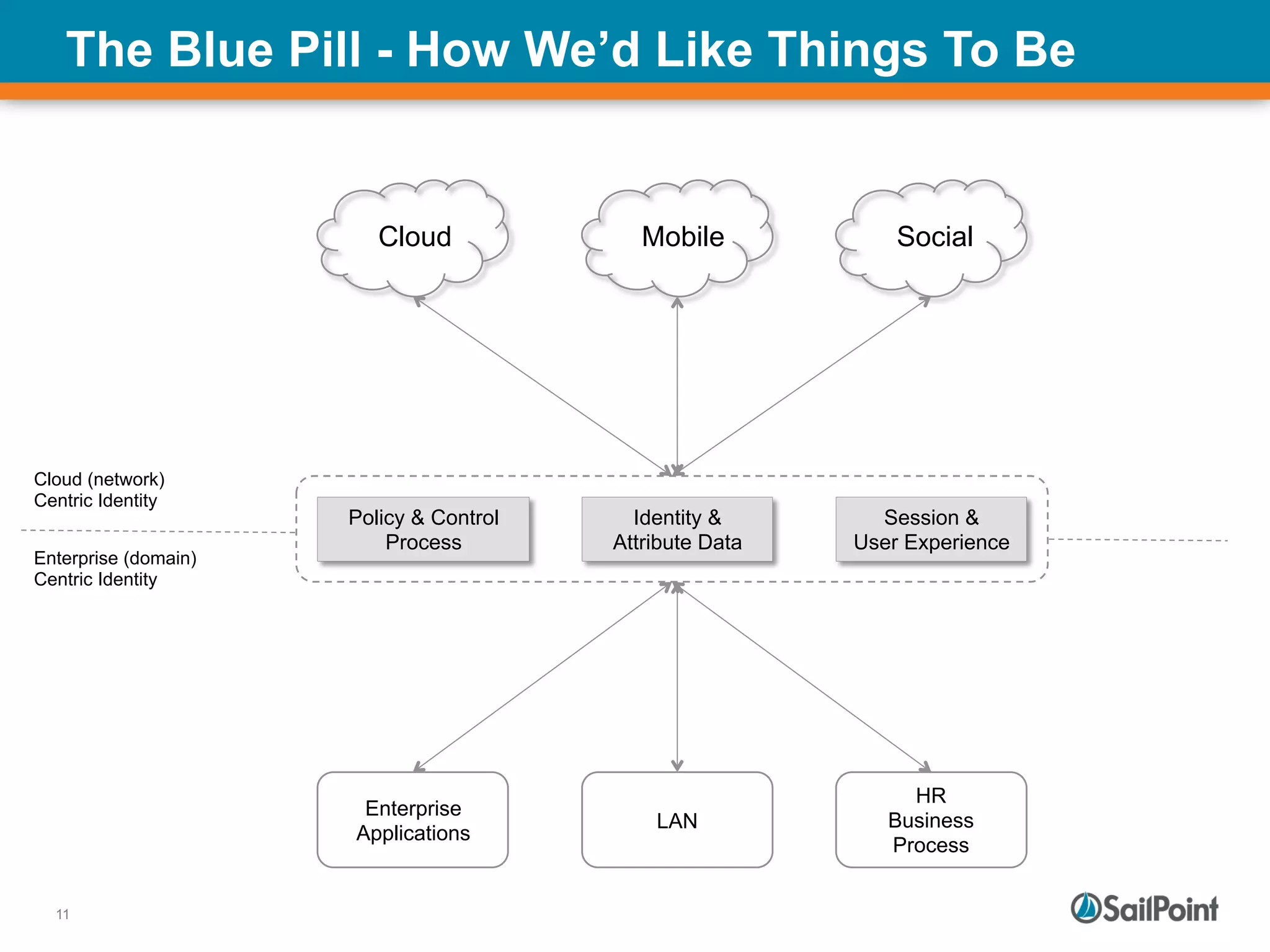
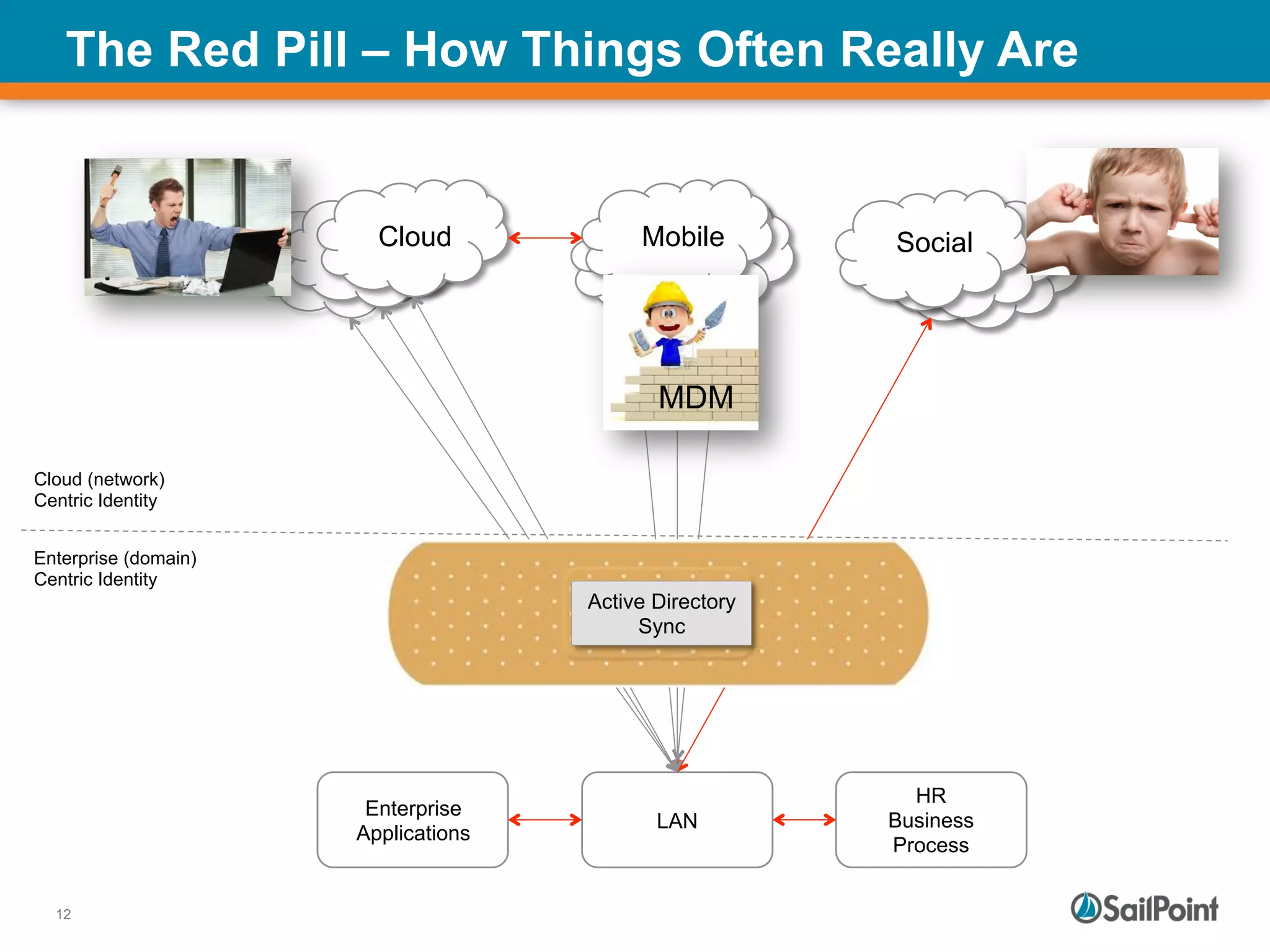
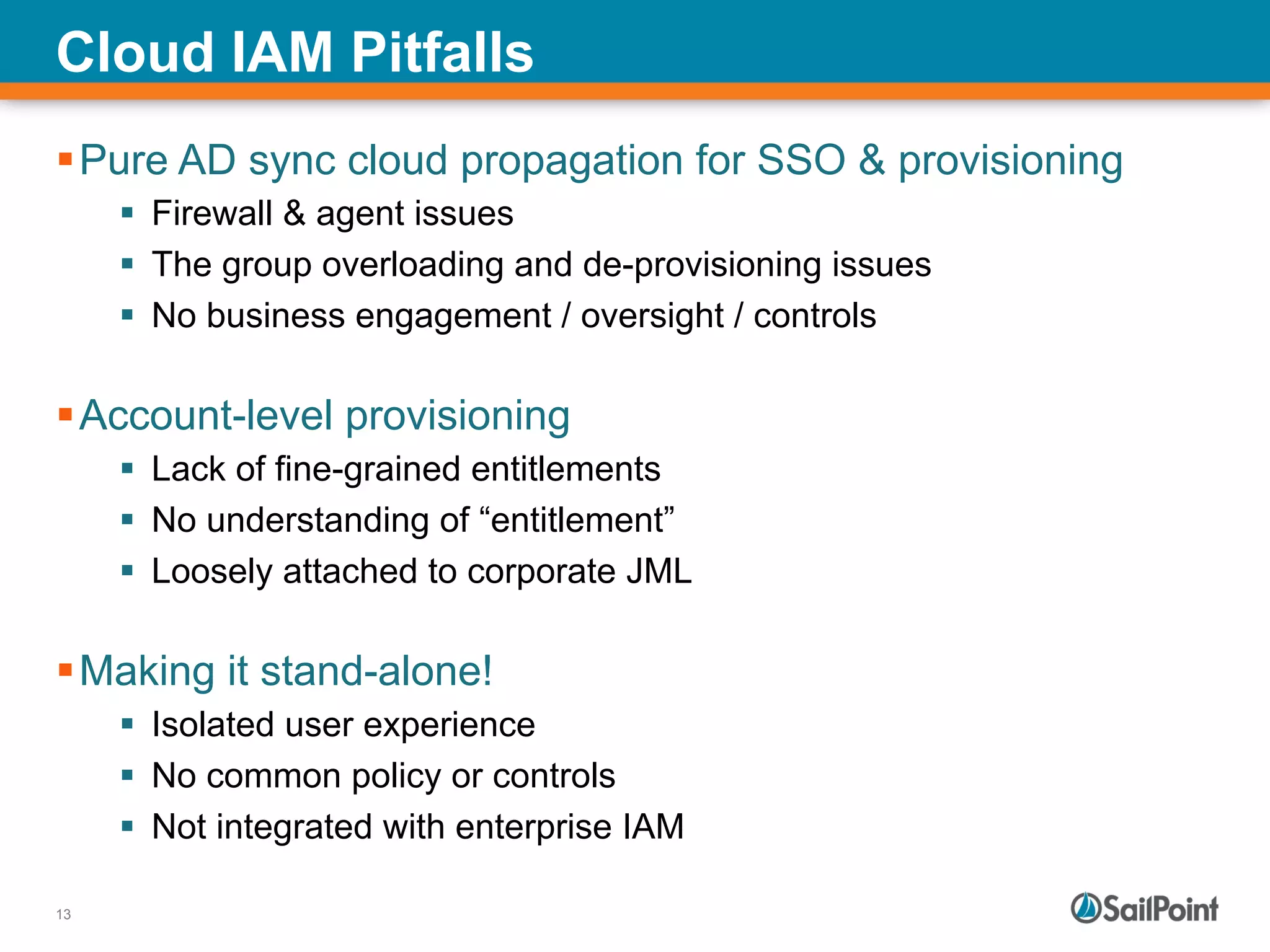
