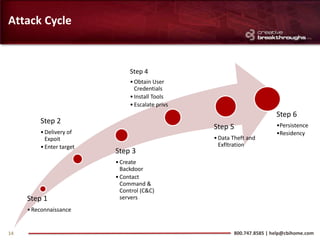
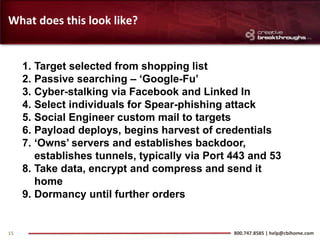
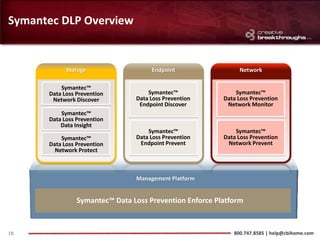
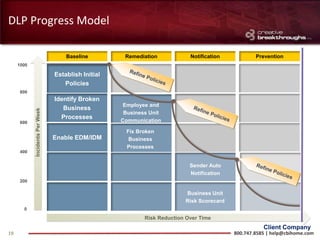
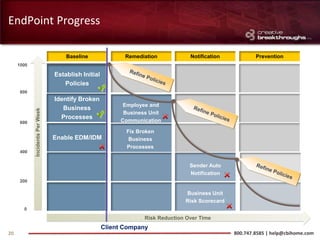
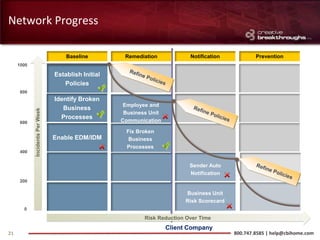
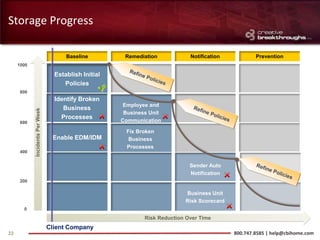
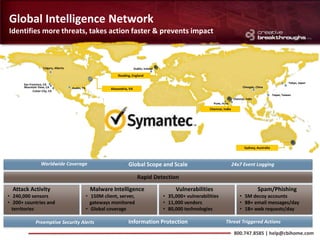
This document provides an overview of advanced persistent threats (APTs) and strategies for addressing them. It summarizes CBI, an IT security solutions provider, and their Enterprise Security Practice. It then details the attack cycle of APTs and provides examples of recent APT attacks. Finally, it recommends deploying Symantec's Data Loss Prevention solution and related services to monitor for data exfiltration and protect confidential information from APTs.