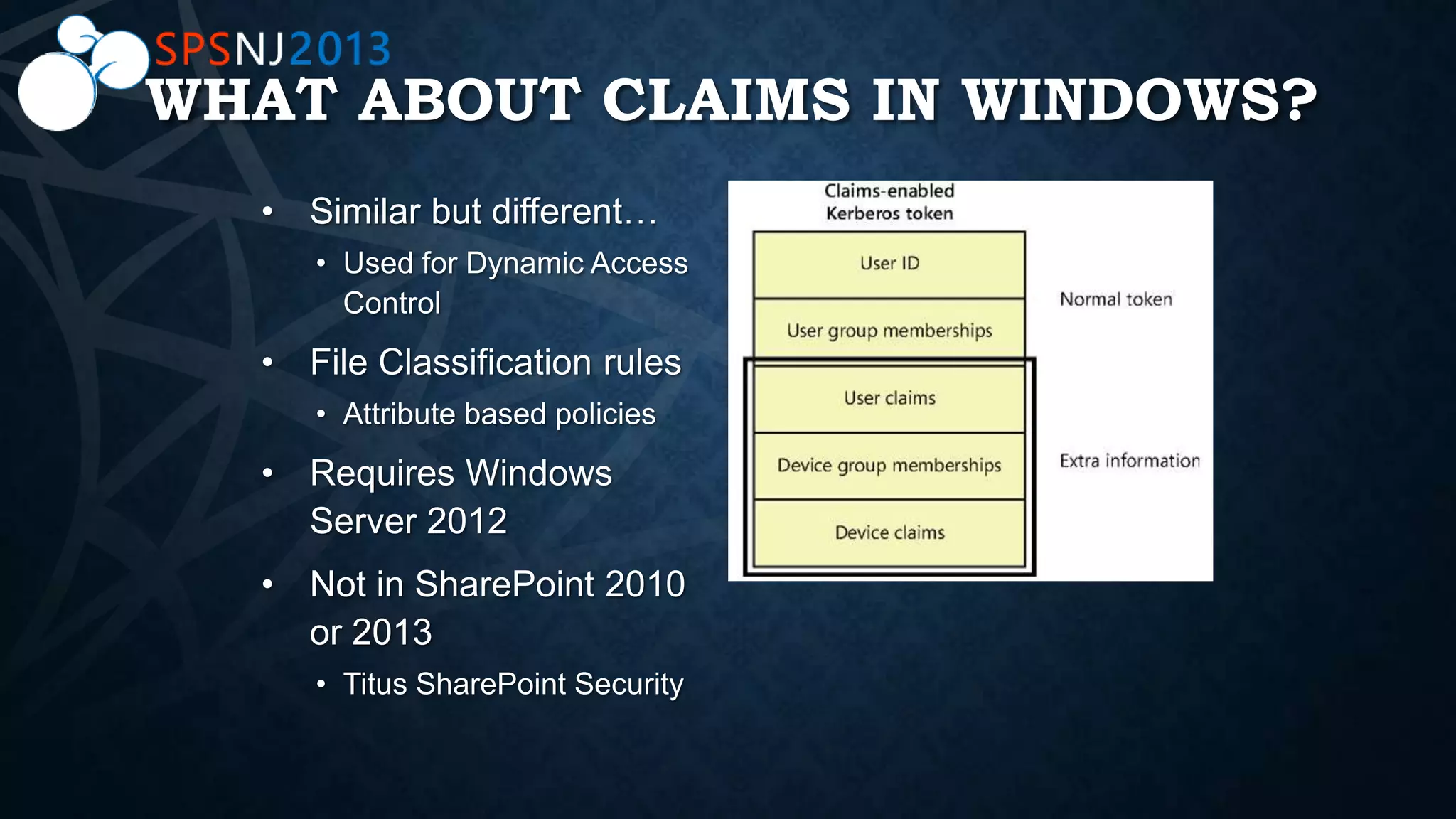
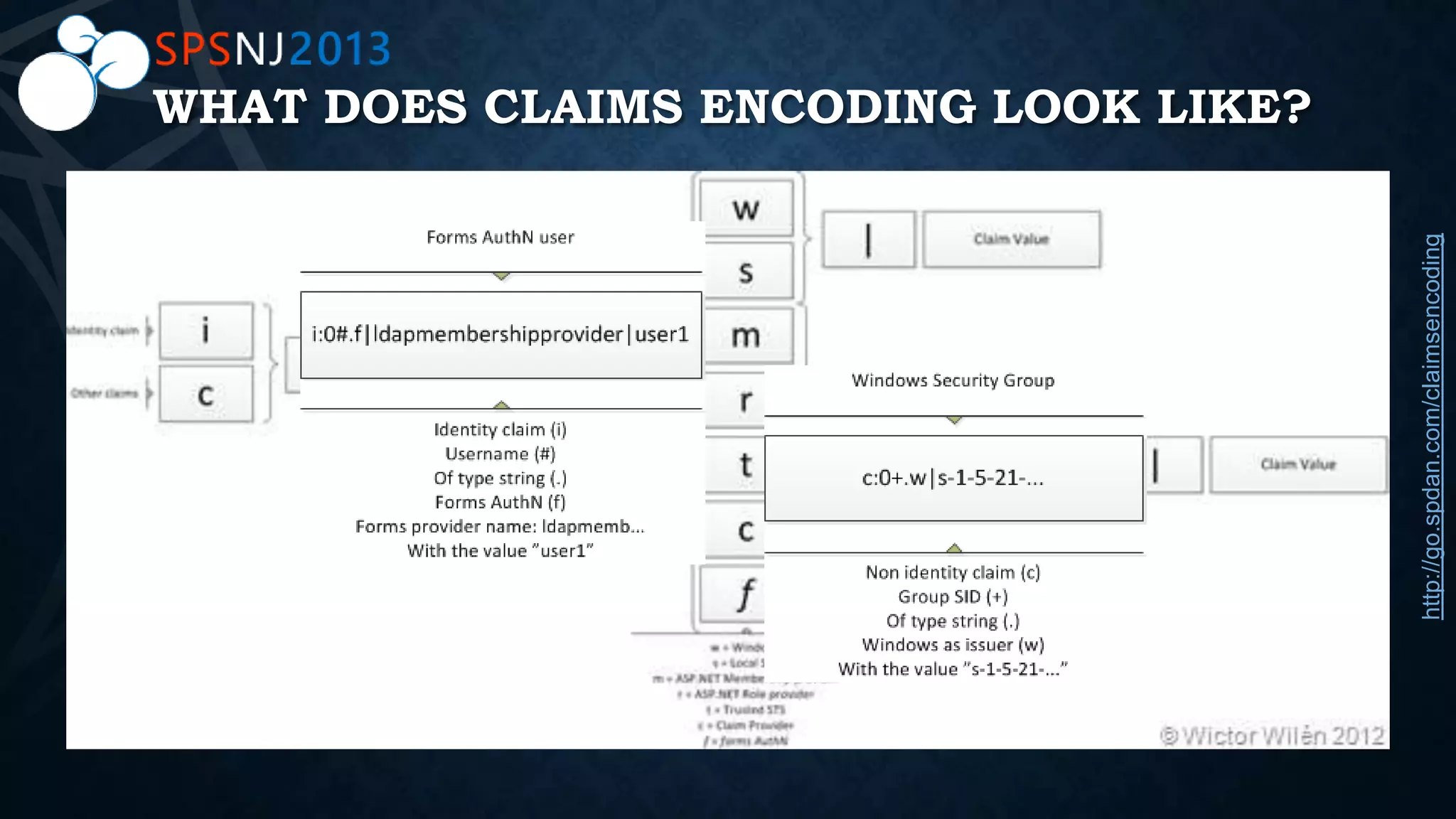
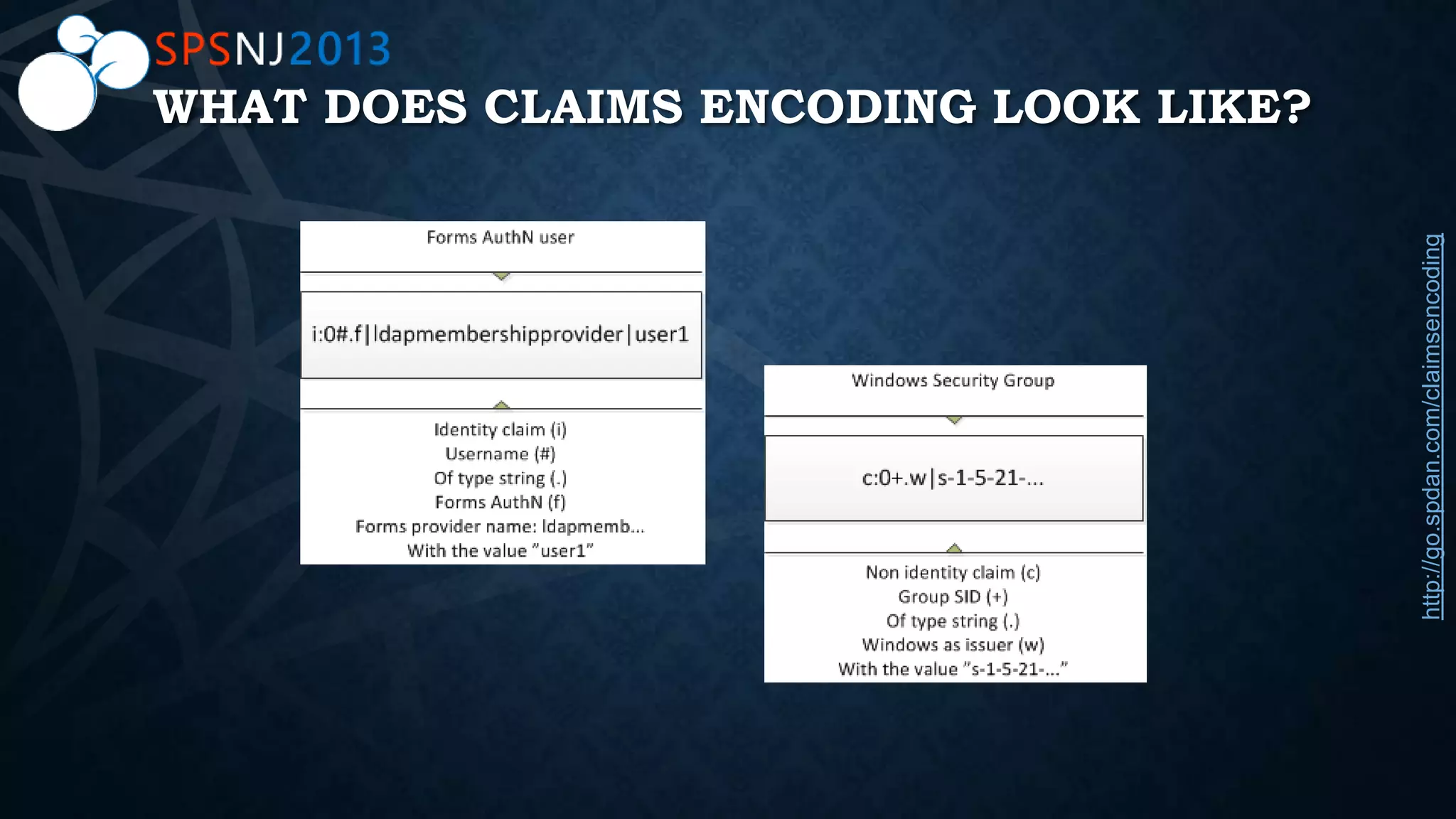
