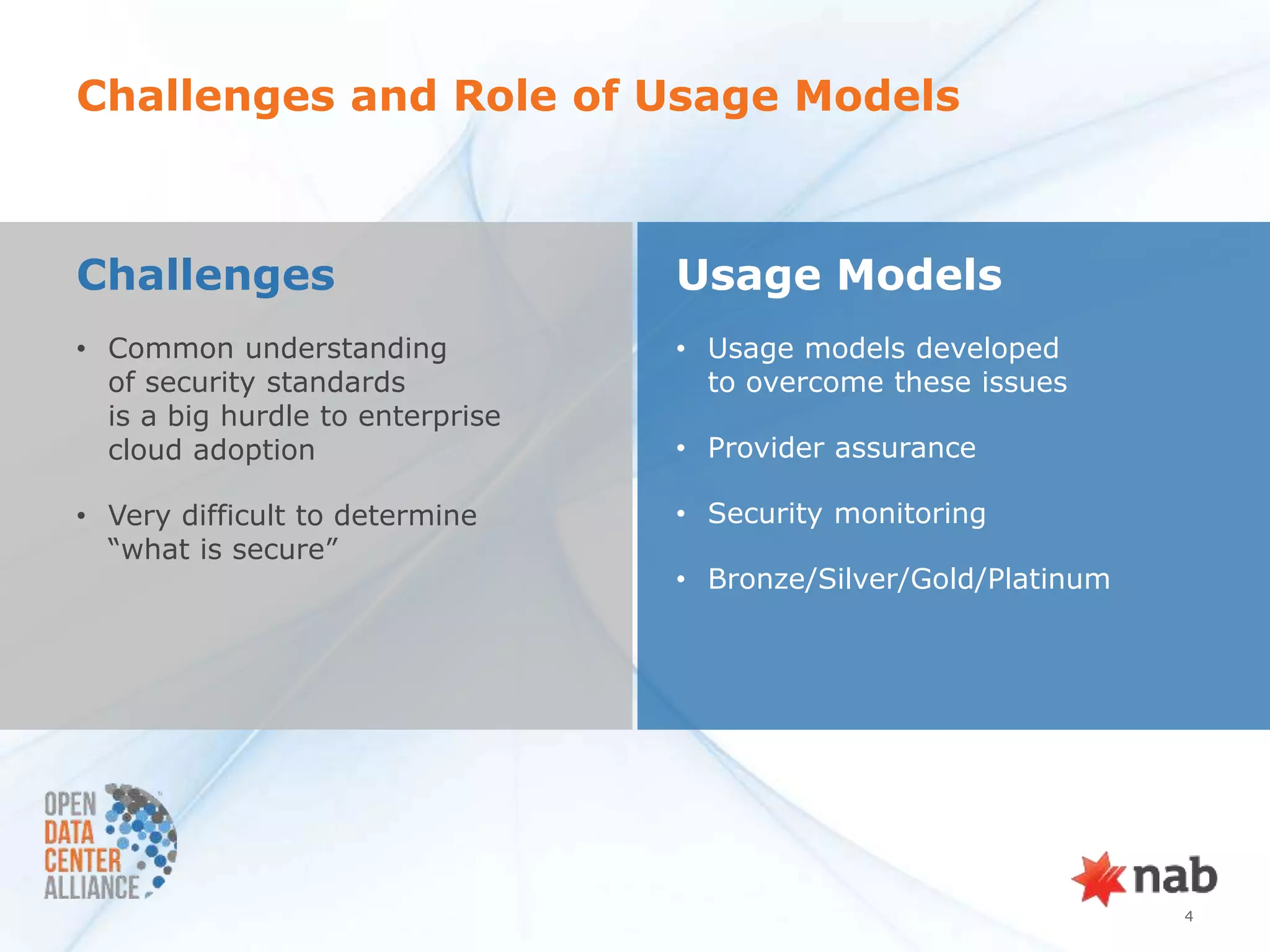
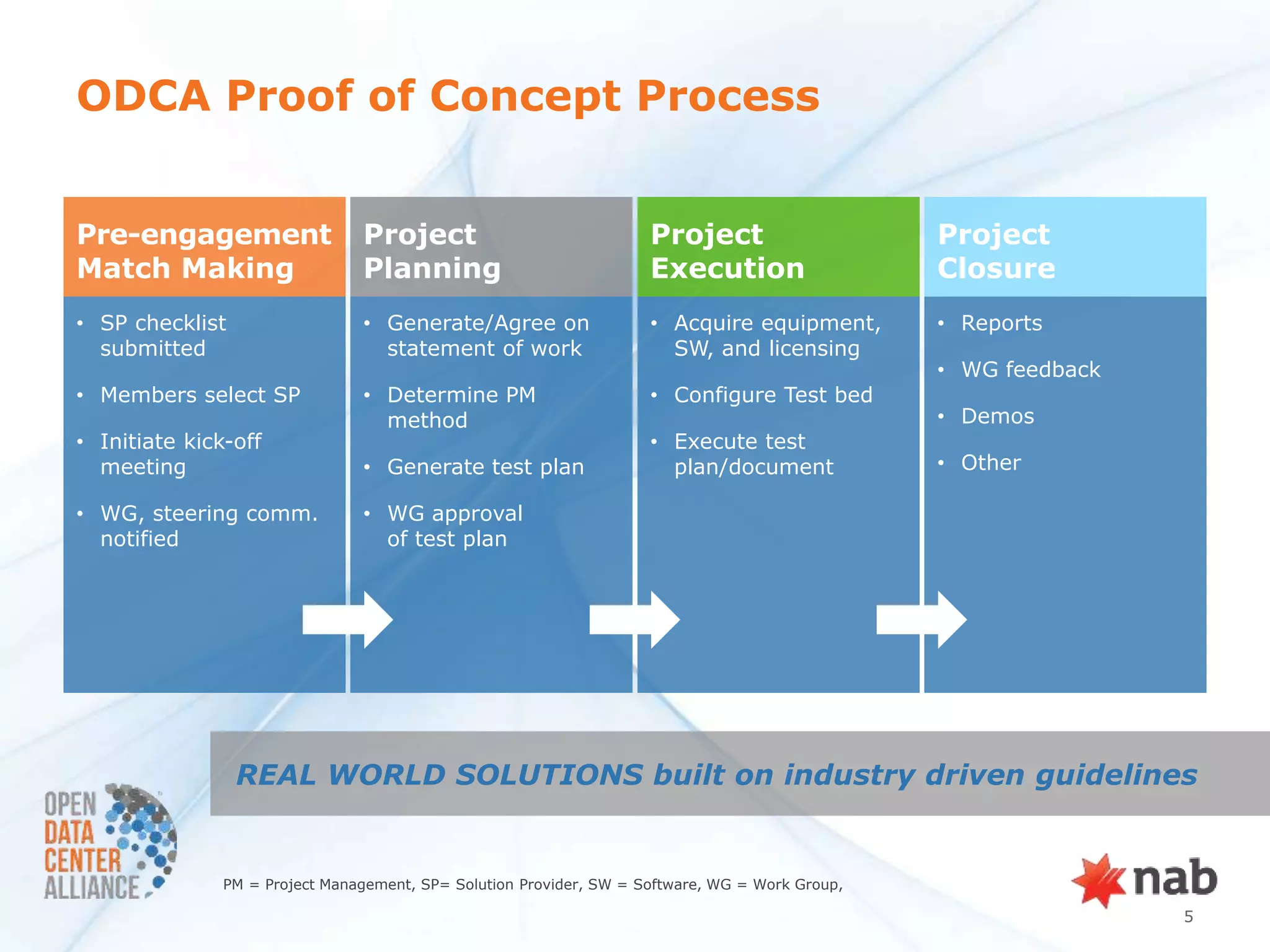
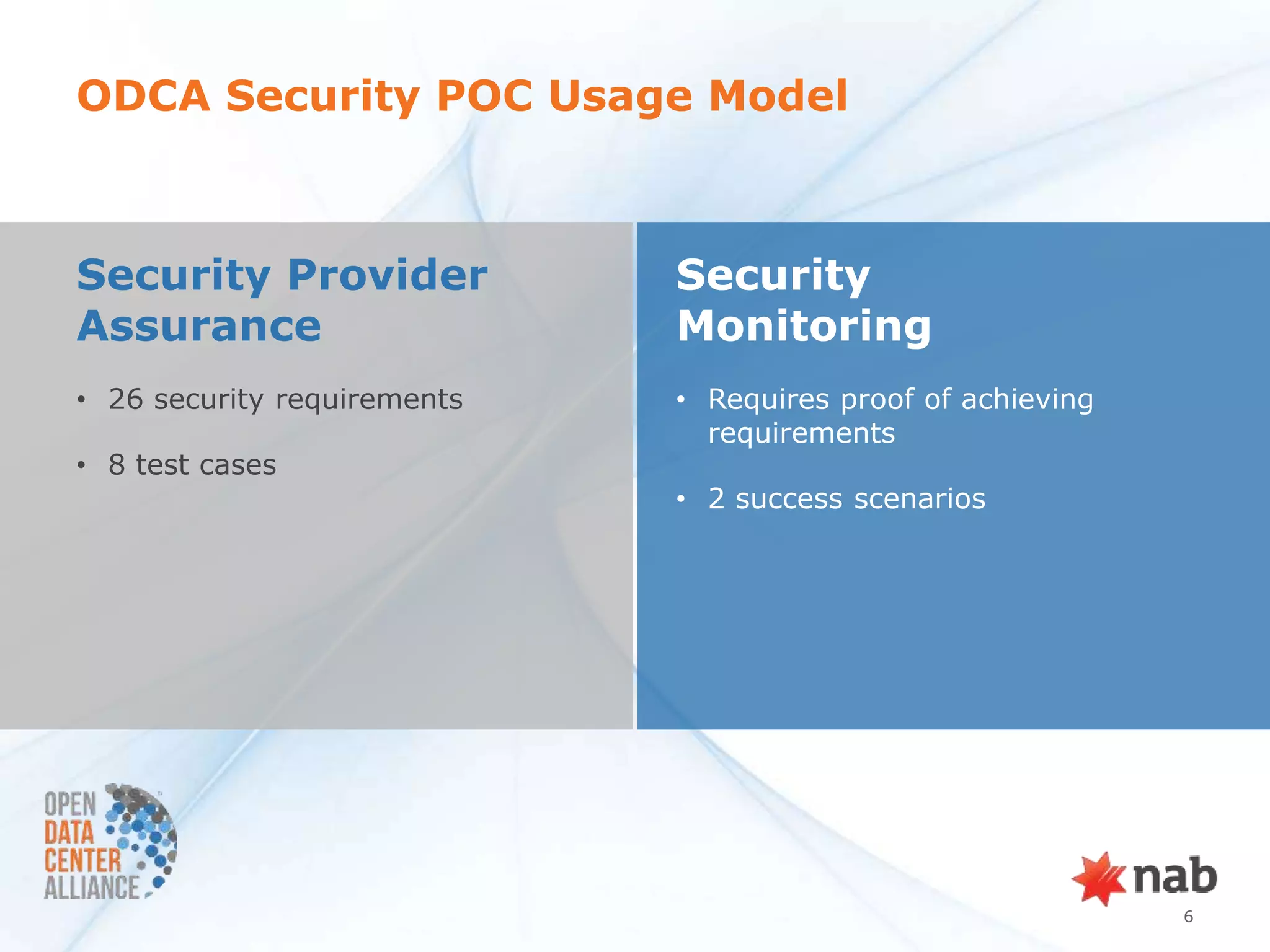
