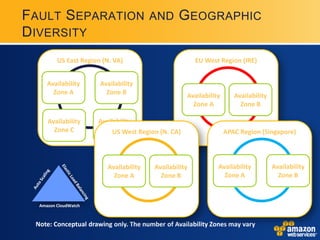
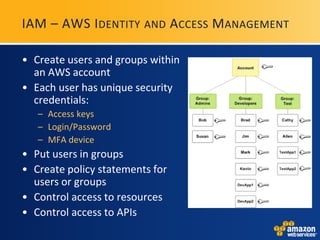
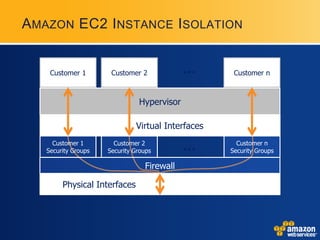
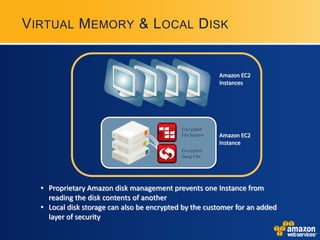
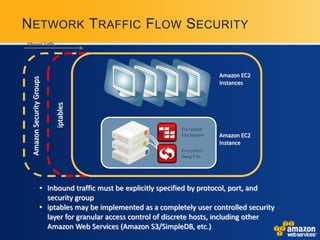
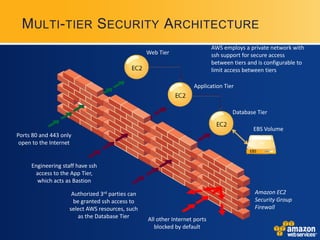
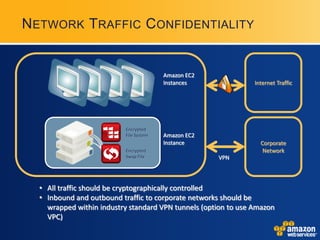
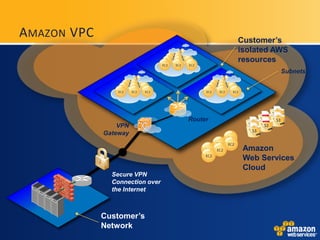
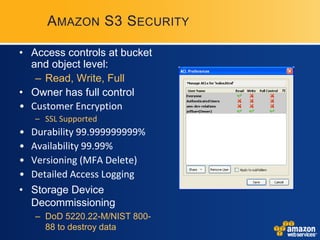
AWS provides security certifications like SAS70 Type II audits and maintains physical and network security controls. It utilizes multiple availability zones, data redundancy, encryption, firewalls, and access management to isolate and protect customer data and infrastructure. The document encourages feedback to further strengthen AWS's security posture and compliance offerings.