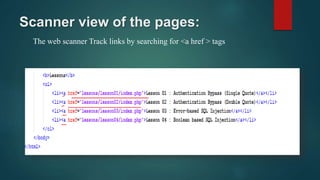
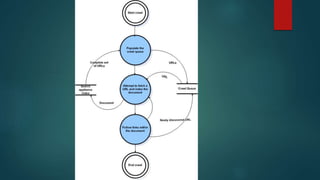
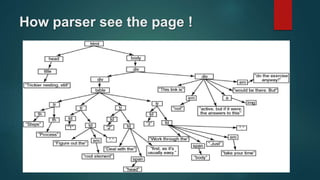
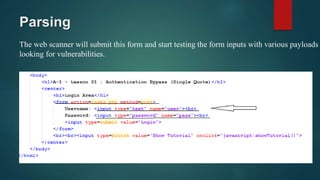
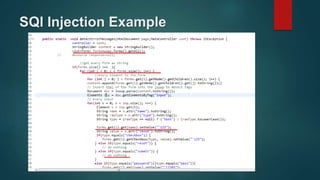
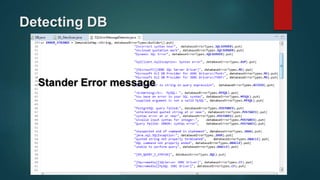
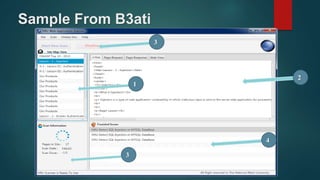
Web application scanners crawl a web application to locate vulnerabilities by simulating attacks. They work by supporting various protocols, crawling and parsing content, testing for vulnerabilities, and generating reports. While scanners help find issues, developers should focus on learning secure coding practices to build applications securely from the start.