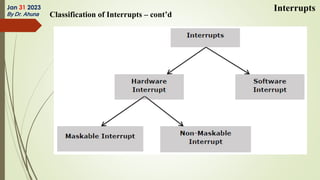
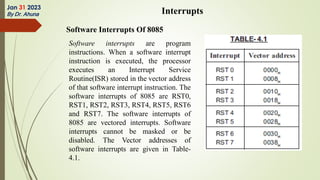
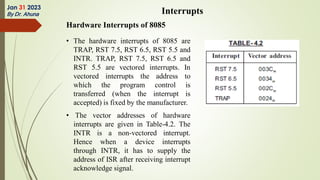
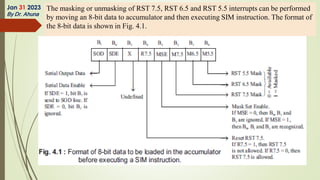
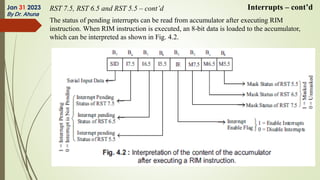
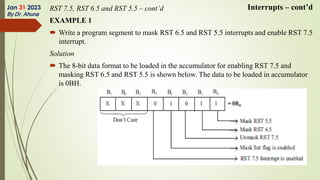
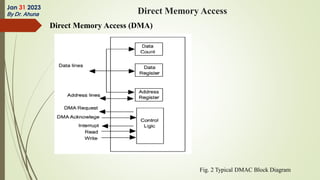
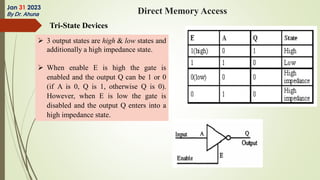
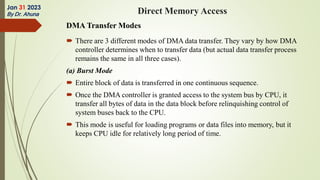
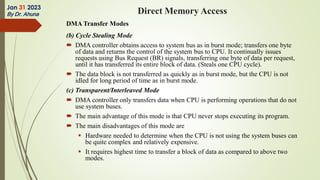
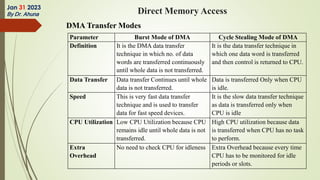
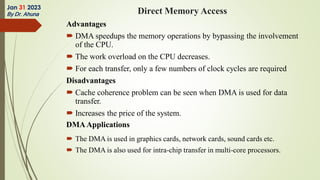
The document discusses interrupts in microprocessor systems, specifically focusing on the 8085 architecture, which employs interrupts for managing data transfer between peripherals and the processor. It categorizes interrupts into hardware and software, maskable and non-maskable, and vectored and non-vectored types, detailing their operation, control, and servicing through interrupt service routines (ISRs). Additionally, it explains Direct Memory Access (DMA) as a method of transferring data between peripherals and memory without processor intervention, using DMA controllers.
![Topic 5a
[1] 8085 Interrupts
[2] Direct Memory Access
Feb 06 2024
By Dr. Ahuna](https://image.slidesharecdn.com/5a8085interruptsdirectmemoryaccesspptx-240901110116-183f9240/75/5a_8085-Interrupts-Direct-Memory-Access_pptx-pdf-1-2048.jpg)