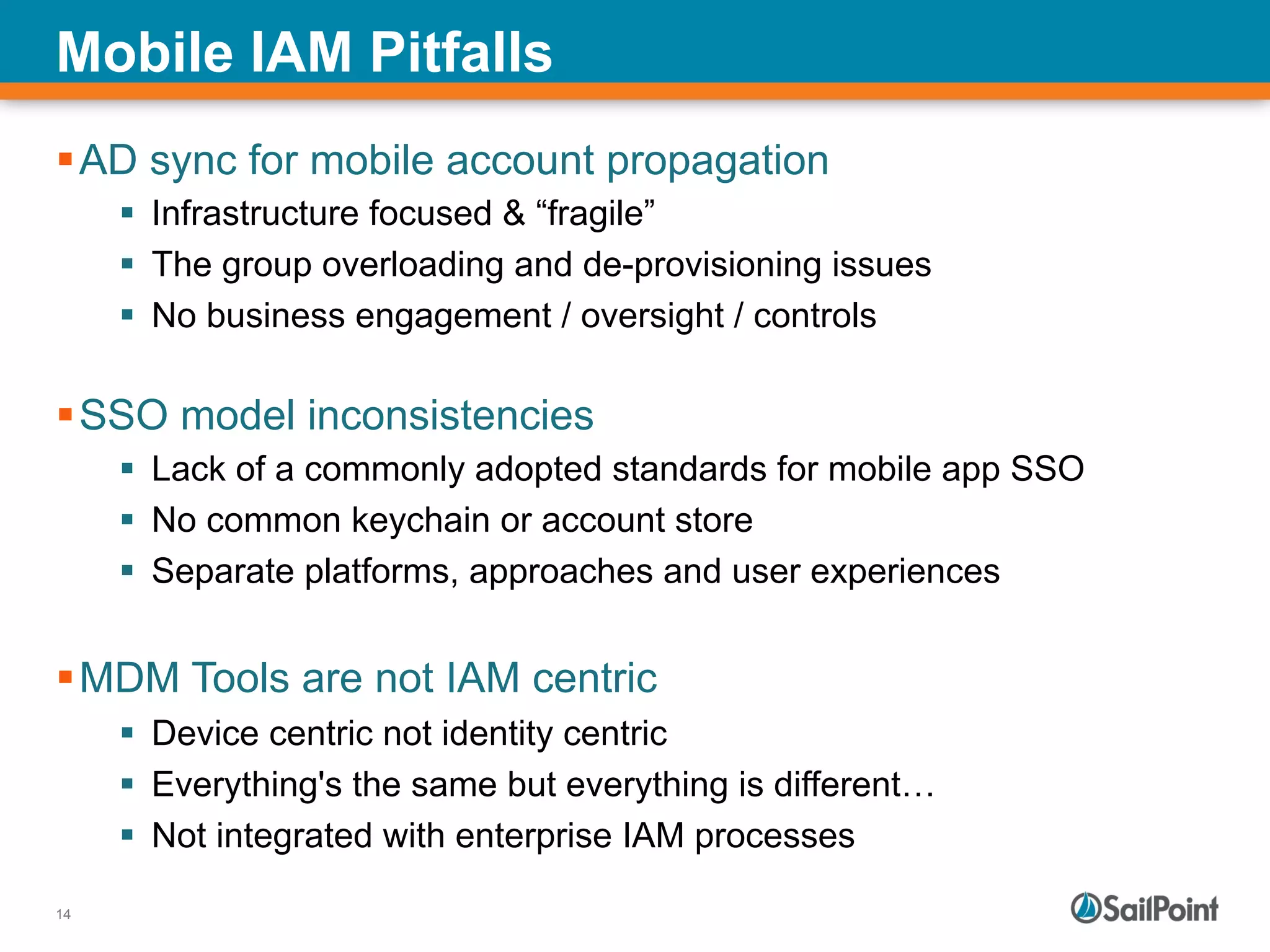
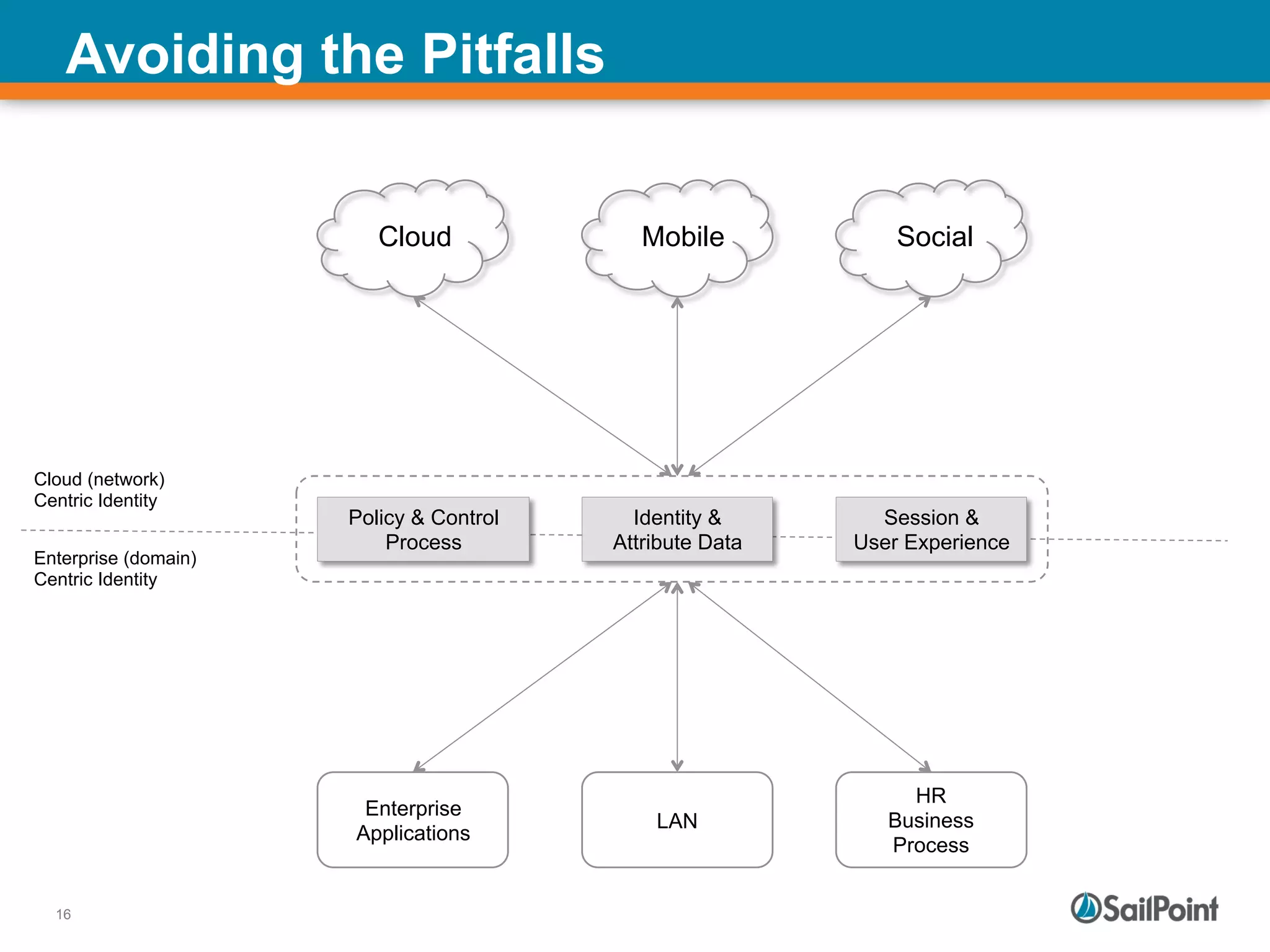
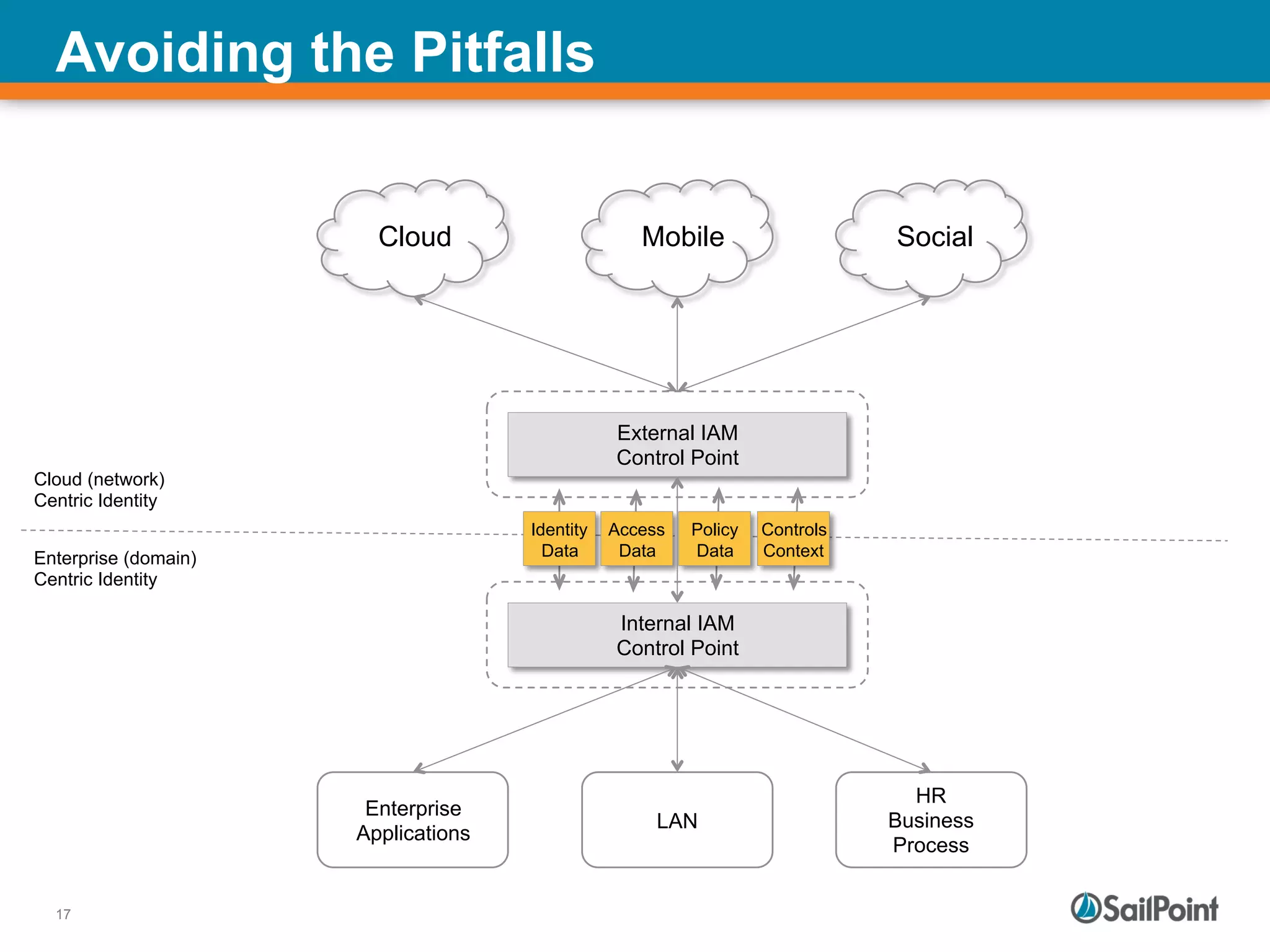