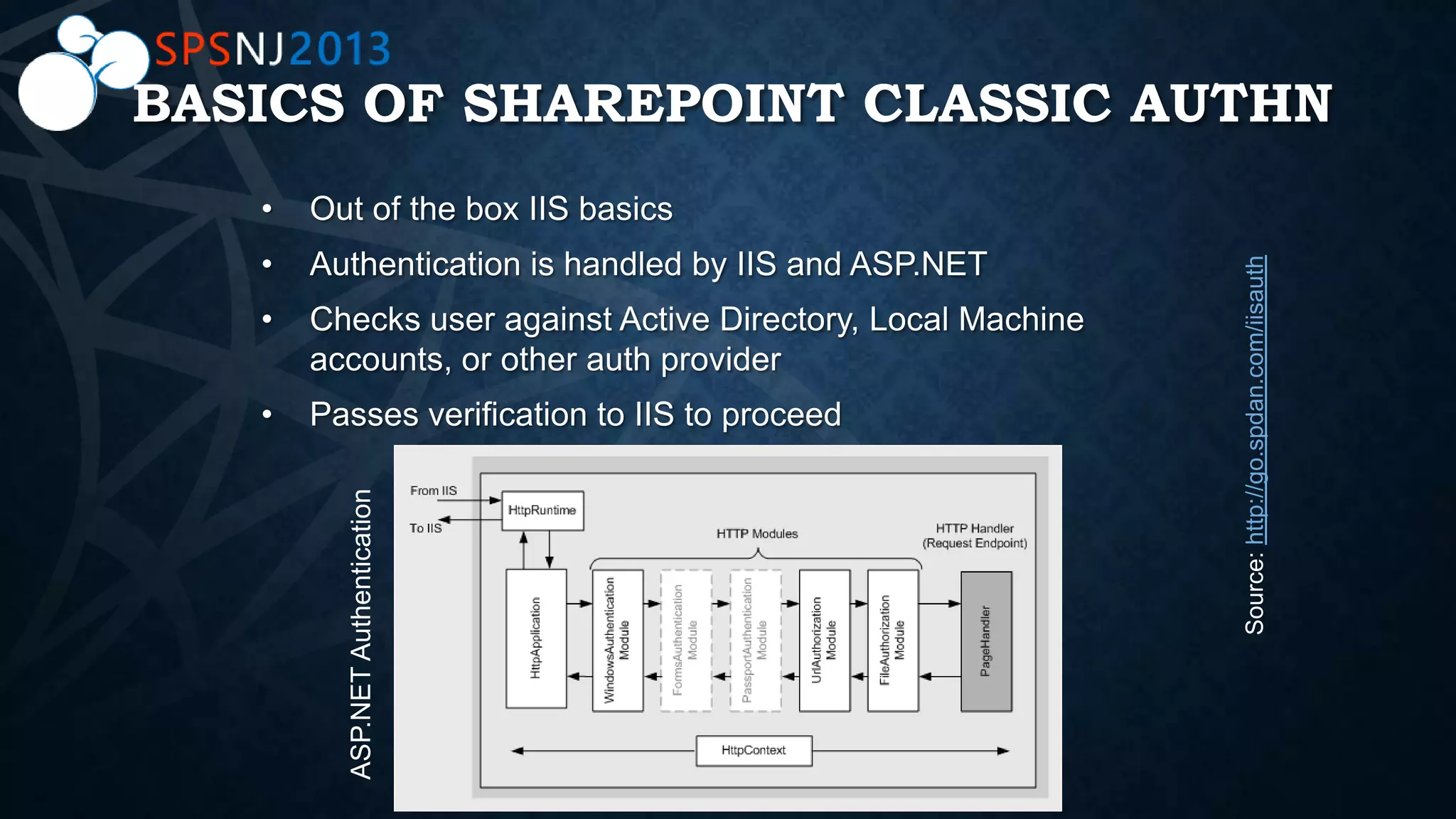
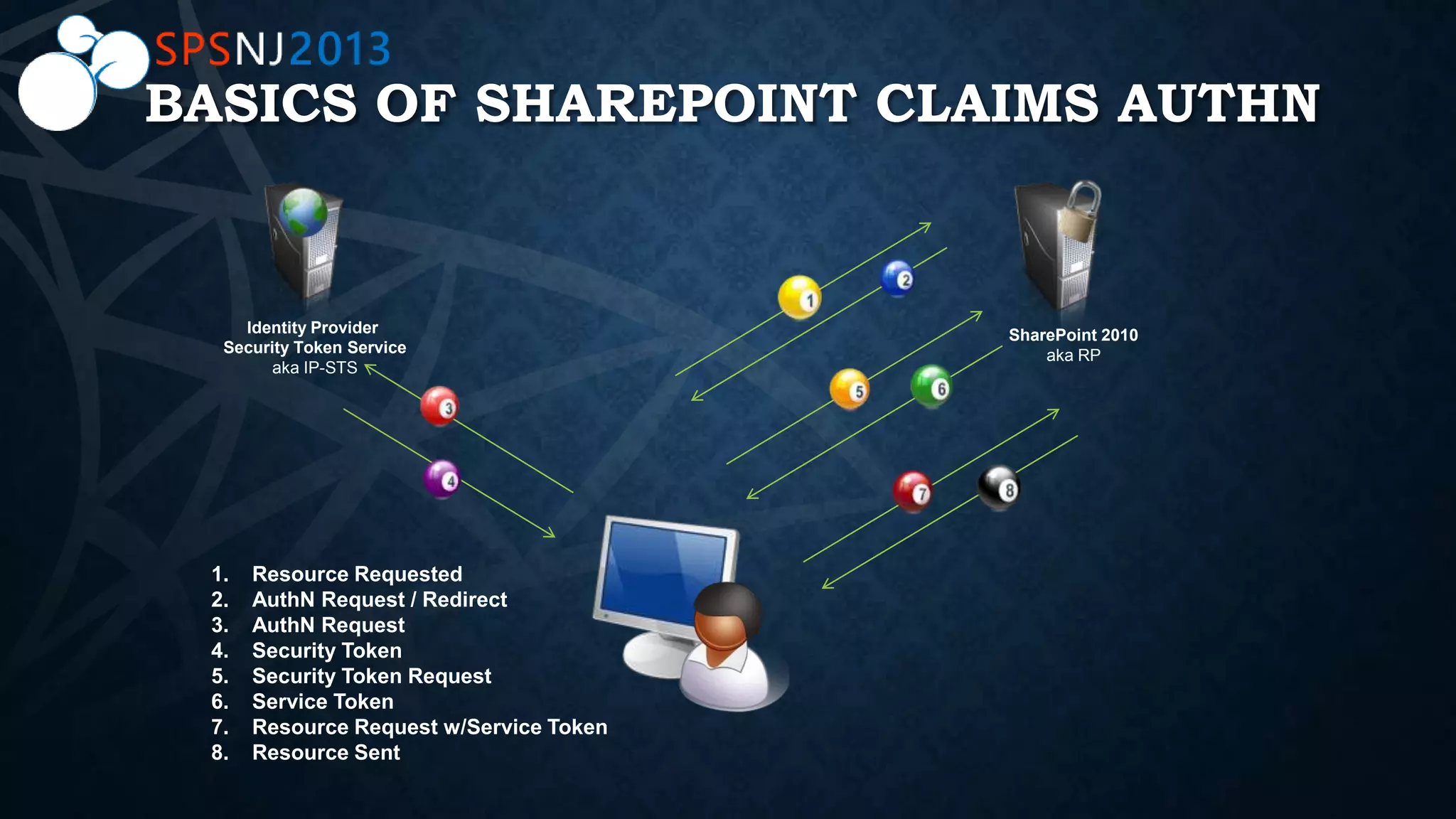
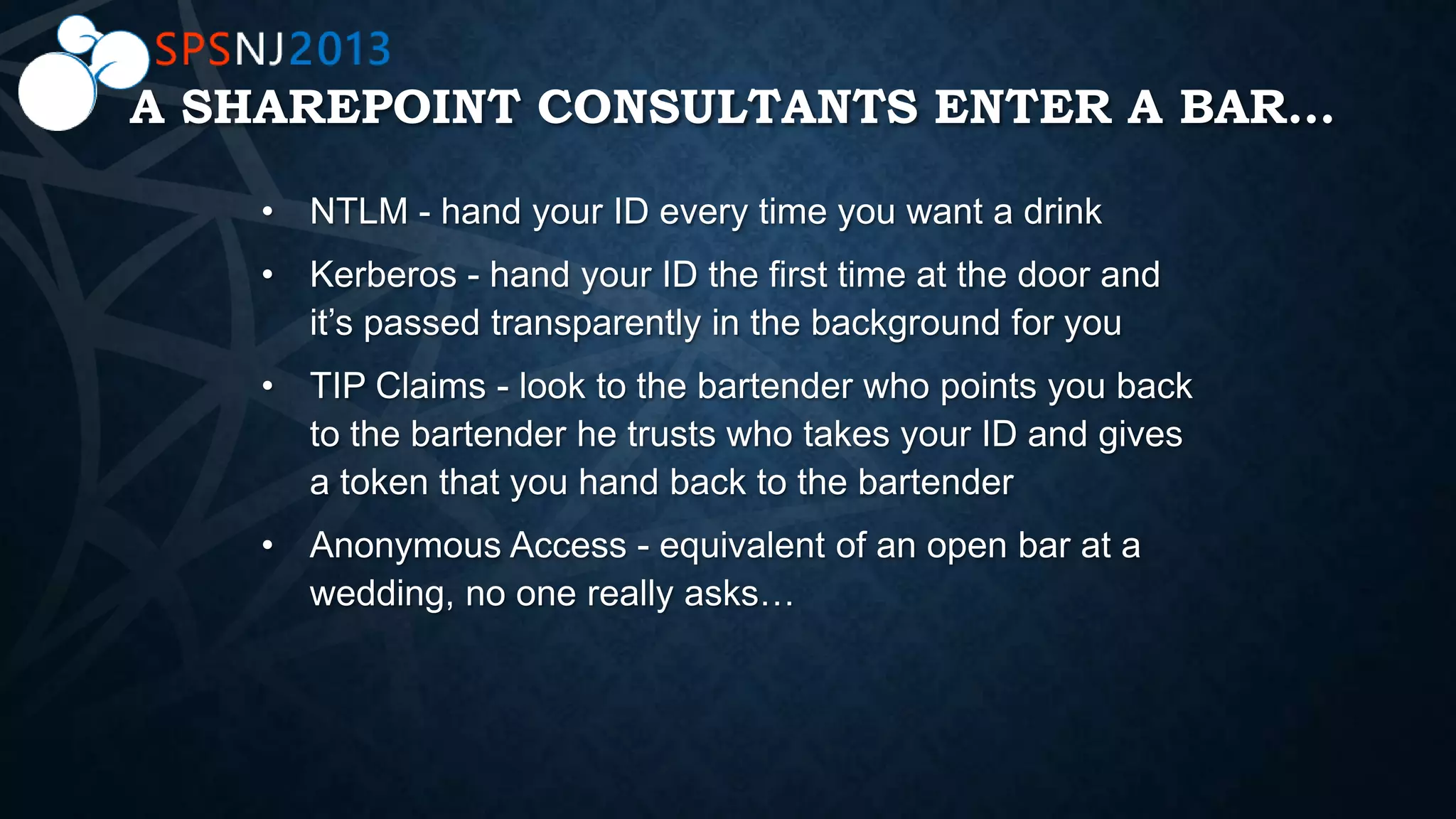
