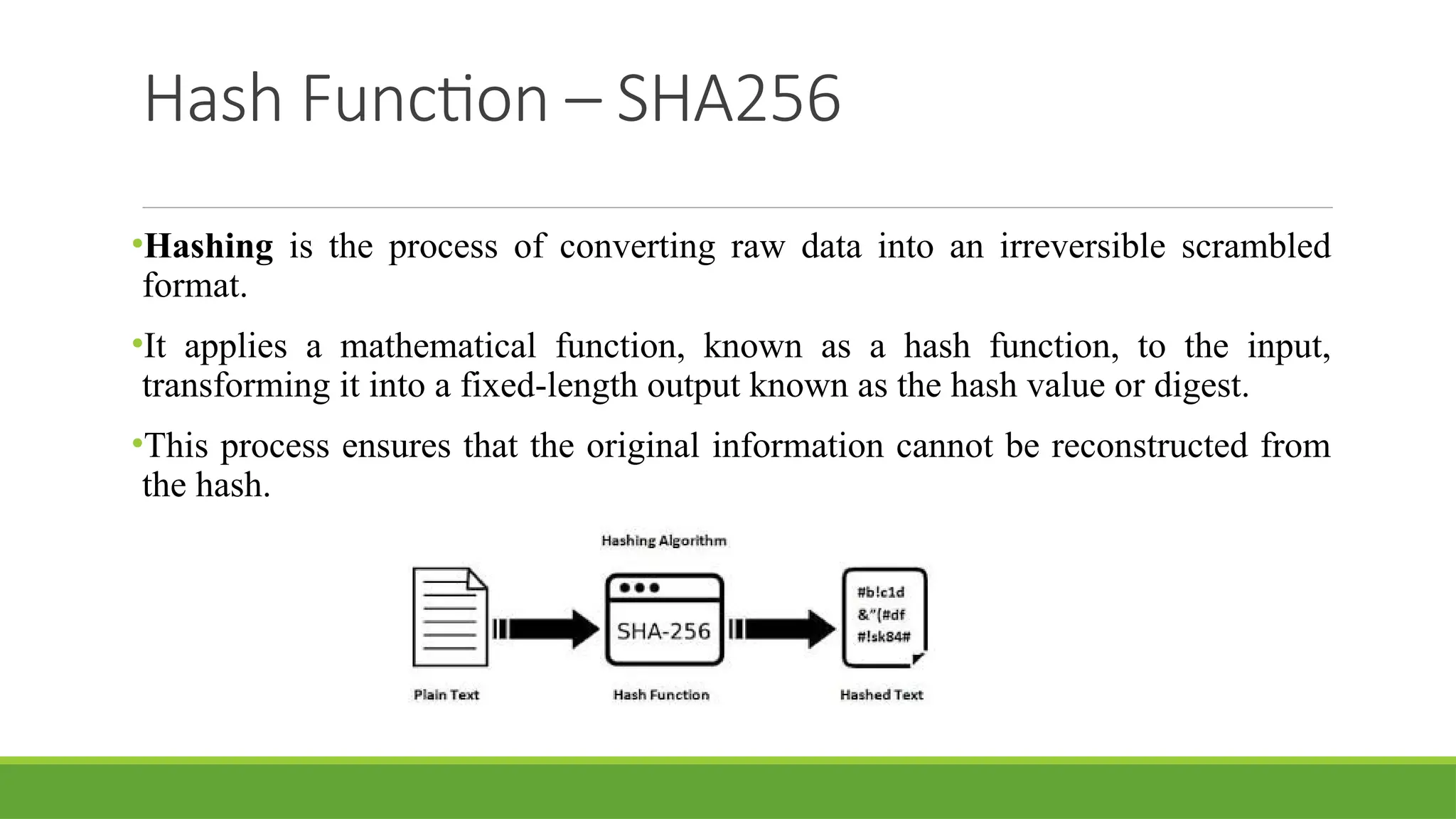
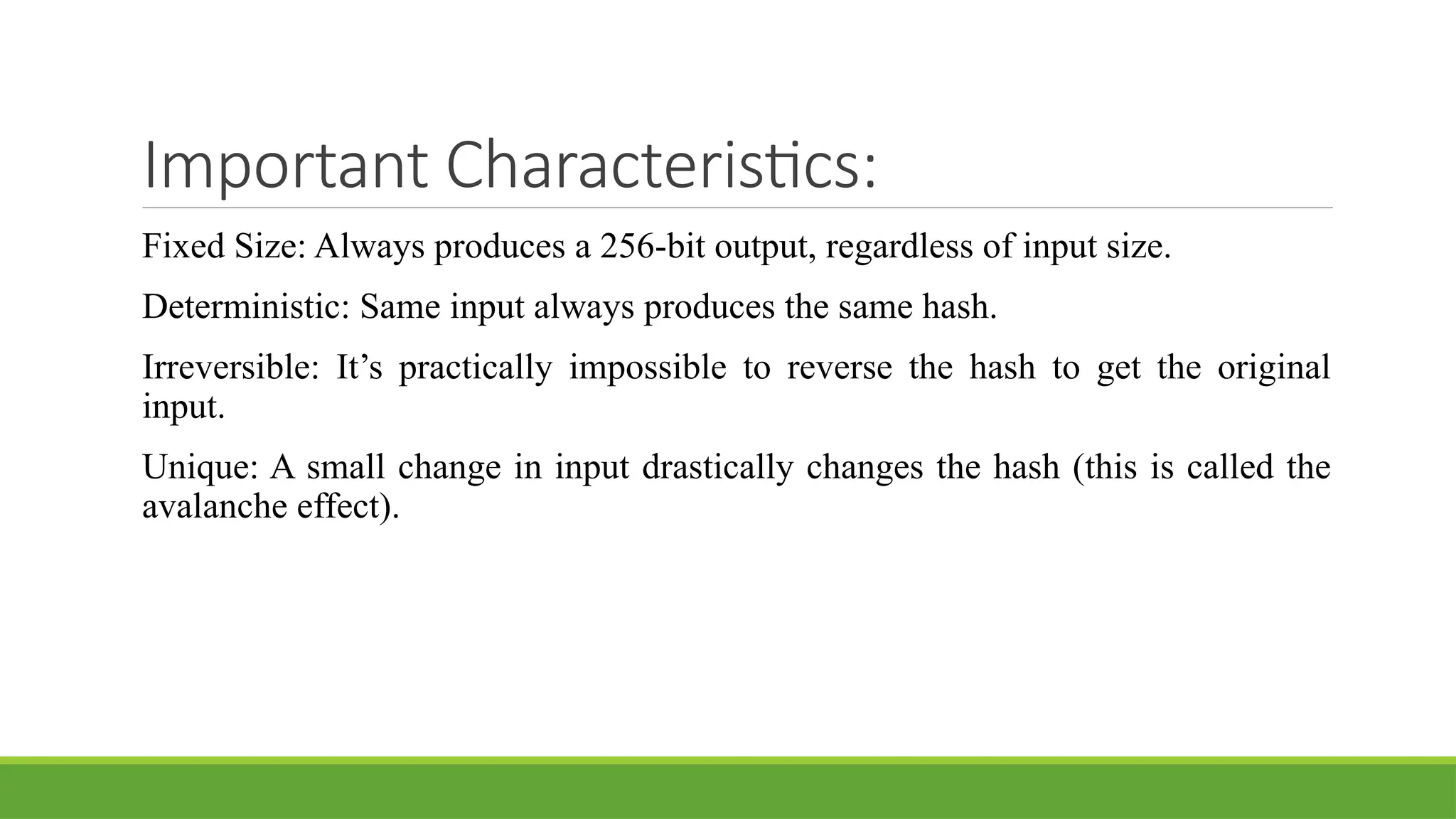
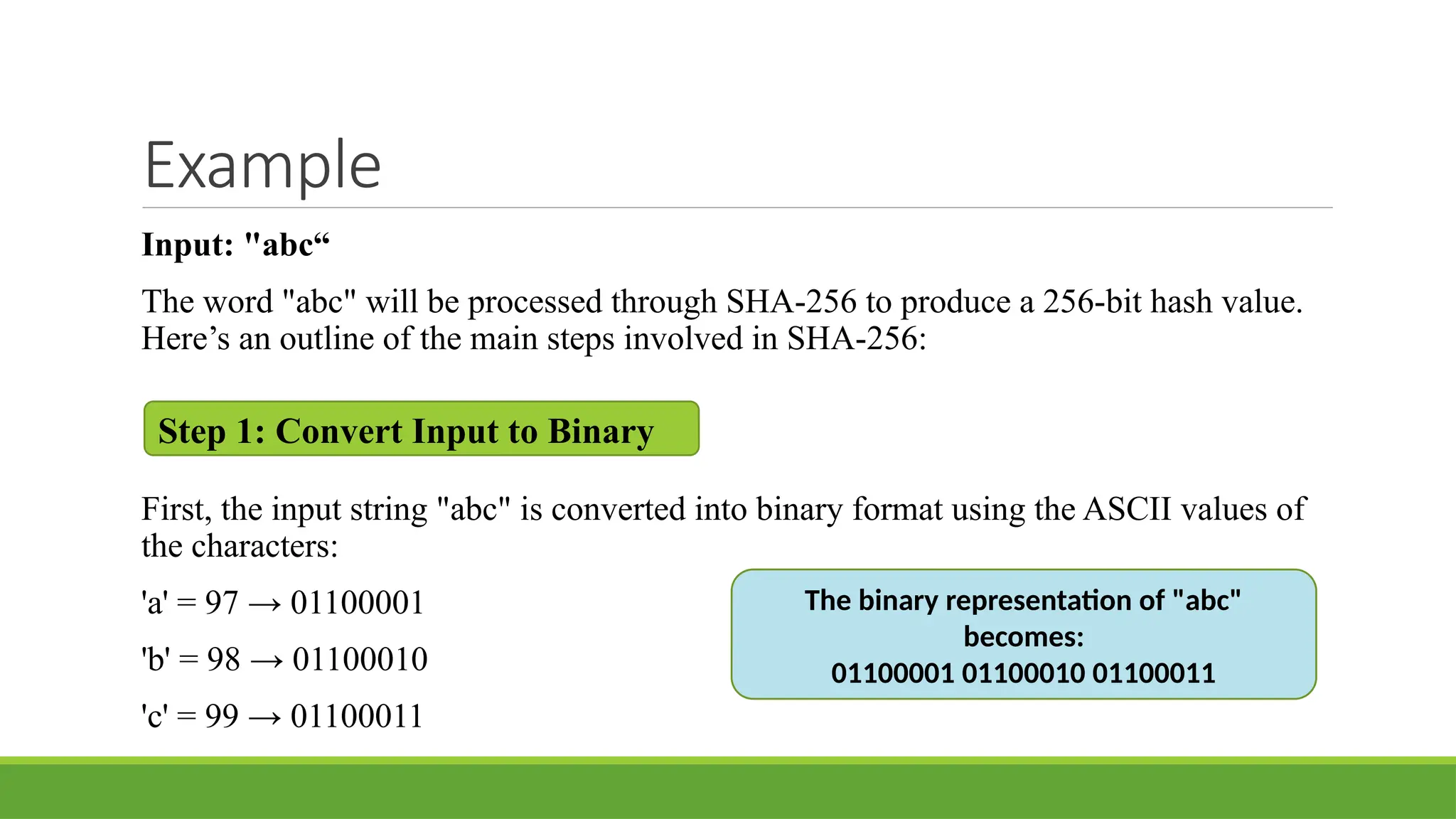