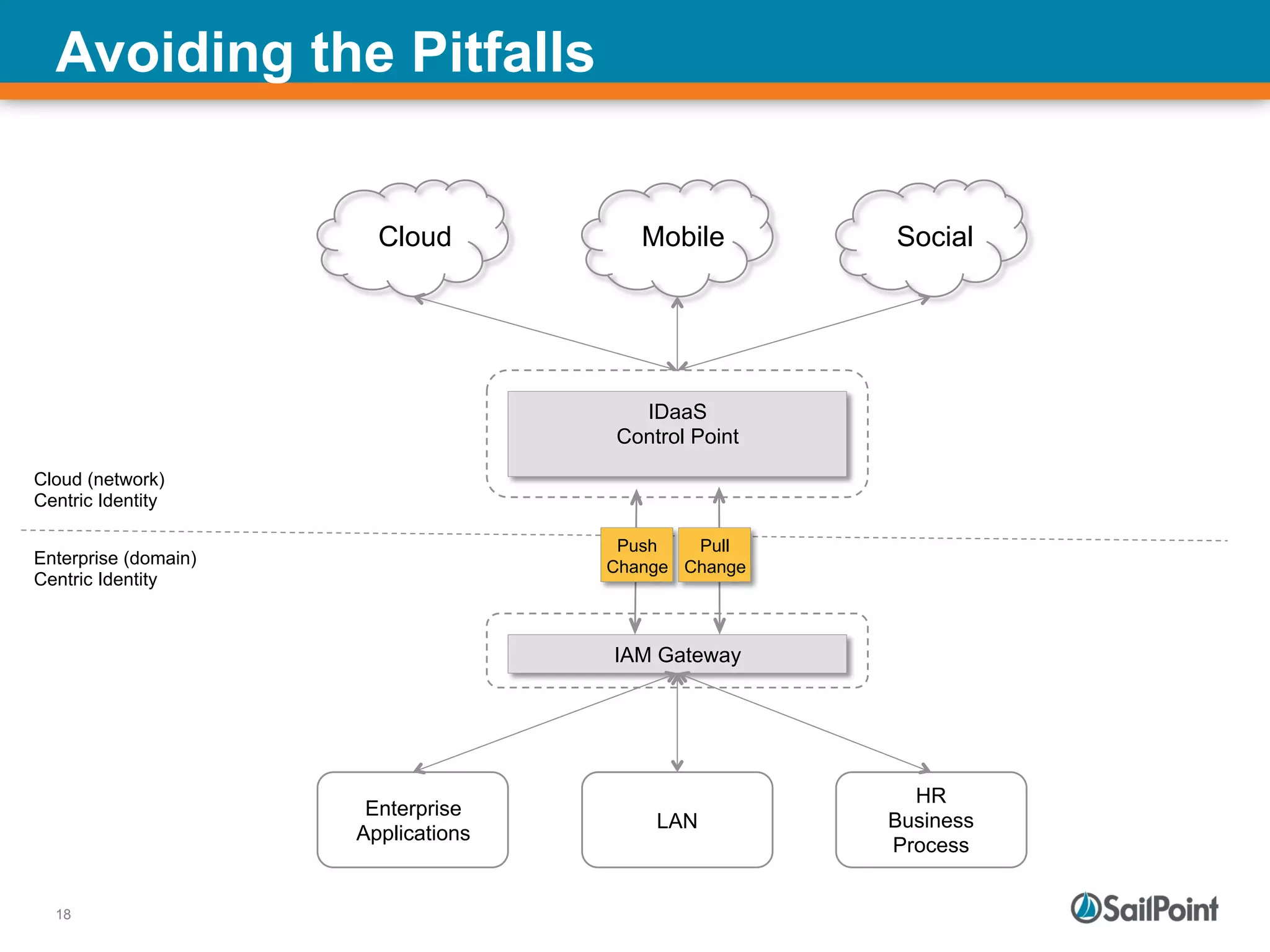
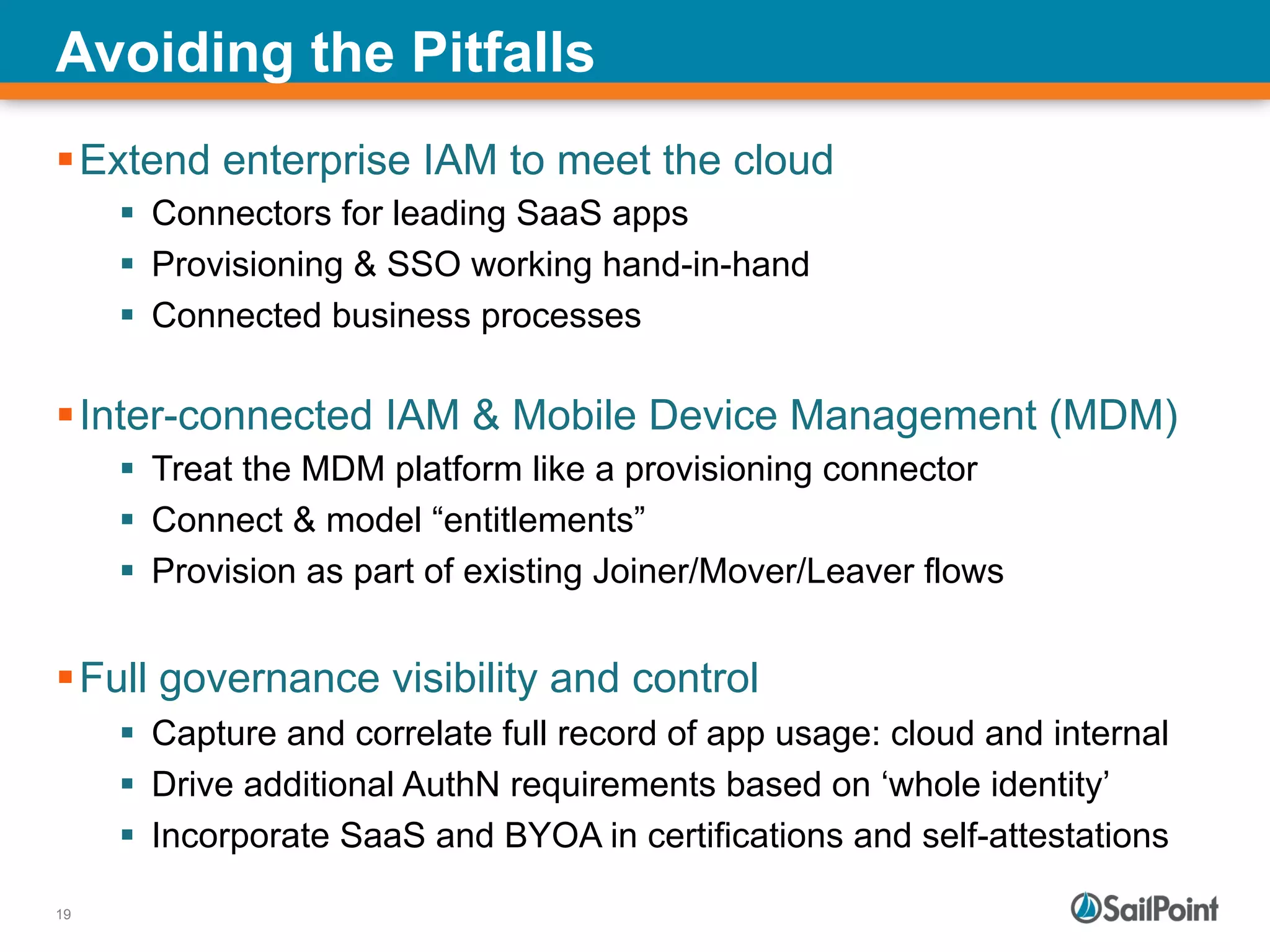
