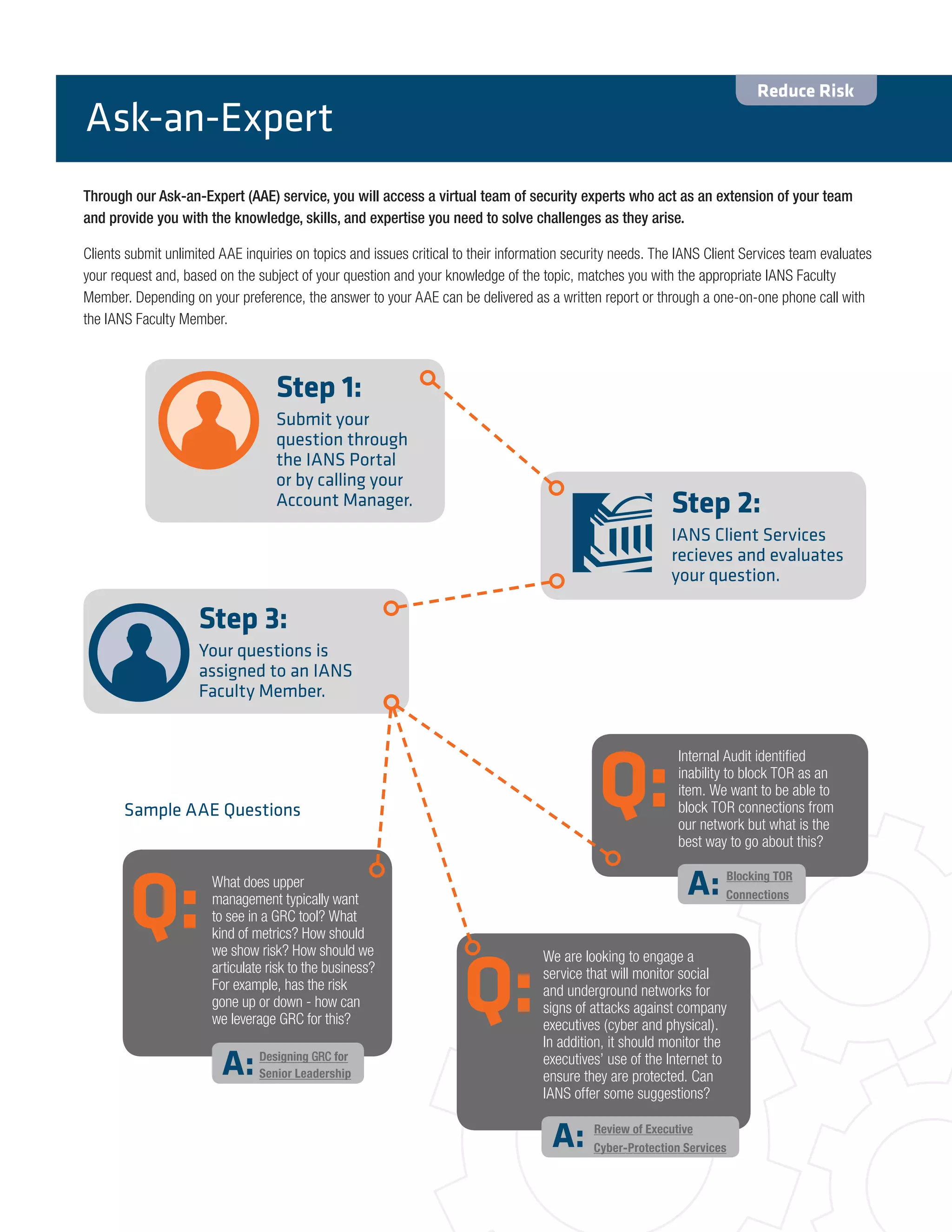
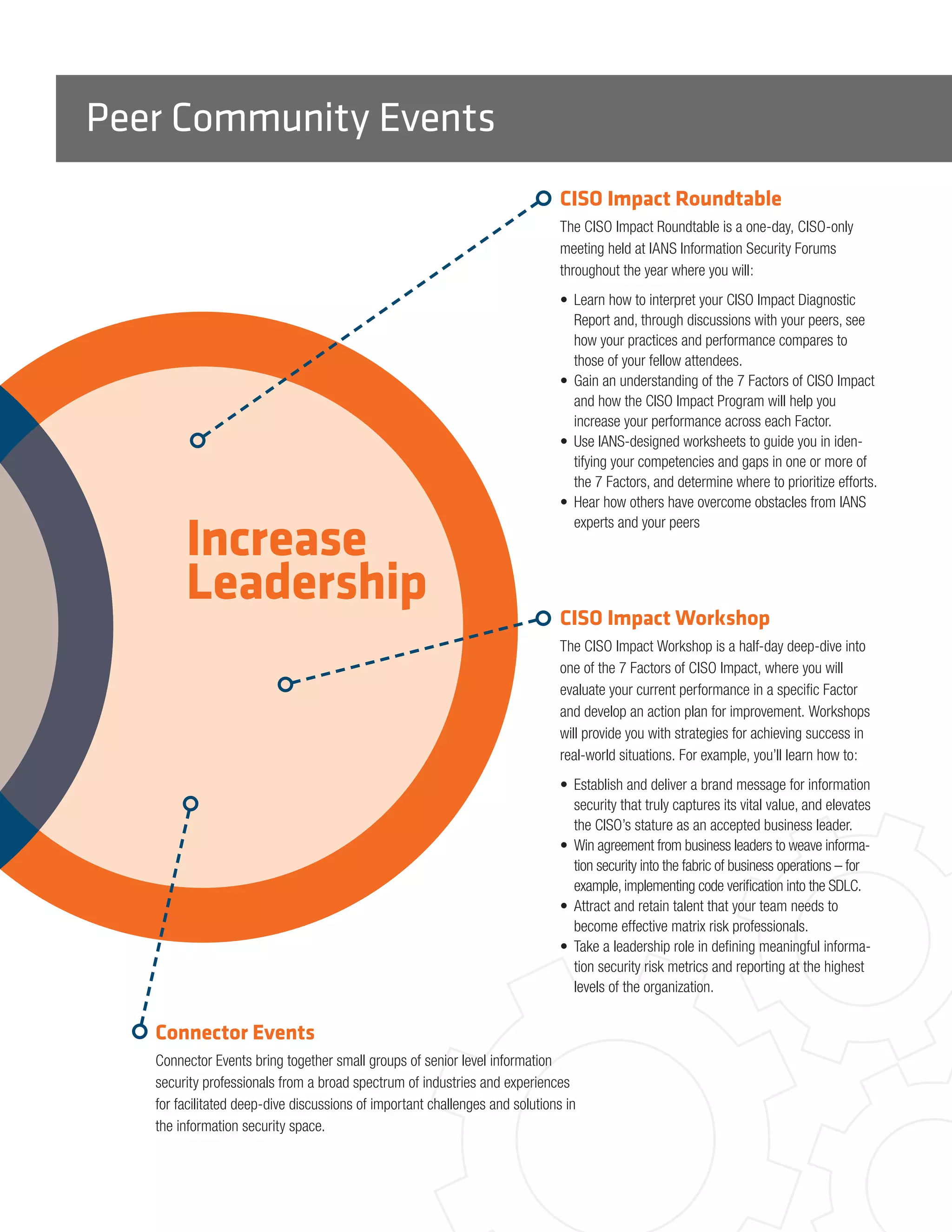
The document provides information about IANS, a decision support service that helps information security professionals reduce risk and increase leadership within their organizations. IANS offers various resources to support security teams, including research, consulting, peer community events, and access to a faculty of security experts. IANS was founded in 2001 and has supported thousands of security teams on current threats, technologies, and risk mitigation strategies. IANS focuses exclusively on security issues and differentiates itself through its depth of knowledge, practitioner expertise over analyst perspectives, and level of peer interaction opportunities provided to clients. IANS aims to help security professionals reduce risk through expert advice and make better decisions, as well as increase leadership through assessments, workshops and frameworks.