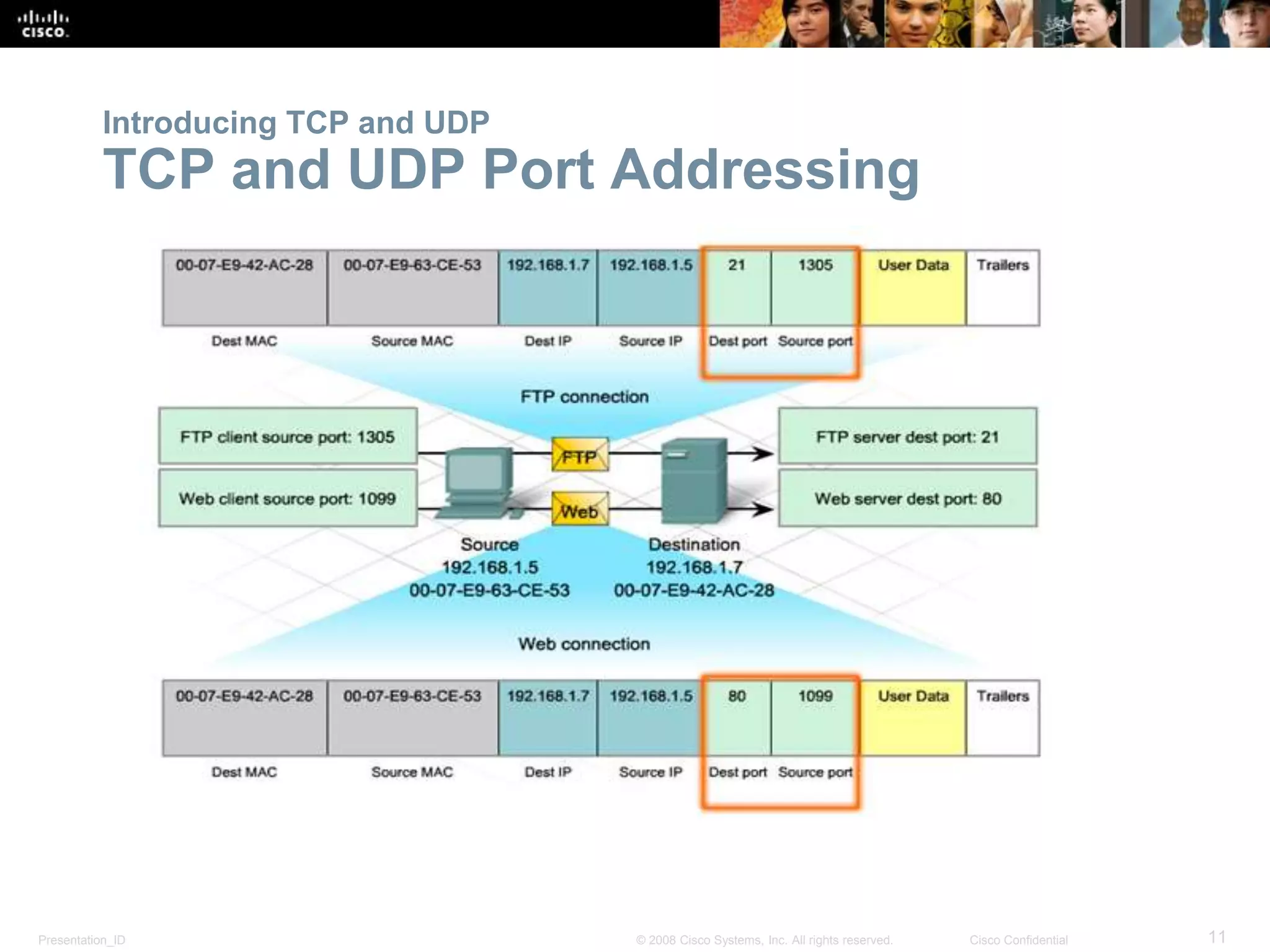
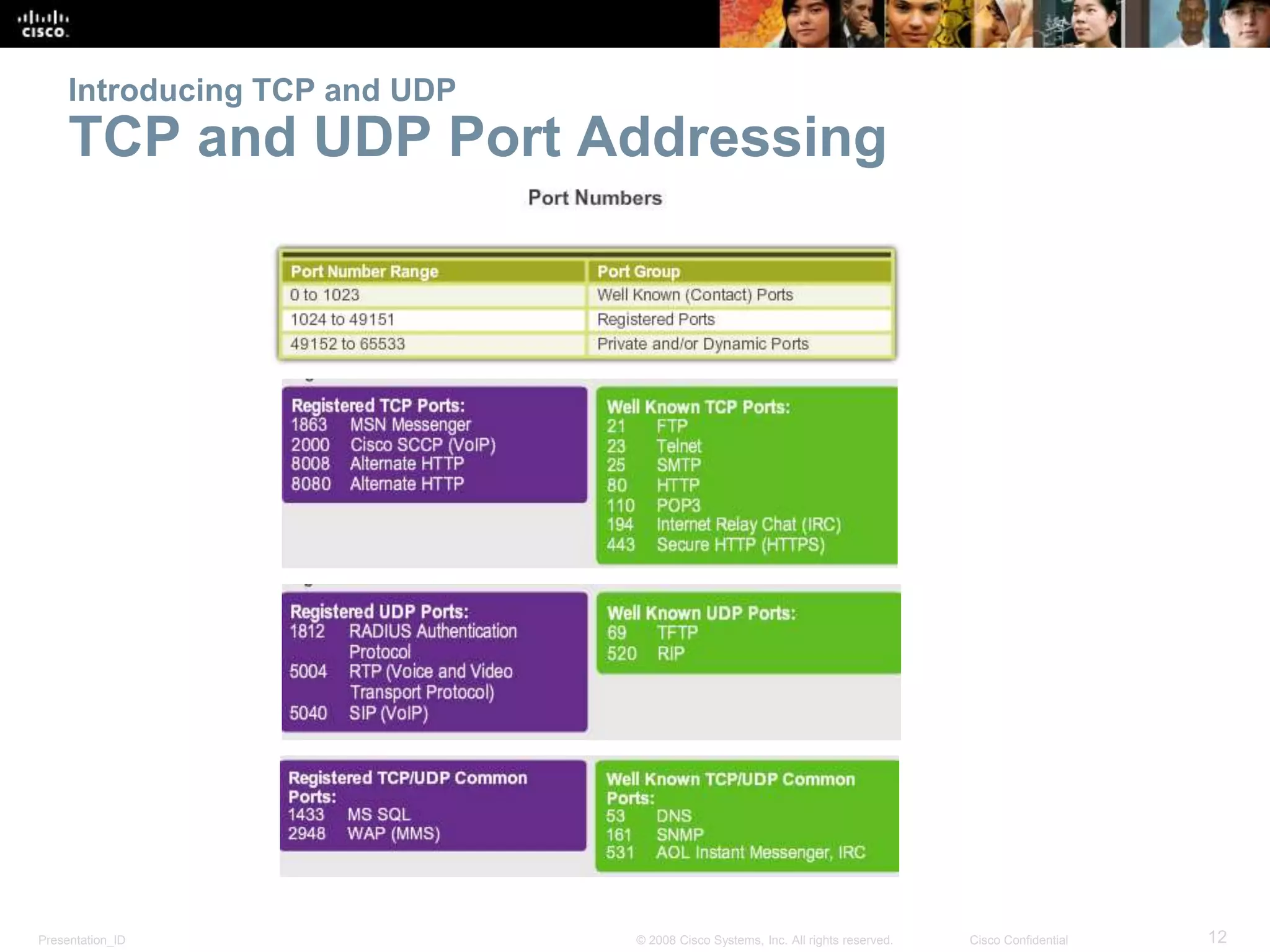
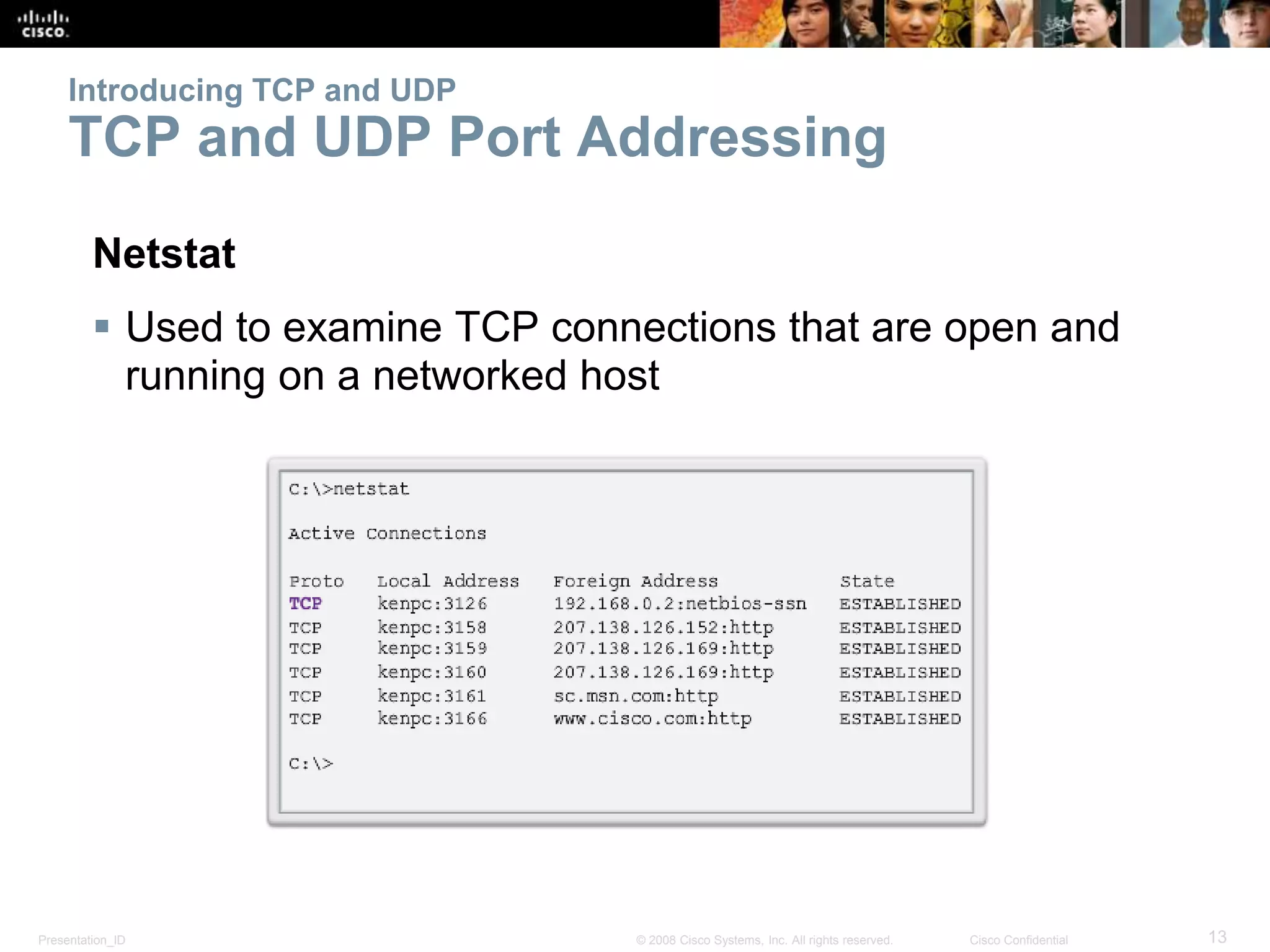
