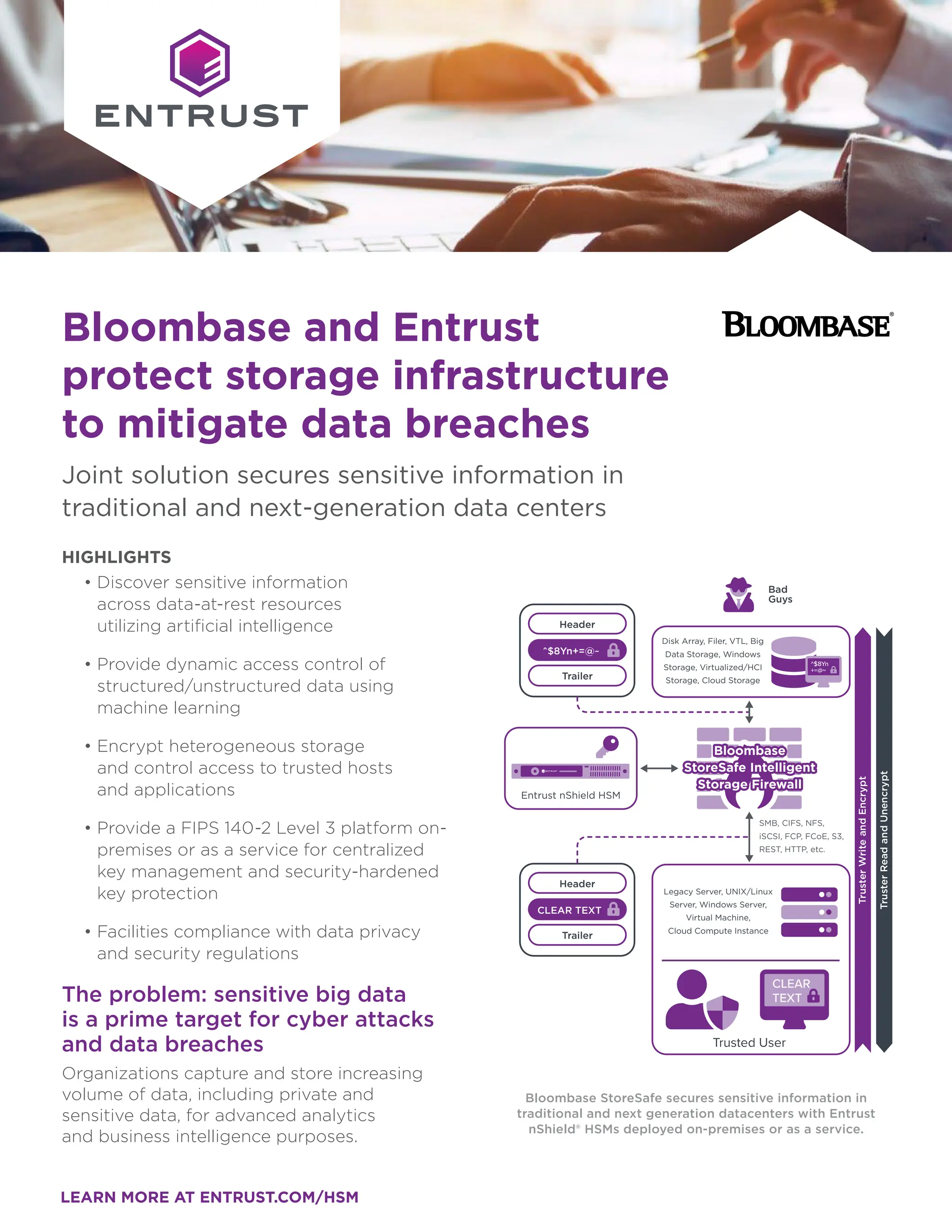
The document discusses the joint solution of Bloombase and Entrust, which focuses on securing sensitive information in both traditional and next-generation data centers to mitigate data breaches. It highlights the use of artificial intelligence and machine learning for dynamic access control, cryptographic protection, and compliance with data security regulations. The collaboration provides a robust encryption and key management solution, enhancing data-at-rest security across various storage environments.