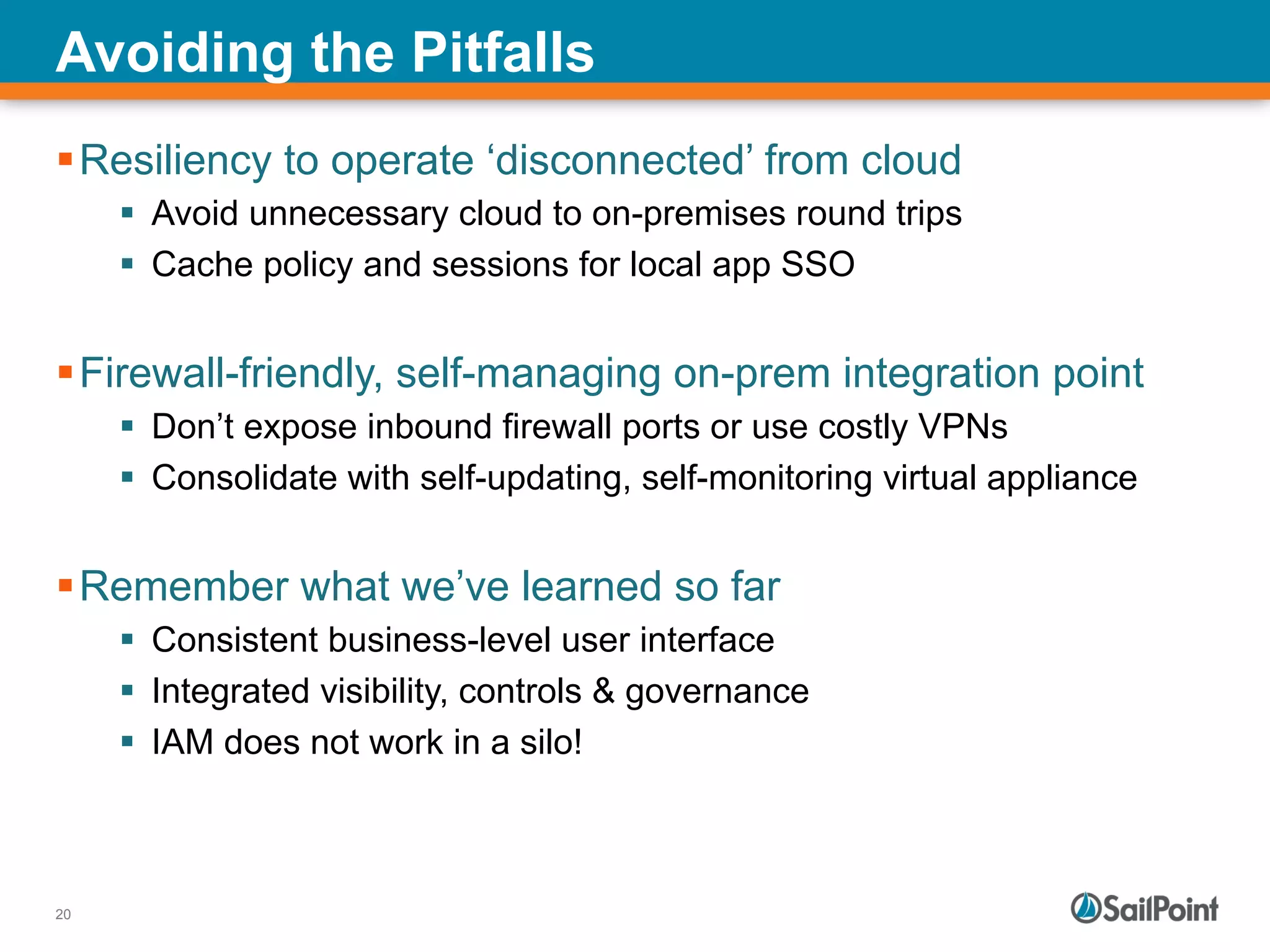
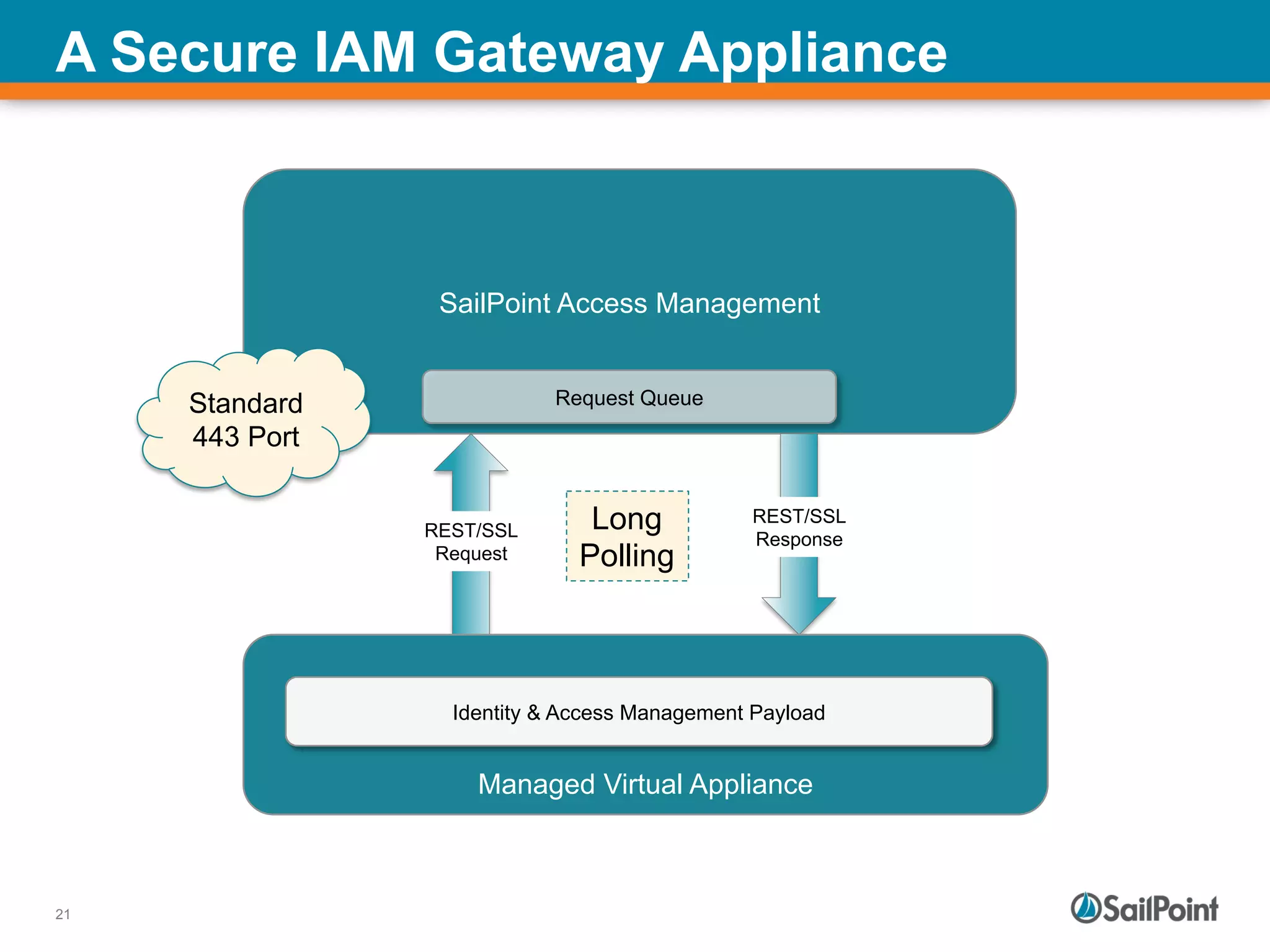
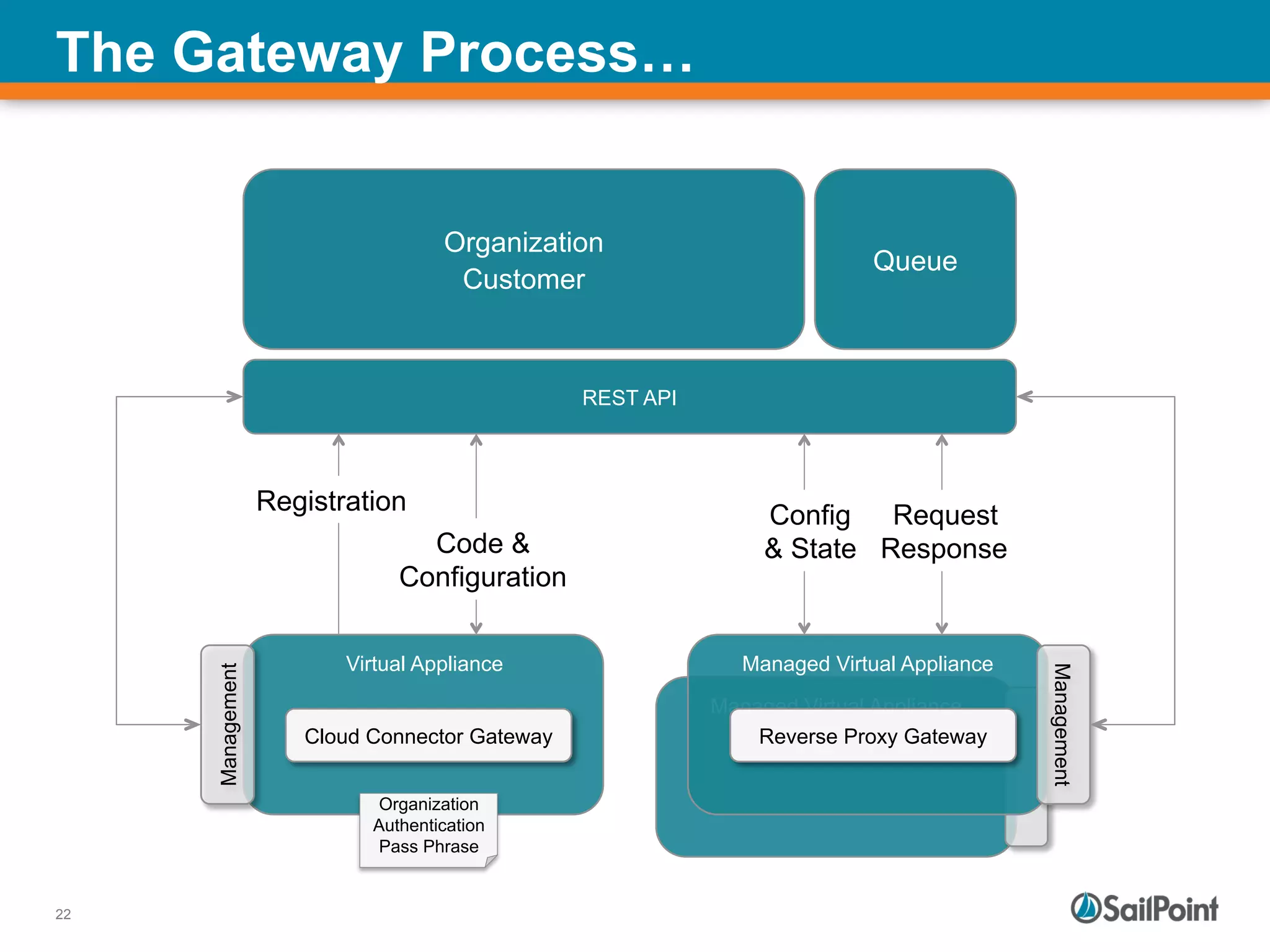