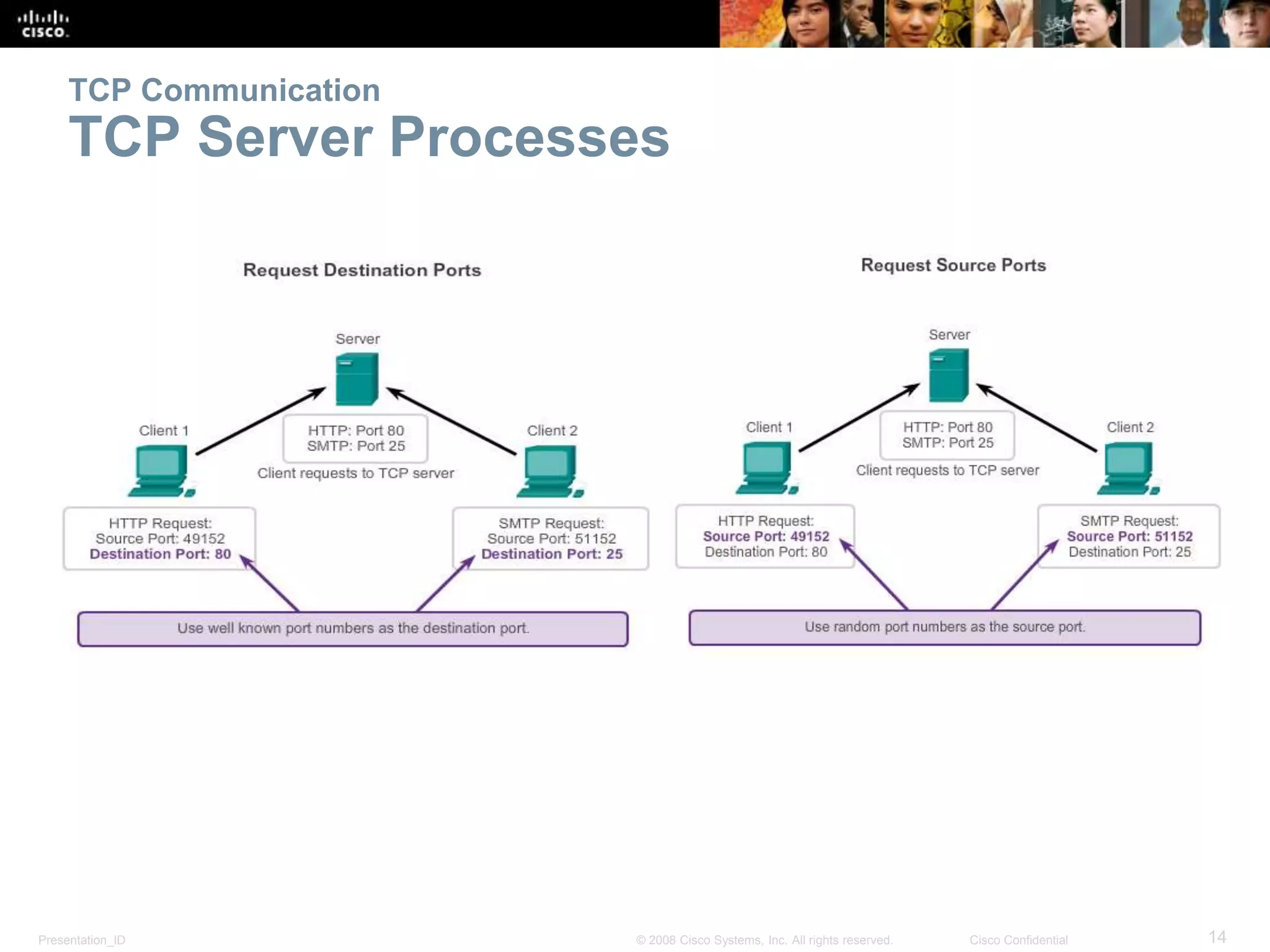
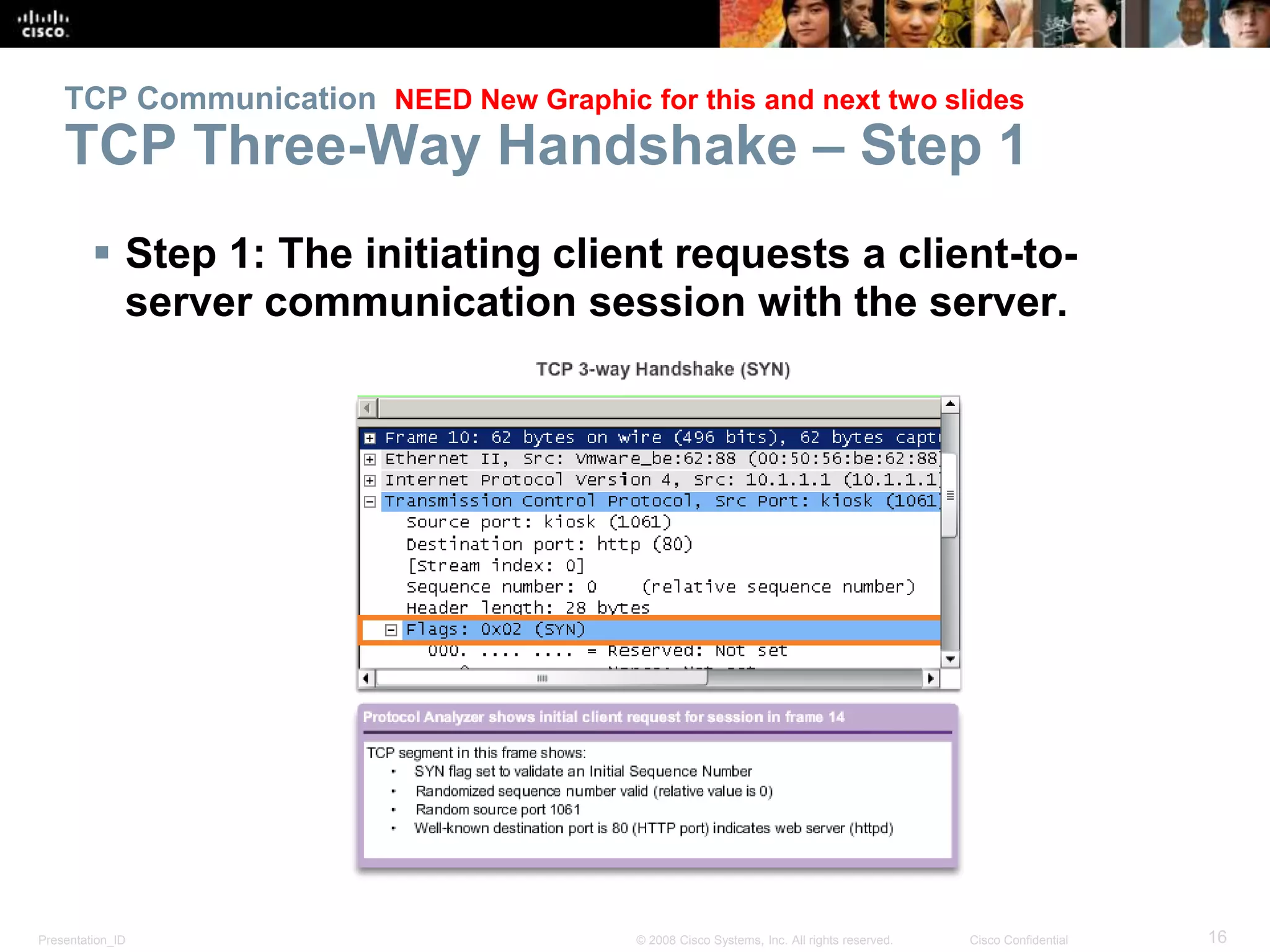
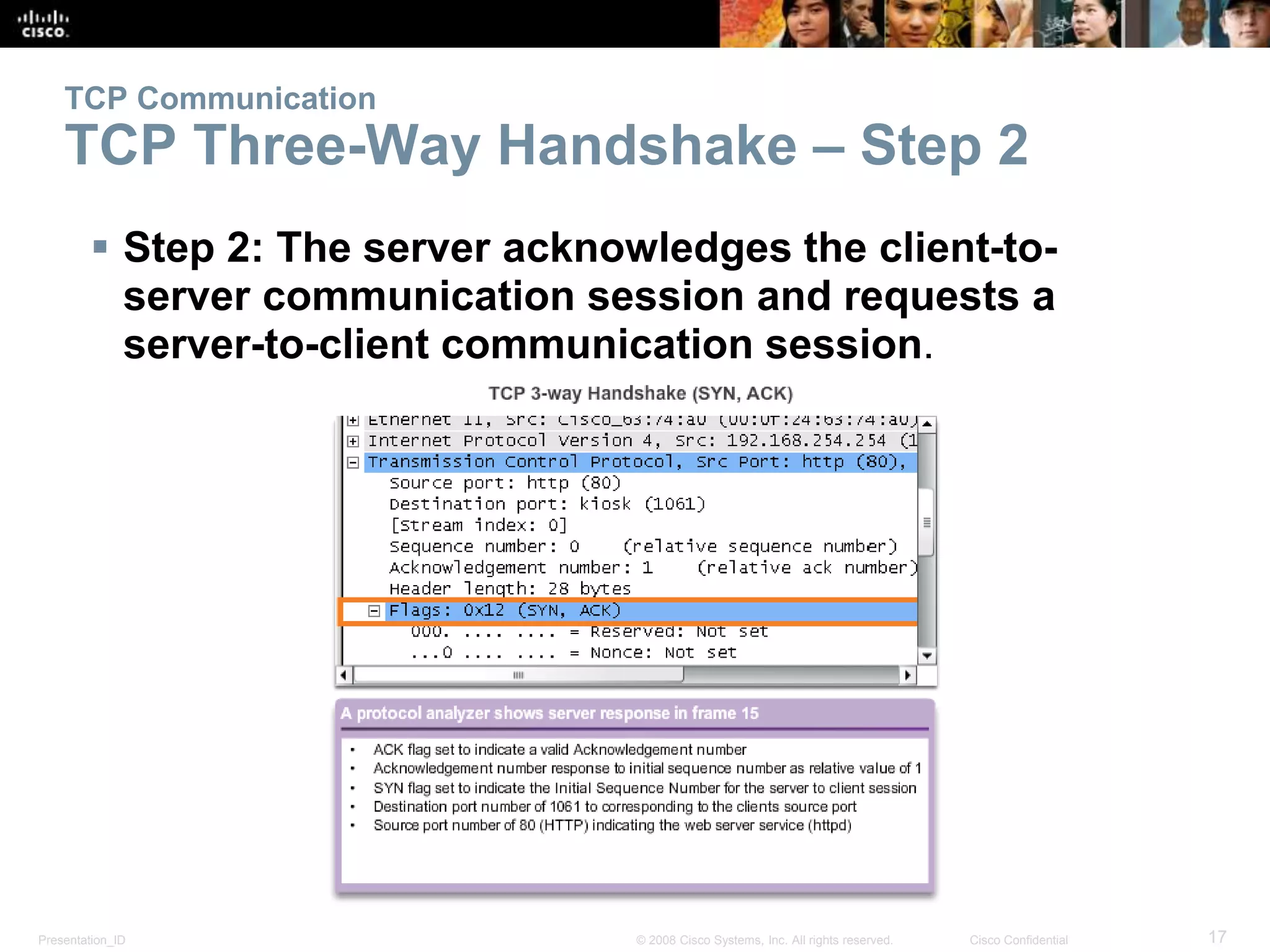
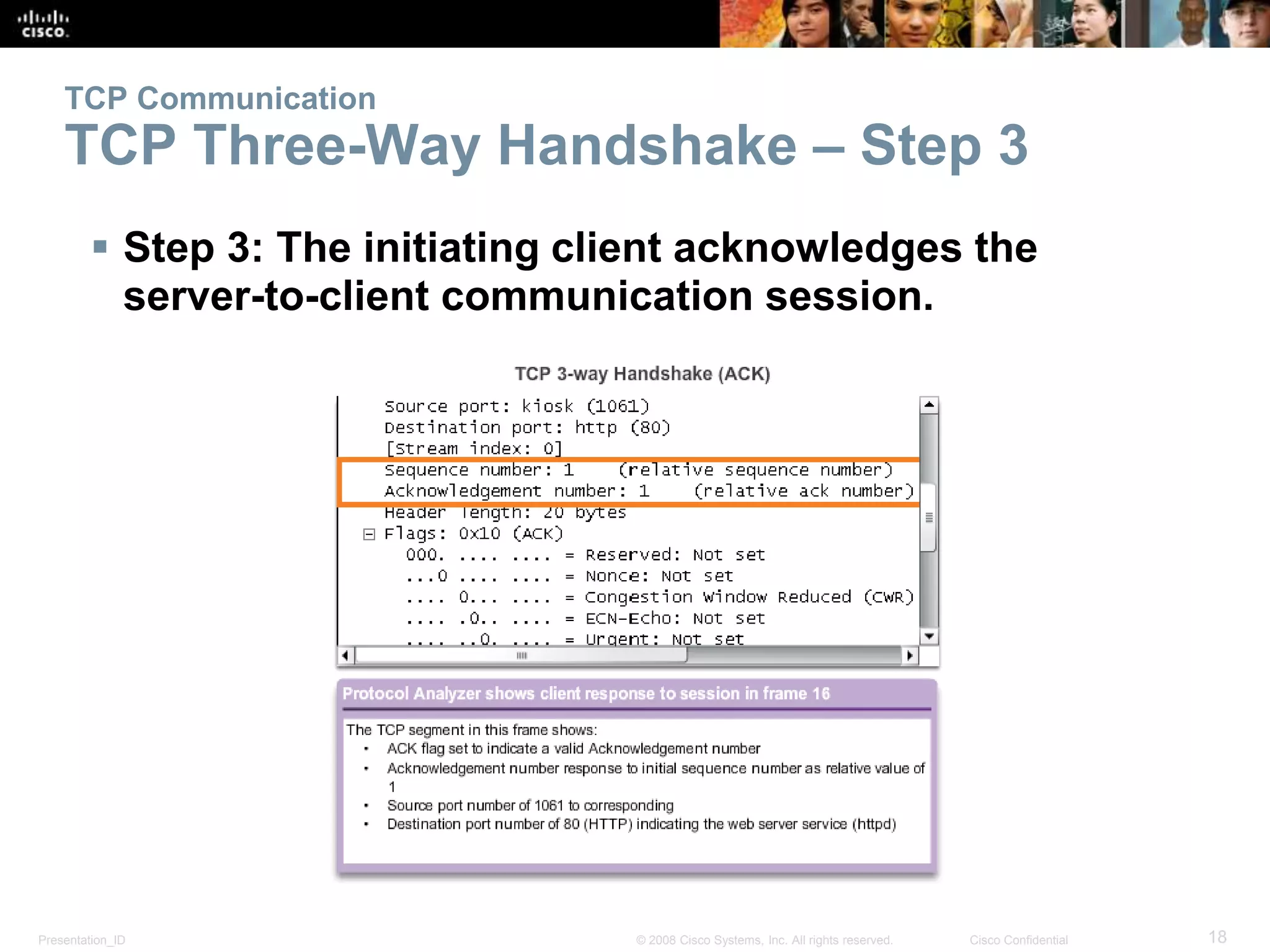