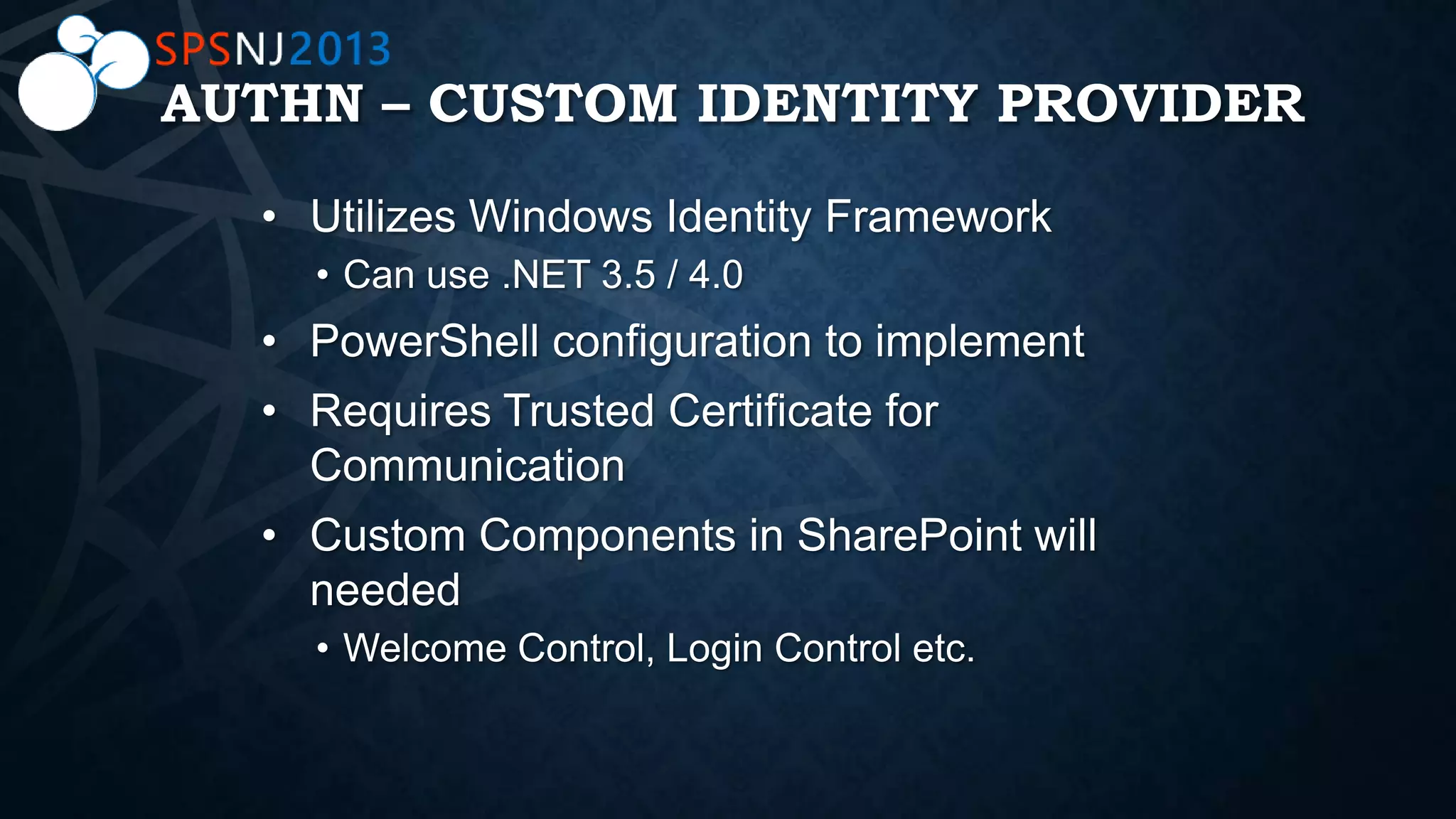
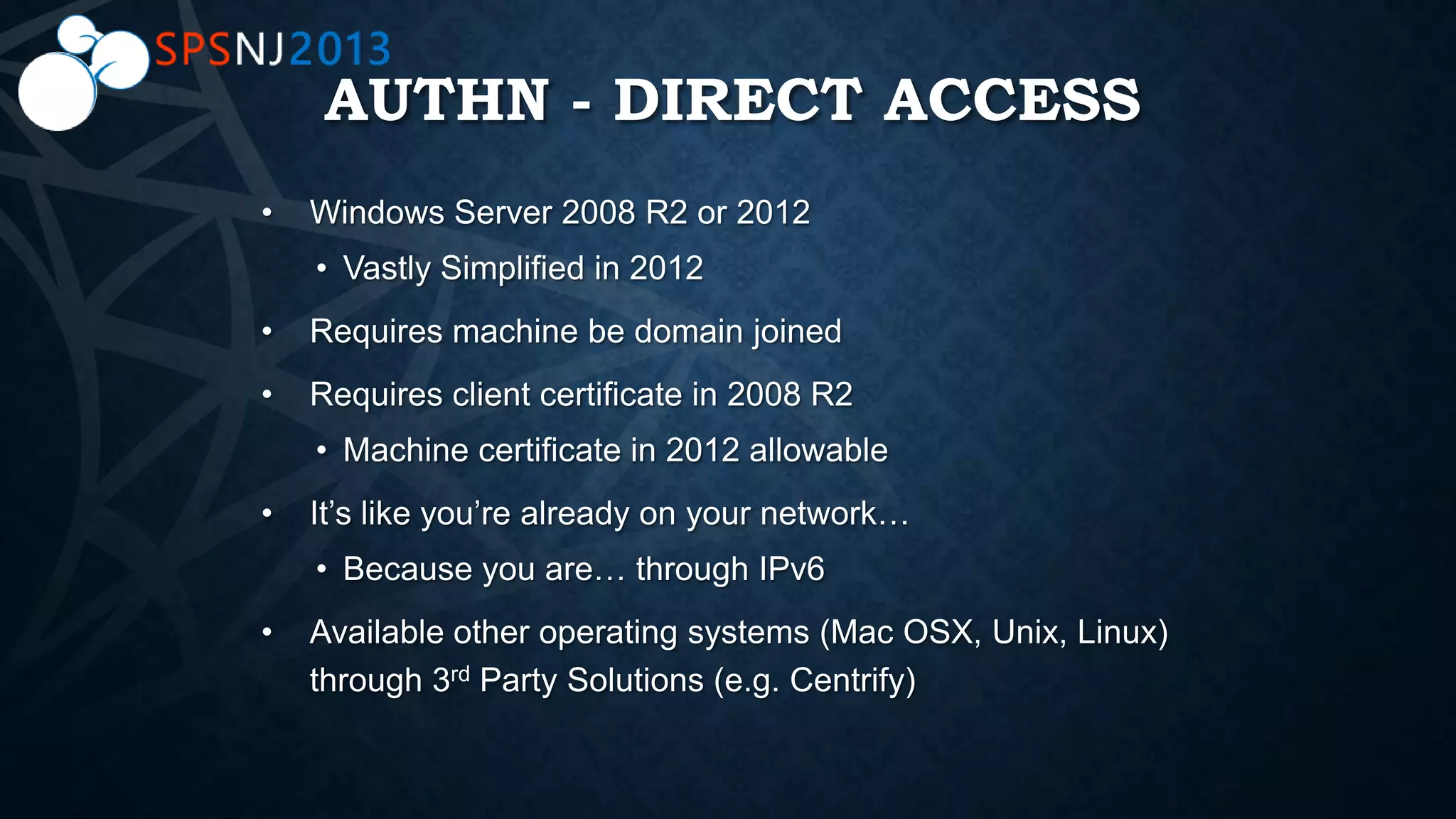
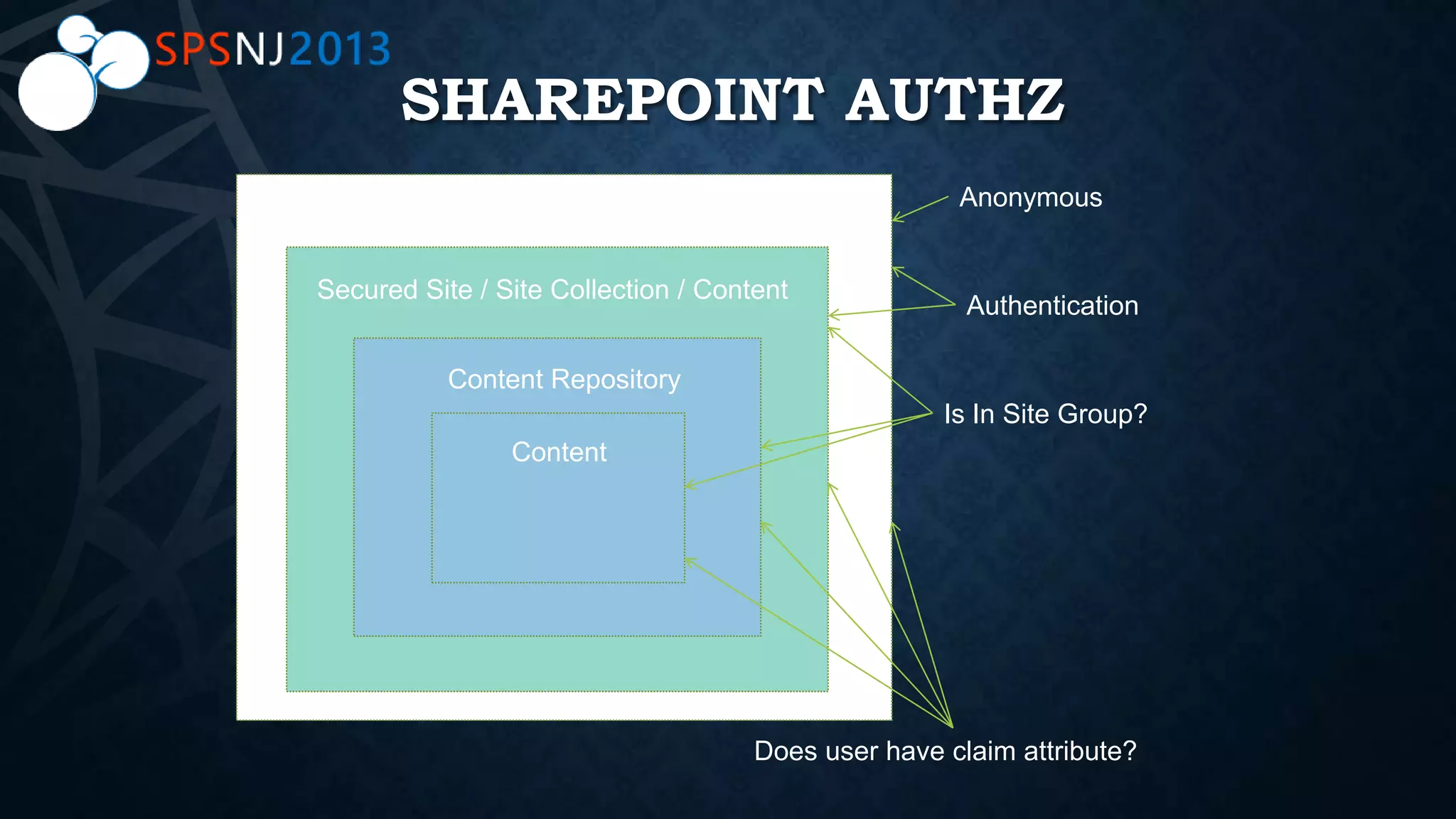
