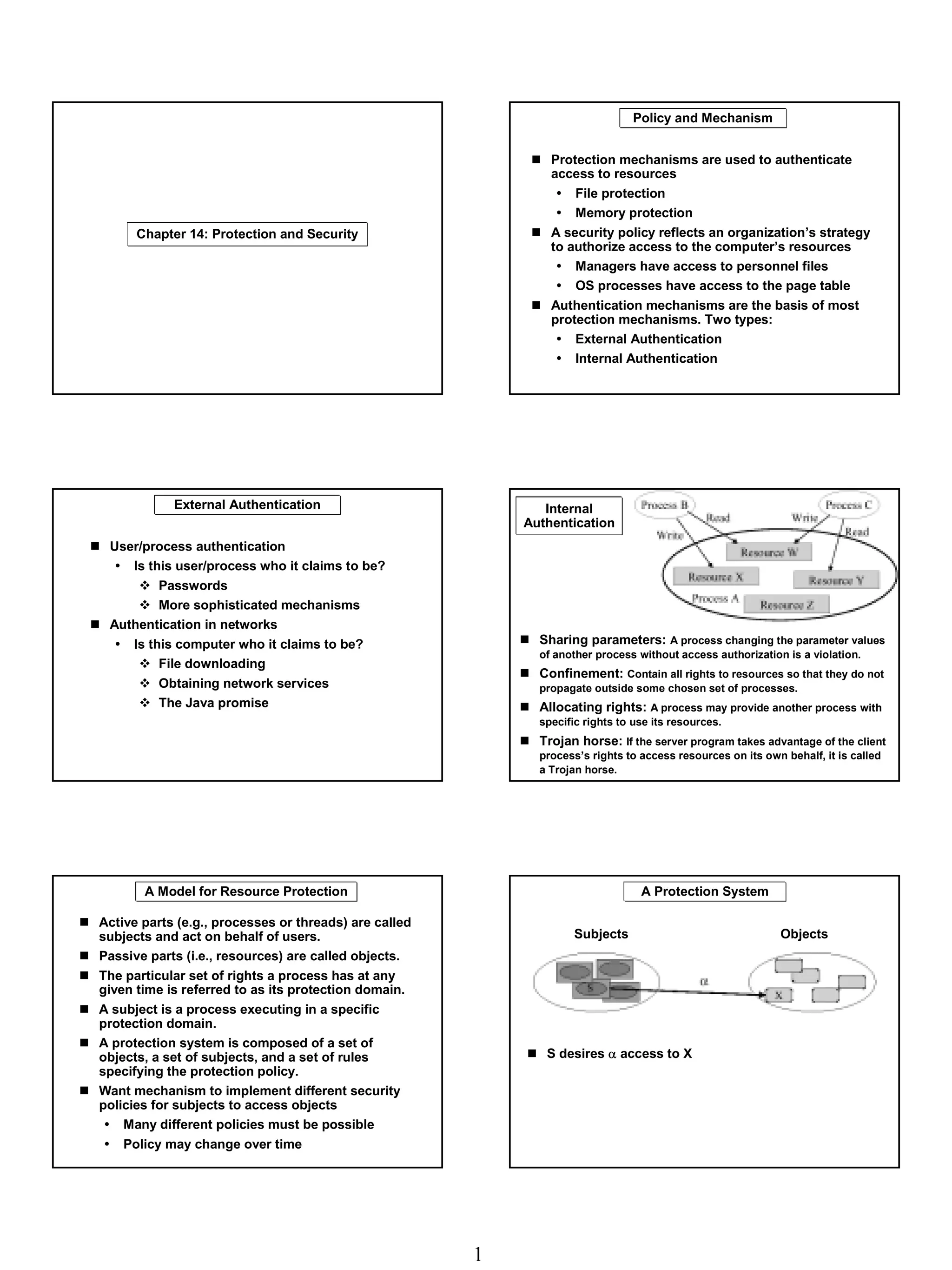
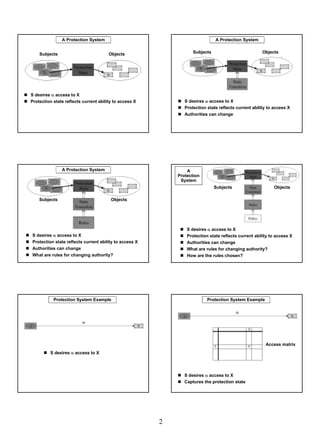
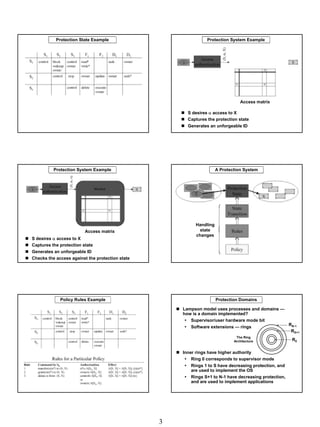
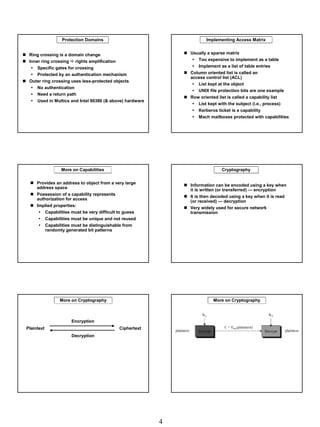
The document discusses computer security policies and protection mechanisms. It covers authentication mechanisms like passwords that verify a user's identity. Protection mechanisms use a security policy to control access to resources based on authentication. The core components are subjects like processes that act on behalf of users, and objects like files that are accessed. Protection systems define rules for what access subjects have to objects.