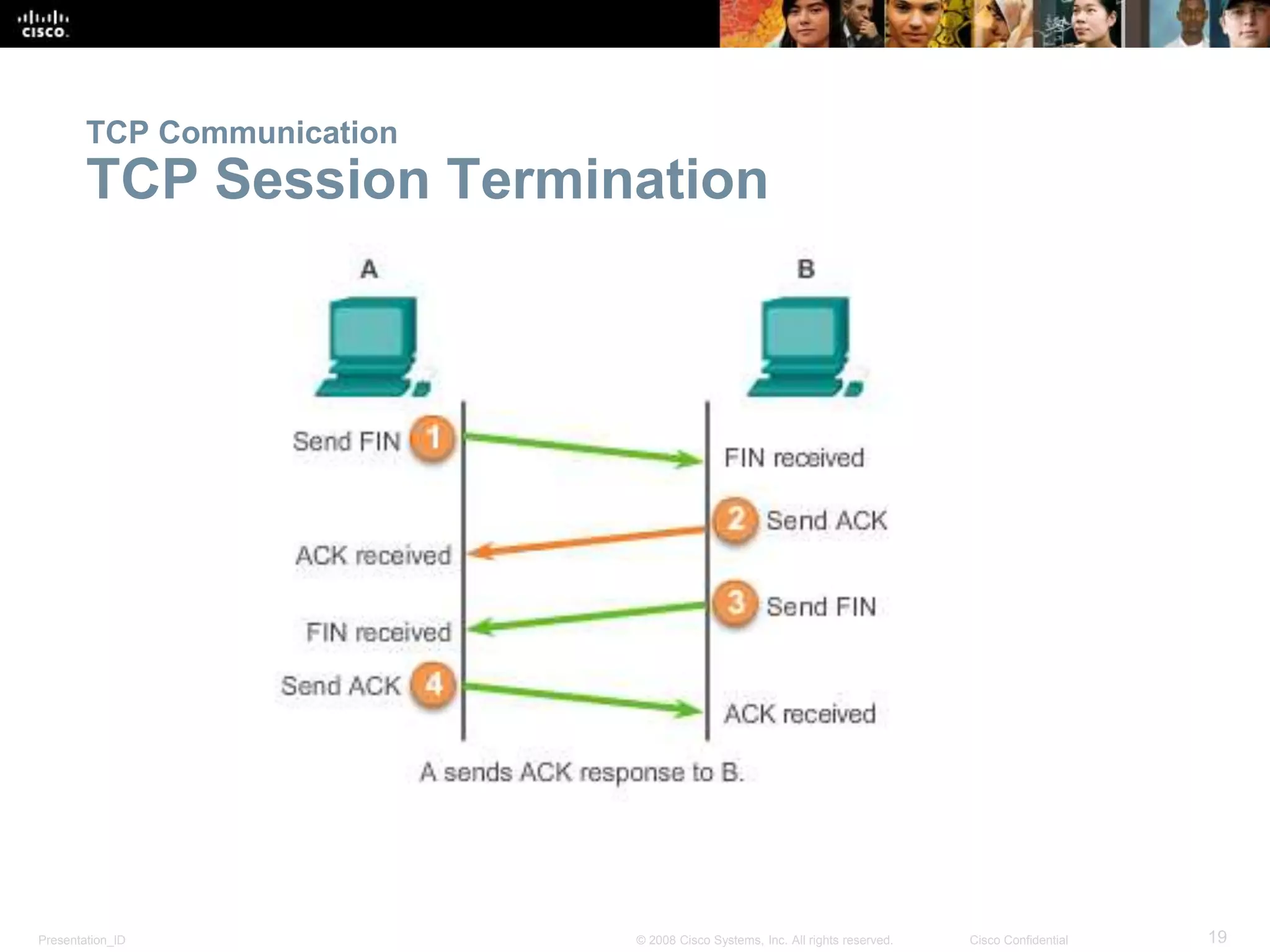
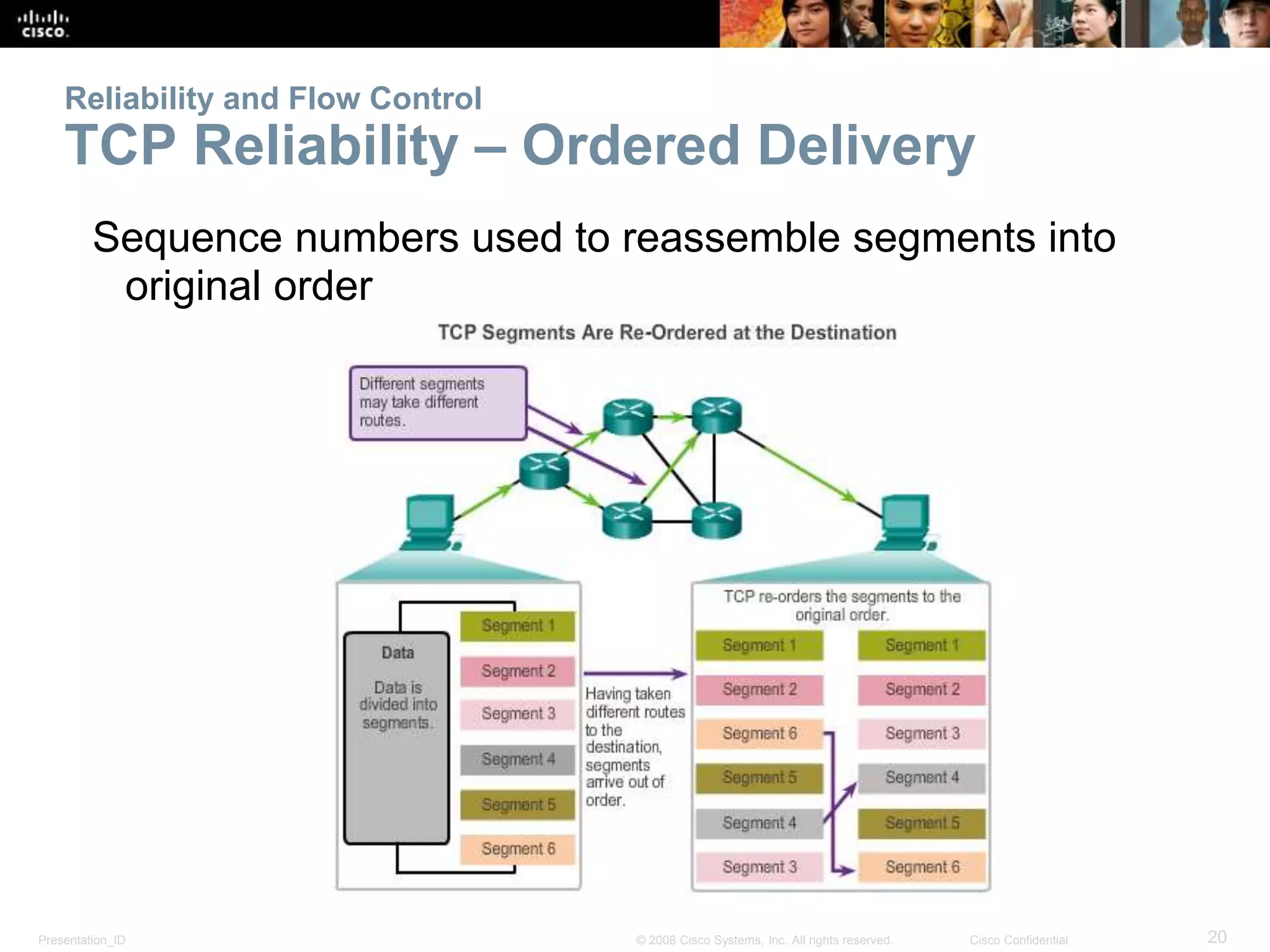
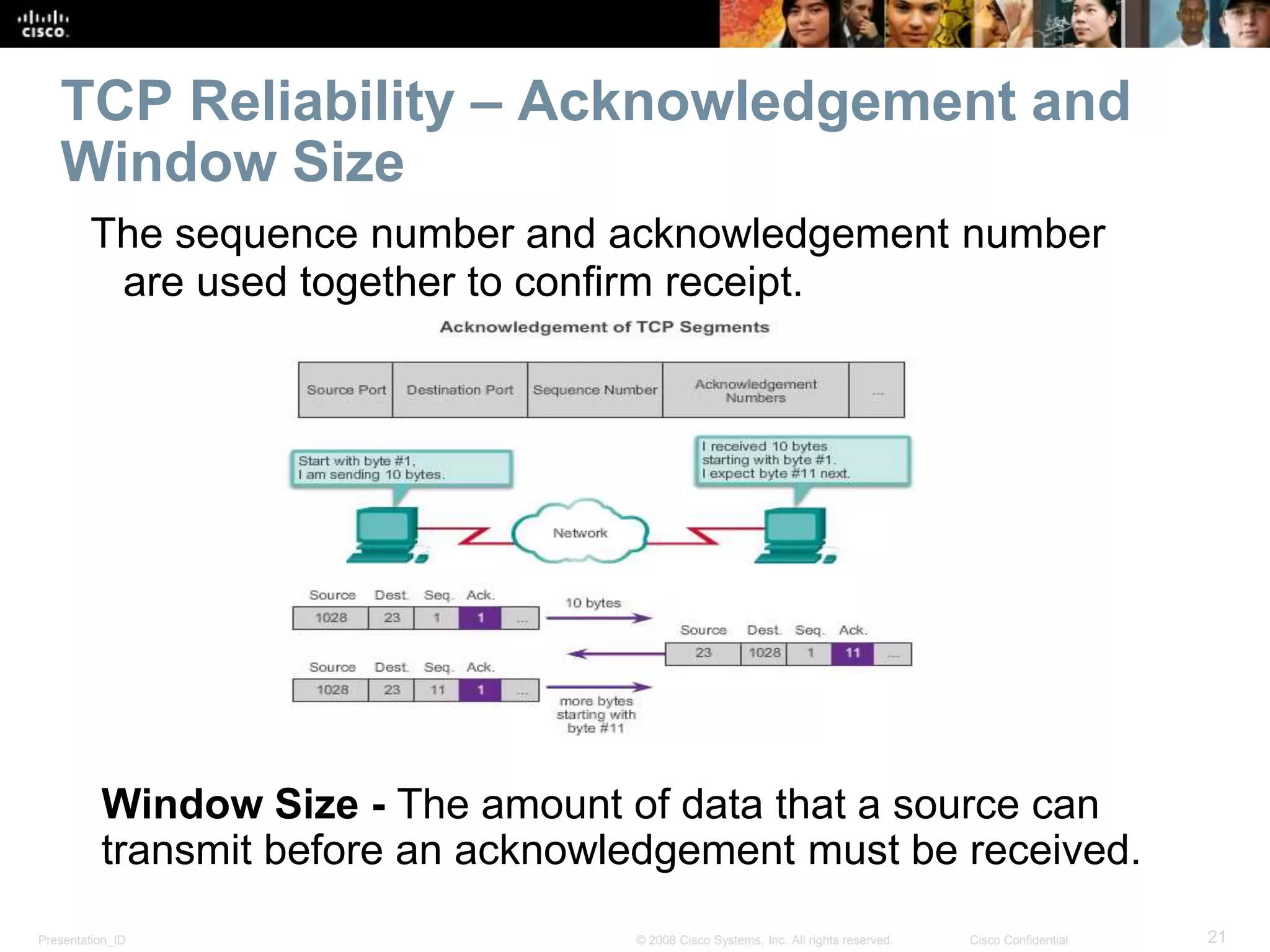