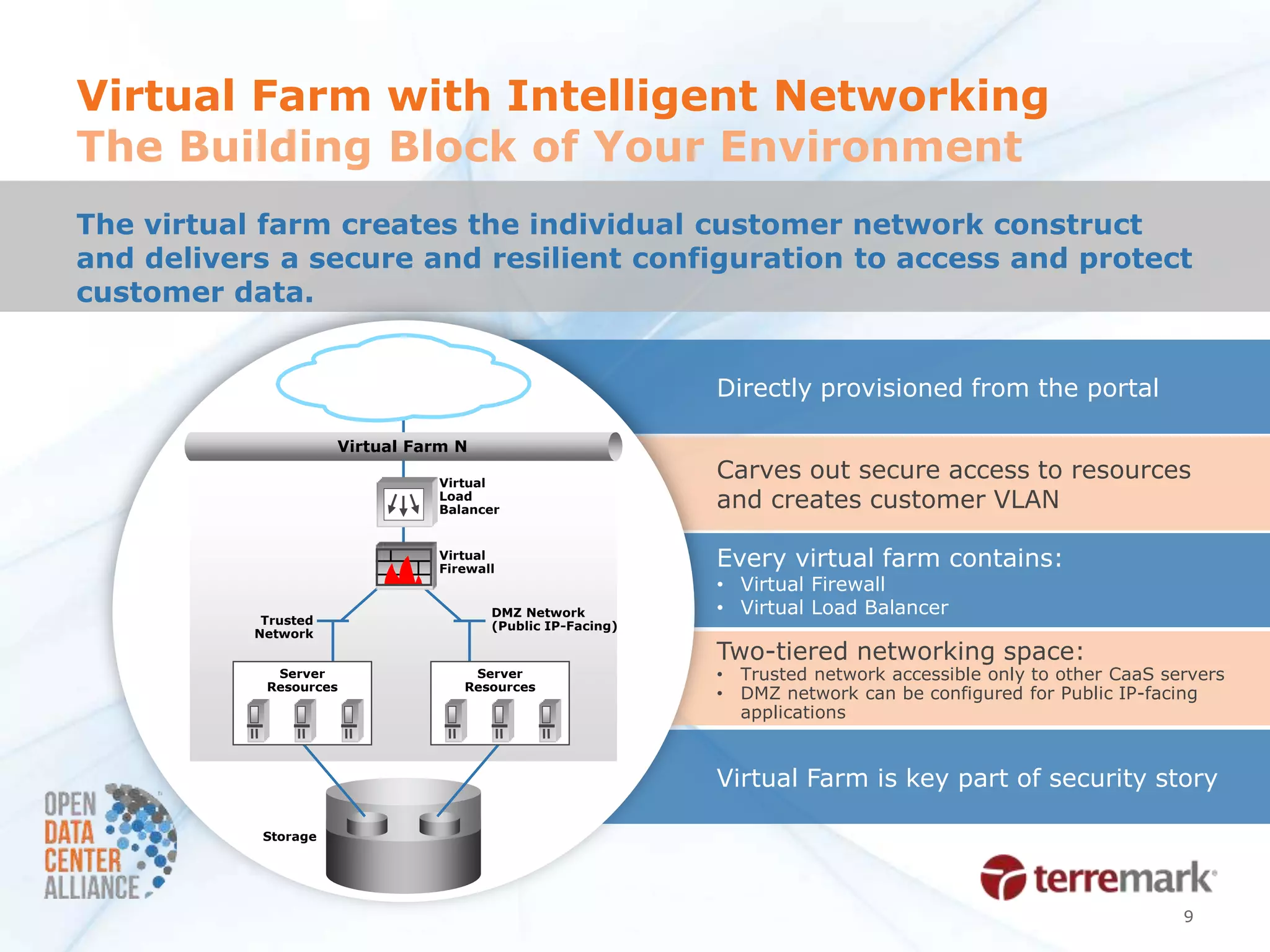
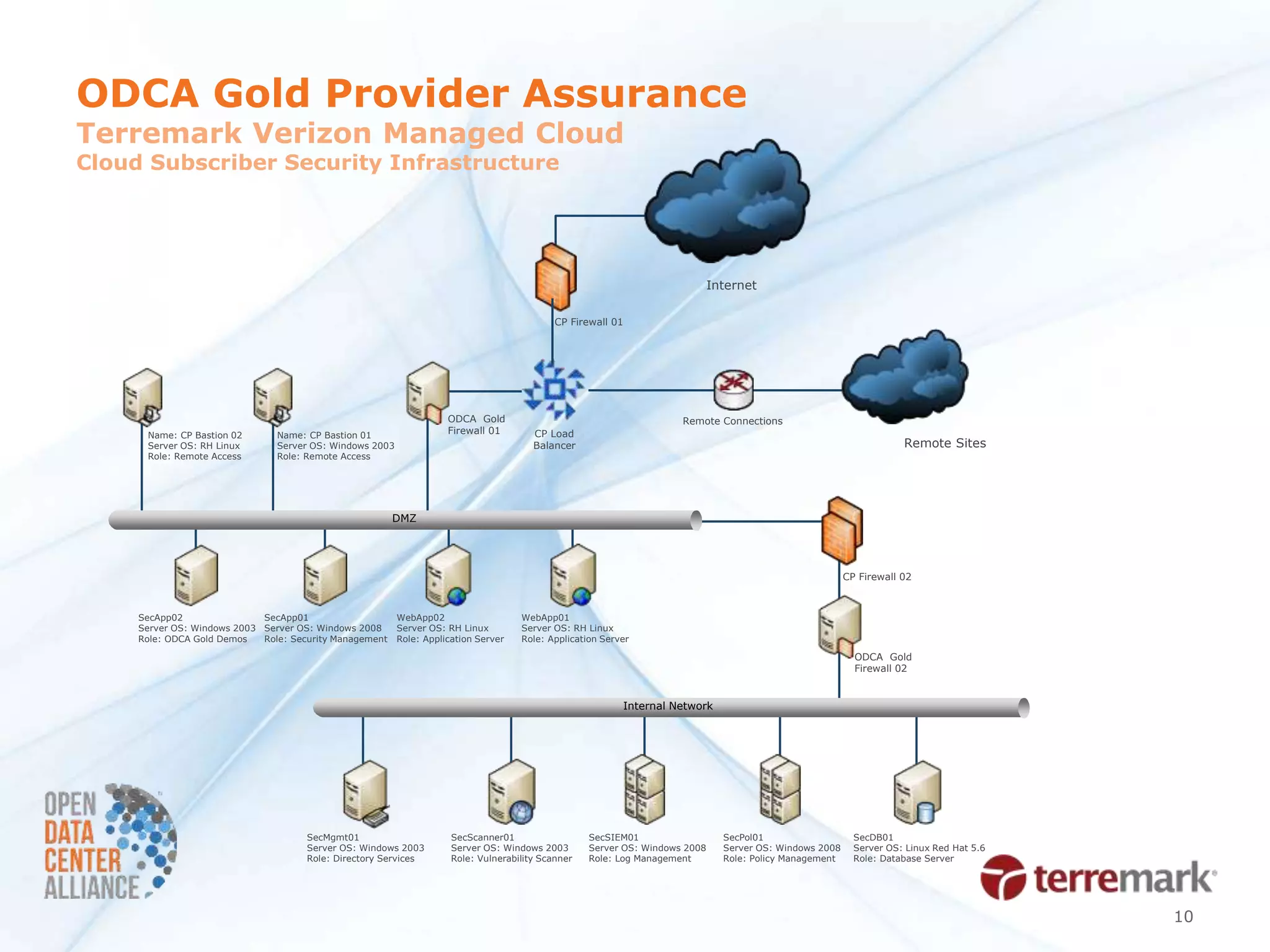
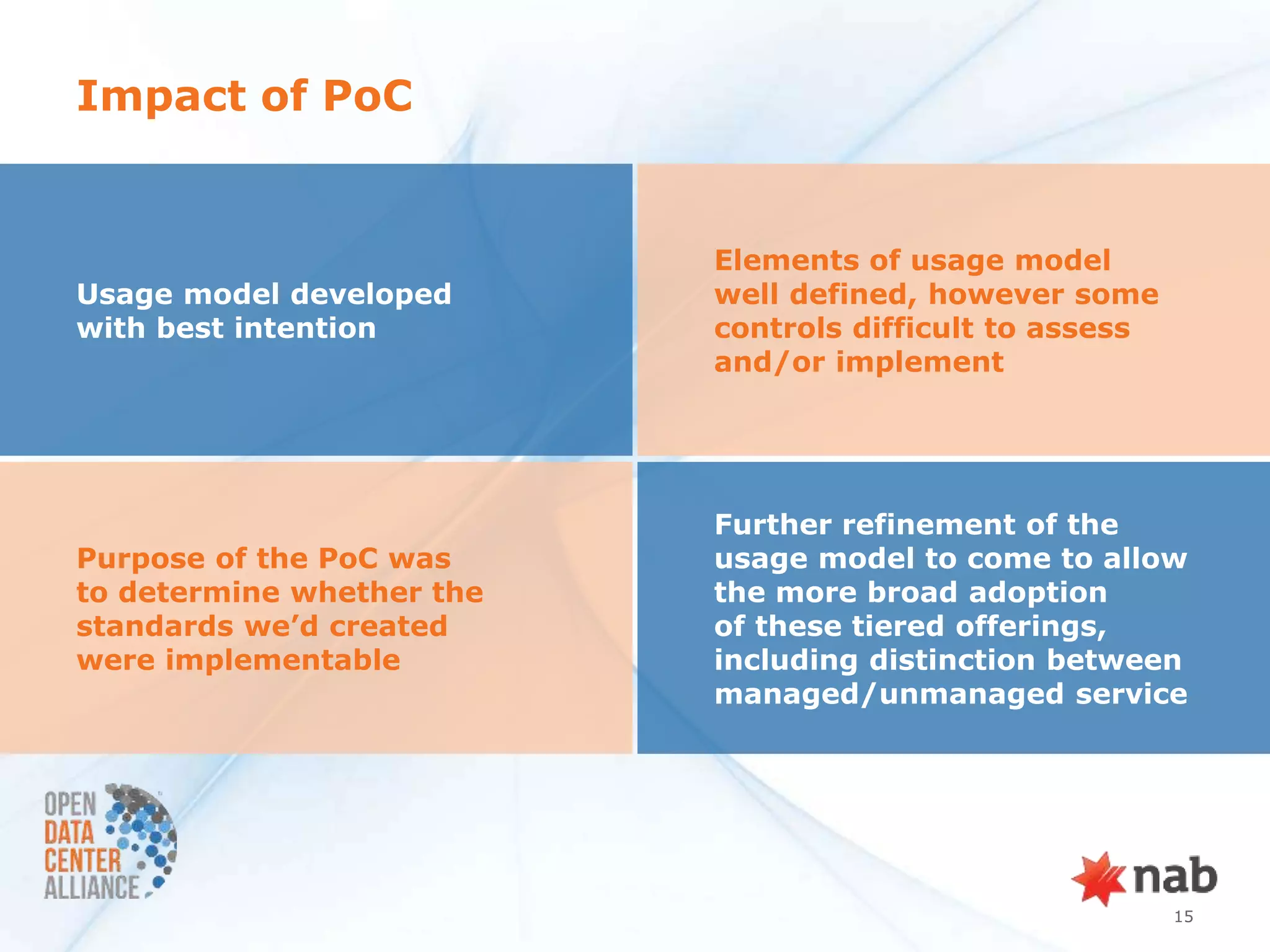
The document summarizes a security POC conducted by the ODCA to test provider assurance requirements for different cloud assurance levels (bronze, silver, gold, platinum). It discusses the challenges in implementing the requirements, outlines the testing methodology used, and summarizes the results and impact. Currently, no service providers are meeting all the requirements for gold-level assurance. The POC highlighted the need to refine both the usage models and RFP requirements to better enable adoption of these tiered security offerings.