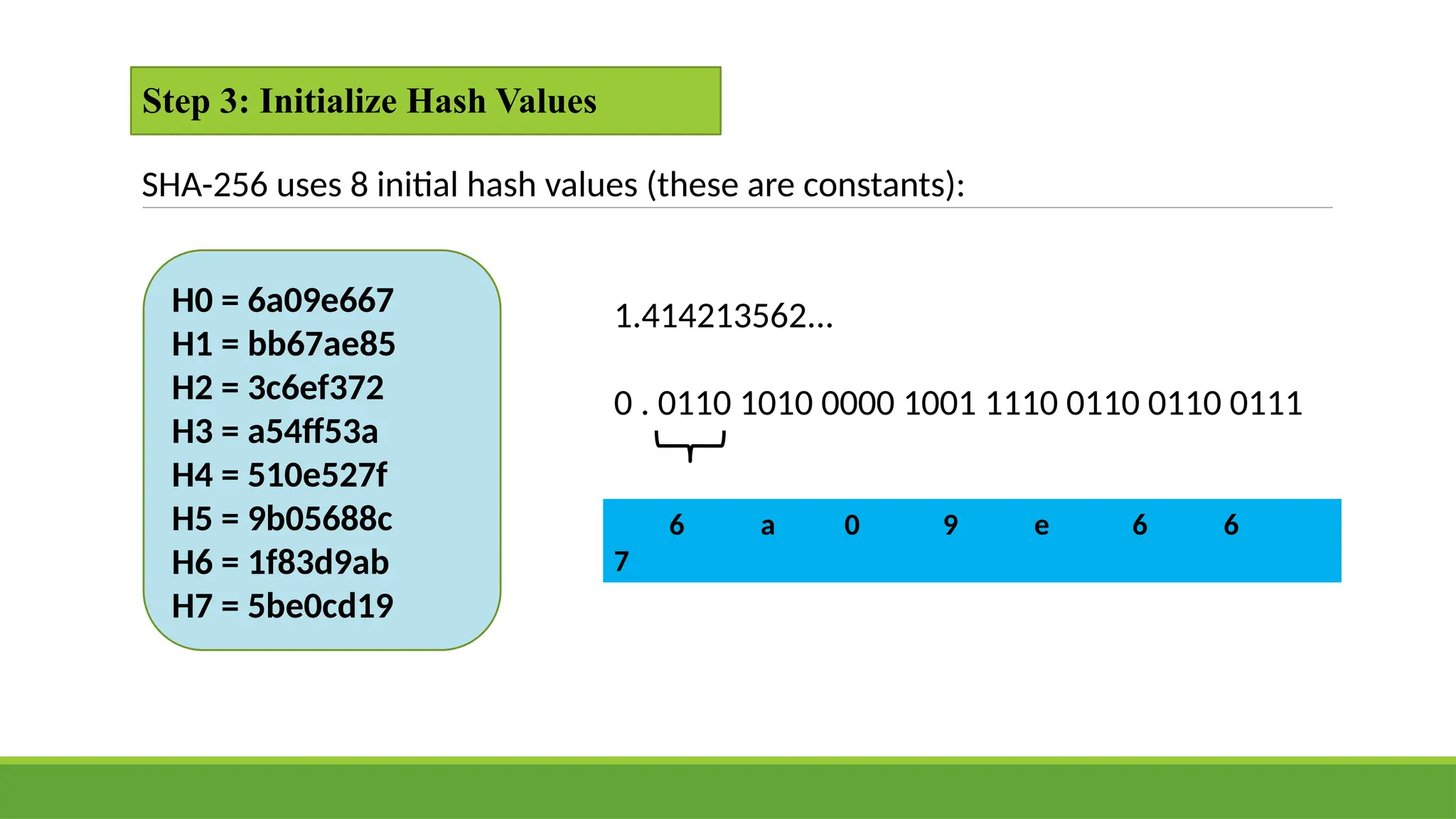
Discover the fundamentals of Blockchain Technology, the innovation powering Bitcoin, cryptocurrencies, and the next generation of the Internet (Web3). This presentation simplifies complex concepts into easy-to-understand visuals and examples, perfect for students, tech enthusiasts, and professionals.
In this presentation, you’ll learn:
What is Blockchain?