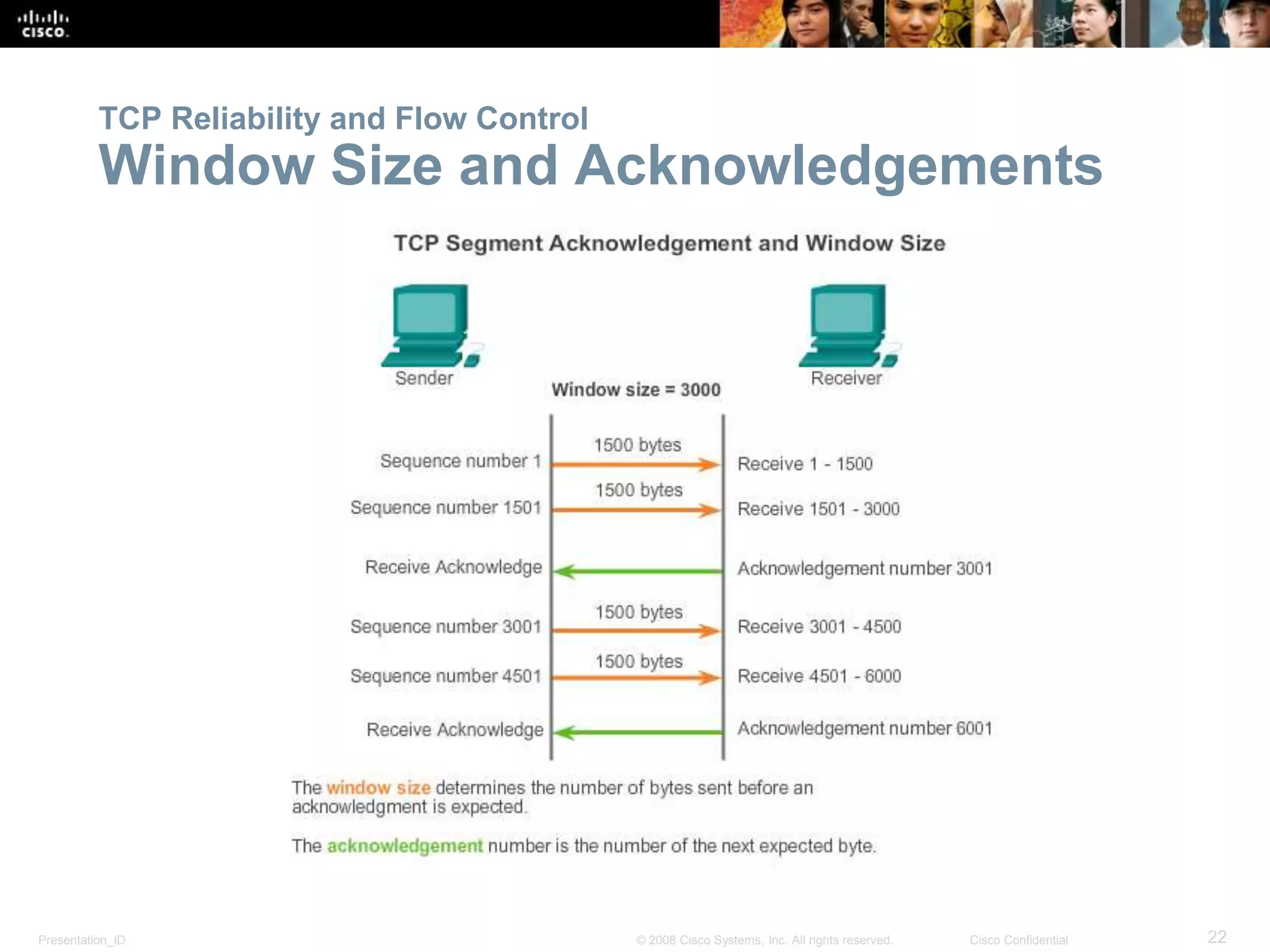
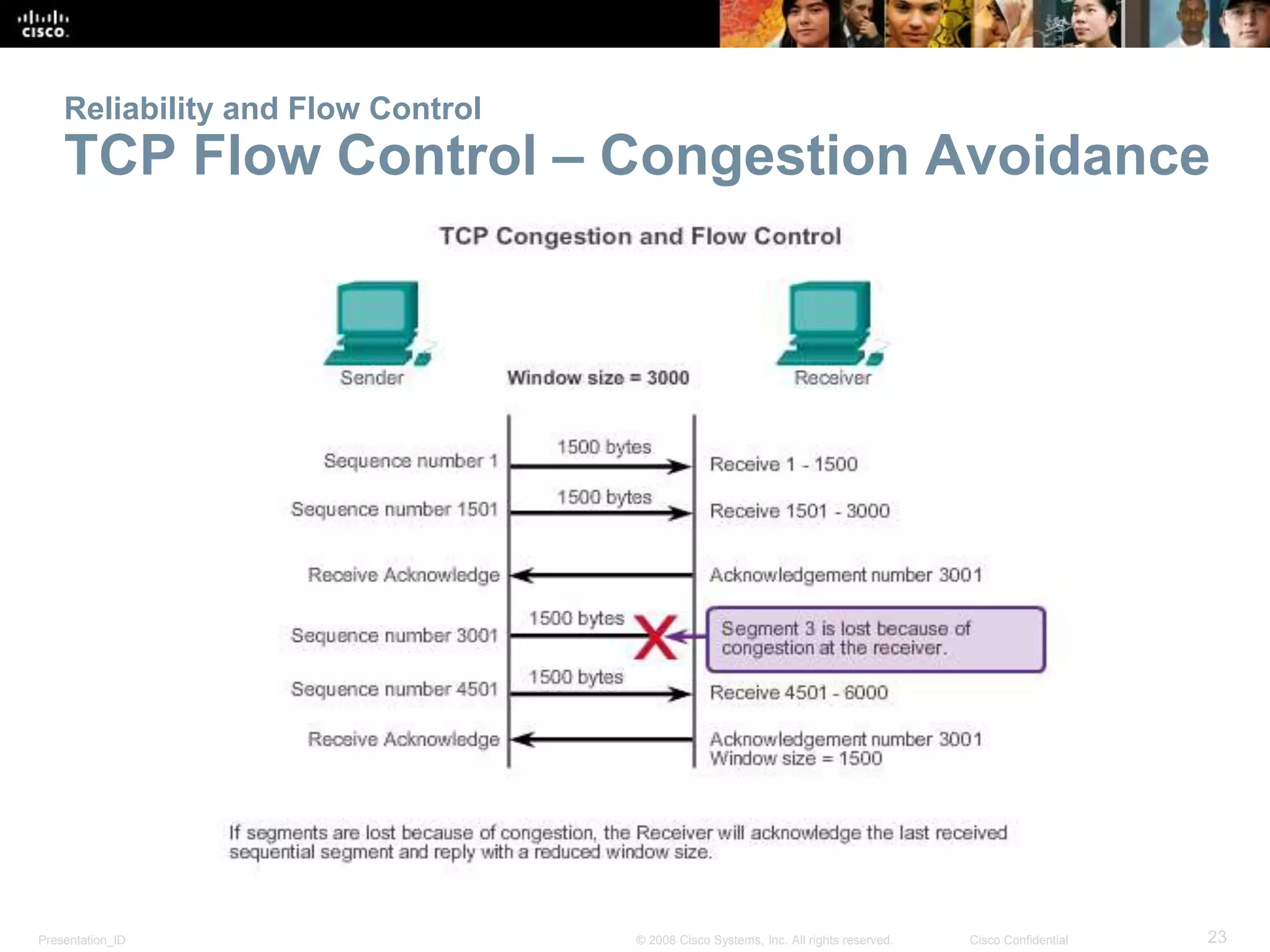
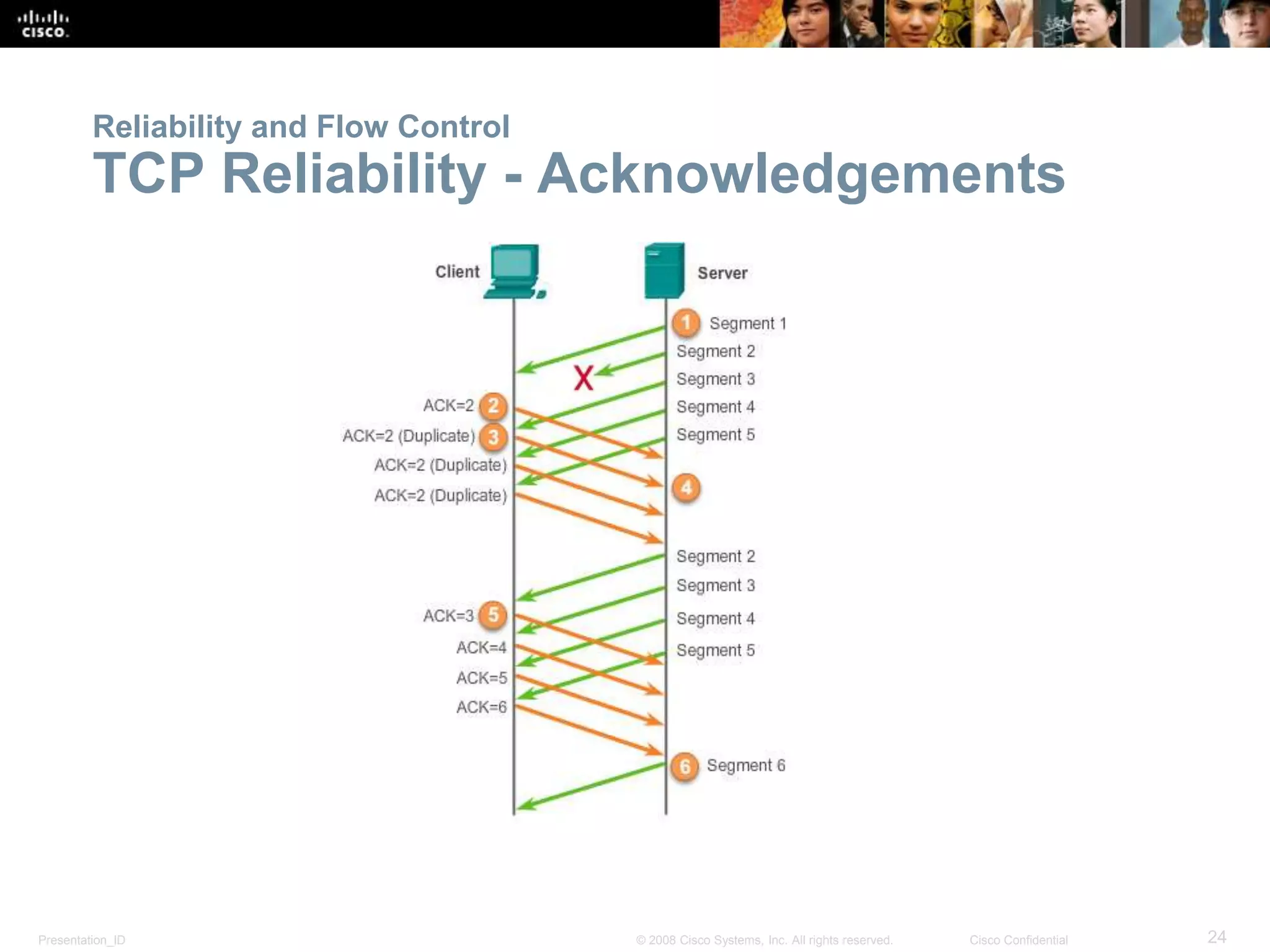
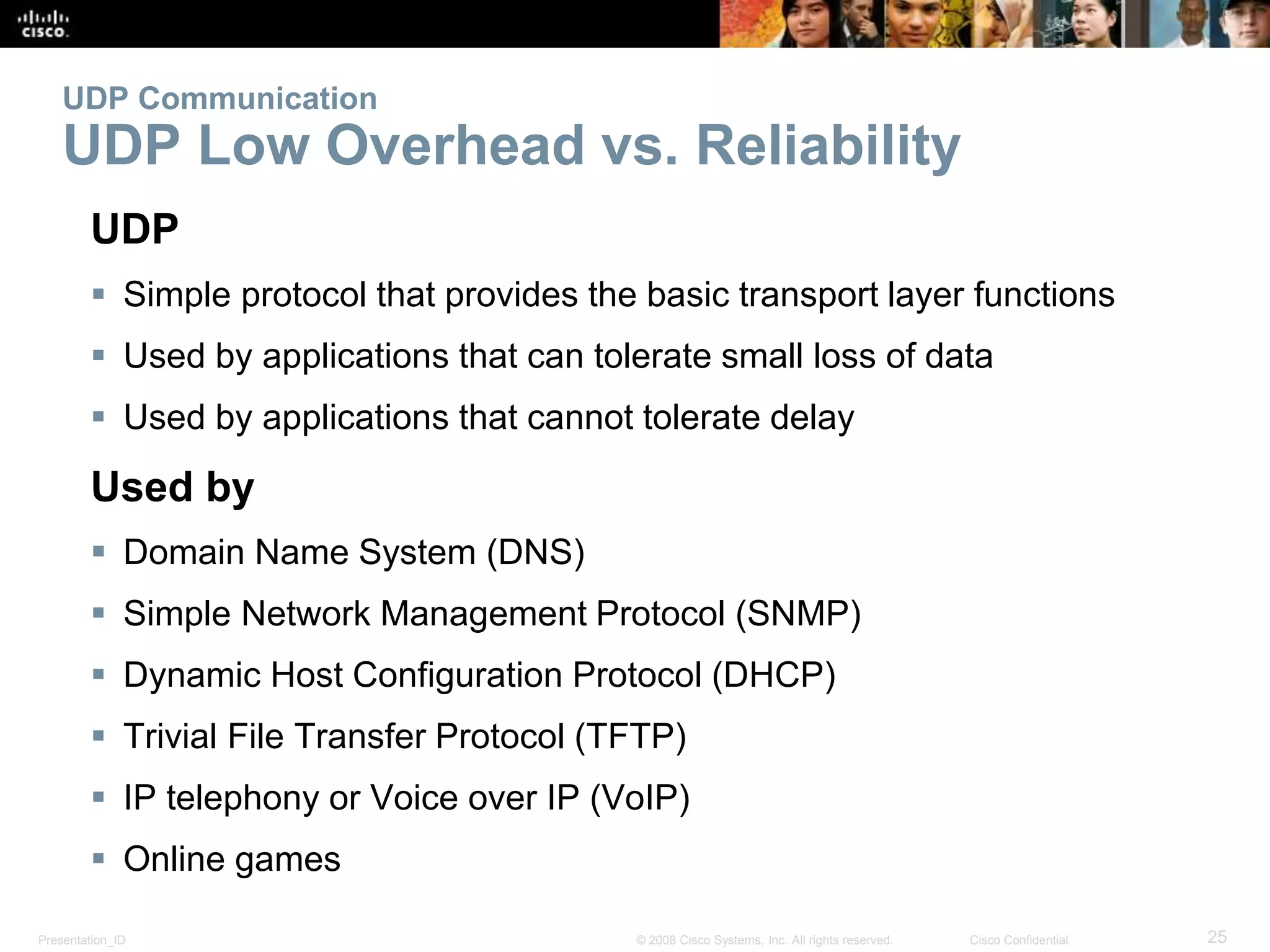
