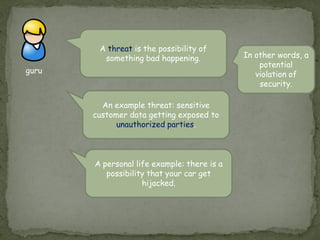
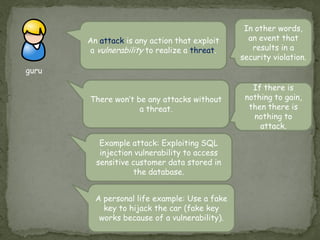
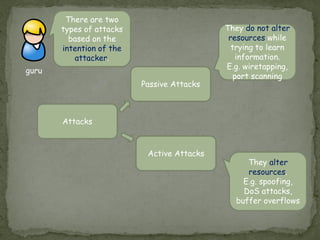
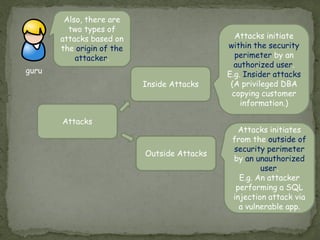
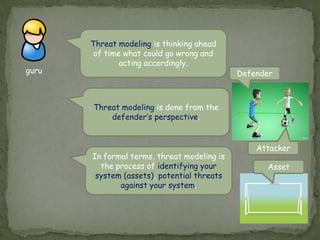
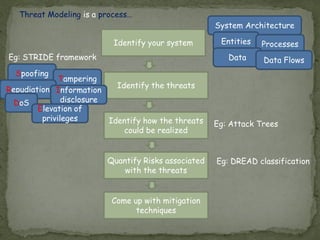
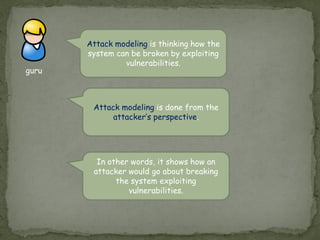
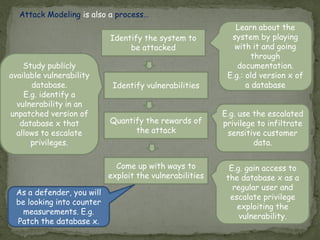
Threat modeling involves identifying potential threats to a system from the defender's perspective in order to mitigate risks. It includes identifying system assets, potential threats using frameworks like STRIDE, and how threats could be realized. Attack modeling takes the attacker's perspective to show how an attacker would exploit vulnerabilities to compromise a system. It involves identifying vulnerabilities, rewards for attacks, and ways to exploit vulnerabilities. While threat modeling is important for protection, attack modeling helps understand attacks more fully to improve security.