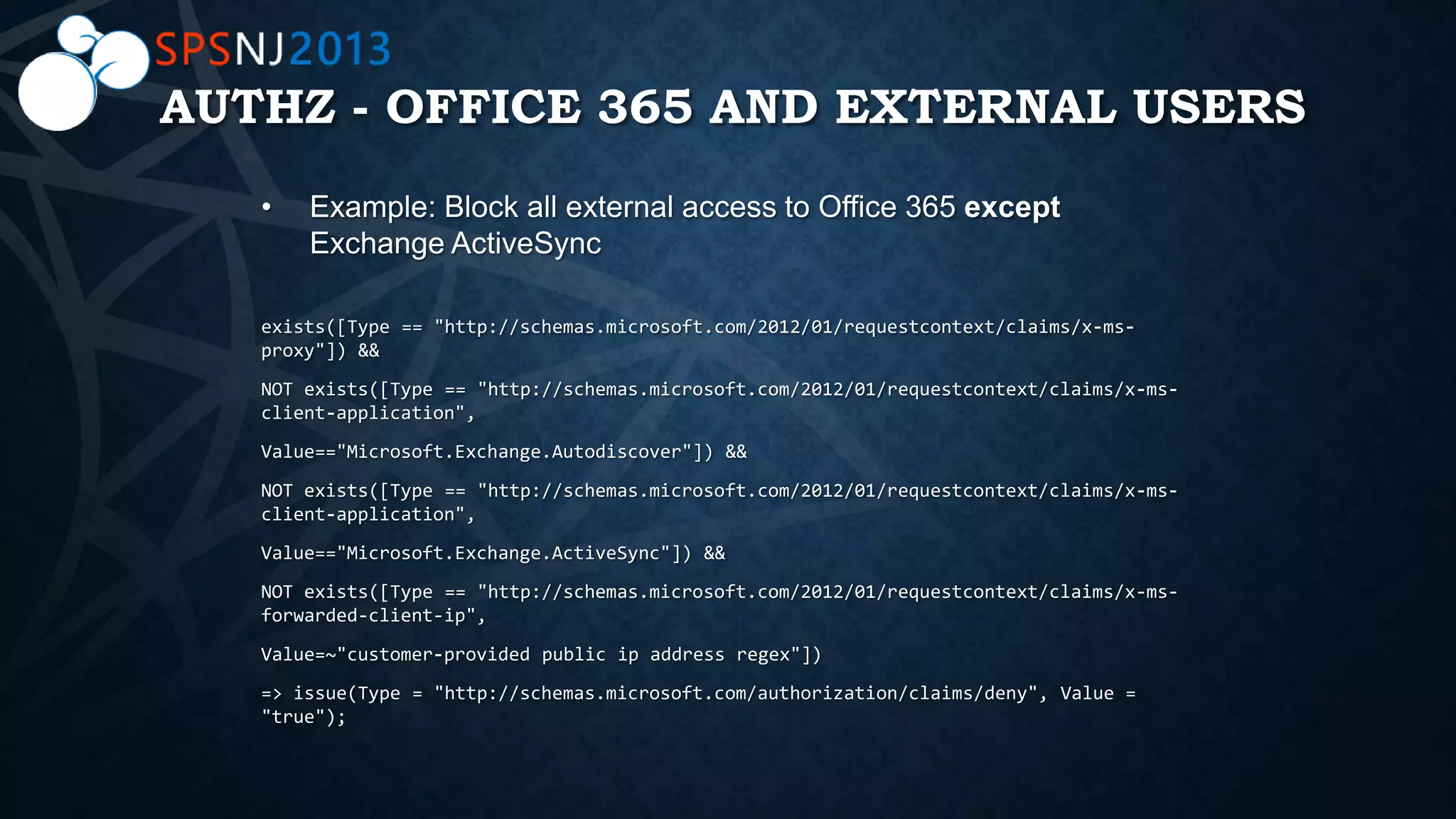
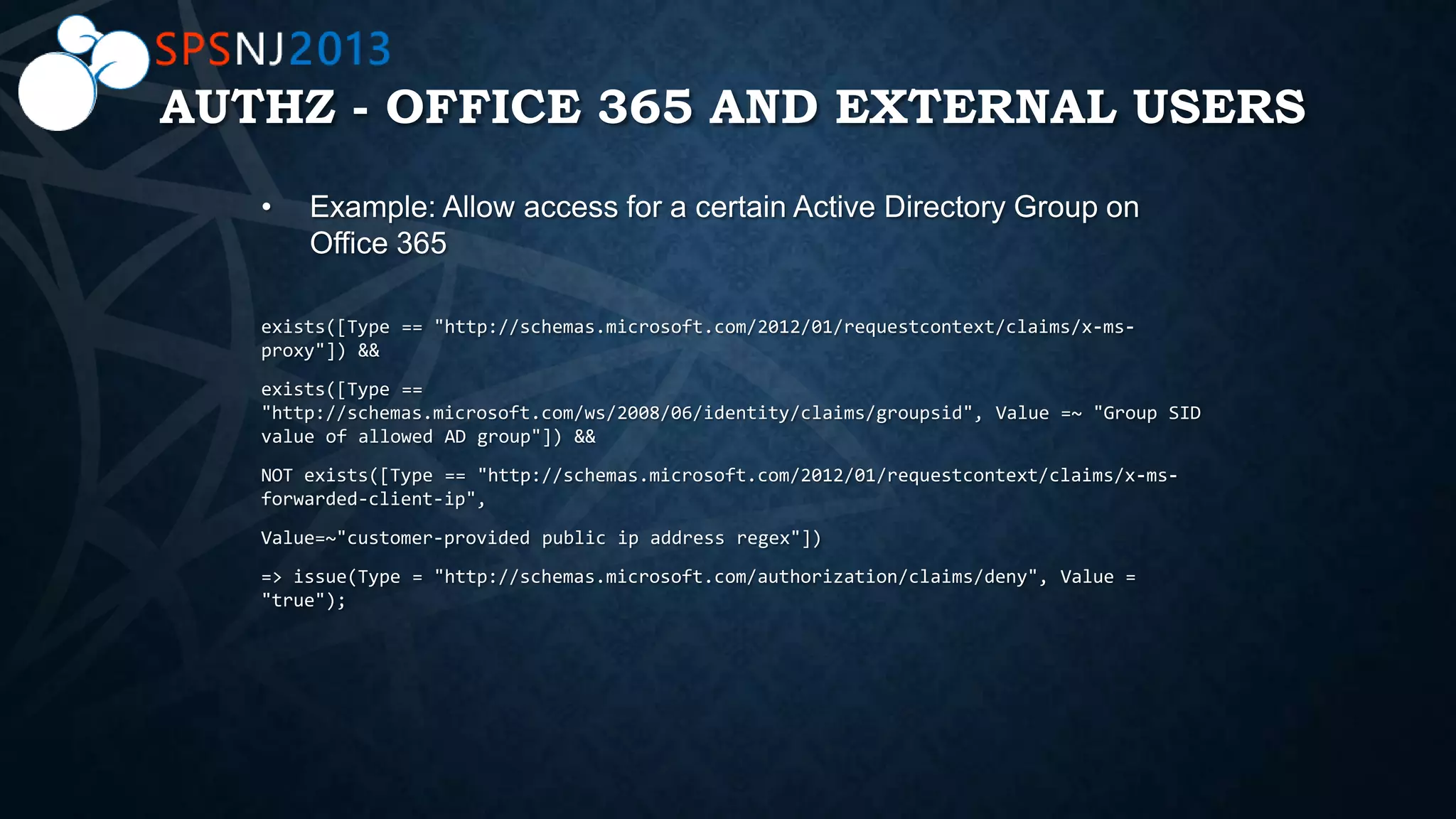
The document outlines a presentation on authentication, authorization, and identity topics within SharePoint, conducted by Scott Hoag and Dan Usher for the Princeton SharePoint User Group. The session includes discussions on security concerns, different authentication methods, claims-based authentication, and best practices for limiting access control. Additionally, there are event details, sponsor mentions, and an encouragement for participants to interact and engage with the content and sponsors.