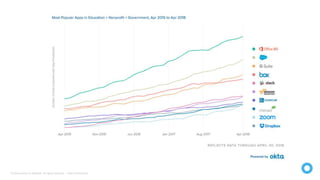
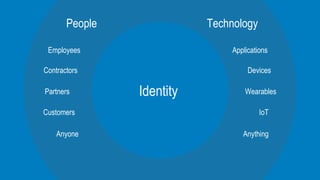
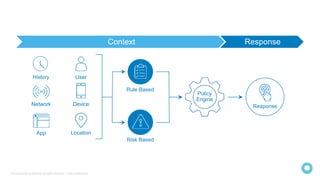
The document discusses how identity and access management solutions from Okta can help organizations accelerate their digital transformations by securely connecting internal and external users to any application or device. It explains Okta's identity solutions which use policy engines and multi-factor authentication methods to securely verify user identities based on the context of device, user, location, network and application in order to mitigate risks and ensure compliance.