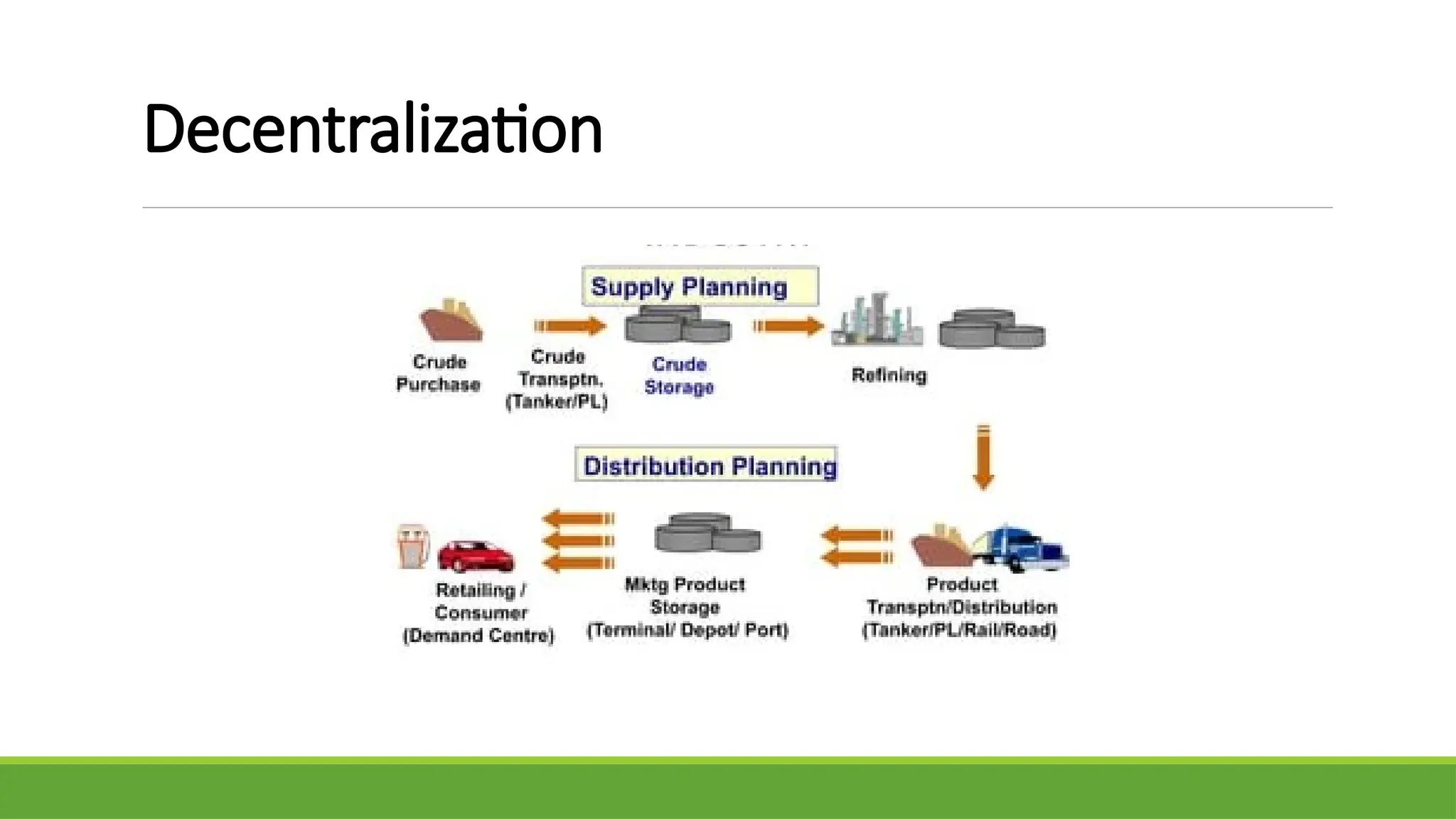
Key Features: Decentralization, Transparency, Immutability
How Blockchain Works
Use Cases Beyond Cryptocurrency
Public vs Private Blockchains
Challenges and Future Trends
Whether you're just starting out or need a quick refresher, this guide will help you grasp the power and potential of blockchain.