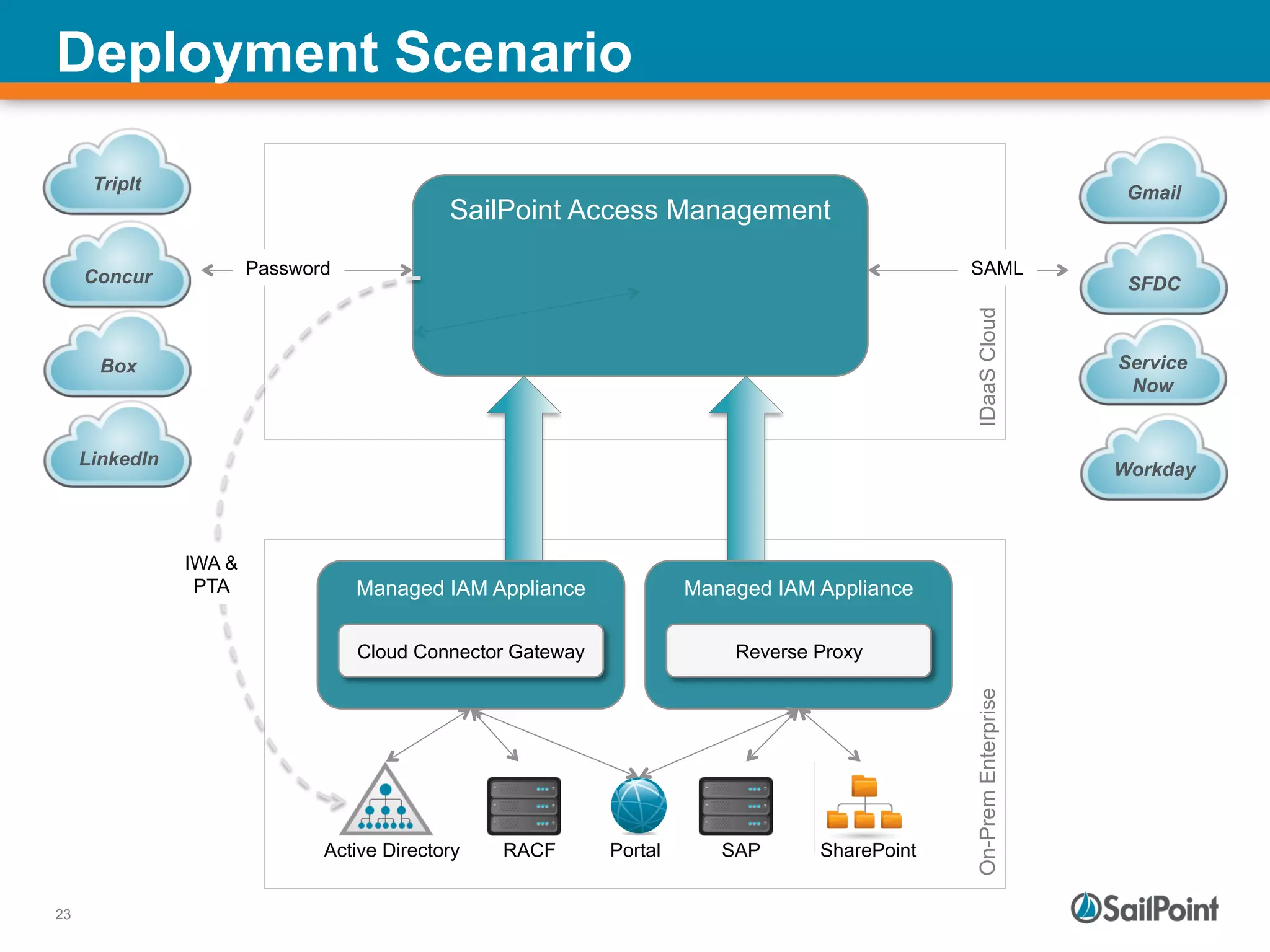
The document discusses the challenges and solutions in managing Identity and Access Management (IAM) for hybrid IT environments. It highlights the shift towards cloud-based and mobile solutions while avoiding pitfalls such as fragmentation and lack of governance. The presentation also includes case studies that illustrate successful IAM implementations and the importance of a cohesive approach to identity management.