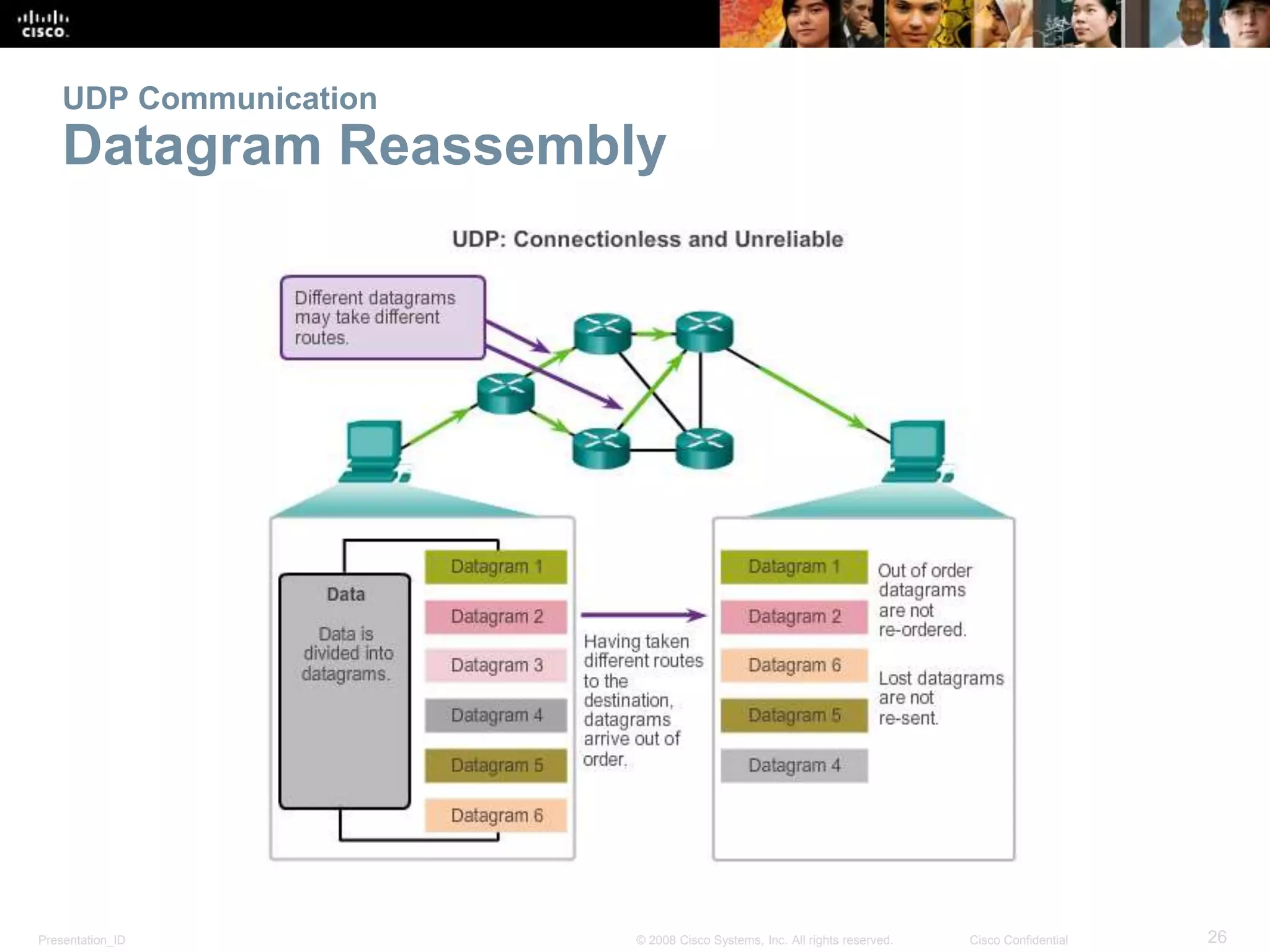
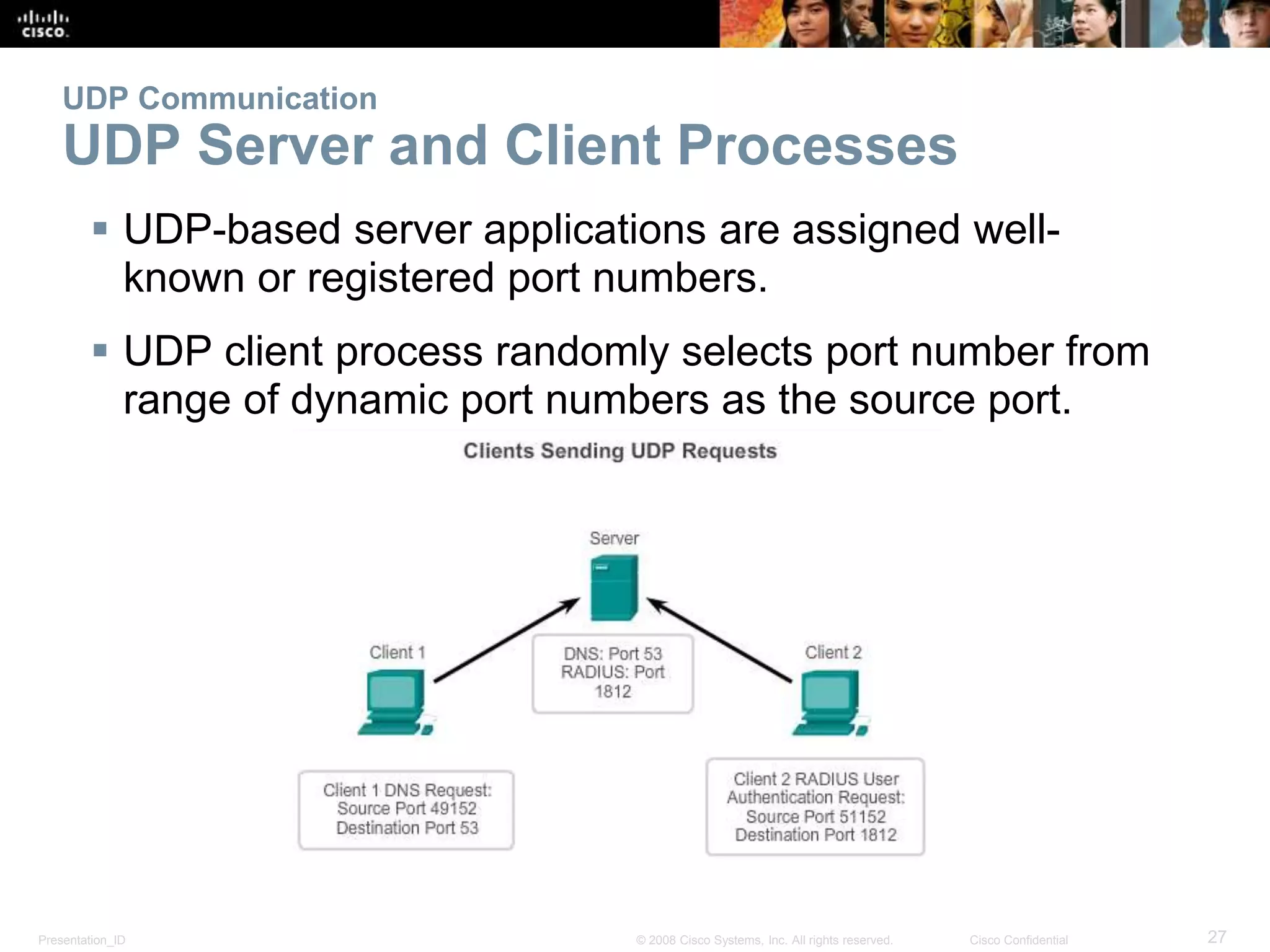
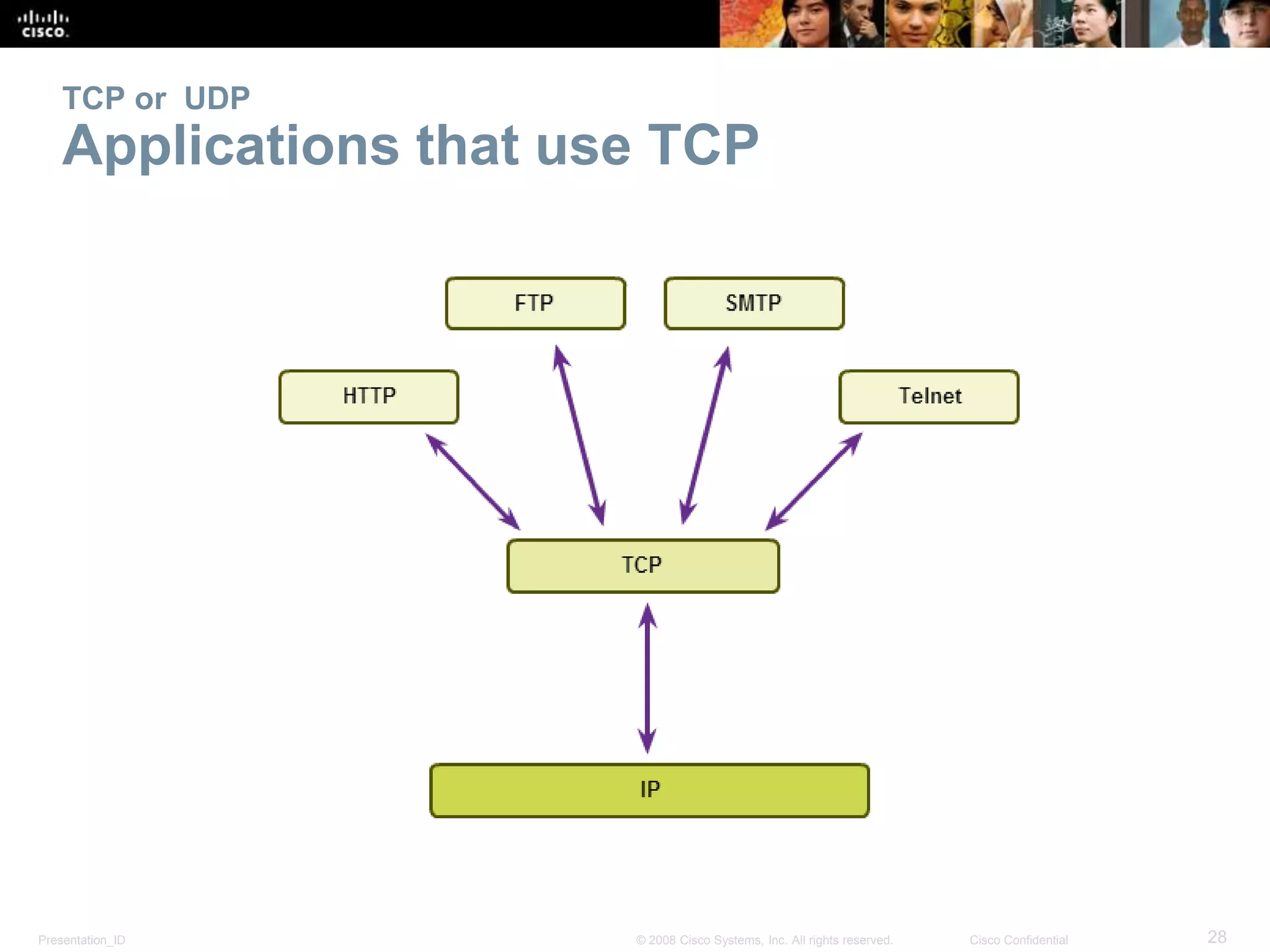
The document discusses the transport layer of computer networking. It describes the roles of two key transport layer protocols: TCP and UDP. TCP provides reliable, connection-oriented data transmission using mechanisms like three-way handshakes, acknowledgements, and window sizing. UDP provides simpler, connectionless transmission of data but with less reliability. Common applications of each protocol are also reviewed.